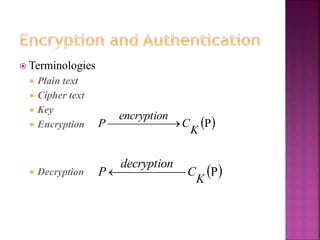
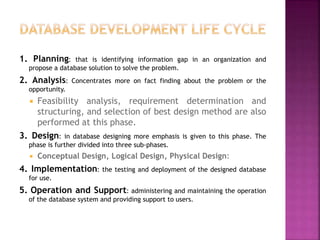
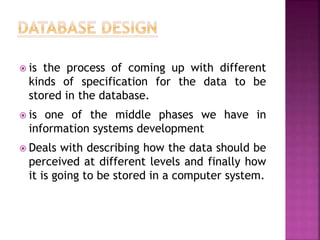
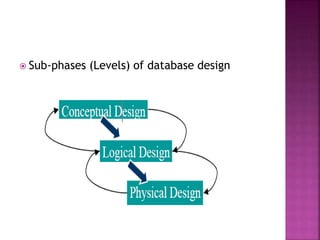
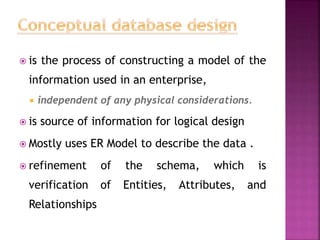
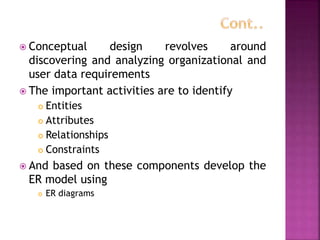
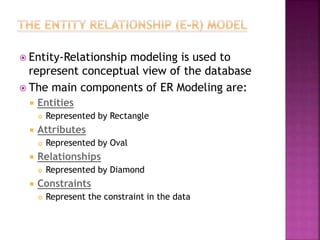
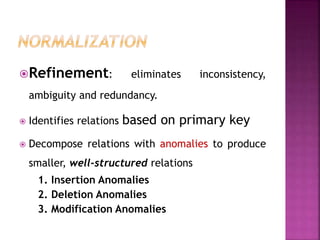
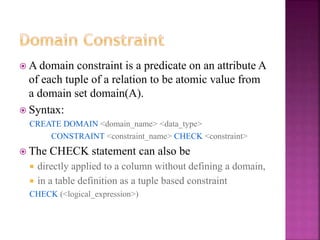
The document discusses the phases of database development: planning, analysis, design, implementation, and operation and support. It also covers database design in depth, including conceptual design, logical design, and physical design. Security concepts like authorization, authentication, encryption, and access control are also summarized.












![23
The trigger events are:
INSERT, DELETE, UPDATE and SELECT.
The actions for the triggers may be taken:
After successful completion of the operation (event): AFTER
Before the execution of the operation (event): BEFORE (INSTEAD OF)
Syntax
CREATE TRIGGER <trigger_name>
ON {<table>|<view>}
{FOR | AFTER | INSTEAD OF} {[INSERT] | [UPDATE] | [DELETE] |
[SELECT]}
AS
<SQL_Statement>](https://image.slidesharecdn.com/chapterfivephysicaldatabasedesign-221125052312-91b4b4df/85/Chapter-Five-Physical-Database-Design-pptx-23-320.jpg)
![24
Create a trigger that inserts the employee id to the
fulltime employee table if the employee is a
fulltime employee otherwise in the part-time
employee table
CREATE TRIGGER EmployeeType
ON [Employees]
AFTER INSERT
AS
If (SELECT empType From inserted) = 1
INSERT INTO [fulltimeEmployees] (empId)
SELECT empId FROM inserted
ELSE
INSERT INTO [parttimeEmployees] (empId)
SELECT empId FROM inserted](https://image.slidesharecdn.com/chapterfivephysicaldatabasedesign-221125052312-91b4b4df/85/Chapter-Five-Physical-Database-Design-pptx-24-320.jpg)



![28
The syntax for privilege granting is as follows:
GRANT <privilege_list> ON {<table>|<view>}
TO <account_list> [WITH GRANT OPTION]
<privilege_list> is possible data level authorization for
the table or view stated as:
{SELECT | INSERT | UPDATE | DELETE | ALL}
To grant access to a specific column in a table:
GRANT REFERENCES (<column>) ON {<table>|<view>}
TO <account_list> [WITH GRANT OPTION]](https://image.slidesharecdn.com/chapterfivephysicaldatabasedesign-221125052312-91b4b4df/85/Chapter-Five-Physical-Database-Design-pptx-28-320.jpg)
![29
The syntax for privilege revoking is as follows:
REVOKE <privilege_list> ON {<table>|<view>}
FROM <account_list> [RESTRICT | CASCADE]
To revoke grant option from an account:
REVOKE GRANT OPTION FOR <privilege_list> ON
{<table>|<view>}
FROM <account_list>](https://image.slidesharecdn.com/chapterfivephysicaldatabasedesign-221125052312-91b4b4df/85/Chapter-Five-Physical-Database-Design-pptx-29-320.jpg)
![30
The syntax to deny a privilege from an account list
is:
DENY <privilege_list> ON {<table>|<view>}
TO <account_list> [CASCADE]](https://image.slidesharecdn.com/chapterfivephysicaldatabasedesign-221125052312-91b4b4df/85/Chapter-Five-Physical-Database-Design-pptx-30-320.jpg)