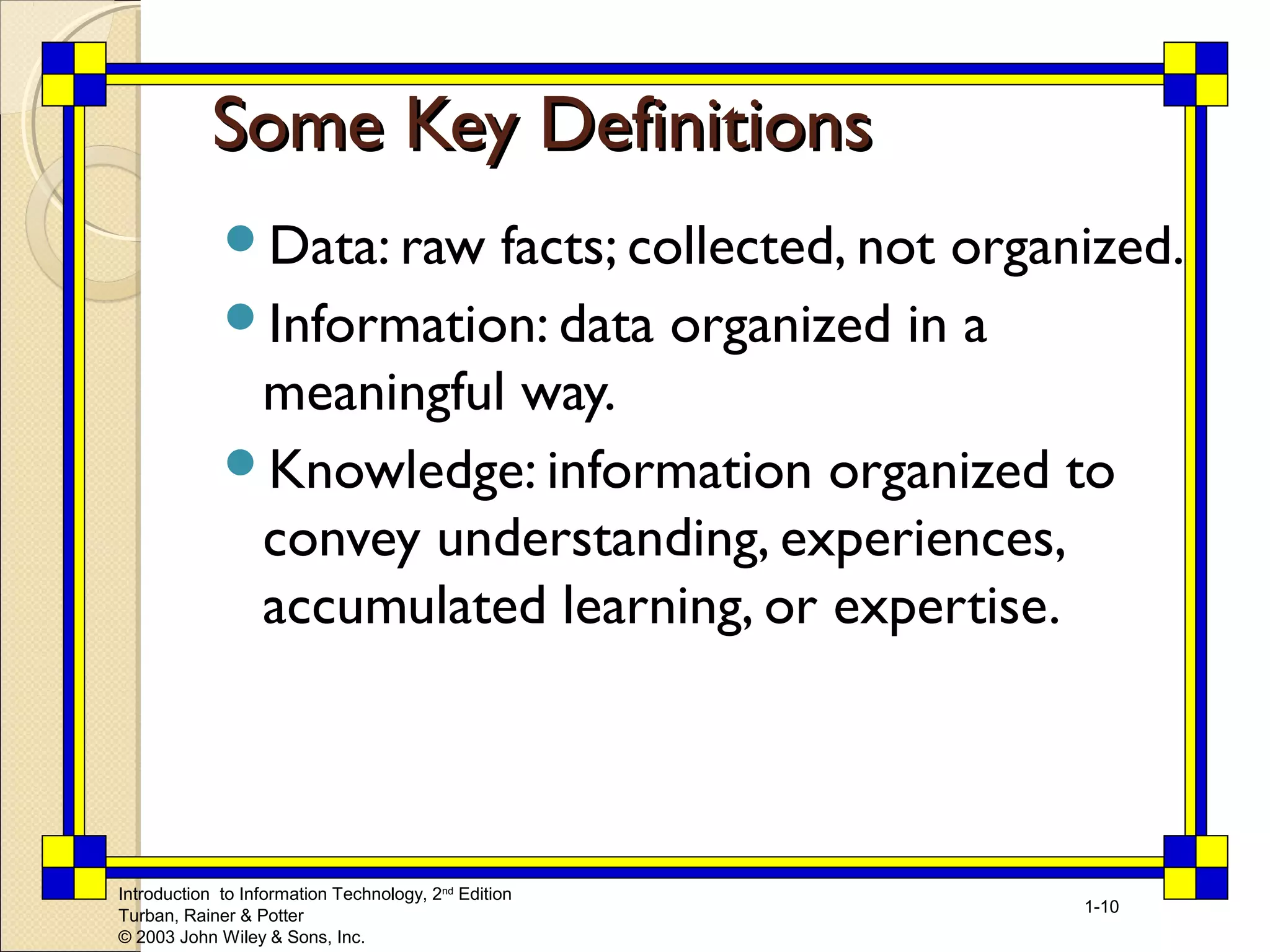
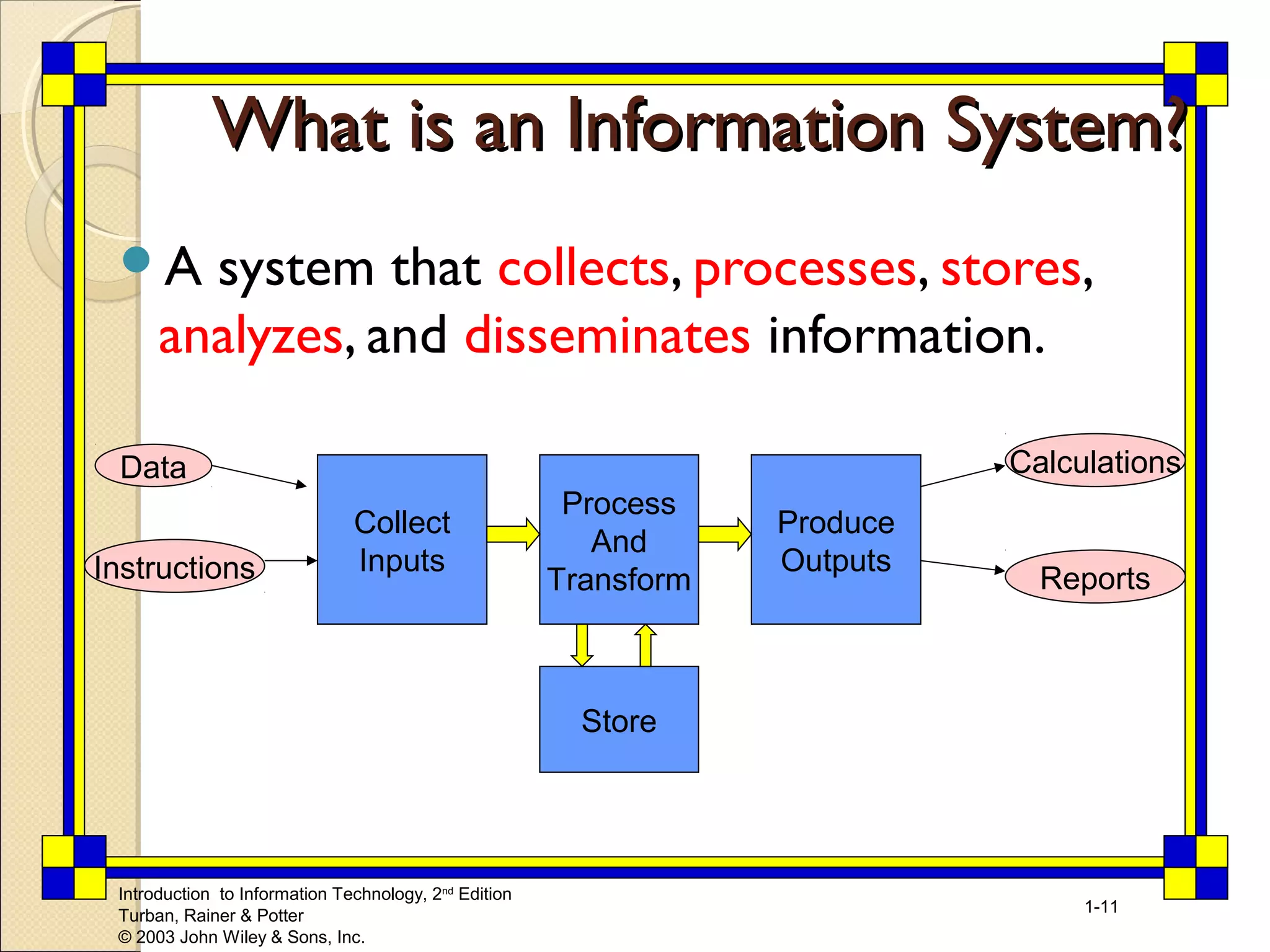
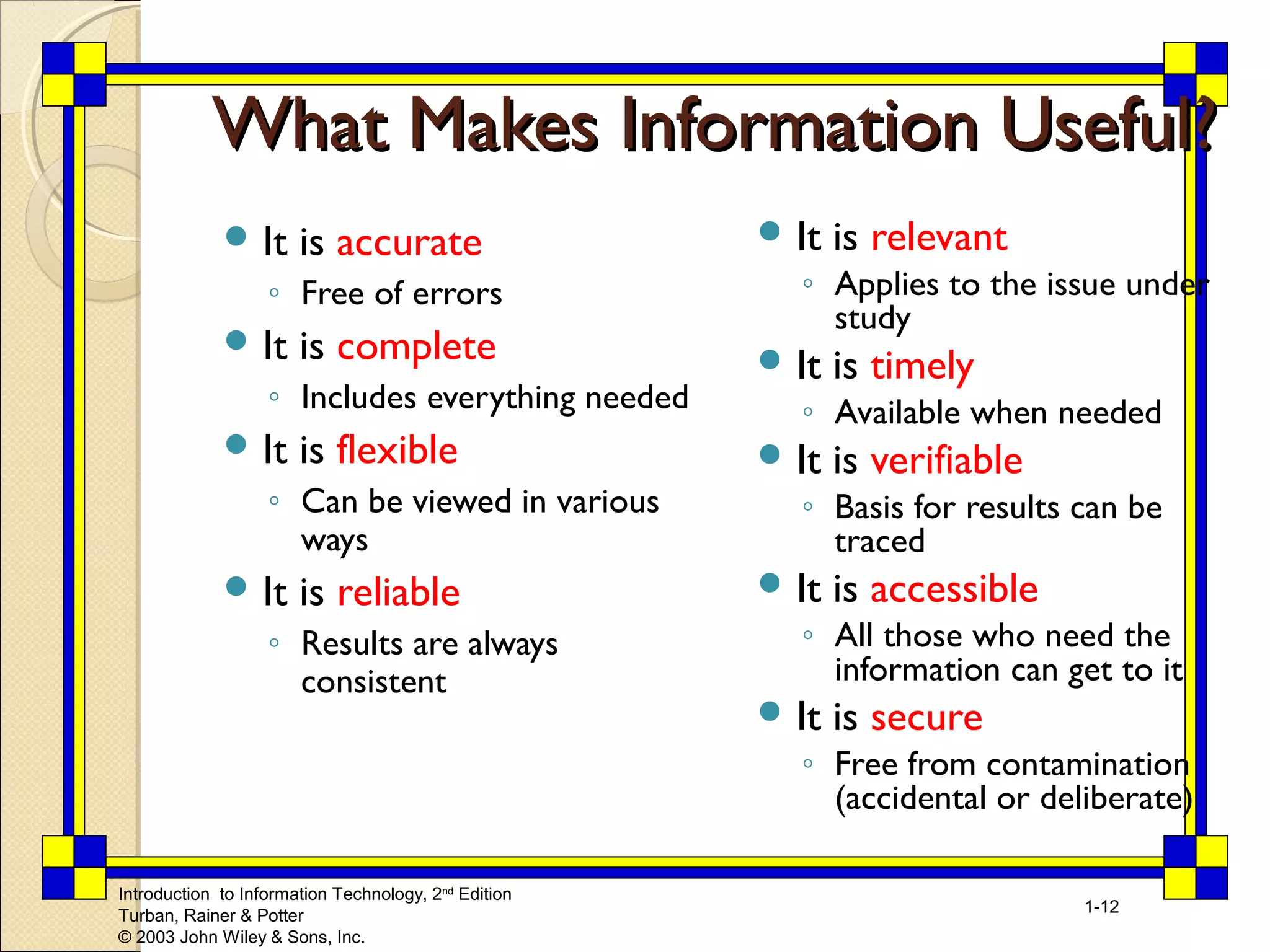
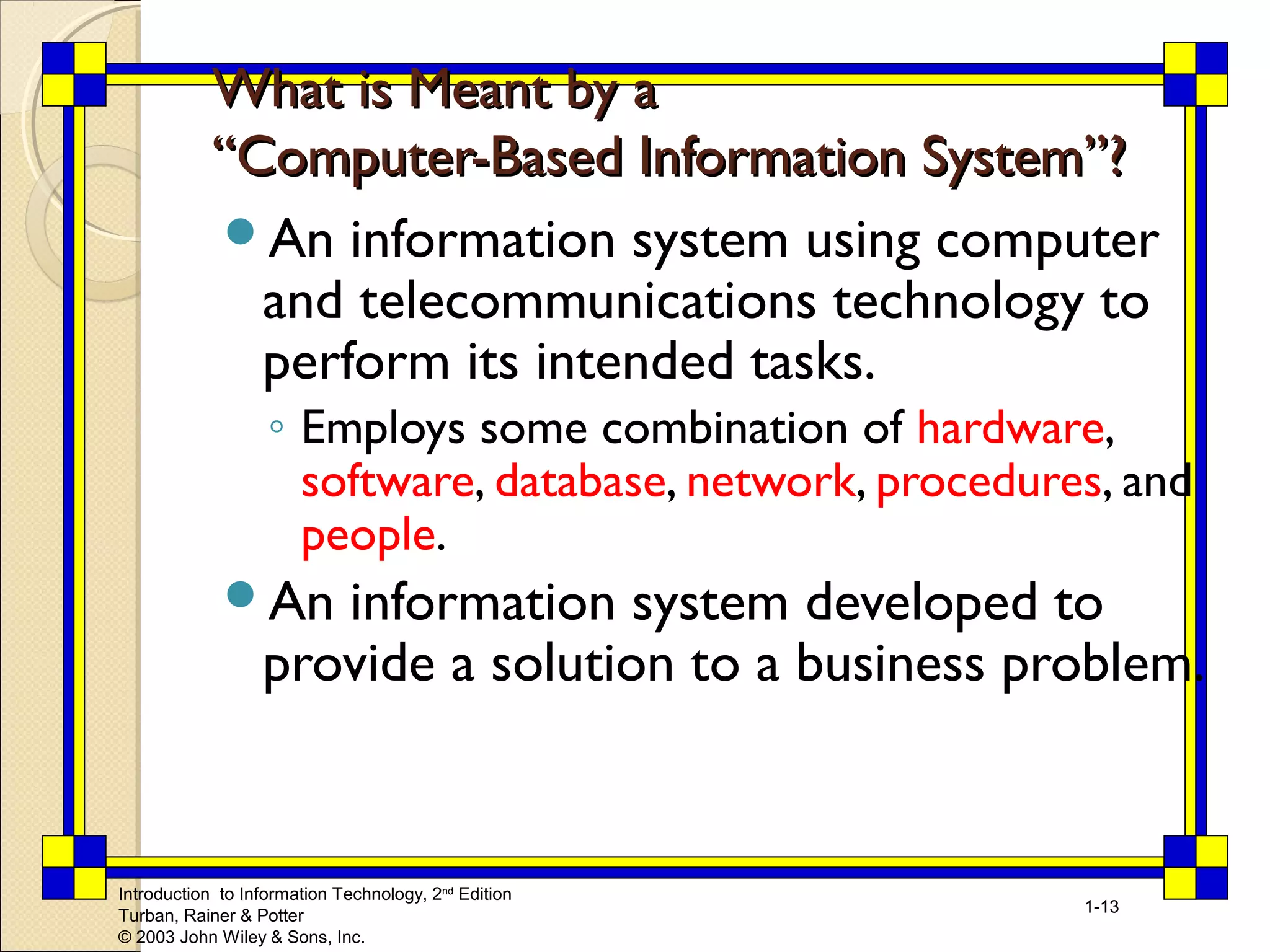
This chapter introduces key concepts relating to information technology and its role in business. It discusses how today's business environment is characterized by rapid change, complexity, and other factors that put pressure on businesses. It also defines important terms like data, information and knowledge. The chapter explores how organizations use information systems to process transactions, support decision making and gain competitive advantages. It provides examples of how companies are leveraging information technology in areas like e-commerce and business intelligence.