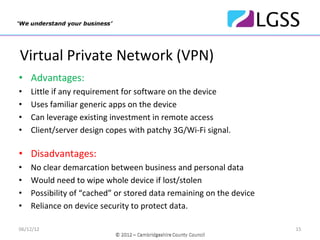
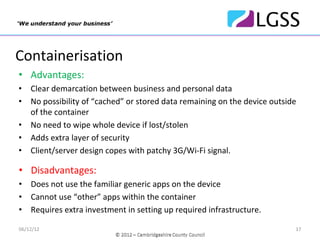
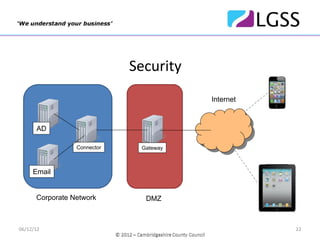
The document discusses Bring Your Own Device (BYOD) policies and a pilot program run by Cambridgeshire County Council to test BYOD solutions. It defines BYOD, examines factors driving its adoption, and outlines potential issues. The pilot tested the Dynamic Mobile Exchange software from Excitor across 50 users and found high levels of acceptance, ease of use and satisfaction. Based on the pilot's success, the Council plans to roll out the BYOD program to all suitable employees by the end of the year.