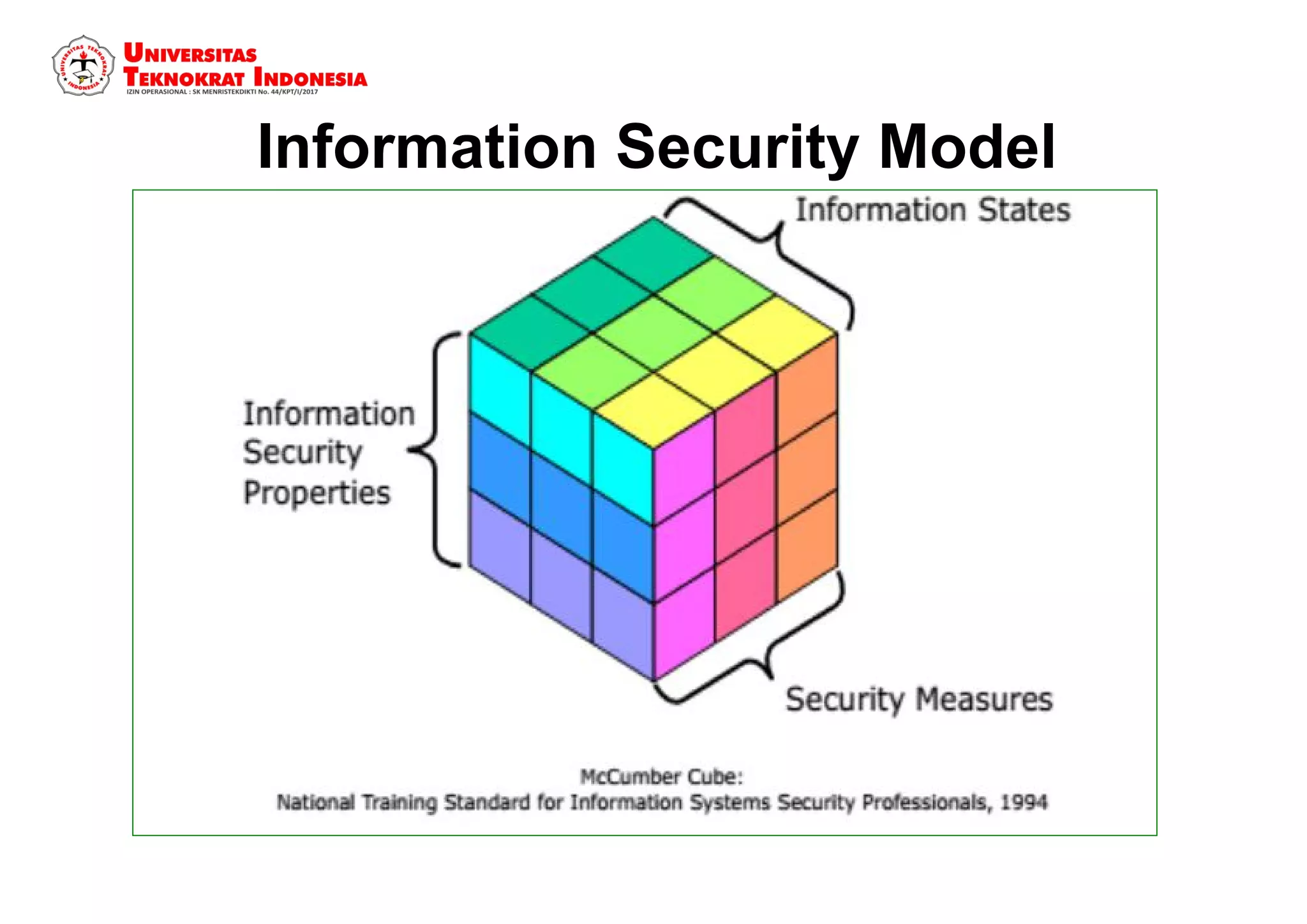
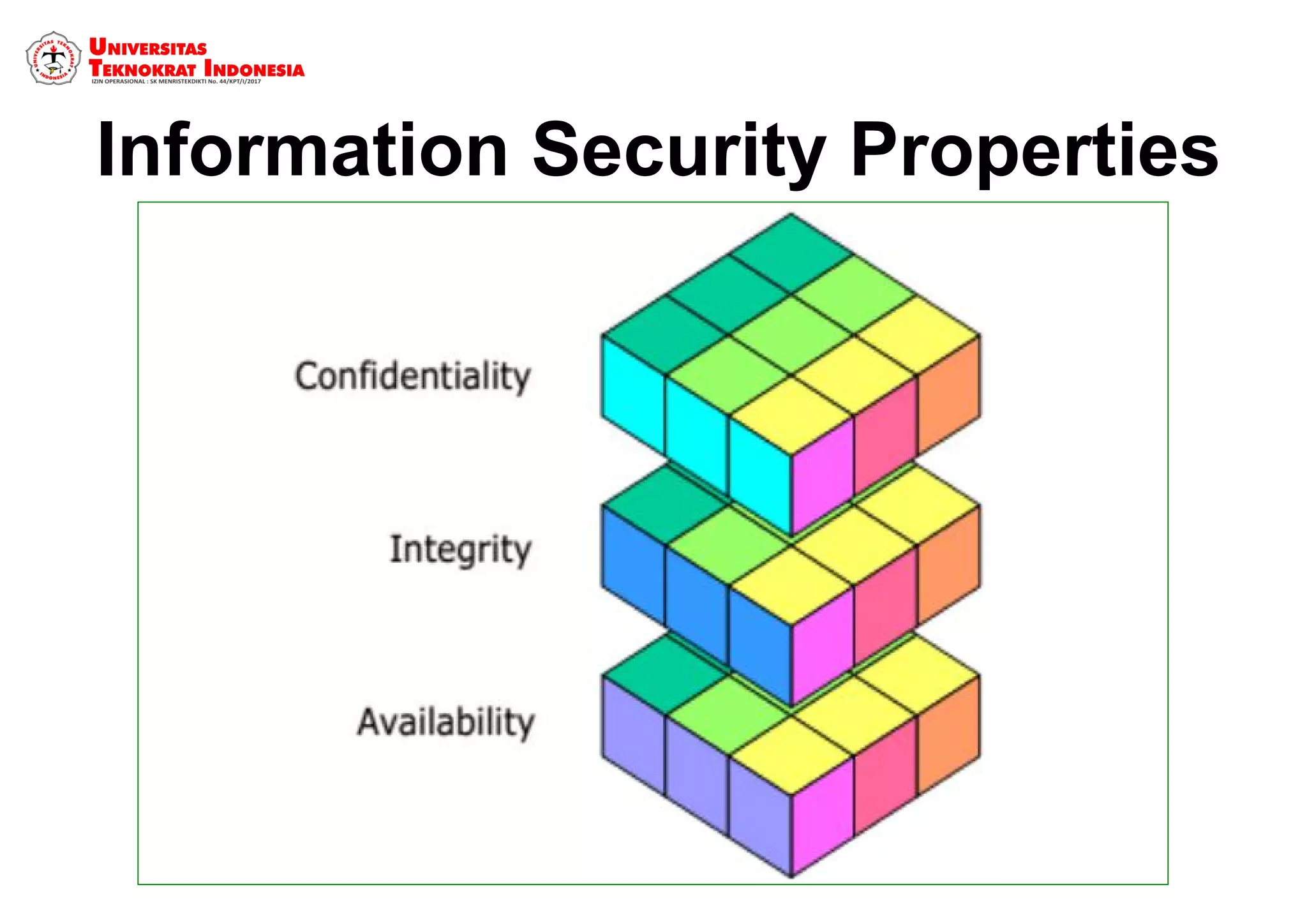
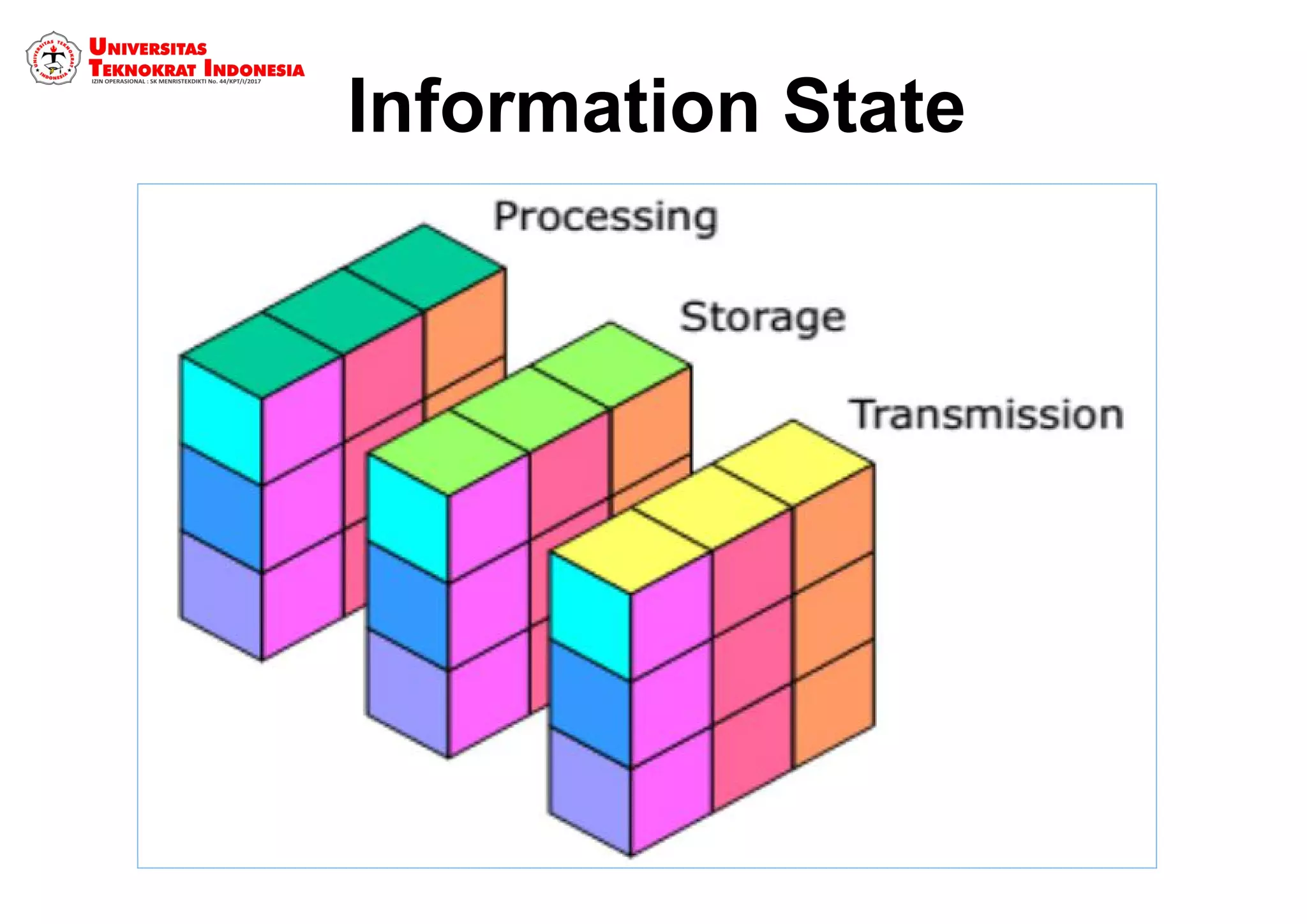
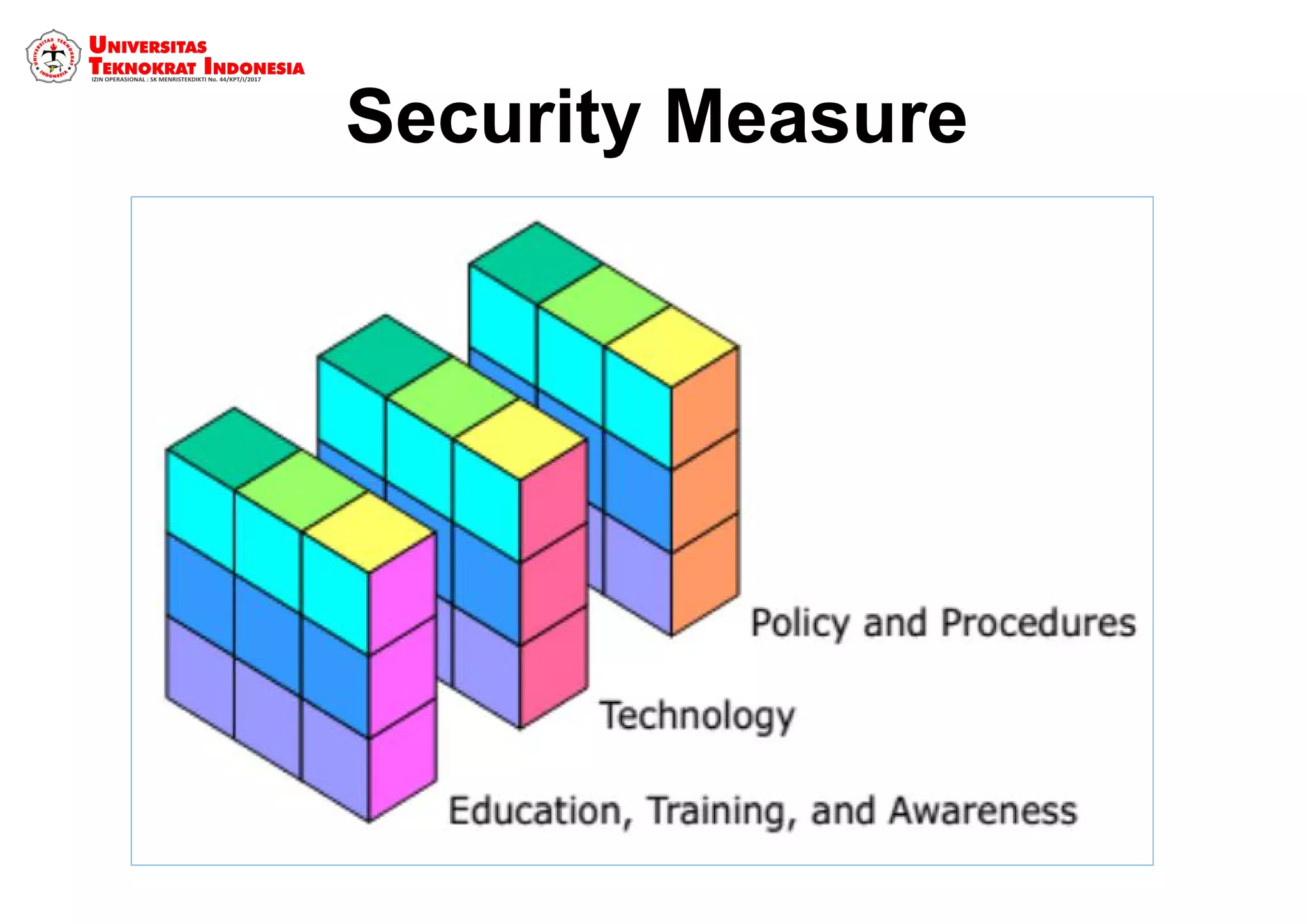
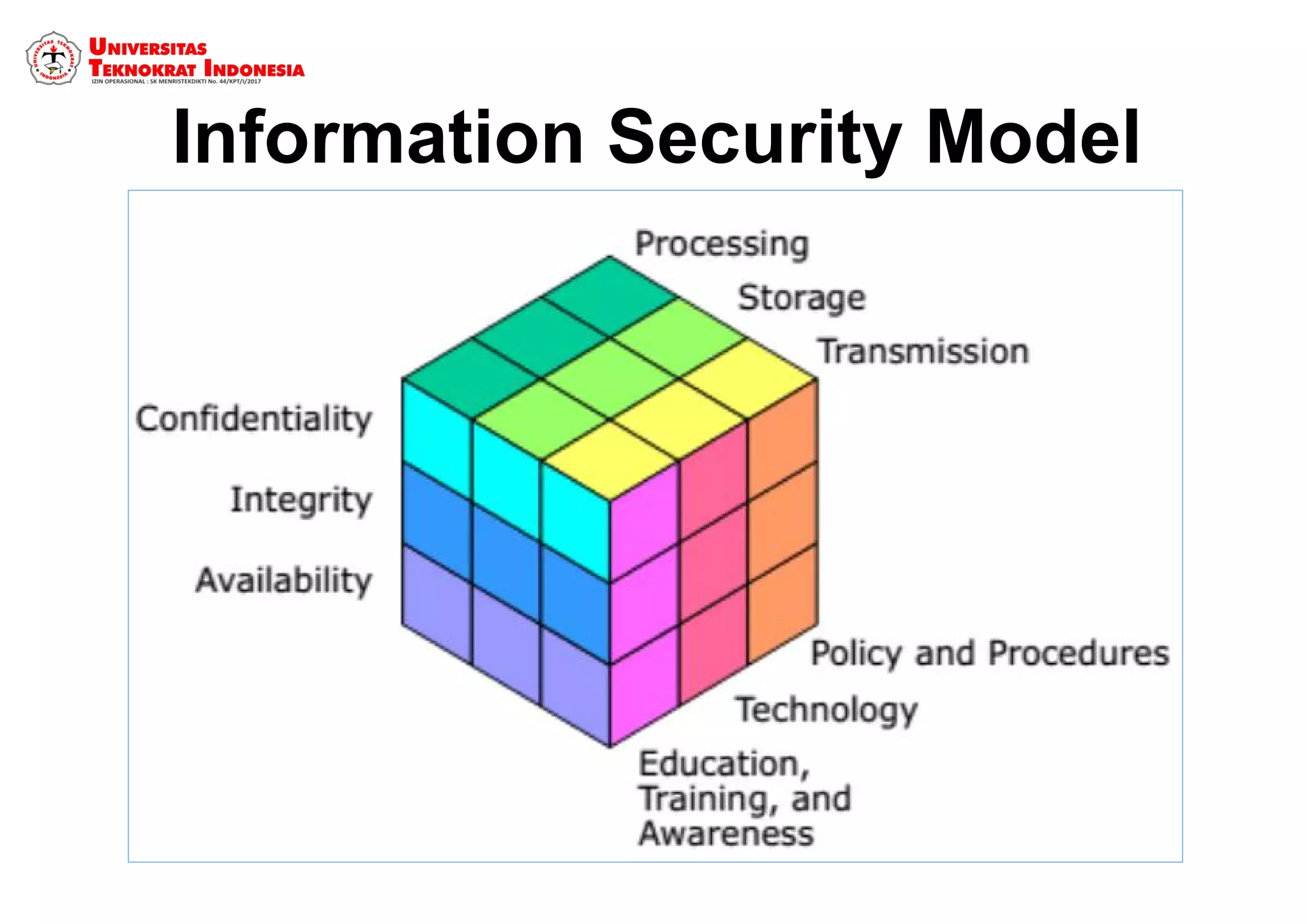
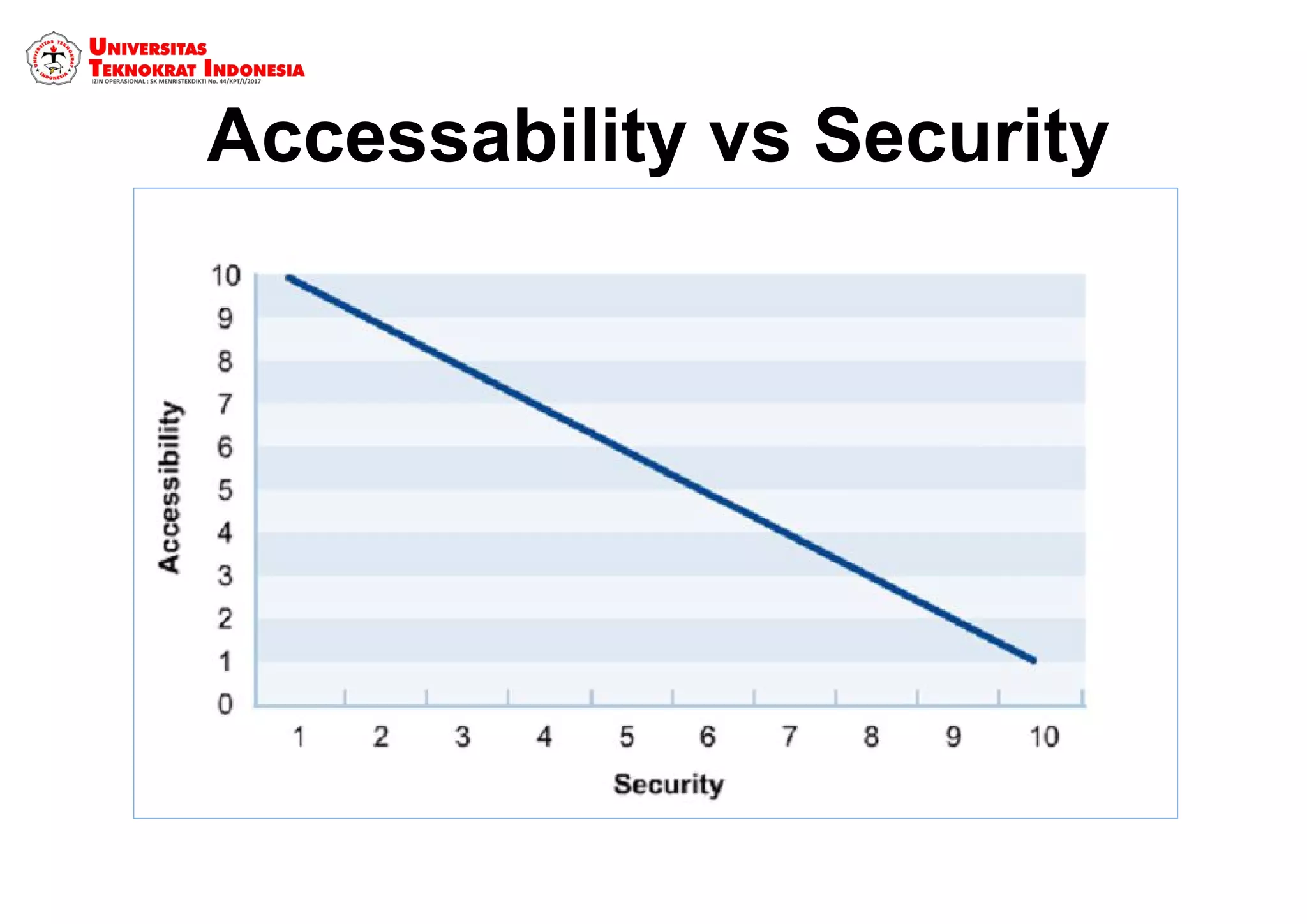
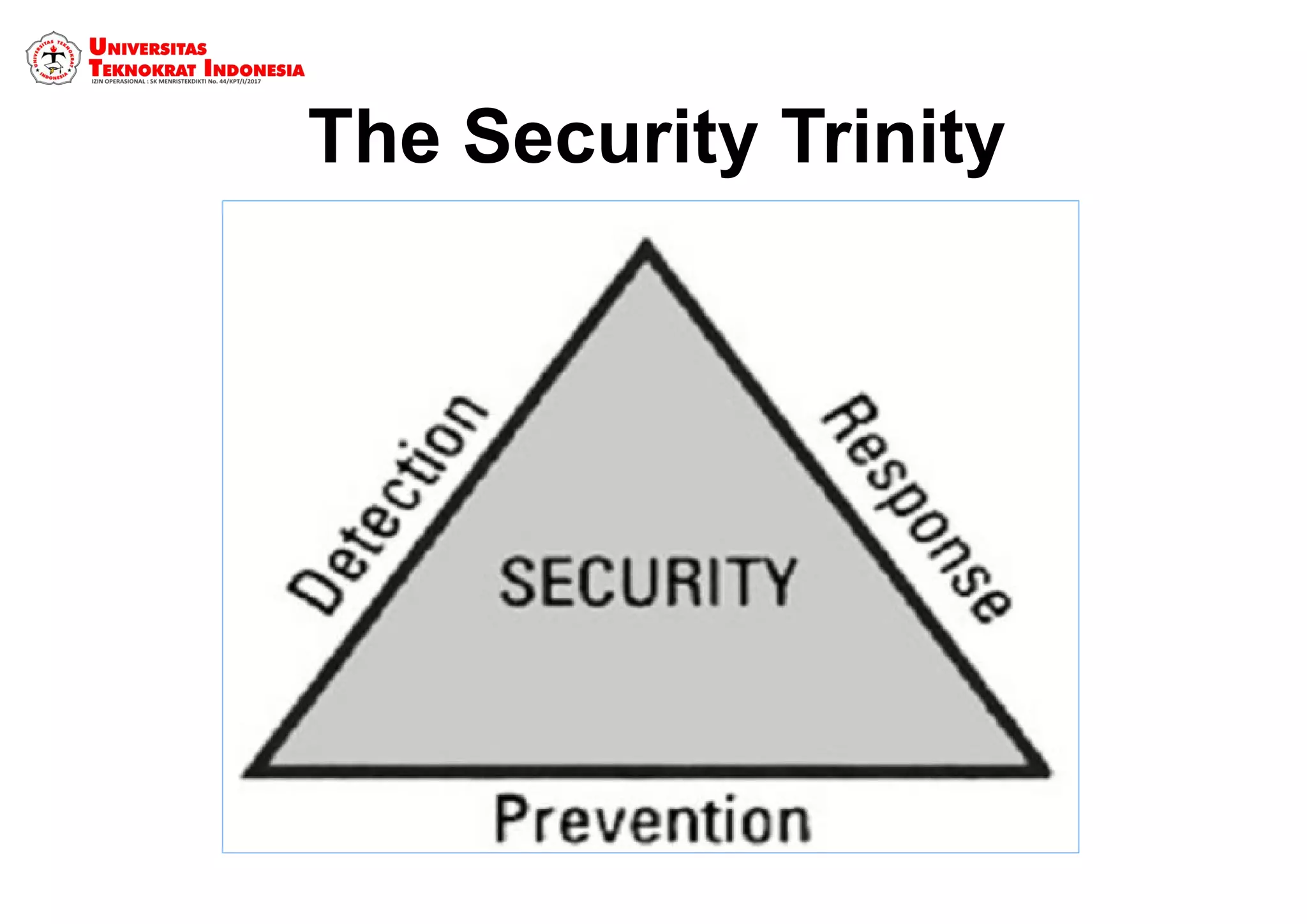
The document discusses information security models and certifications. It covers several common security certifications such as the CISSP, CISM, and CEH. It also discusses the importance of network security and protecting different types of data, including public, internal, confidential, and secret information. The primary goals of a good security system are outlined as protecting confidentiality, ensuring data integrity, and ensuring data availability.