Embed presentation
Downloaded 46 times






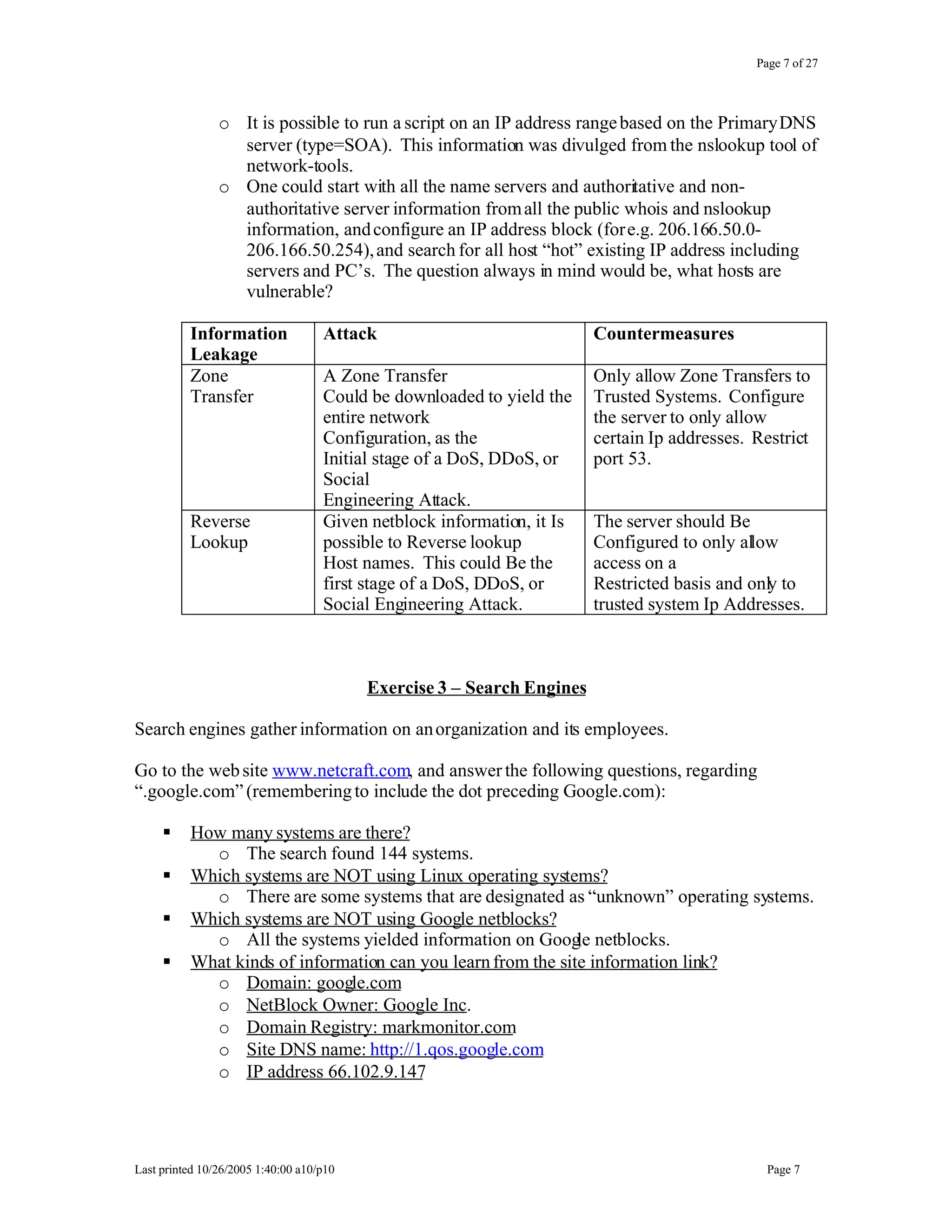
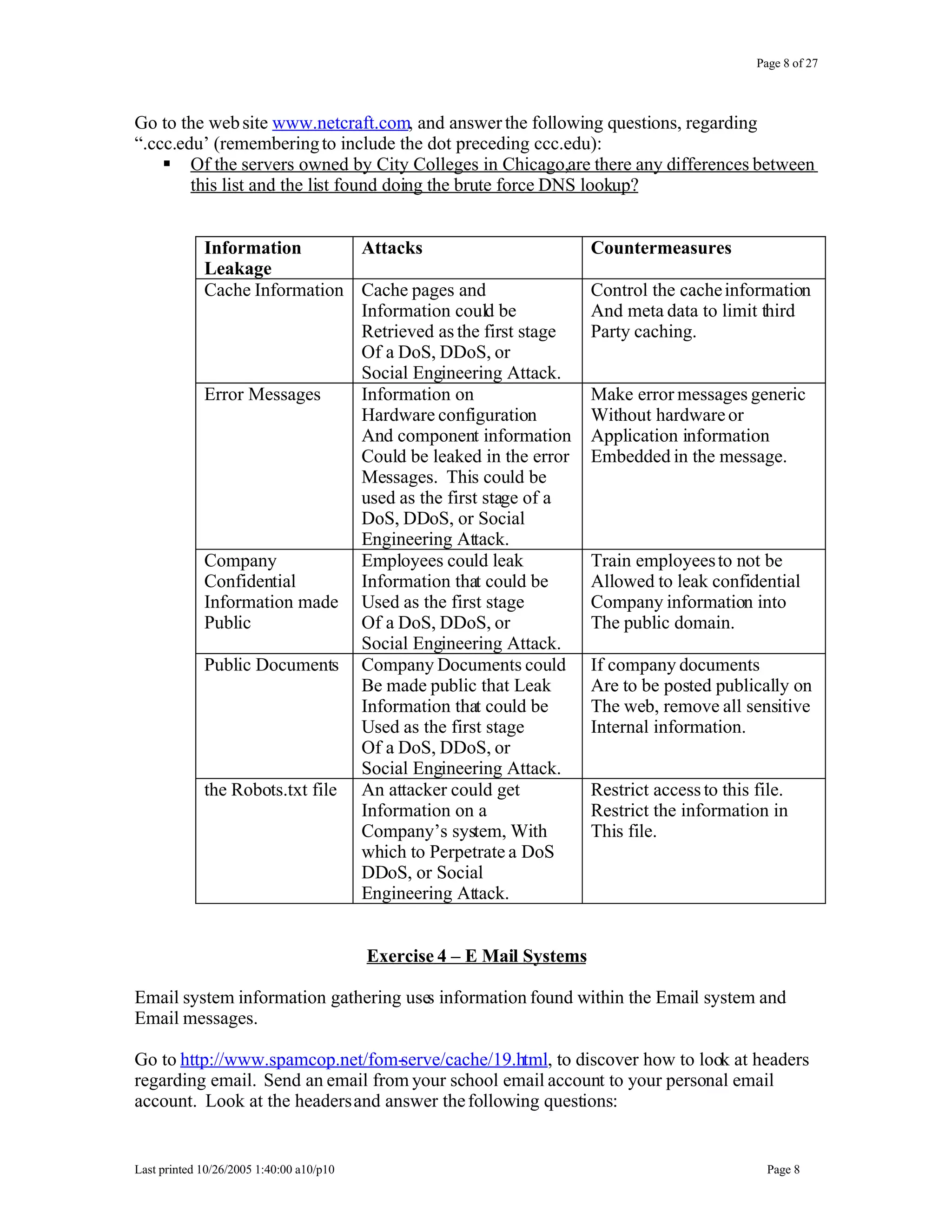



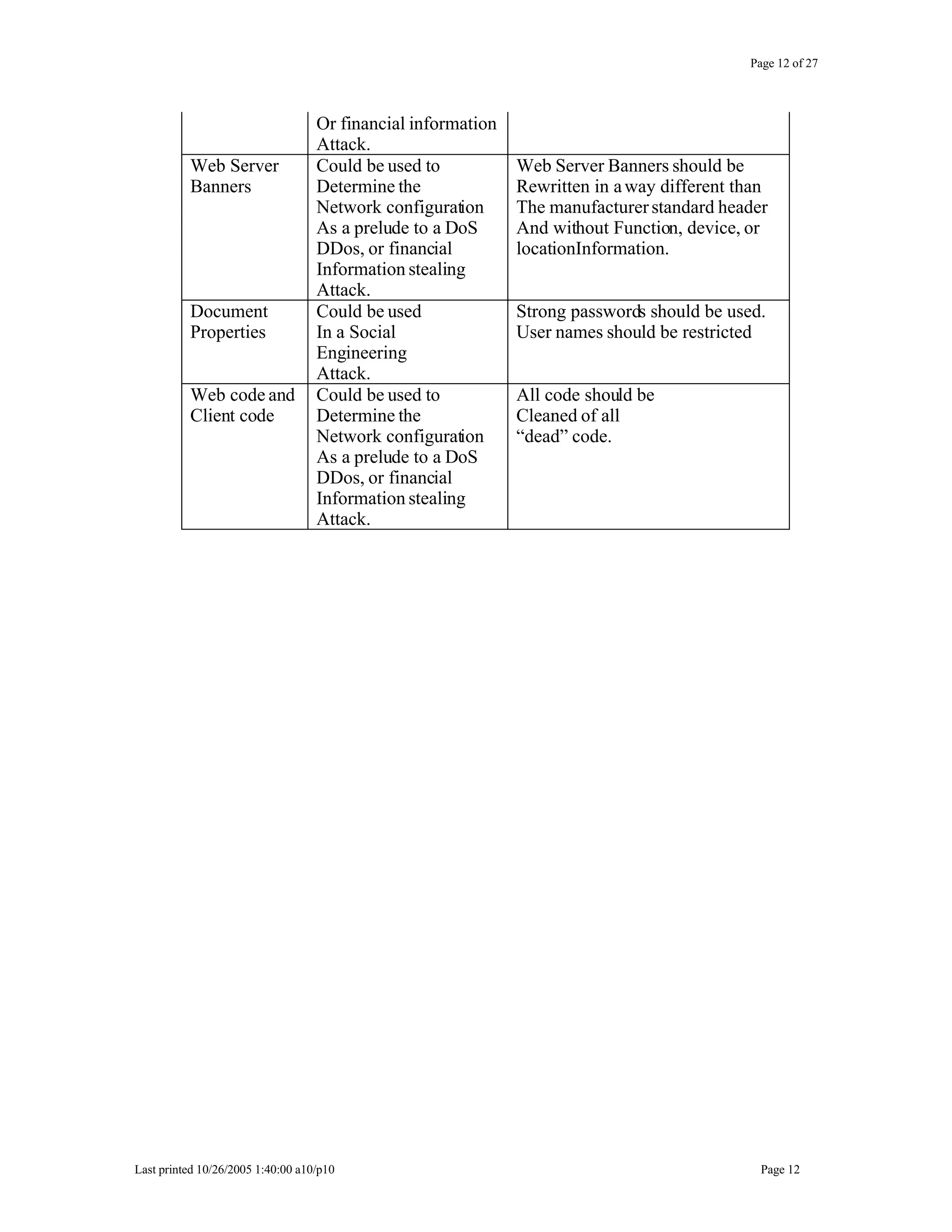


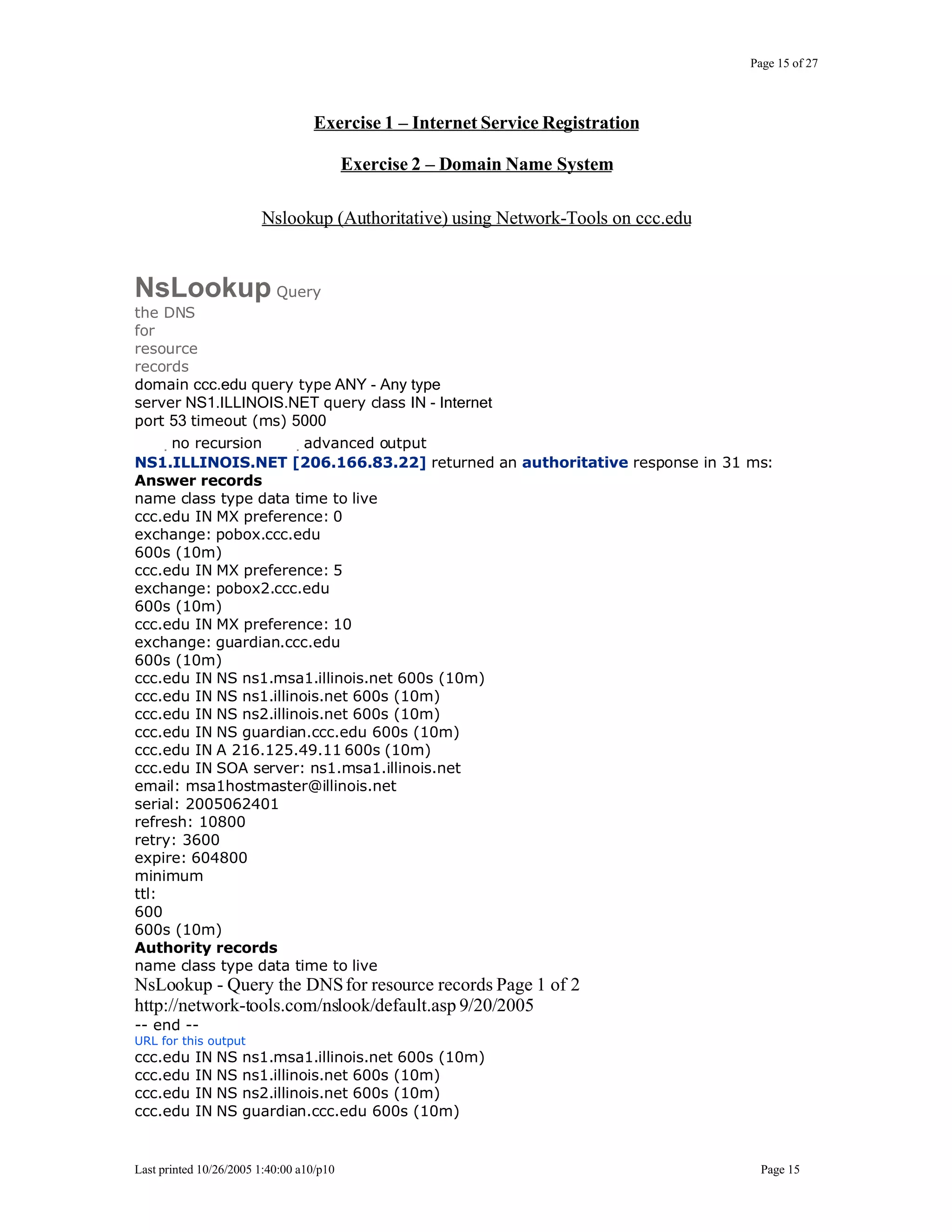

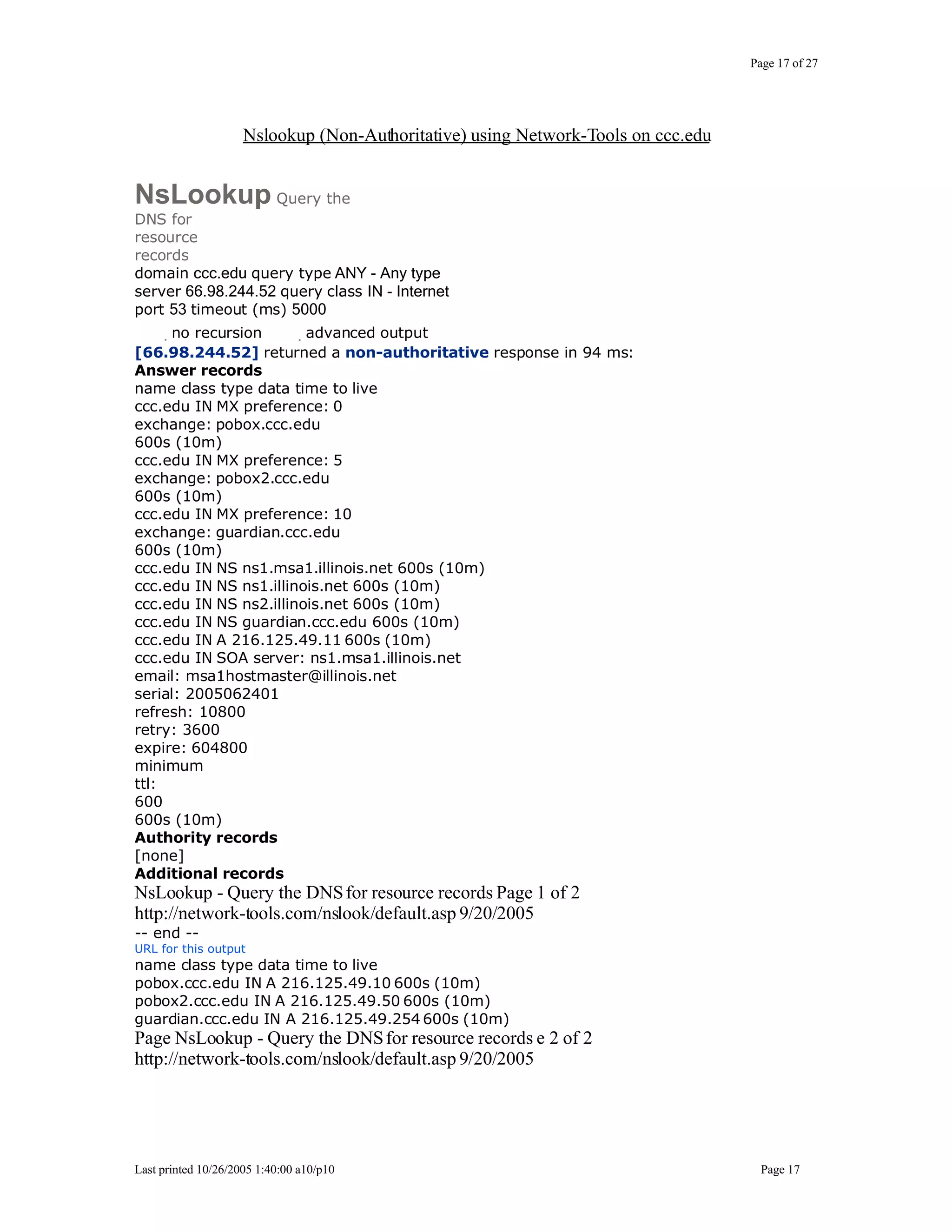
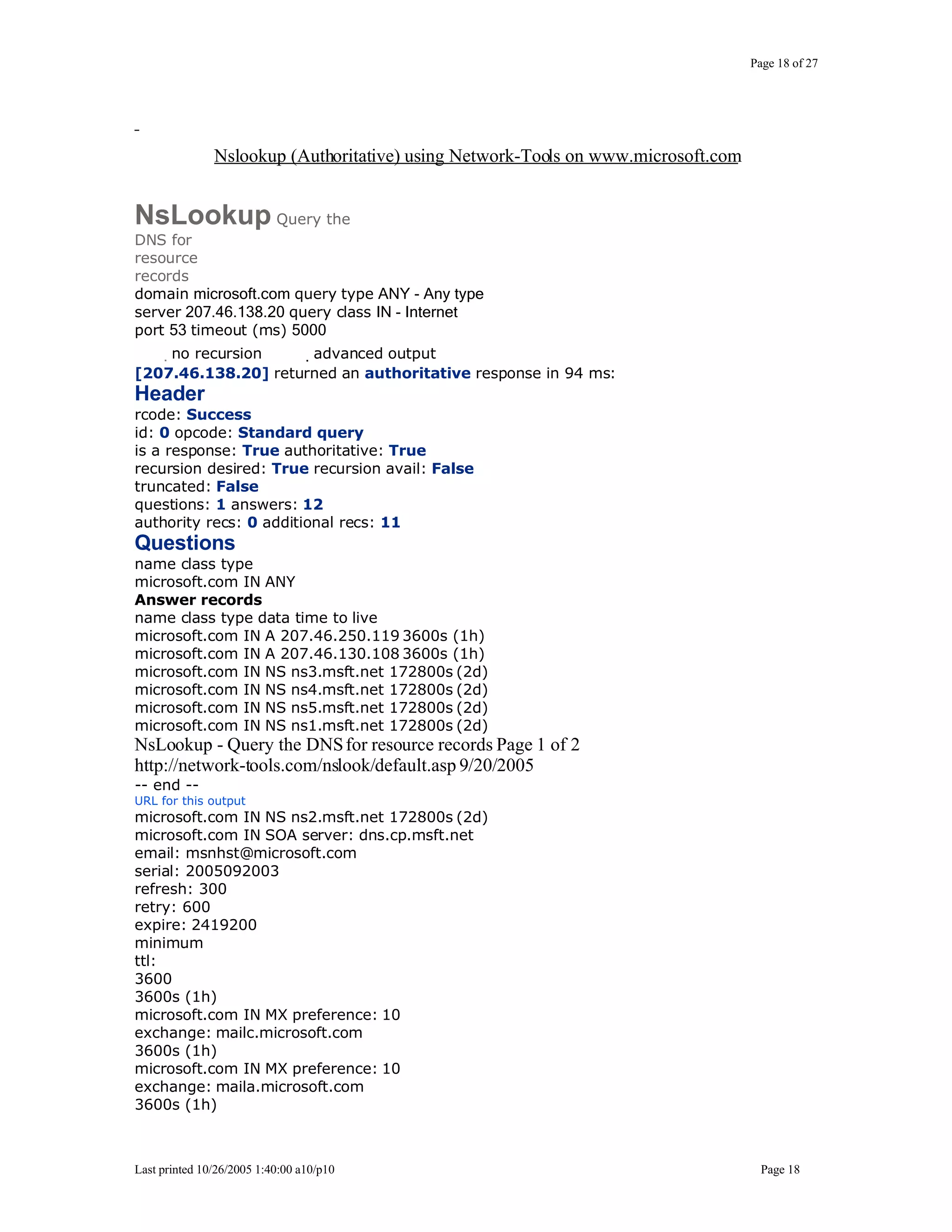
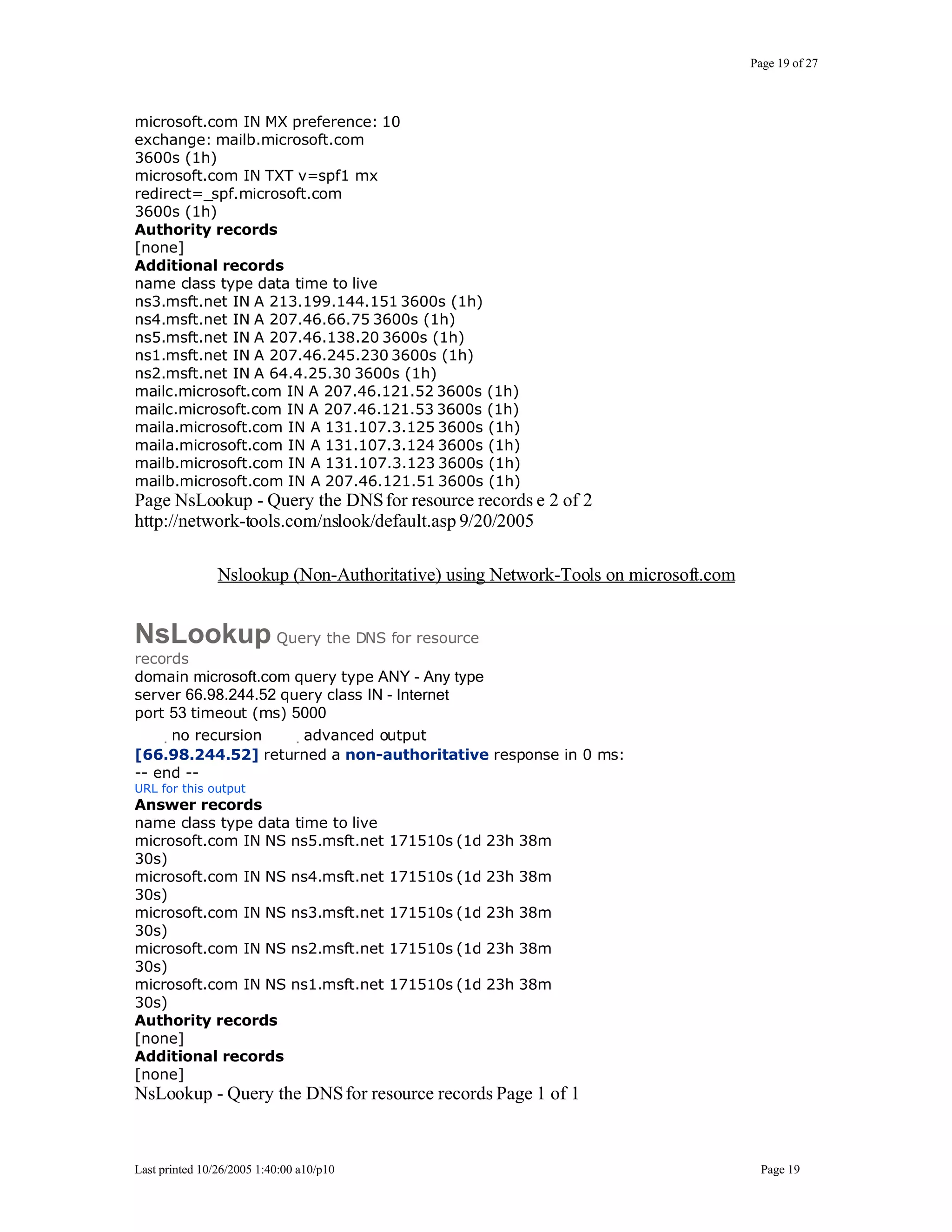


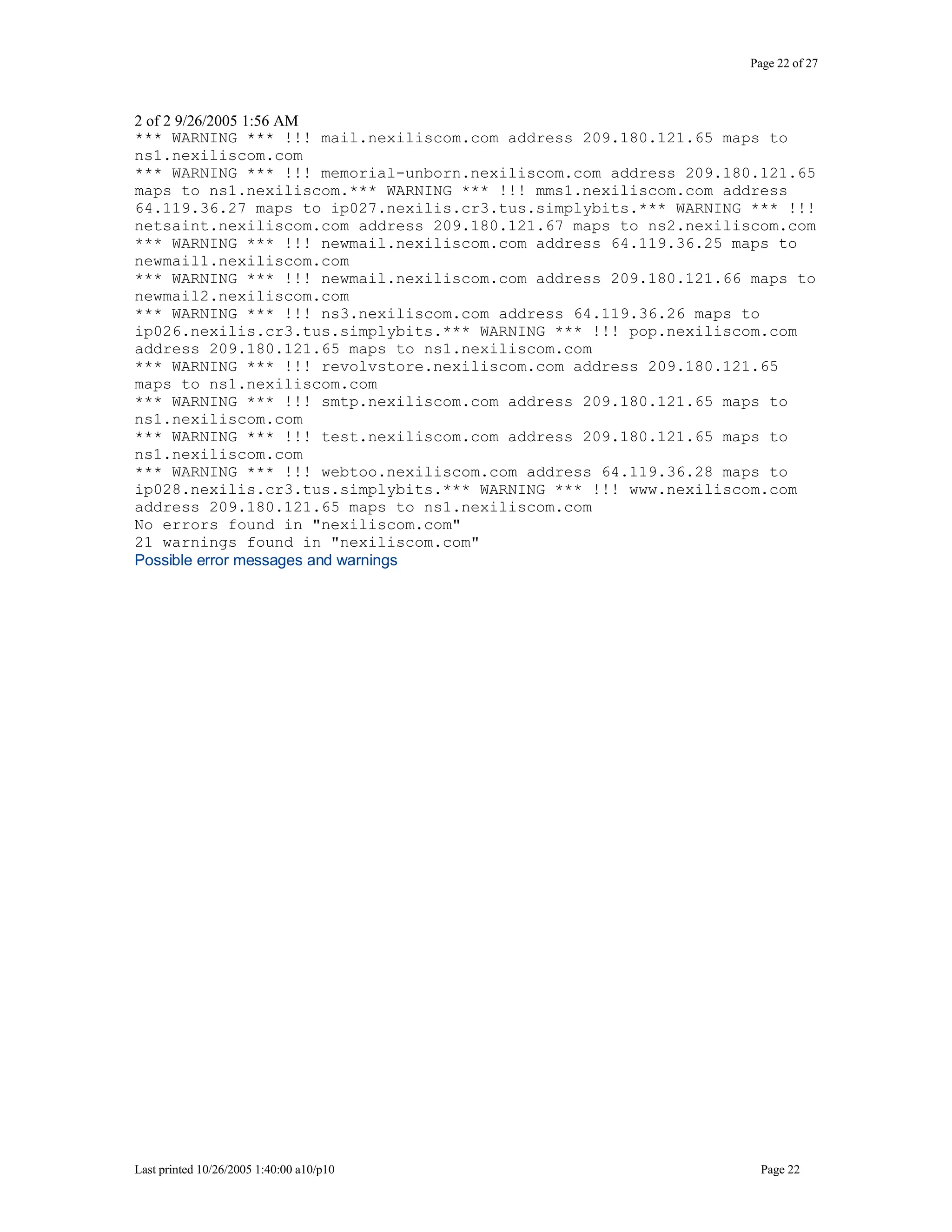
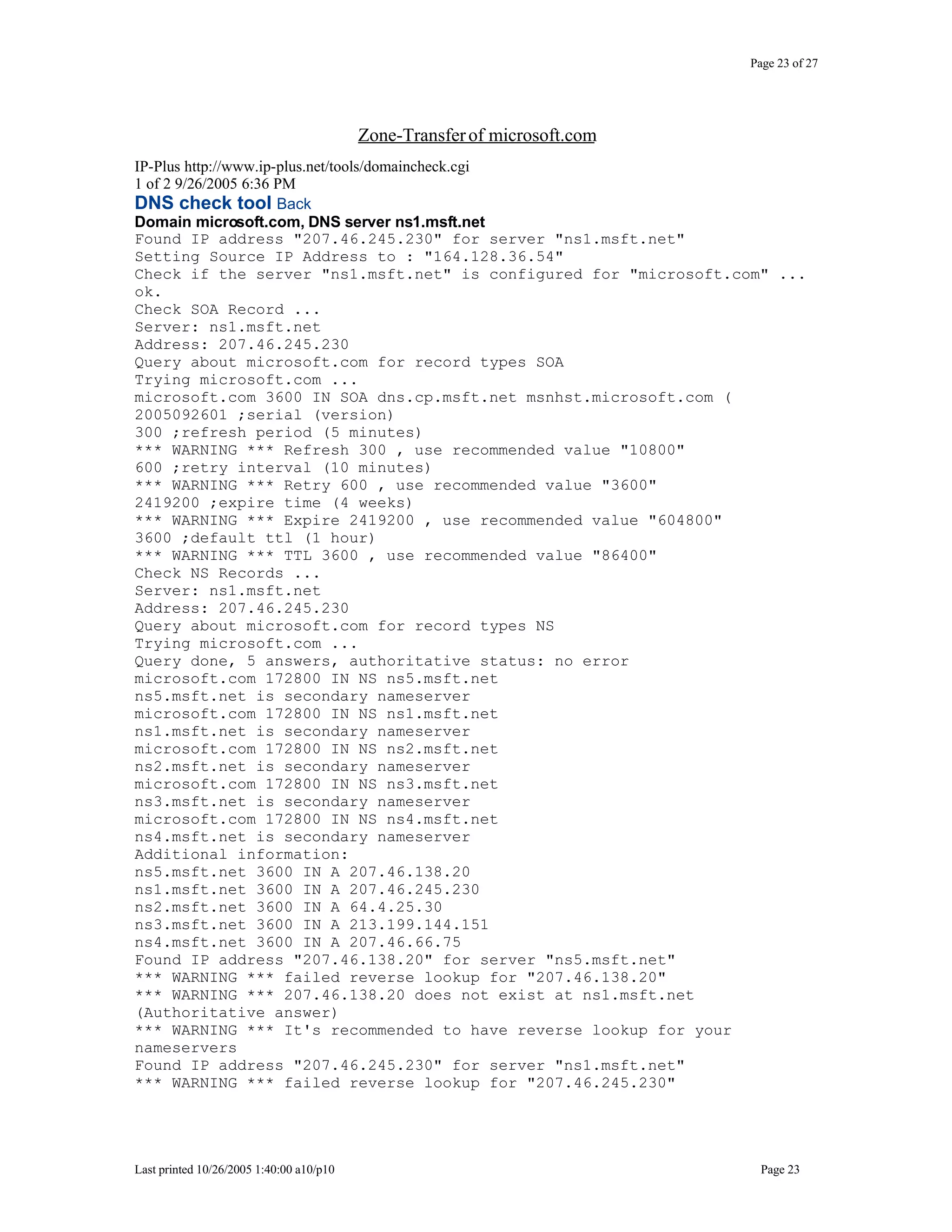
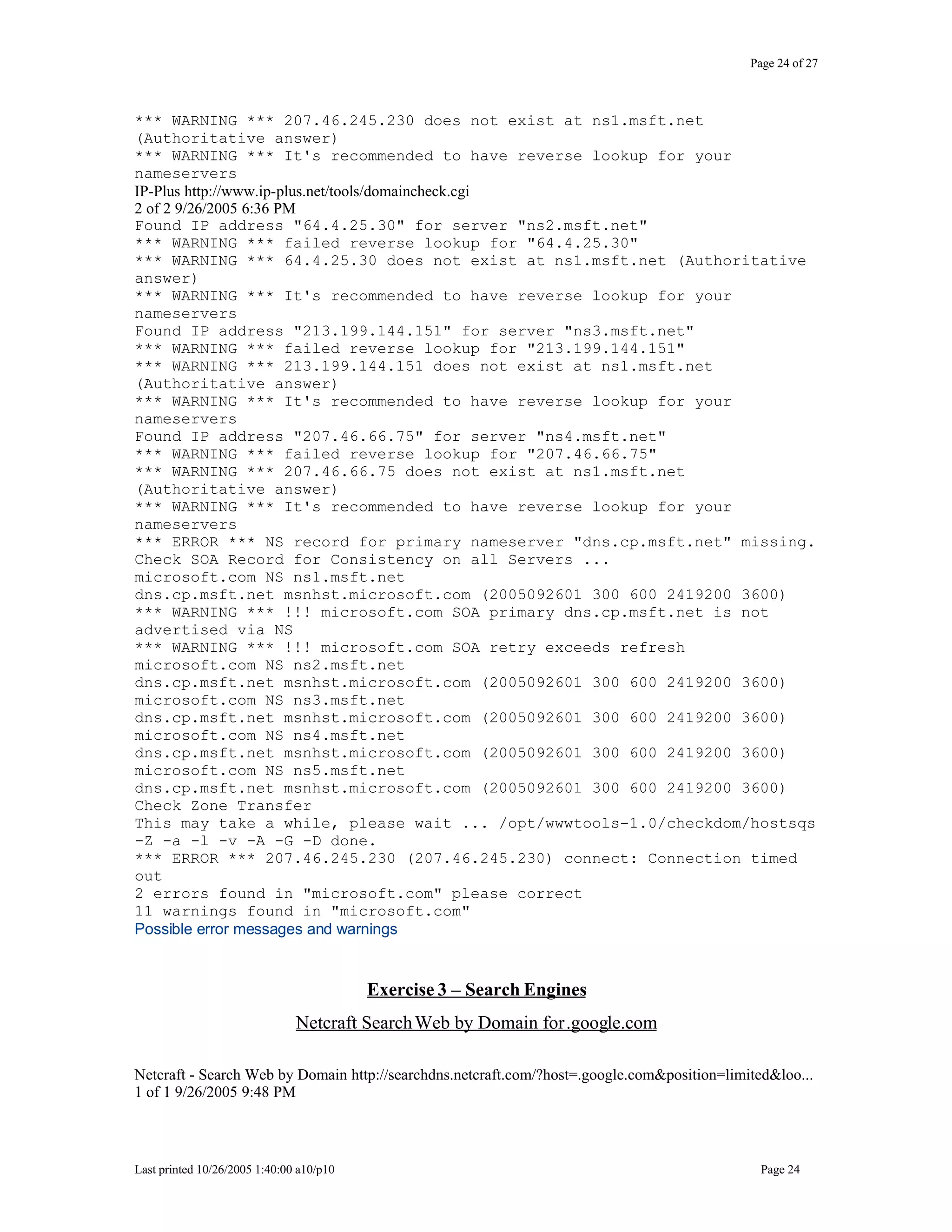
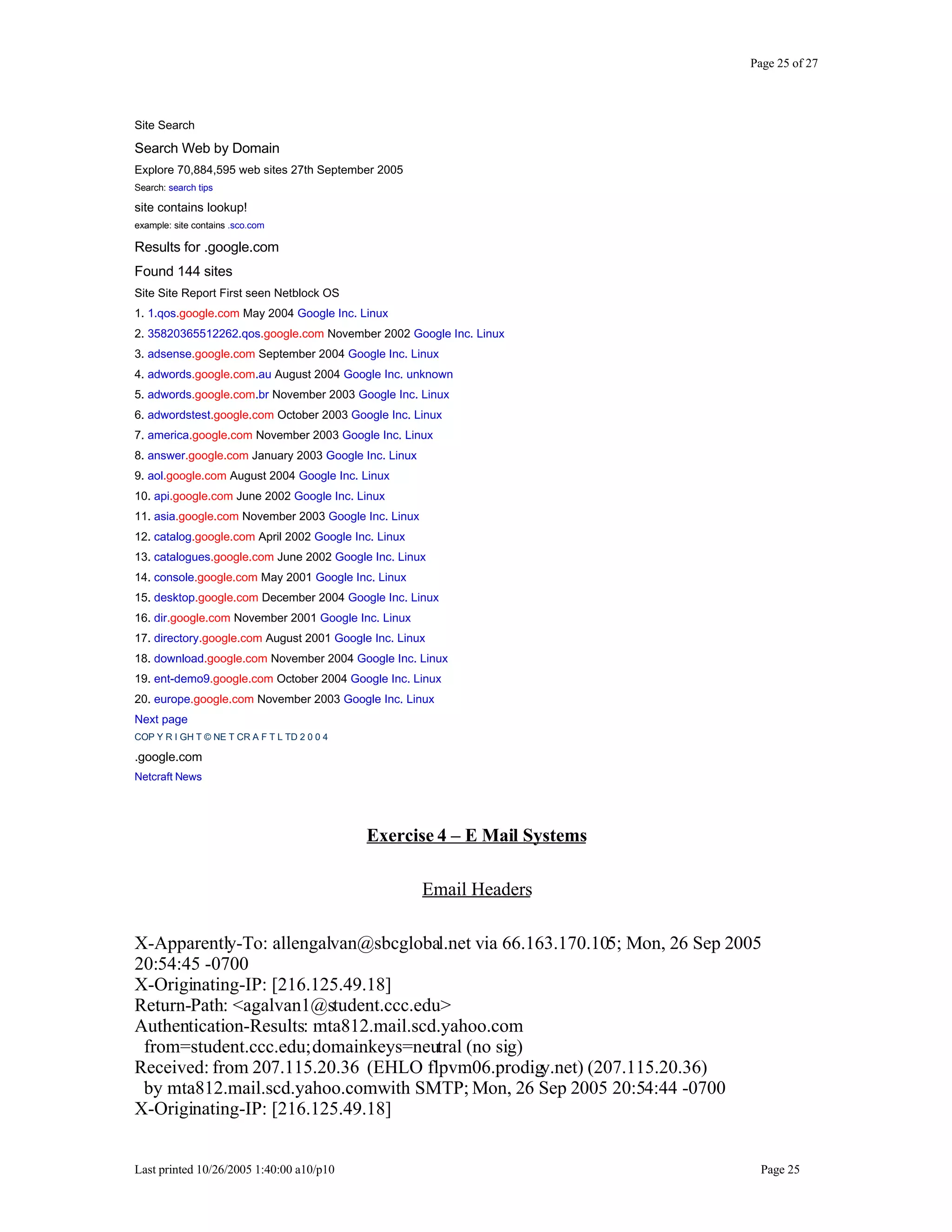

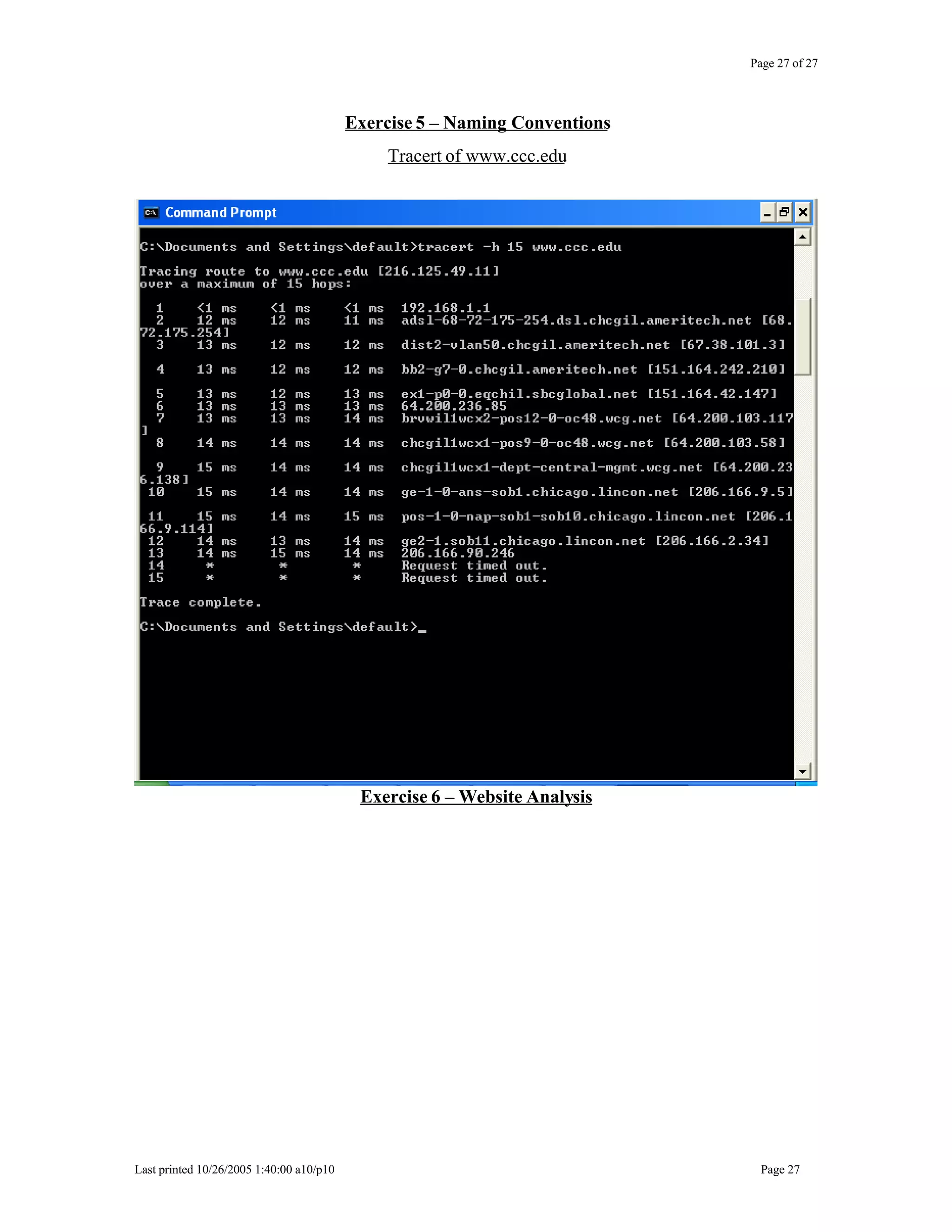
This document outlines exercises for reconnaissance and passive information gathering related to network security. It details steps to gather information from internet service registration records, domain name system queries, search engines, email systems, naming conventions, and website analysis. The exercises uncover potential vulnerabilities from information leakage that could enable social engineering attacks, technical attacks, or serve as initial stages for denial of service attacks. Countermeasures are also discussed to limit what information is exposed publicly.


























