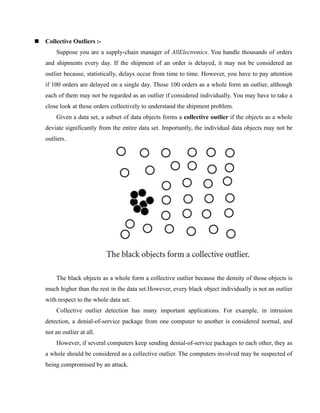
This document discusses outlier detection, including types of outliers (global, contextual, collective), challenges of outlier detection (modeling normal vs abnormal data, application dependence, handling noise), and methods for outlier detection (supervised, unsupervised, proximity-based, clustering-based). Global outliers significantly deviate from the overall data set. Contextual outliers deviate based on specific contextual attributes. Collective outliers involve a subset of data objects that together deviate from the data set, even if individually they are not outliers.