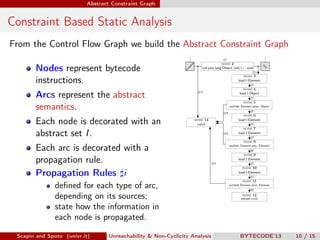
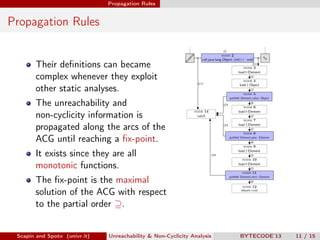
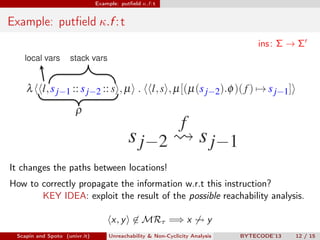
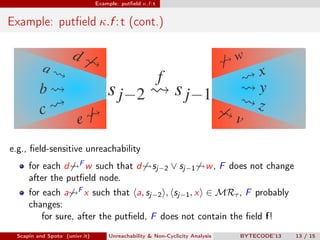
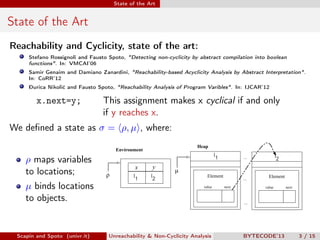
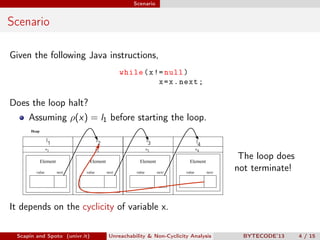
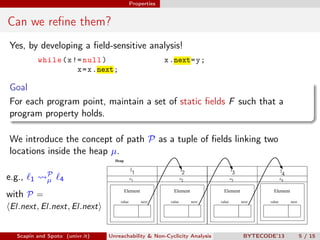
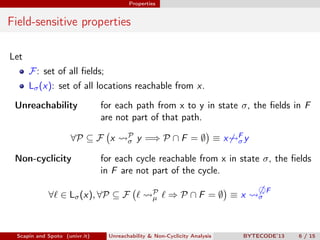
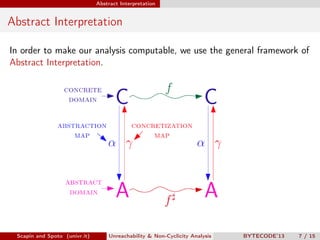
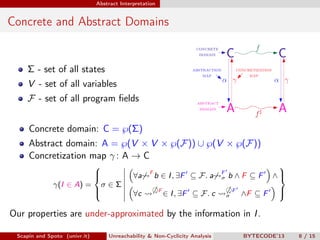
Scapin and Spoto propose a field-sensitive unreachability and non-cyclicity analysis to refine static analysis properties. They define states as mappings from variables to locations and locations to objects. A path links locations via fields in the heap. The analysis maintains properties holding for each program point by tracking a set of static fields. This allows determining if loops terminate by analyzing the cyclicity of variables.



![Methodology
Methodology
1 Program Under Analysis
class Element {
private Object value ;
private Element prec , next ;
public Element ( Object value ){
this . value = value ;
}
public Element ( Object value , Element prec ){
this . value = value ;
this . prec = prec ;
prec . next = this ;
}
}
public class MWexample {
public static void main ( String [] args ){
Element top = new Element ( new Integer (0));
for ( int i =1; i <=3; i ++)
top = new Element ( new Integer ( i ) , top );
}
}
Scapin and Spoto (univr.it) Unreachability & Non-Cyclicity Analysis BYTECODE’13 9 / 15](https://image.slidesharecdn.com/scapinbytecode13-130326155005-phpapp01/85/Bytecode-13-presentation-14-320.jpg)
![Methodology
Methodology
2 Java Bytecode
invokespecial #1 < Object / < init >() V >
aload_0
1 Program Under Analysis aload_1
putfield #2 Element . value : Object
aload_0
class Element {
aload_2
private Object value ;
putfield #3 Element . prec : Element
private Element prec , next ;
aload_2
aload_0
public Element ( Object value ){
putfield #4 Element . next : Element
this . value = value ;
return
}
public Element(Object value, Element prec){
this.value=value;
this.prec=prec;
prec.next=this;
}
}
public class MWexample {
public static void main ( String [] args ){
Element top = new Element ( new Integer (0));
for ( int i =1; i <=3; i ++)
top = new Element ( new Integer ( i ) , top );
}
}
Scapin and Spoto (univr.it) Unreachability & Non-Cyclicity Analysis BYTECODE’13 9 / 15](https://image.slidesharecdn.com/scapinbytecode13-130326155005-phpapp01/85/Bytecode-13-presentation-15-320.jpg)
![Methodology
Methodology
2 Java Bytecode
invokespecial #1 < Object / < init >() V >
aload_0
1 Program Under Analysis aload_1
putfield #2 Element . value : Object
aload_0
class Element {
aload_2
private Object value ;
putfield #3 Element . prec : Element
private Element prec , next ;
aload_2
aload_0
public Element ( Object value ){
putfield #4 Element . next : Element
this . value = value ;
return
}
public Element(Object value, Element prec){
this.value=value;
this.prec=prec; 3 Control Flow Graph
prec.next=this;
call java.lang.Object. init () : void
}
}
public class MWexample { load 0 Element
load 1 Object
public static void main ( String [] args ){ putfield Element.value : Object
catch
Element top = new Element ( new Integer (0)); throw java.lang.Throwable
for ( int i =1; i <=3; i ++)
load 0 Element
top = new Element ( new Integer ( i ) , top ); load 2 Element
putfield Element.prec : Element
}
}
load 2 Element
load 0 Element
putfield Element.next : Element
return void
Scapin and Spoto (univr.it) Unreachability & Non-Cyclicity Analysis BYTECODE’13 9 / 15](https://image.slidesharecdn.com/scapinbytecode13-130326155005-phpapp01/85/Bytecode-13-presentation-16-320.jpg)