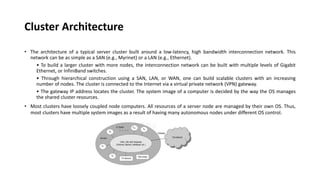
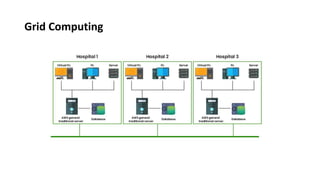
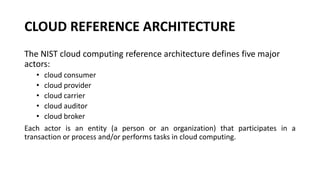
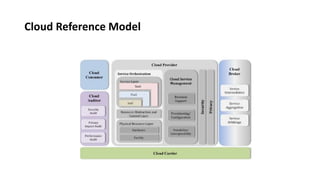
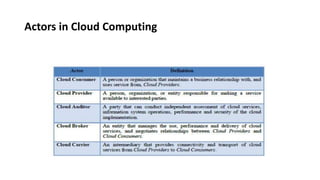
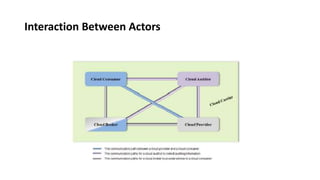
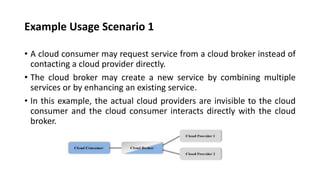
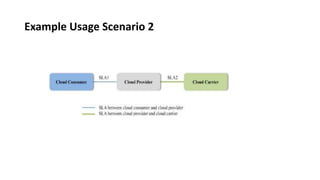
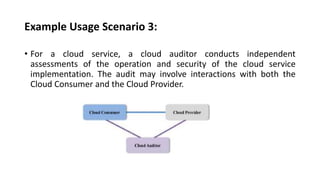
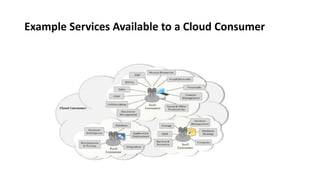
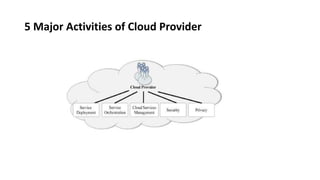
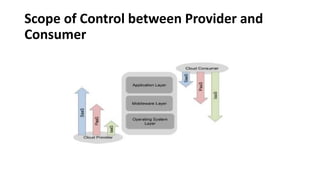
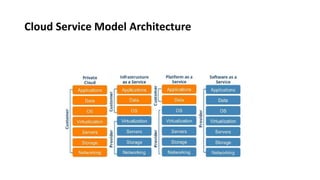
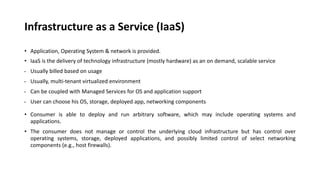
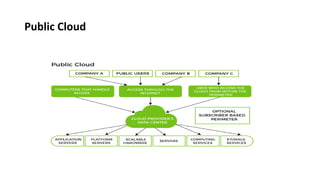
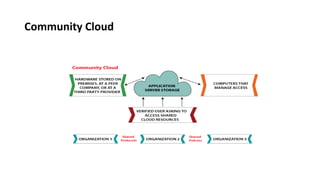
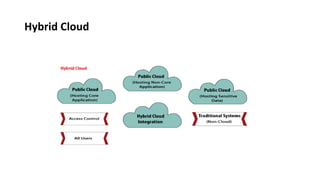
This document provides an overview of different distributed computing models including cluster computing, grid computing, peer-to-peer networks, and cloud computing. It describes key characteristics of each model such as architecture, advantages, disadvantages, and applications. Cluster computing uses interconnected stand-alone computers that work cooperatively, while grid computing consists of distributed systems from different administrative domains. Peer-to-peer networks allow sharing of files directly between nodes without a centralized server. Cloud computing provides scalable computing resources over the Internet.