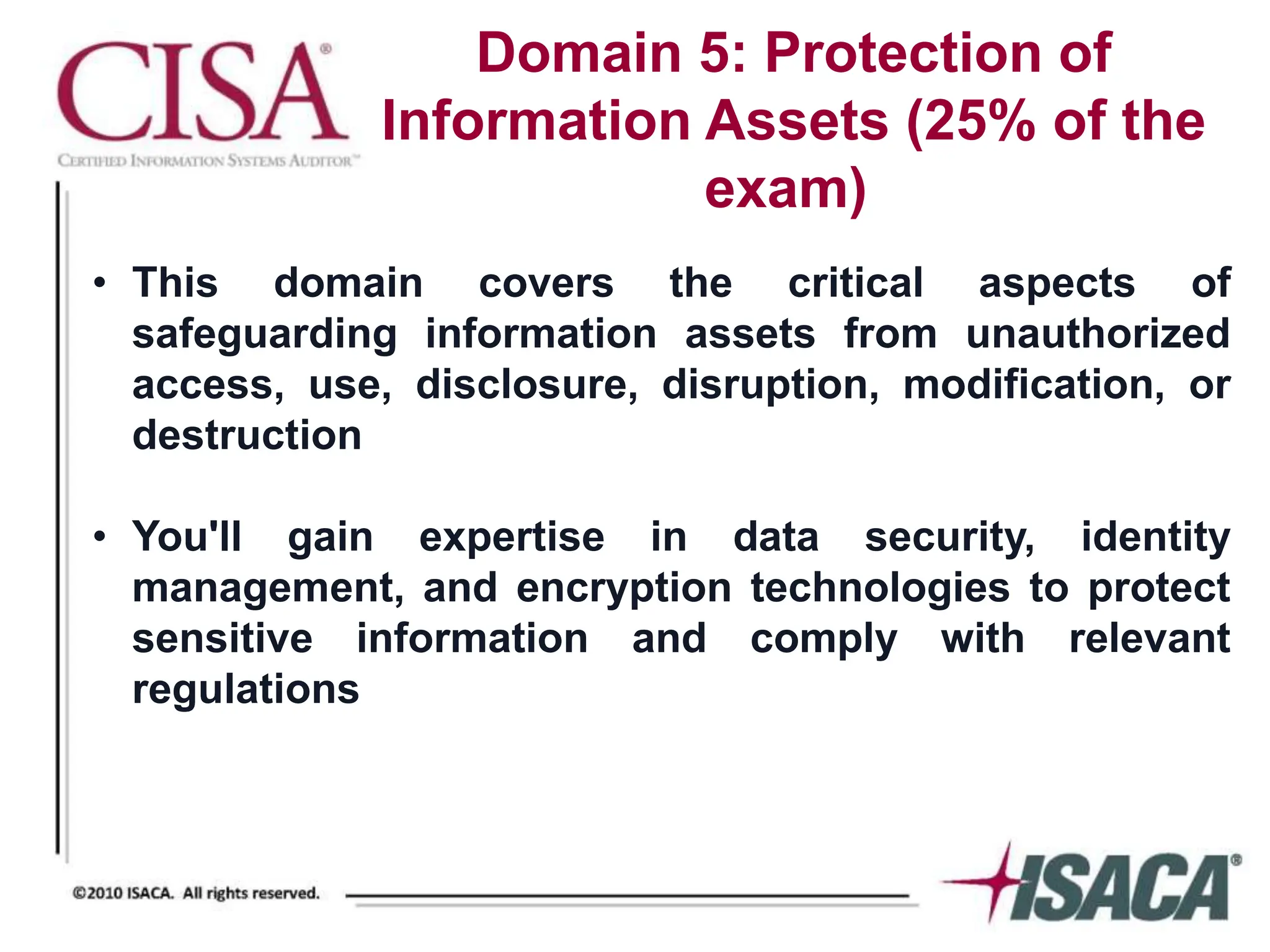
This document provides an overview of Domain 5 - Protection of Information Assets, which covers 25% of the Certified Information Systems Auditor (CISA) exam. Domain 5 focuses on evaluating controls to protect information assets, including logical security controls, physical and environmental security controls, information management, and evaluating the overall effectiveness of the security system. Specific topics covered include data security principles, access control, encryption, security incident response, privacy laws, and risks of BYOD and cloud computing.