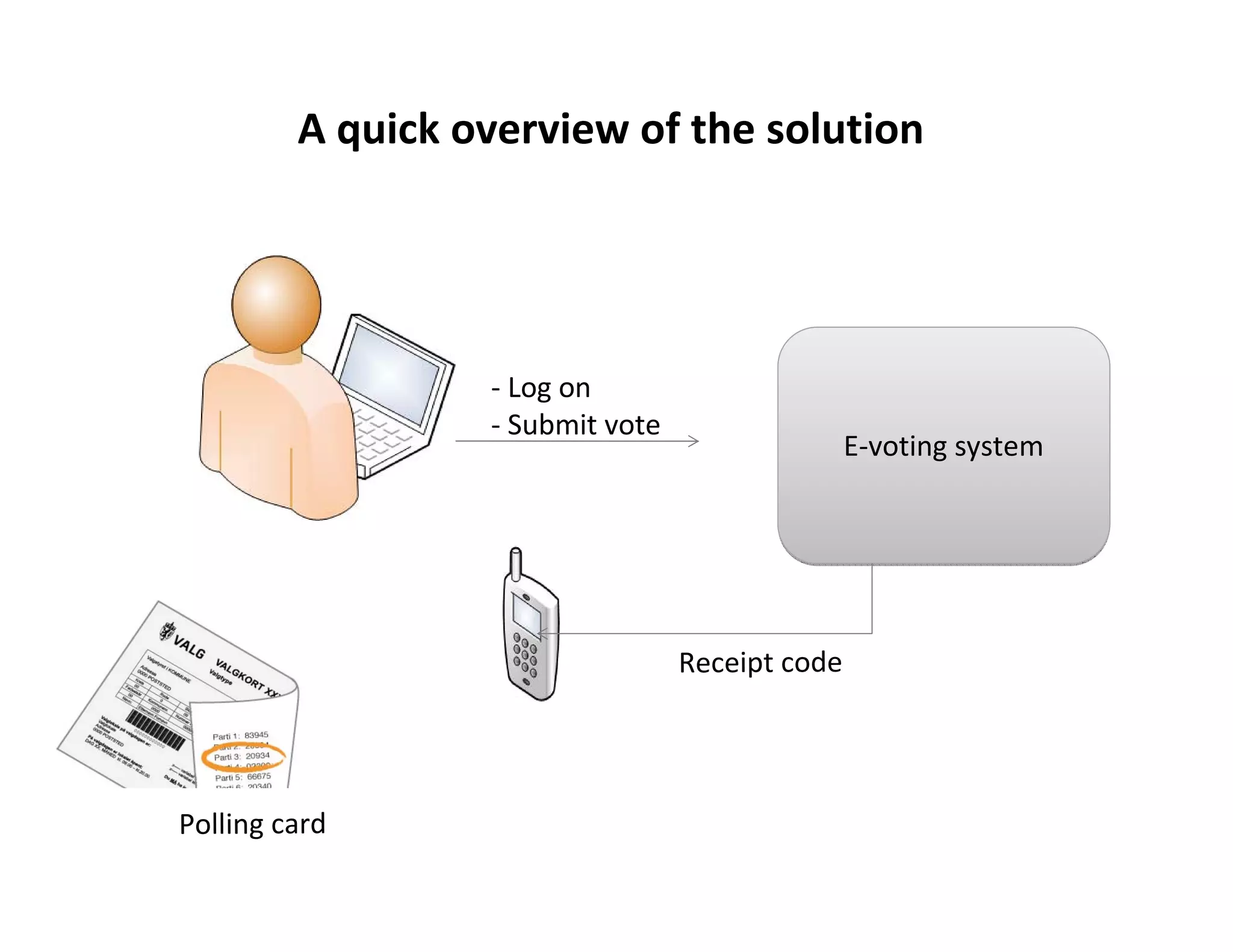
This document discusses the challenges and risks of remote electronic voting (e-voting) over the internet. It outlines some of the key requirements for a remote e-voting system, such as ballot secrecy and strong voter authentication. It also examines several challenges in more depth, like ensuring the system is transparent and auditable to non-experts, preventing the buying and selling of votes, and addressing risks of coercion and home computer security issues. The document proposes some solutions to these challenges, like allowing voters to change their votes an unlimited number of times and prioritizing paper votes over electronic ones.