Embed presentation
Downloaded 14 times




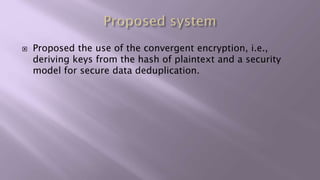
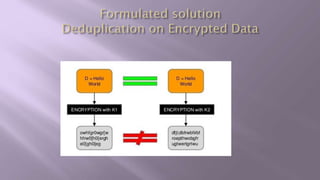
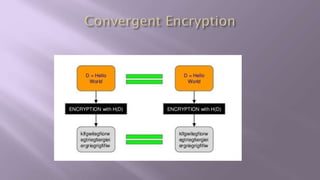
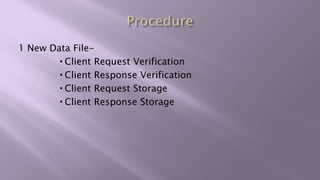
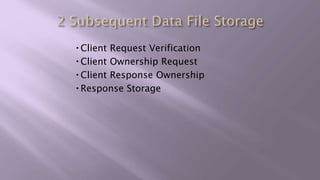

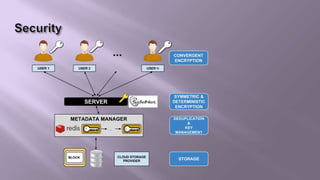






This document proposes a system for secure client-side data deduplication for cloud storage. It suggests using convergent encryption, where keys are derived from the hash of the plaintext, along with a security model. The solution includes a metadata manager that handles deduplication on encrypted blocks and key management separately from data storage. A prototype is being tested for performance analysis of typical operations like edit, append and delete with promising initial results. The proposed system provides confidentiality while allowing for block-level deduplication with negligible performance impact.
















