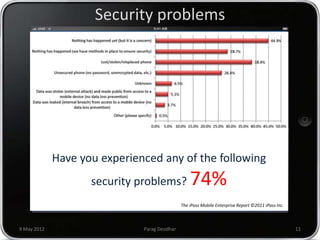
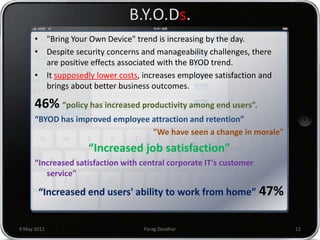
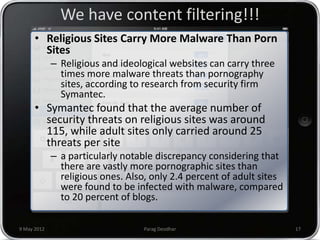
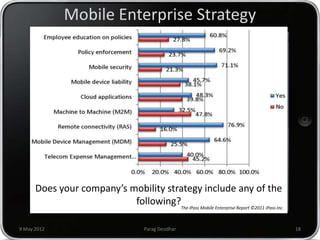
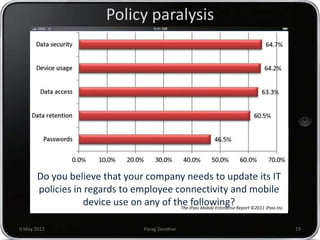
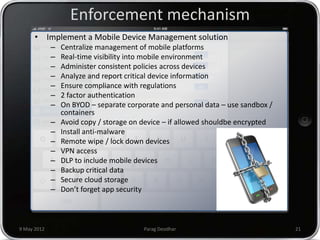
Parag Deodhar presented on securing mobile workplaces at the Enterprise Mobility Summit on May 9th, 2012 in Bengaluru. He discussed how mobility is changing how IT operates as data moves outside of corporate networks. This crossing of the "Lakshman Rekha" or corporate firewall poses security risks. He highlighted issues with bring your own device policies including difficulty securing and managing personal devices on the network. Deodhar argued that organizations need a mobile enterprise strategy including device management, updated security policies, training, and enforcement mechanisms to balance security and productivity in an increasingly mobile workplace.