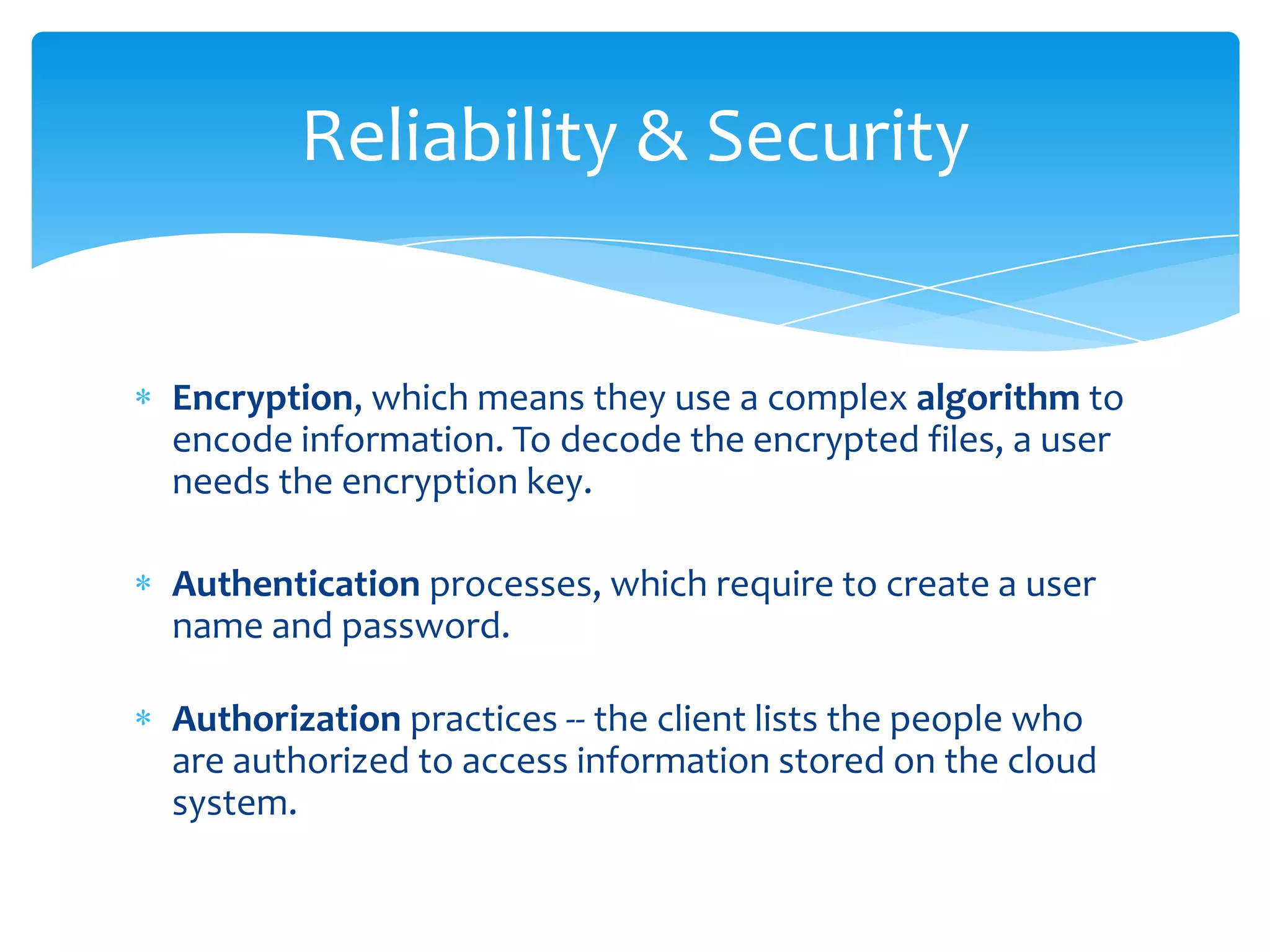
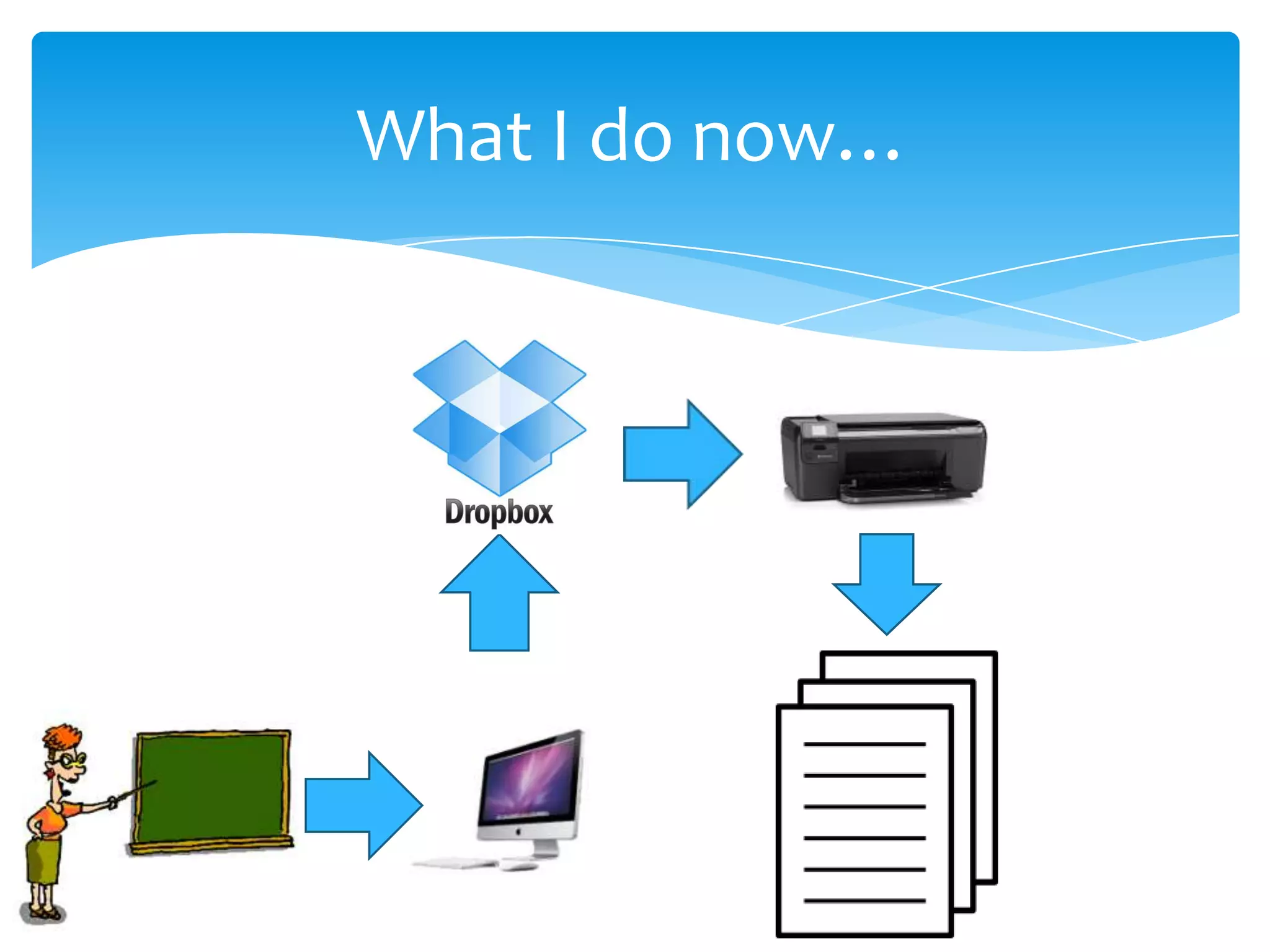
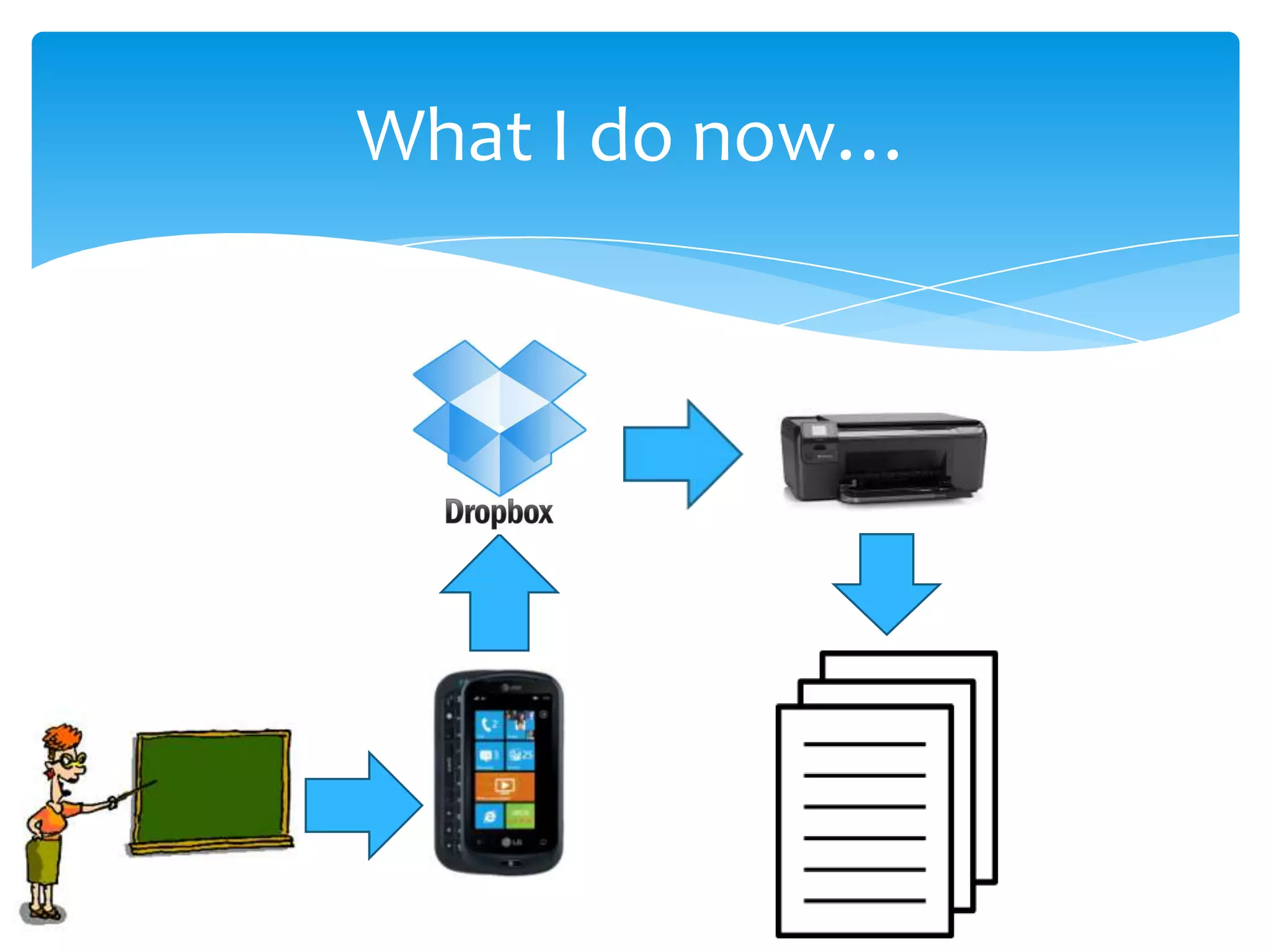
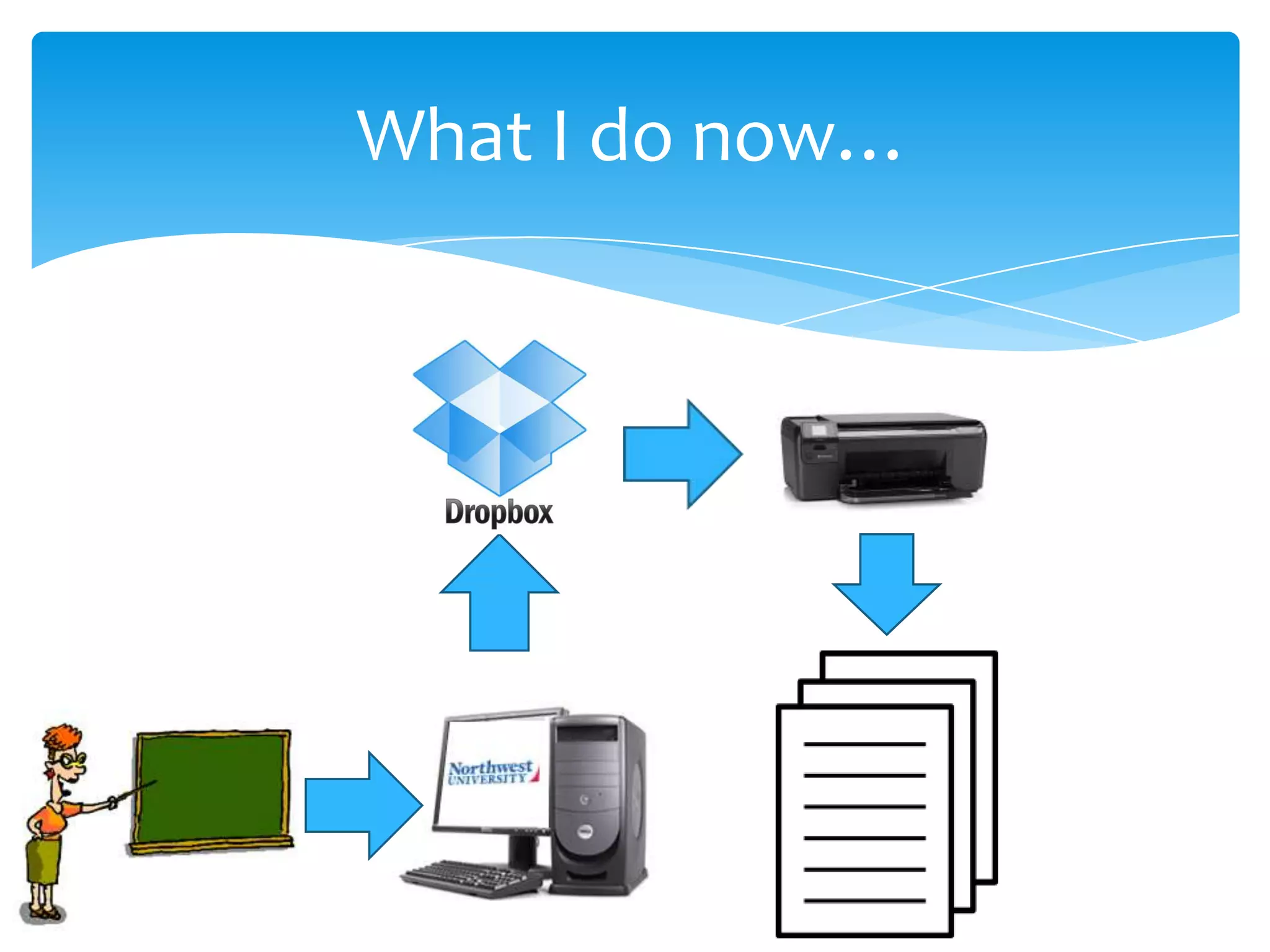
Cloud computing refers to storing and accessing data and programs over the Internet instead of a computer's hard drive. It allows access to data from any location, collaboration, and relies on encryption and authentication for security. Popular cloud storage systems include Dropbox, Google Drive, OneDrive, iCloud, and Amazon Drive.