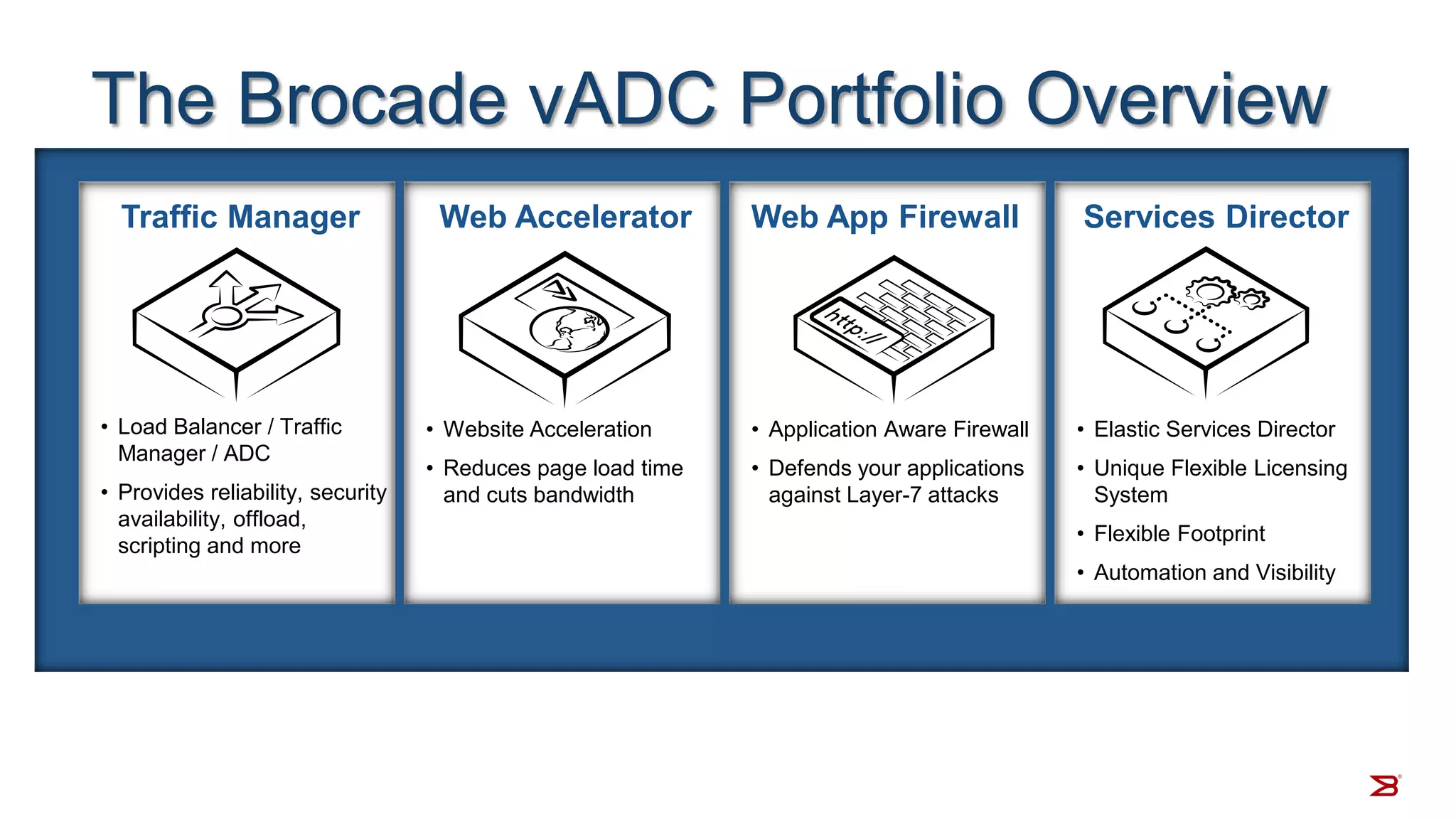
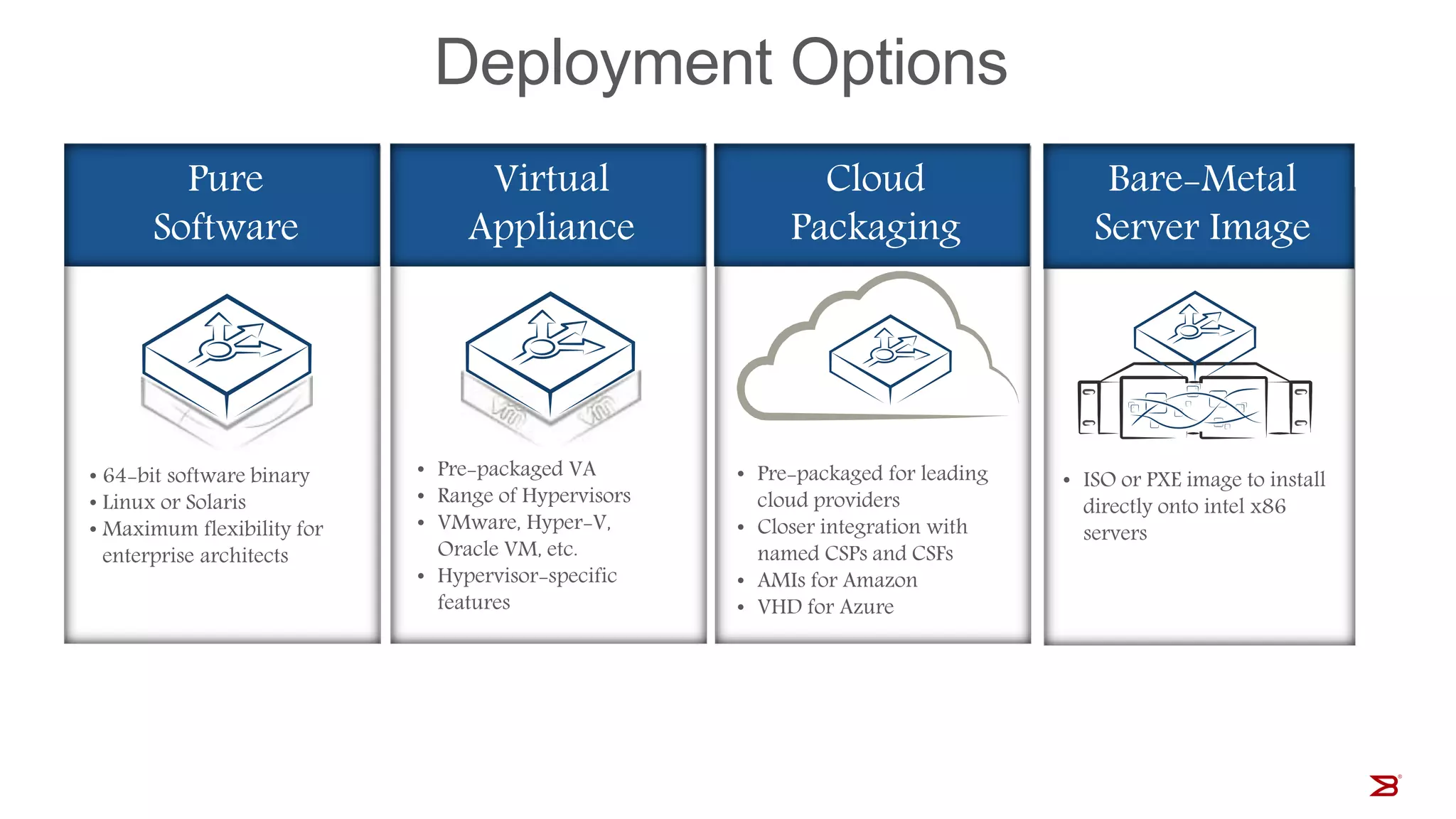
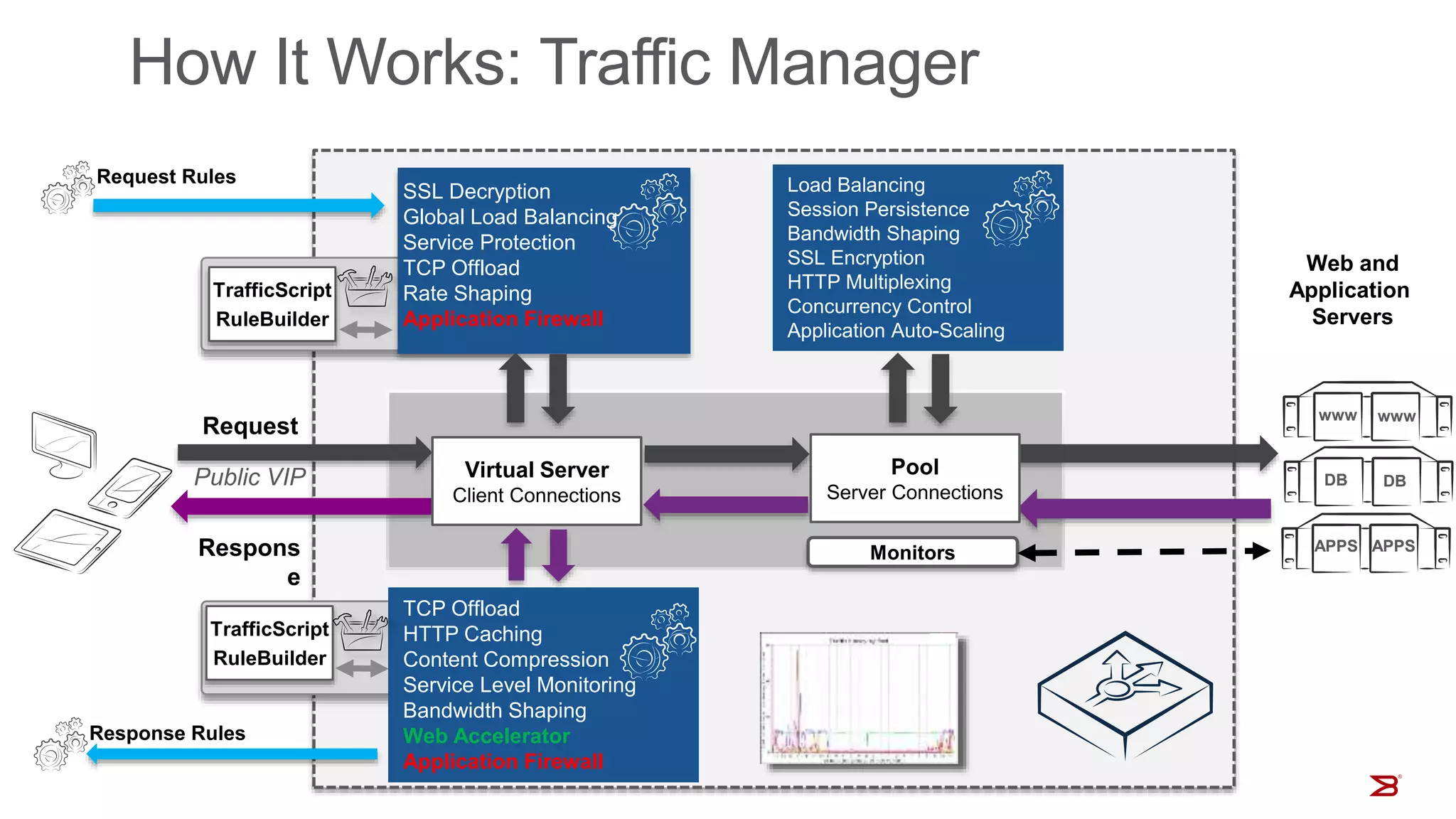
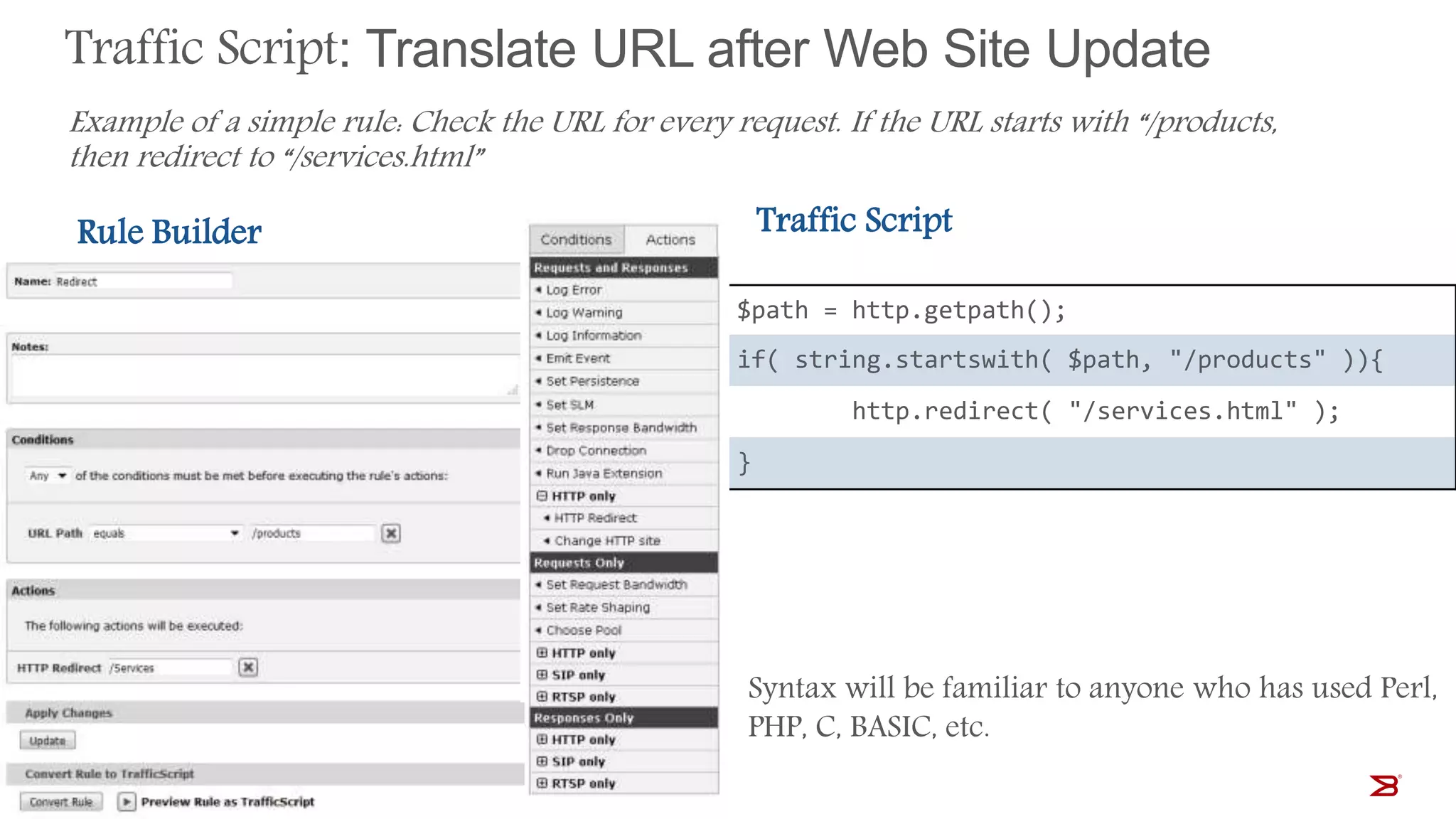
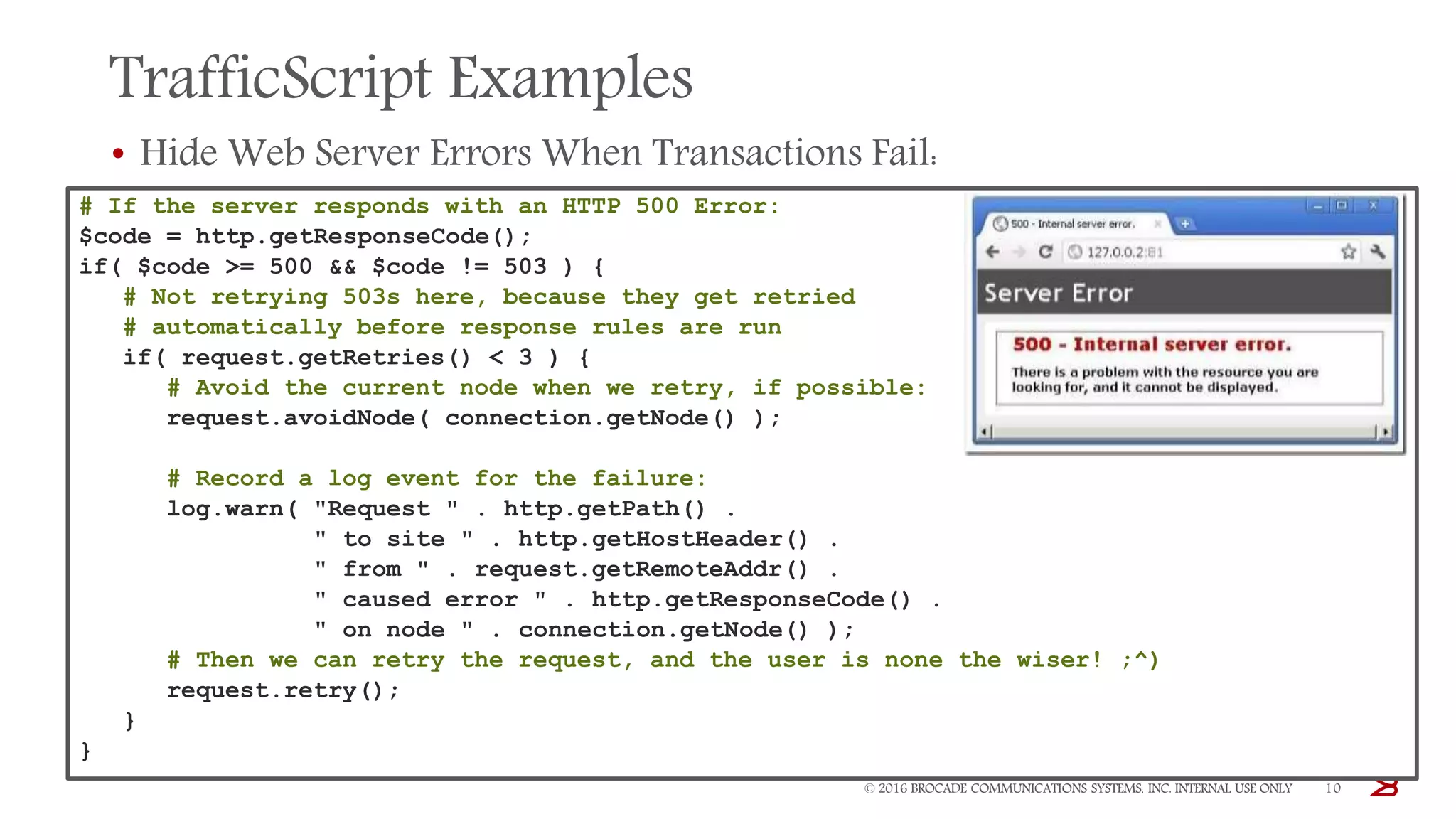
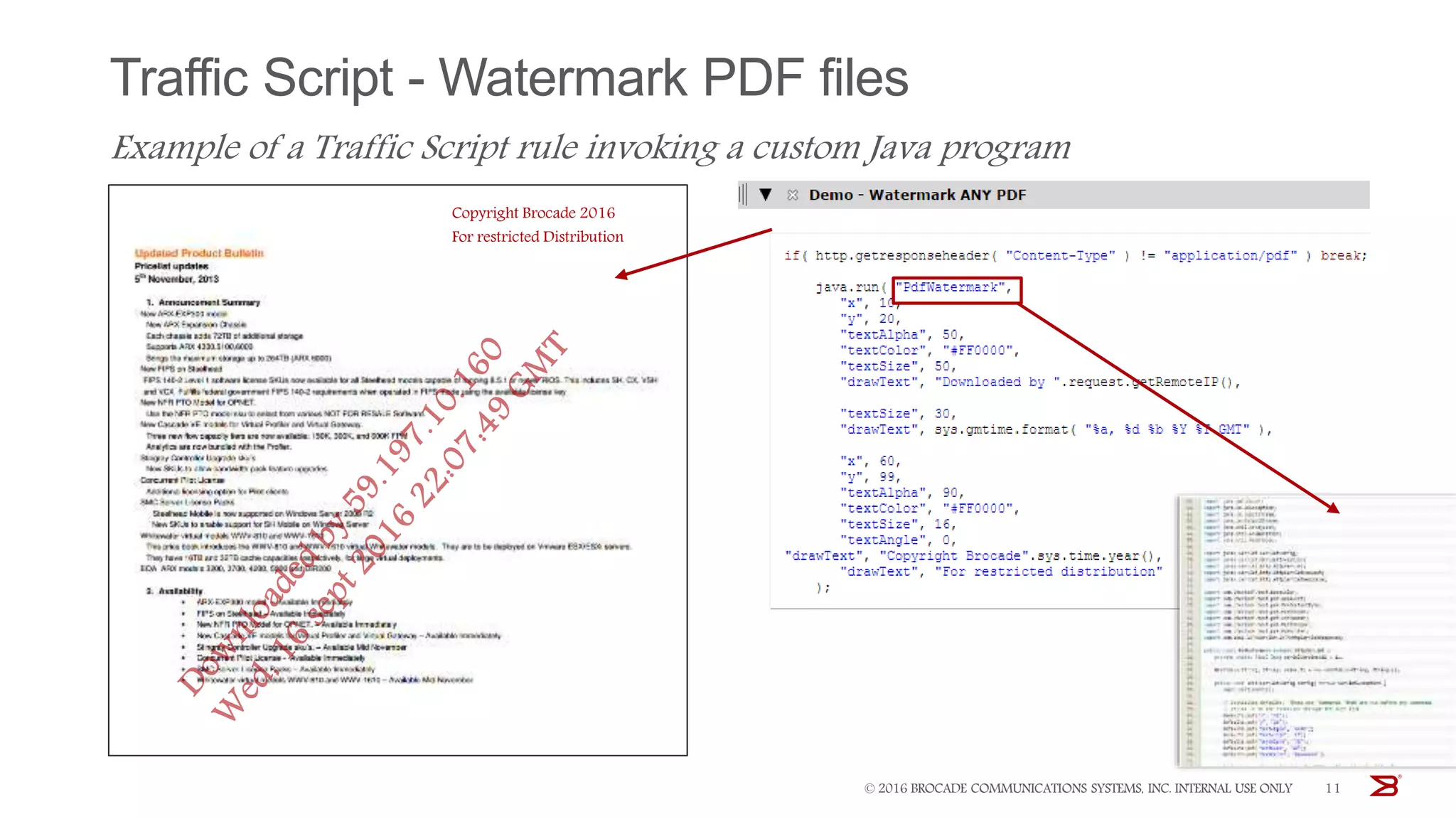
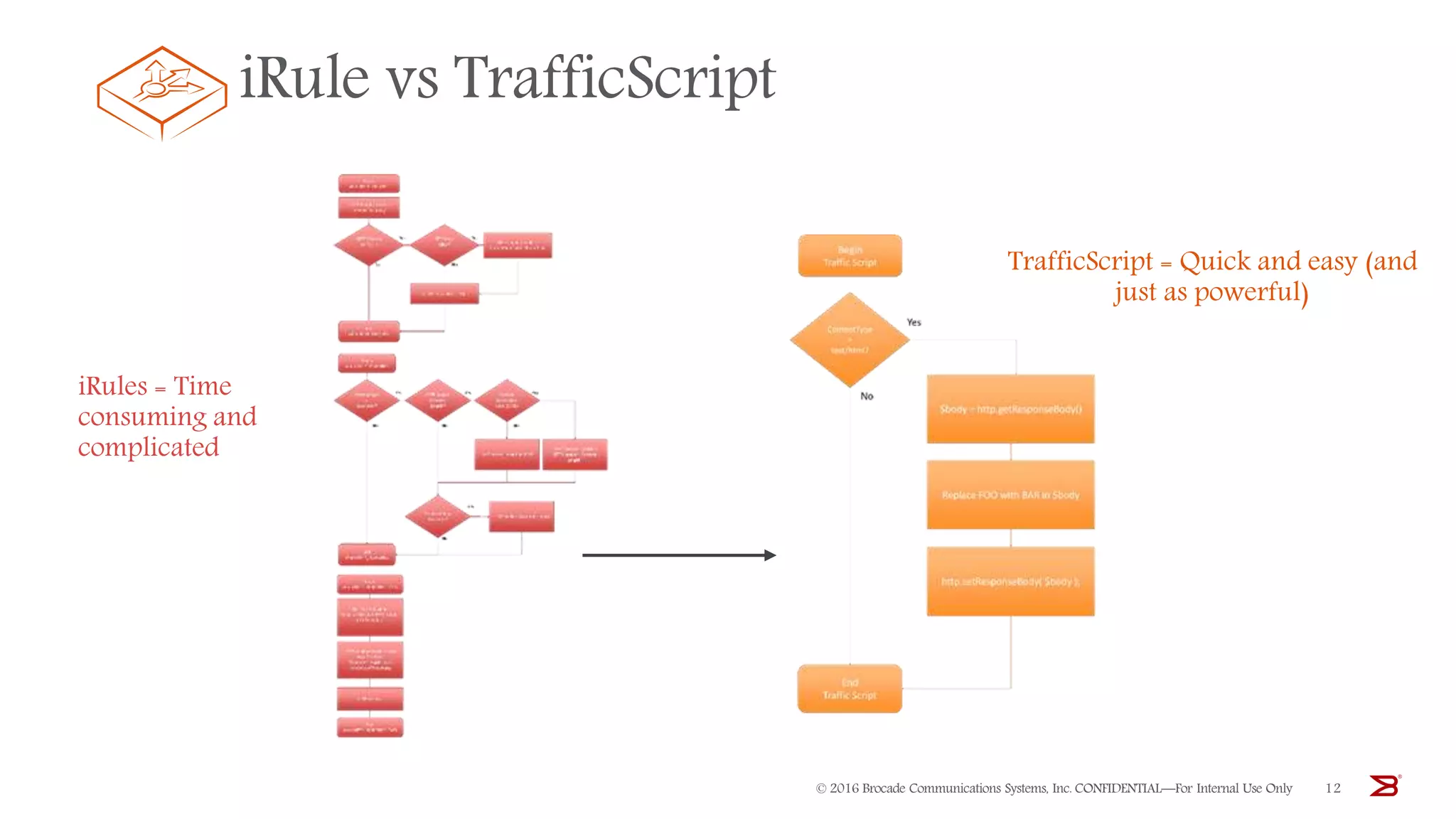
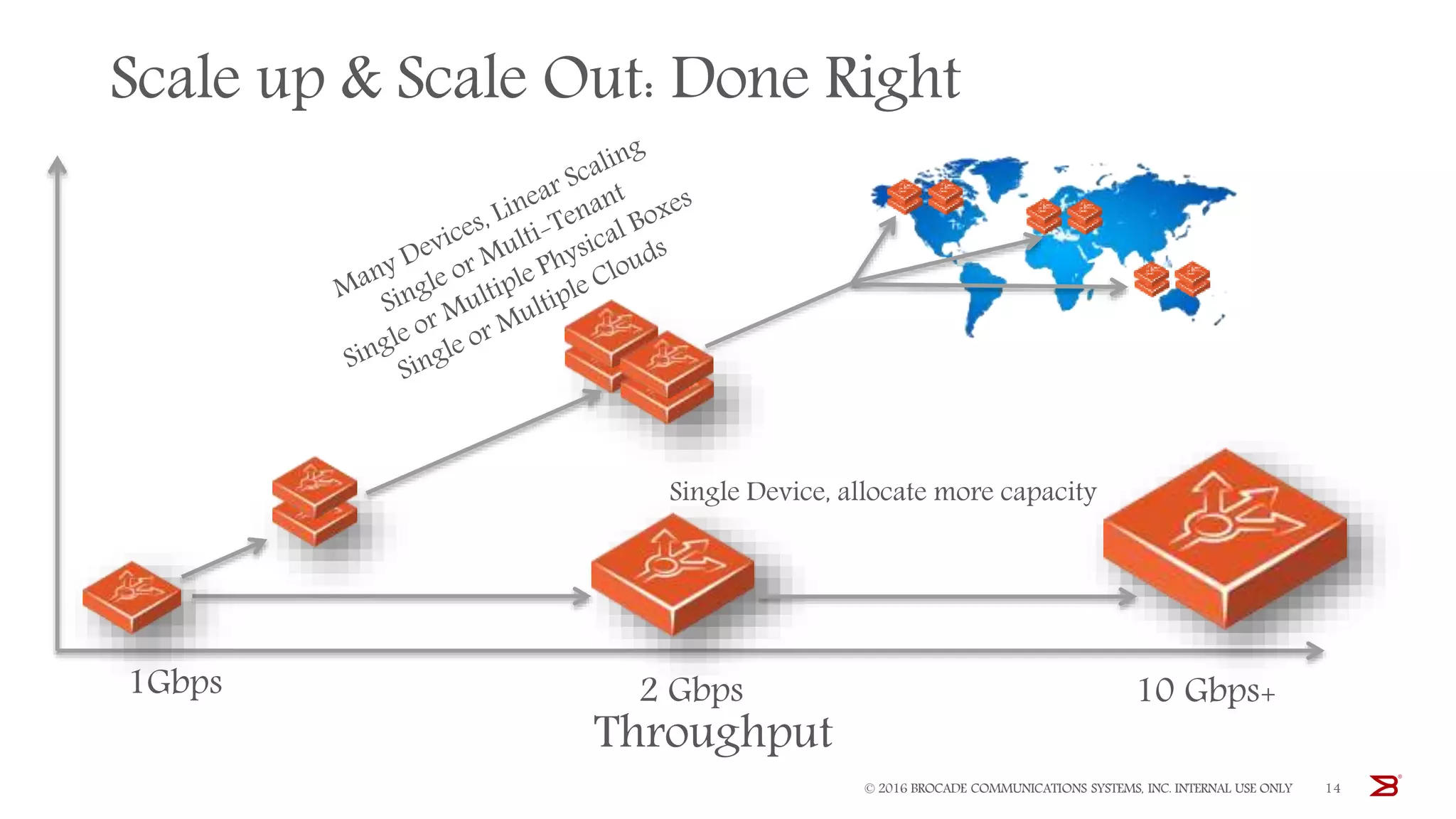
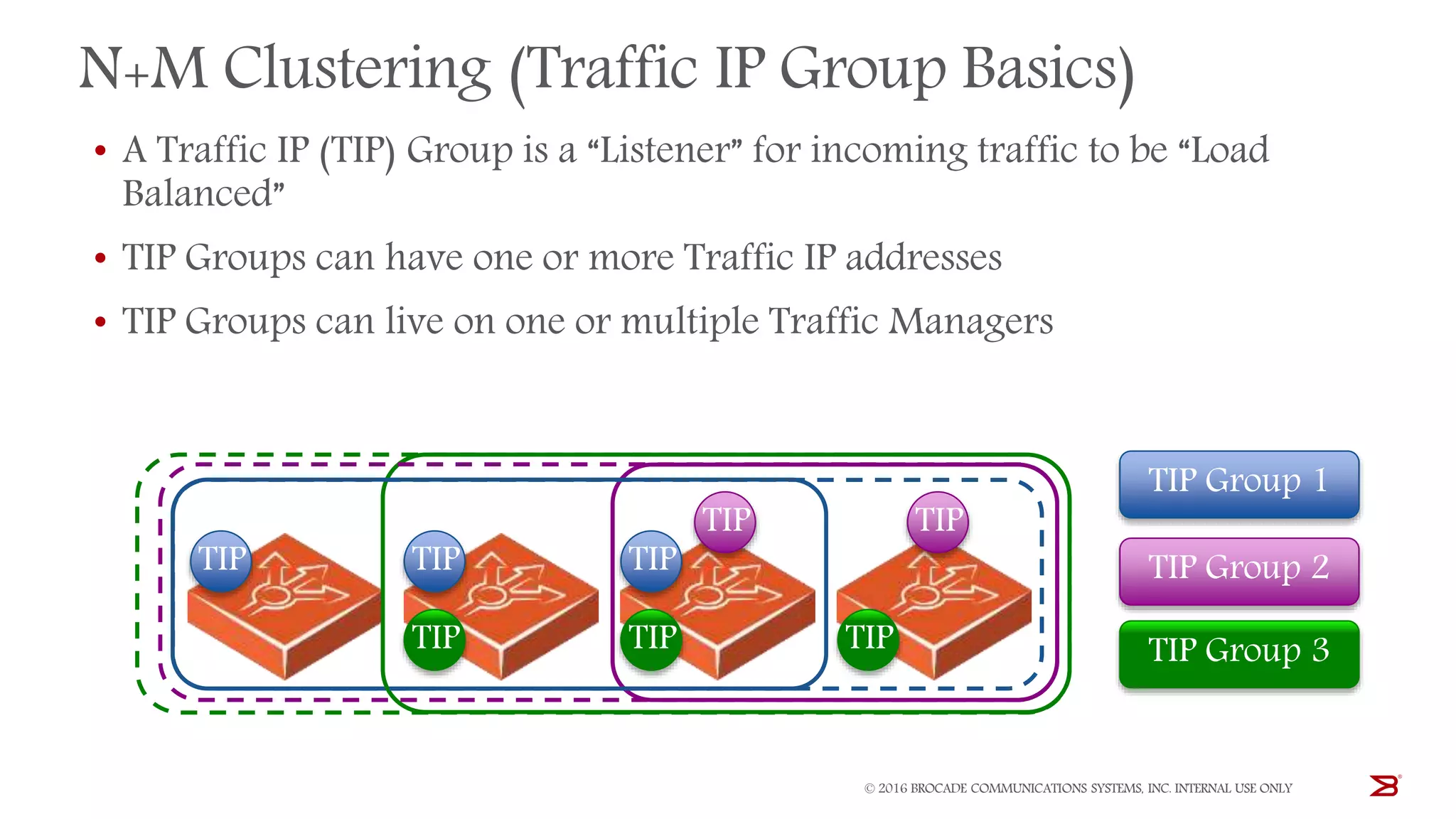
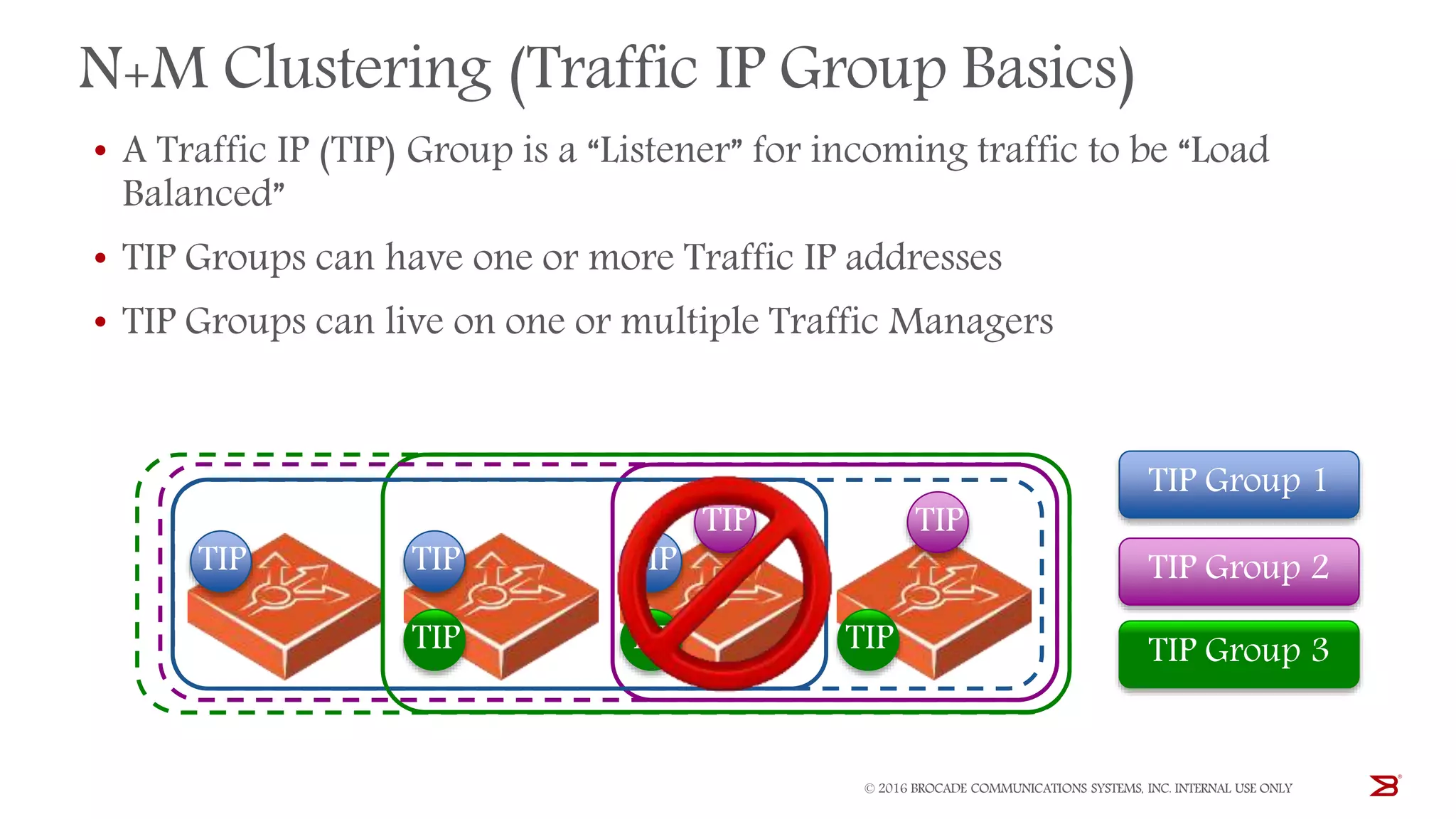
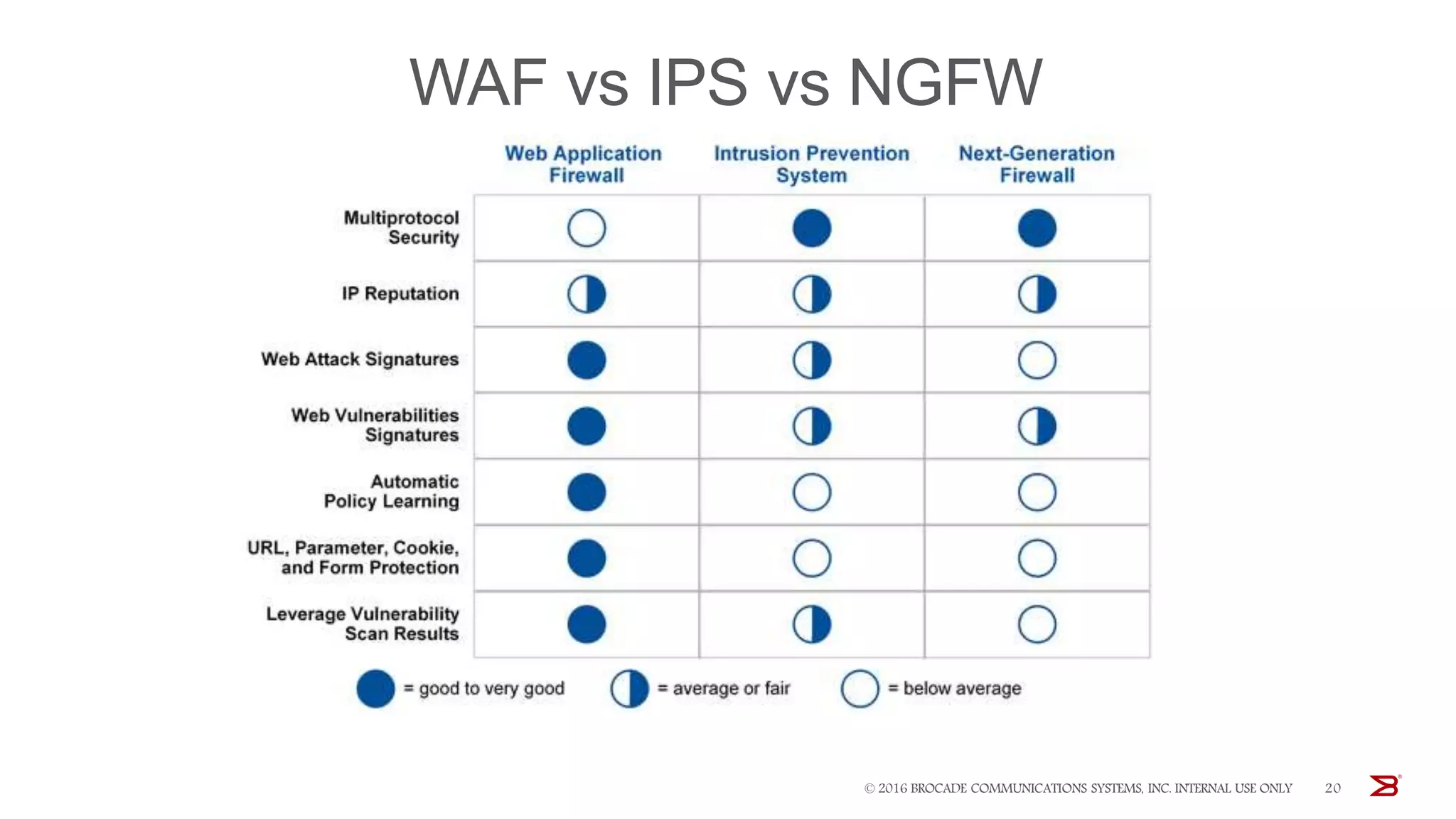
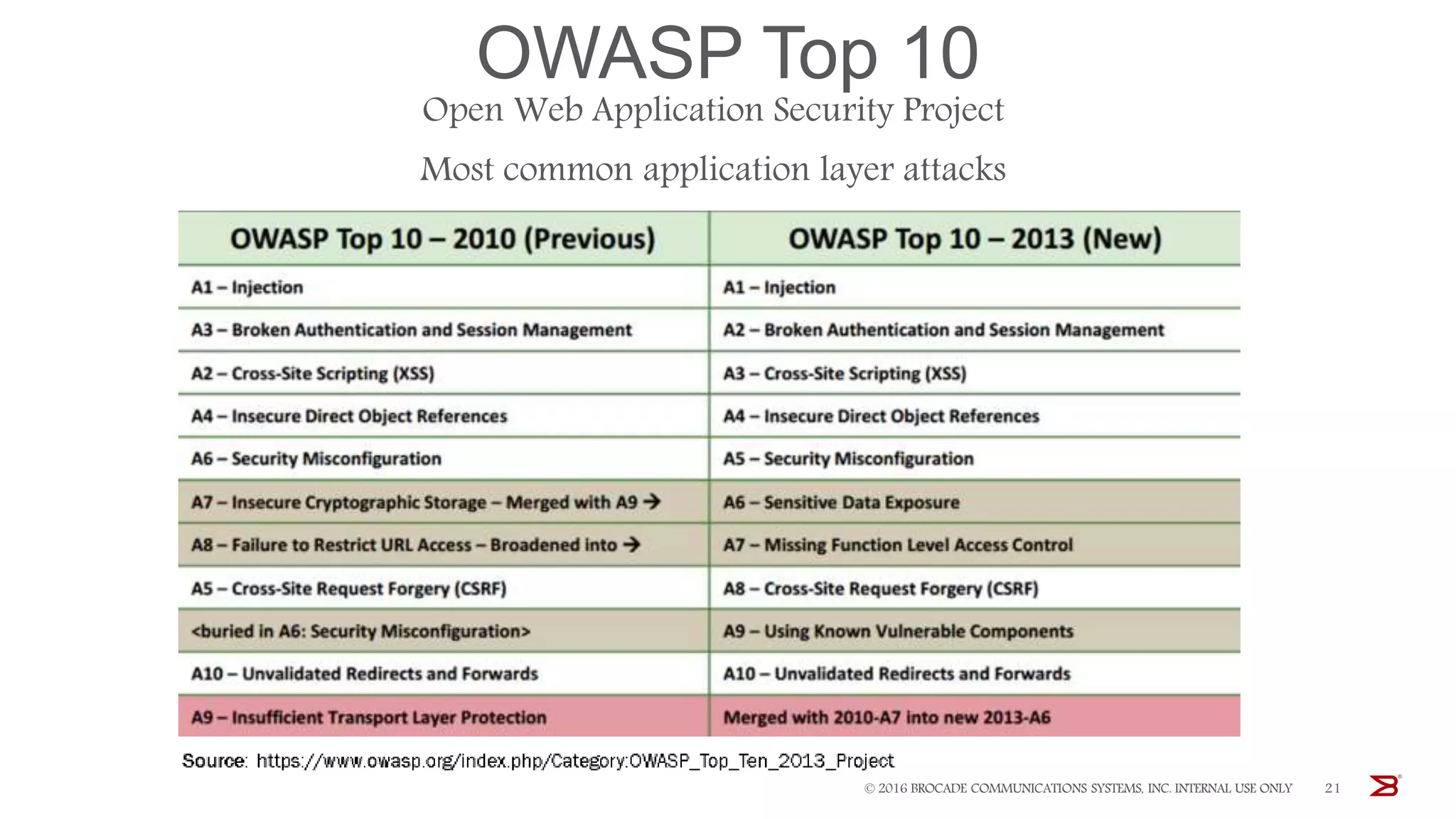
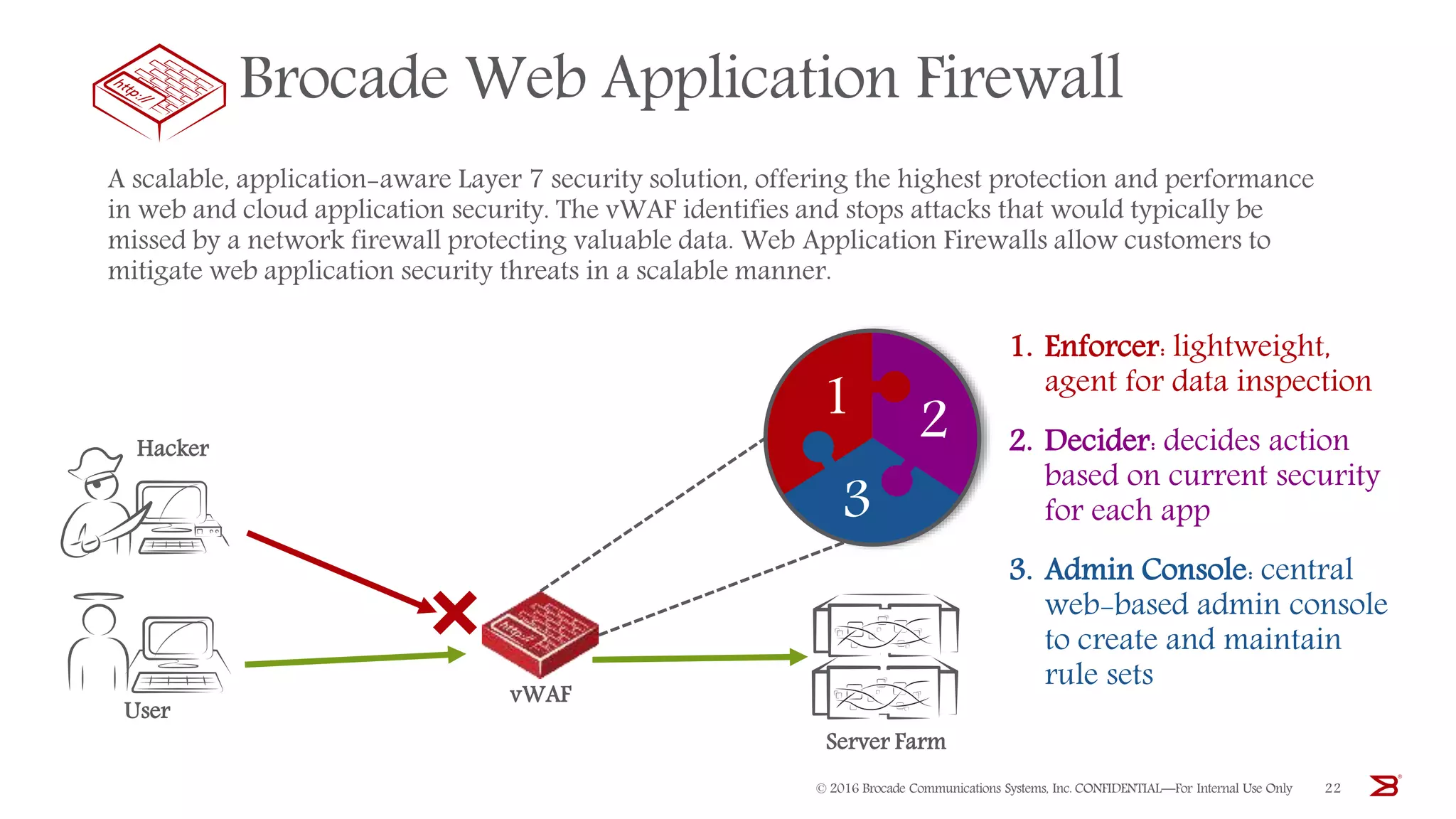
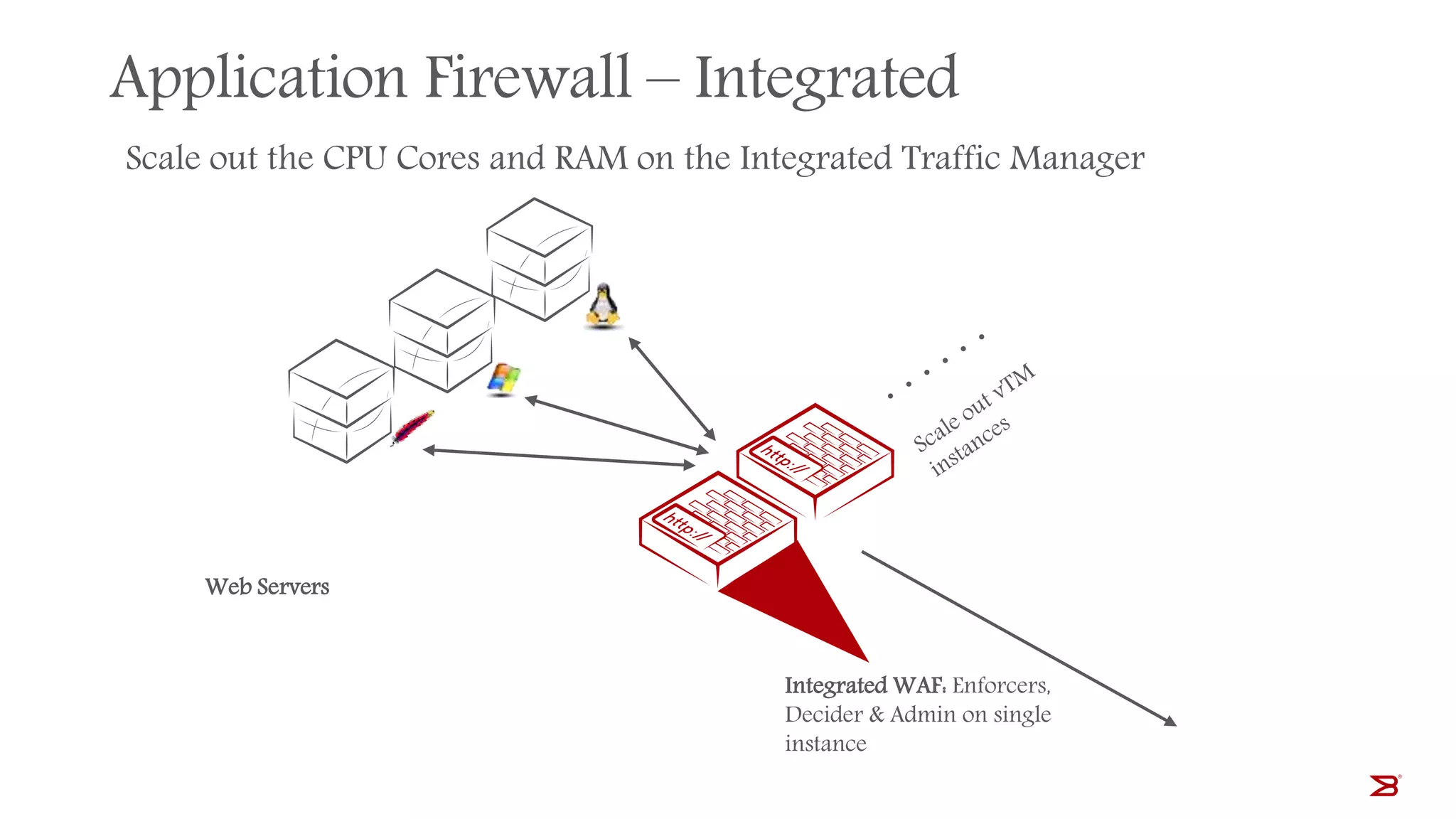
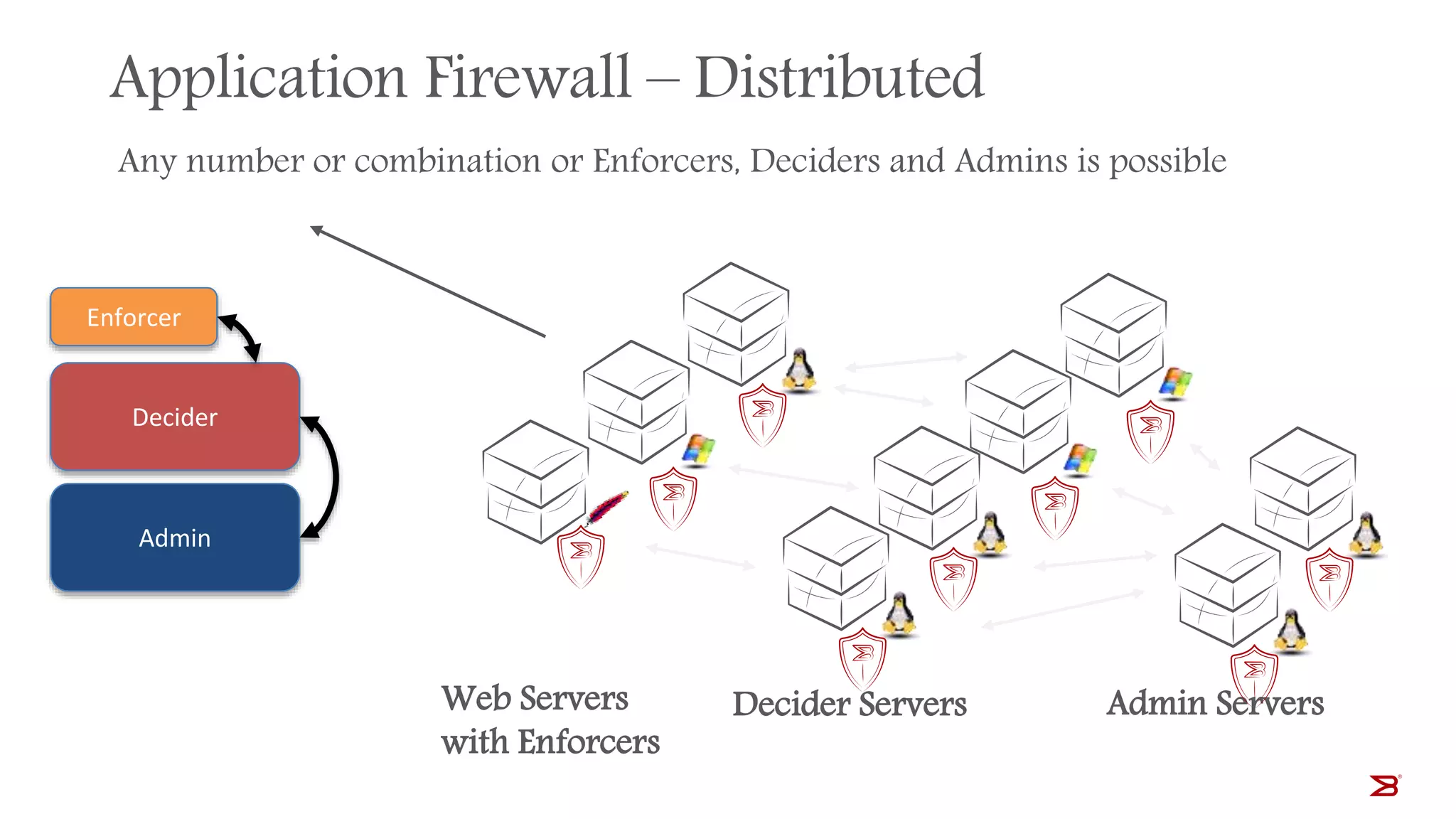
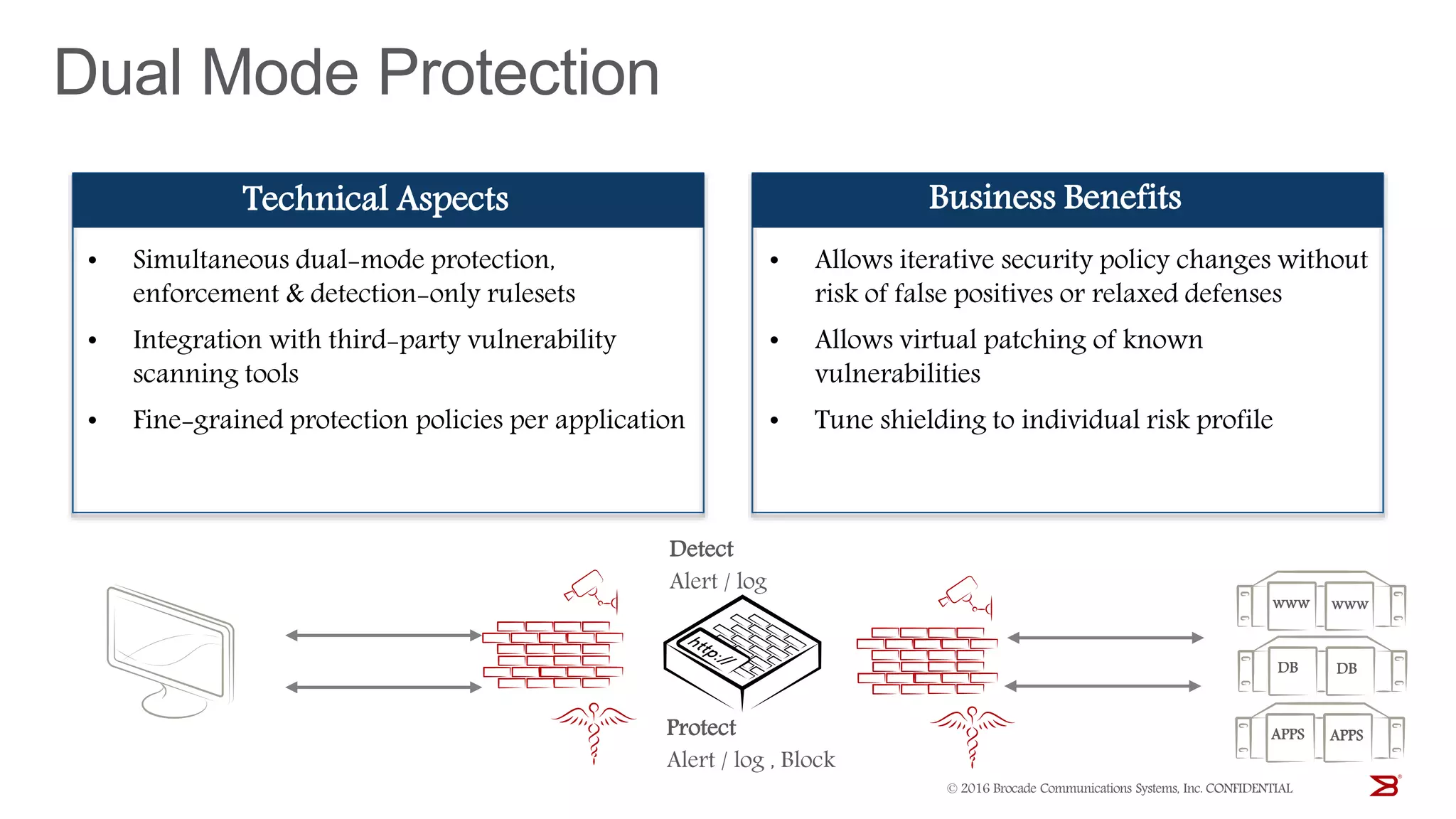
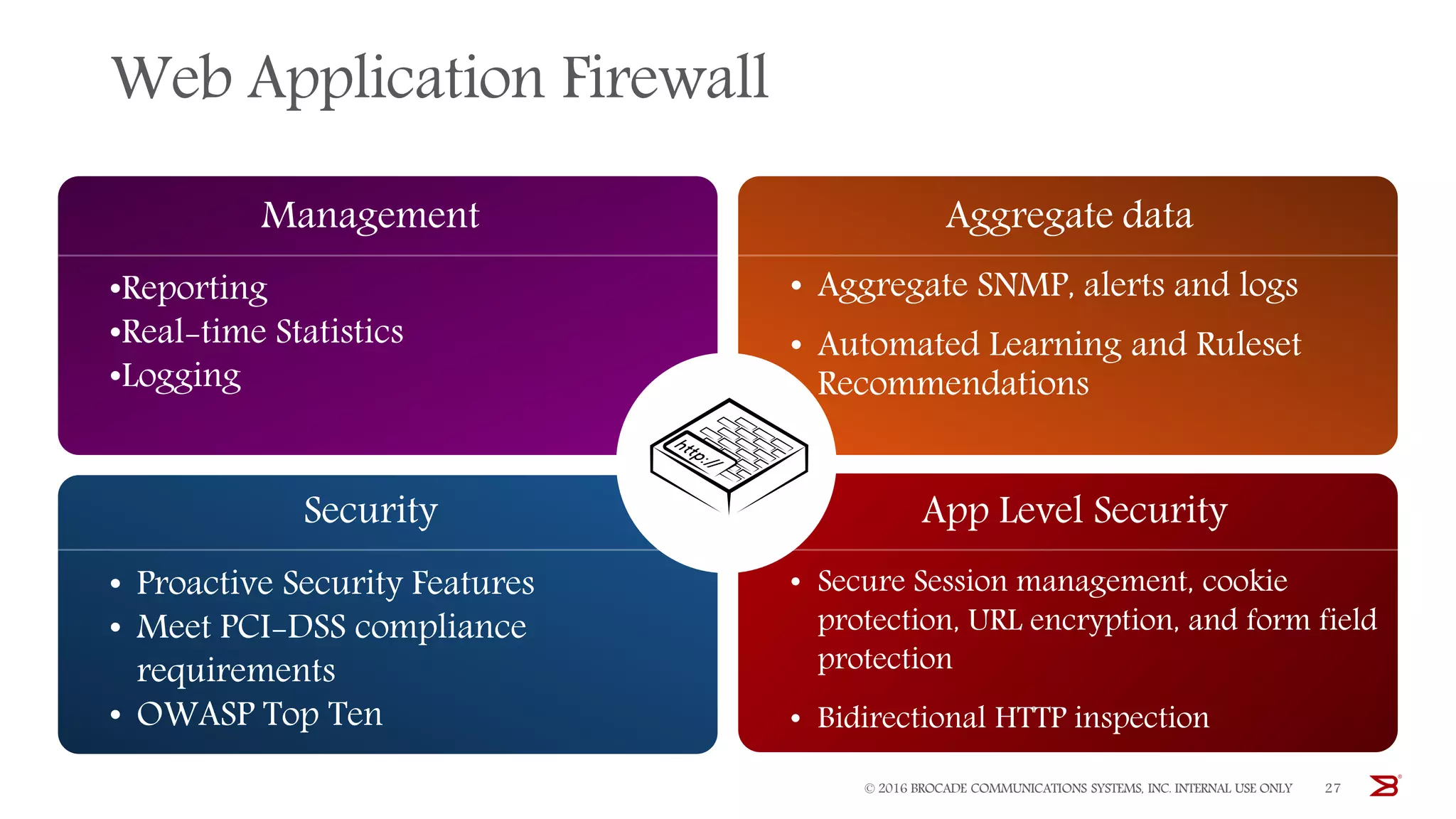
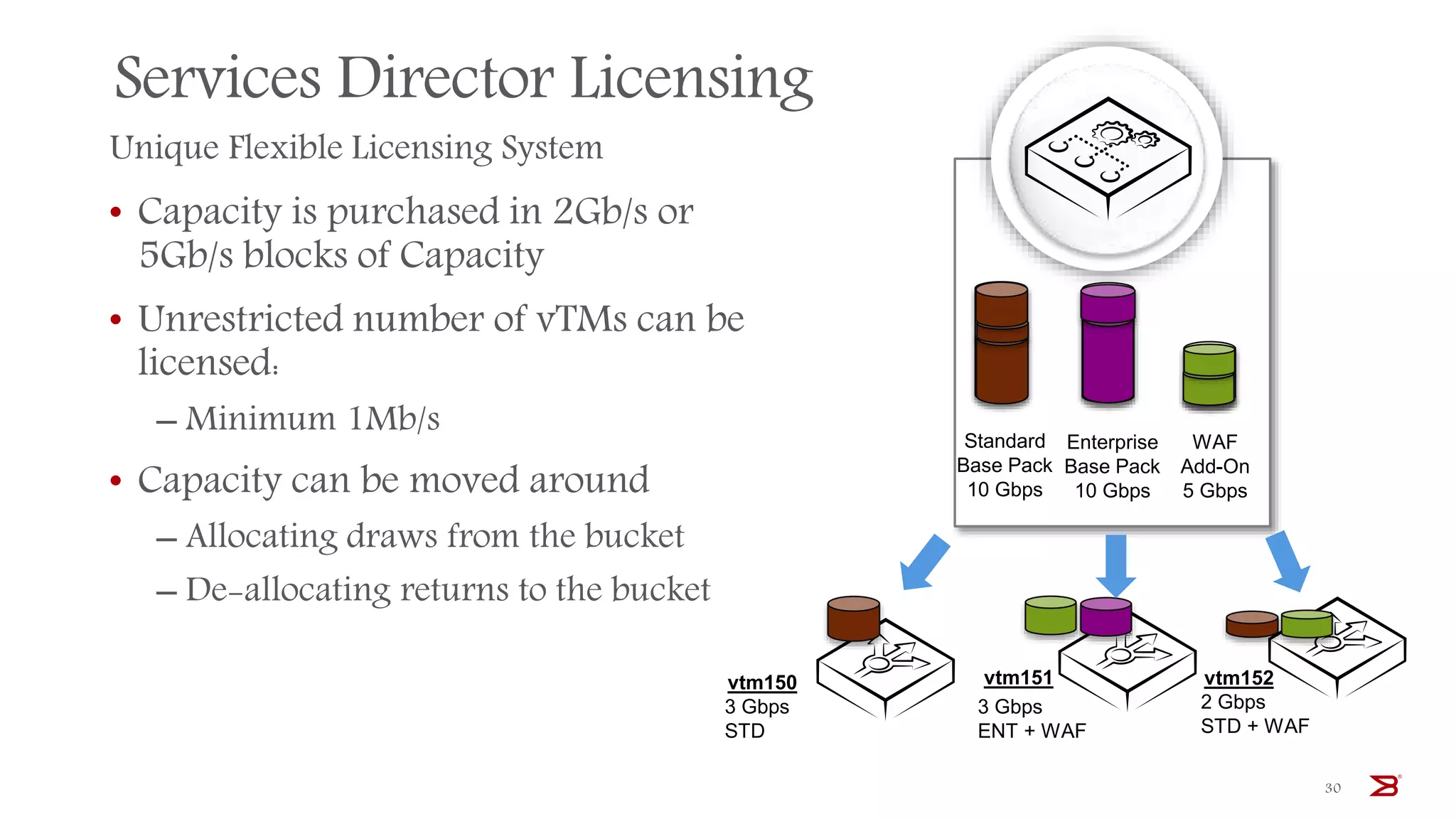
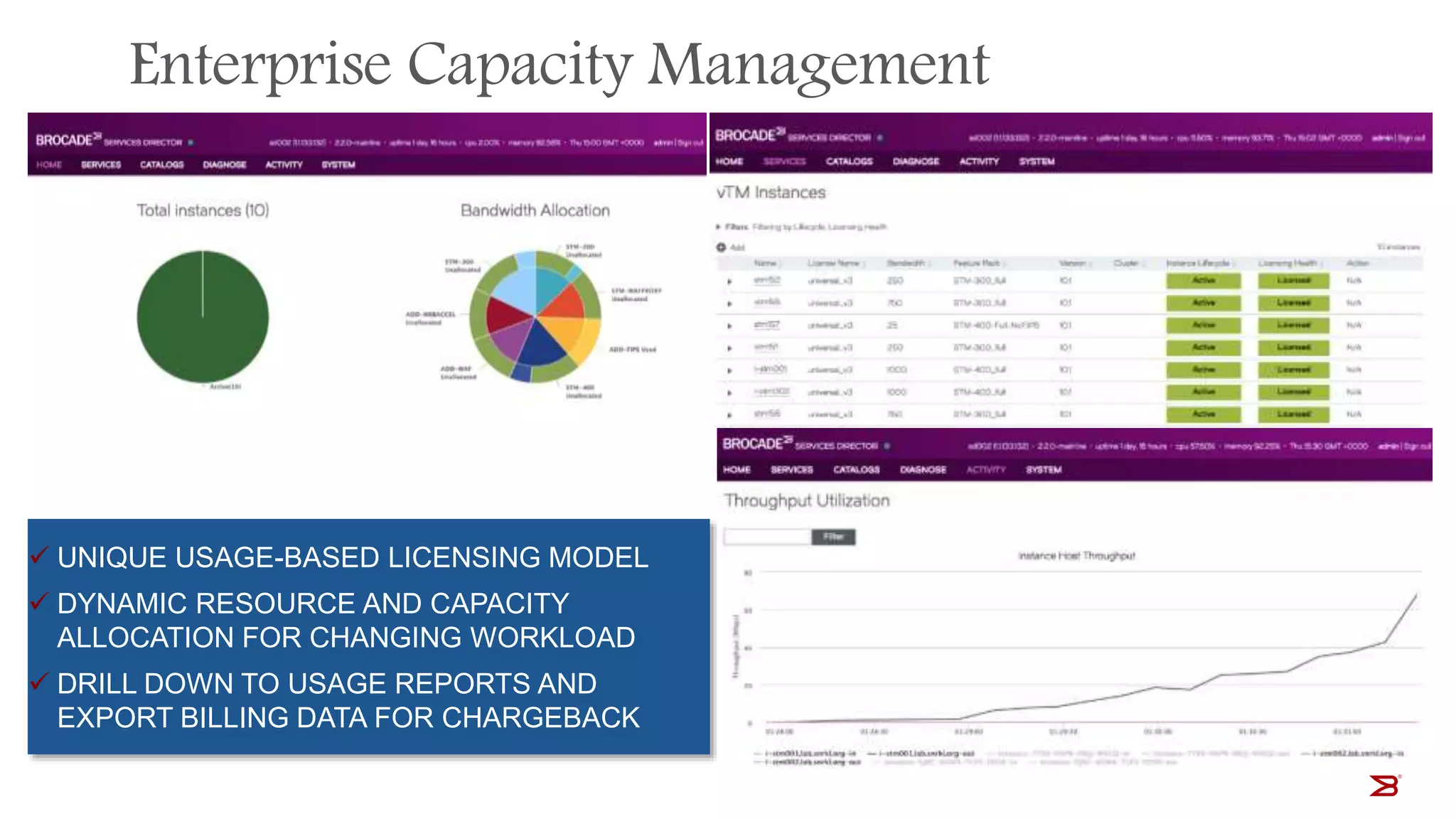
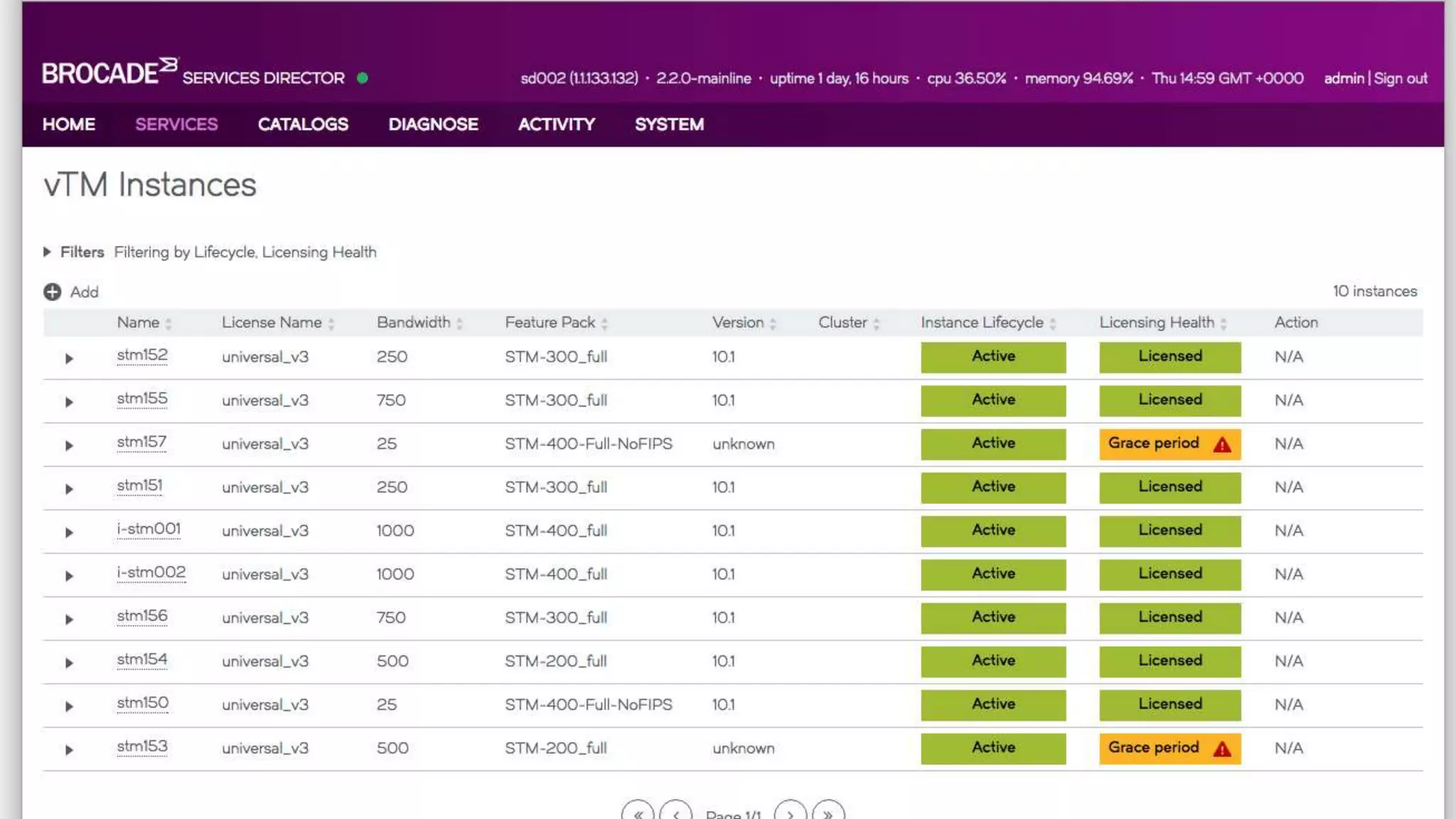
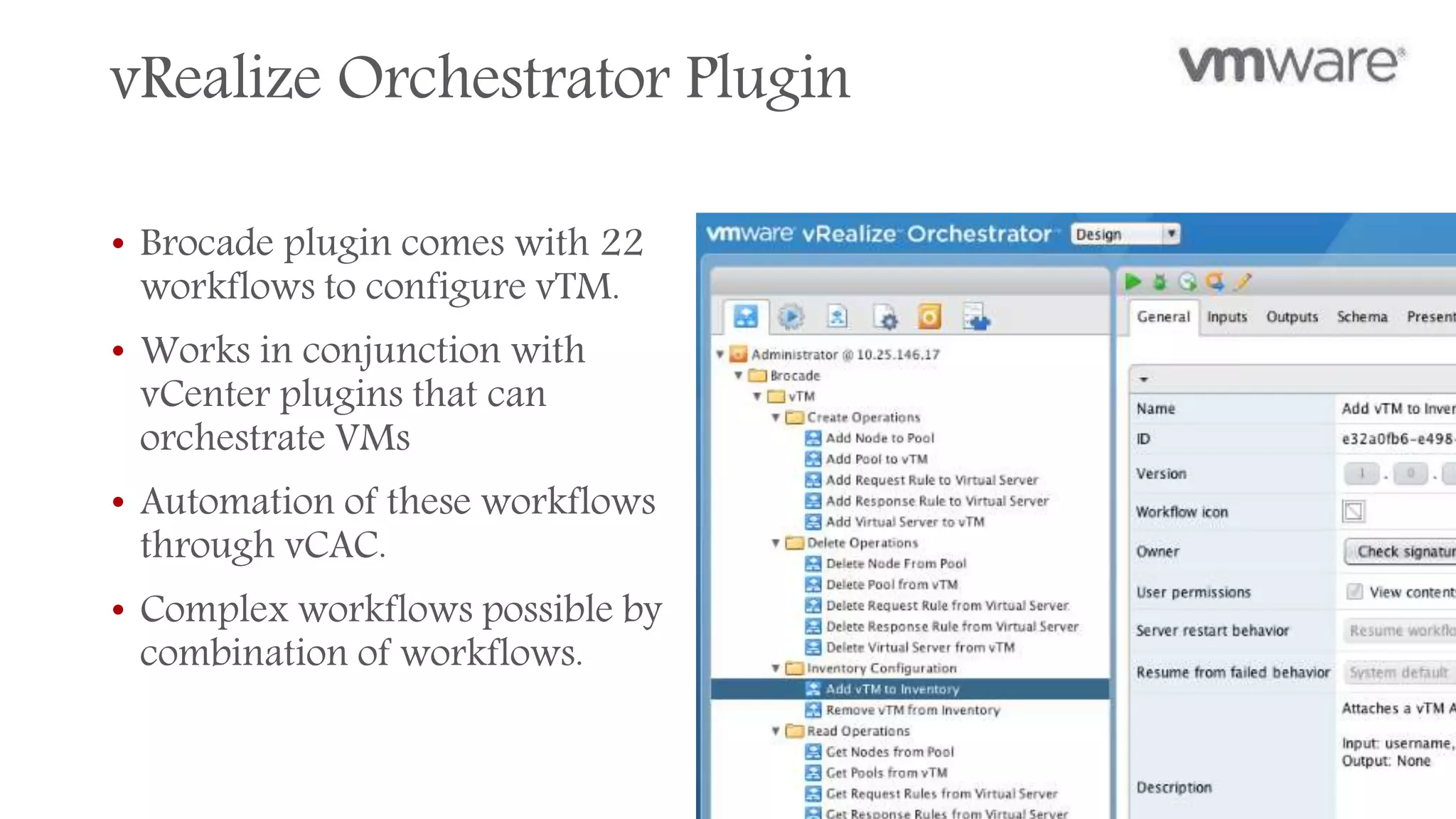
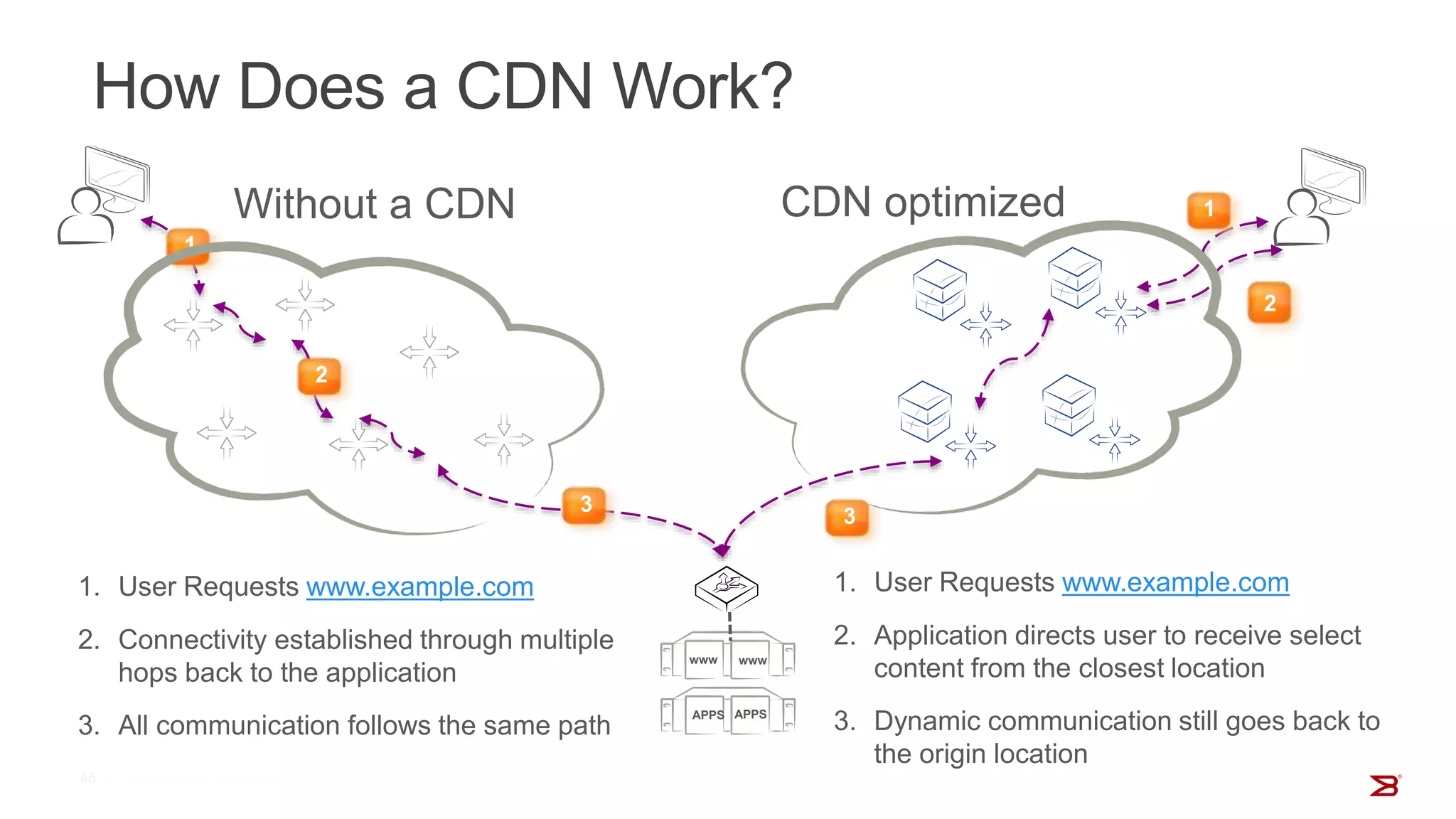
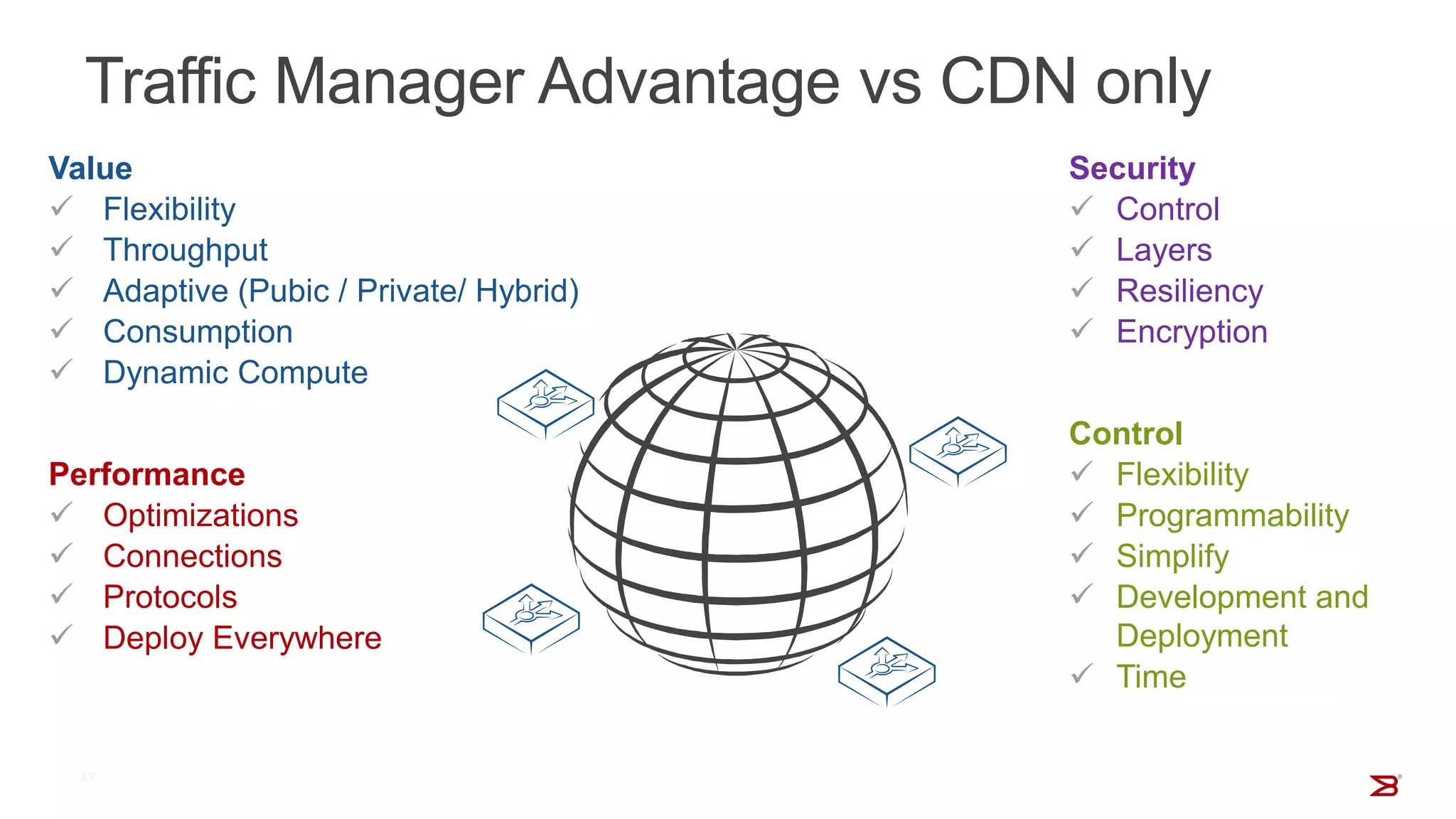
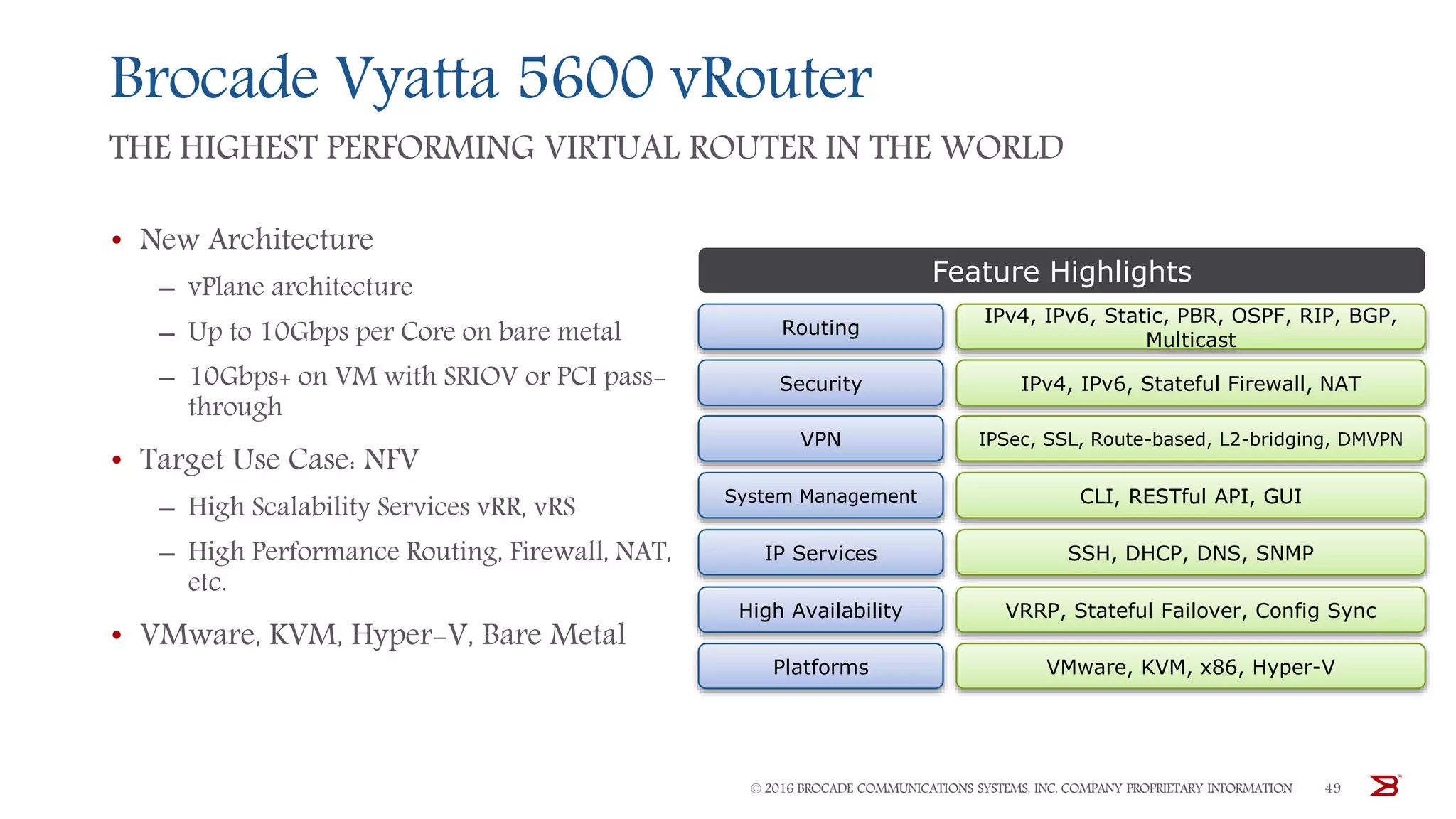
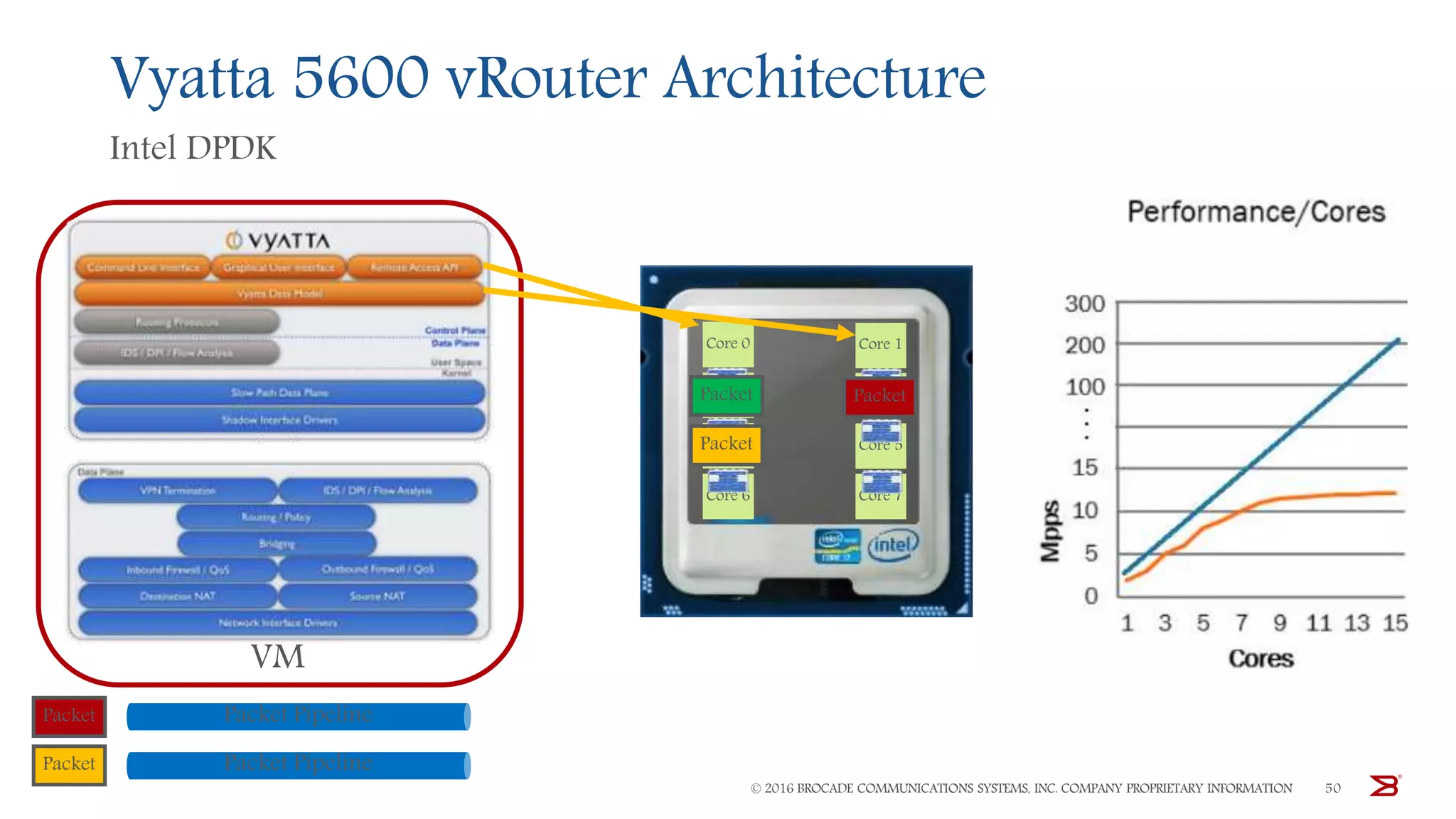
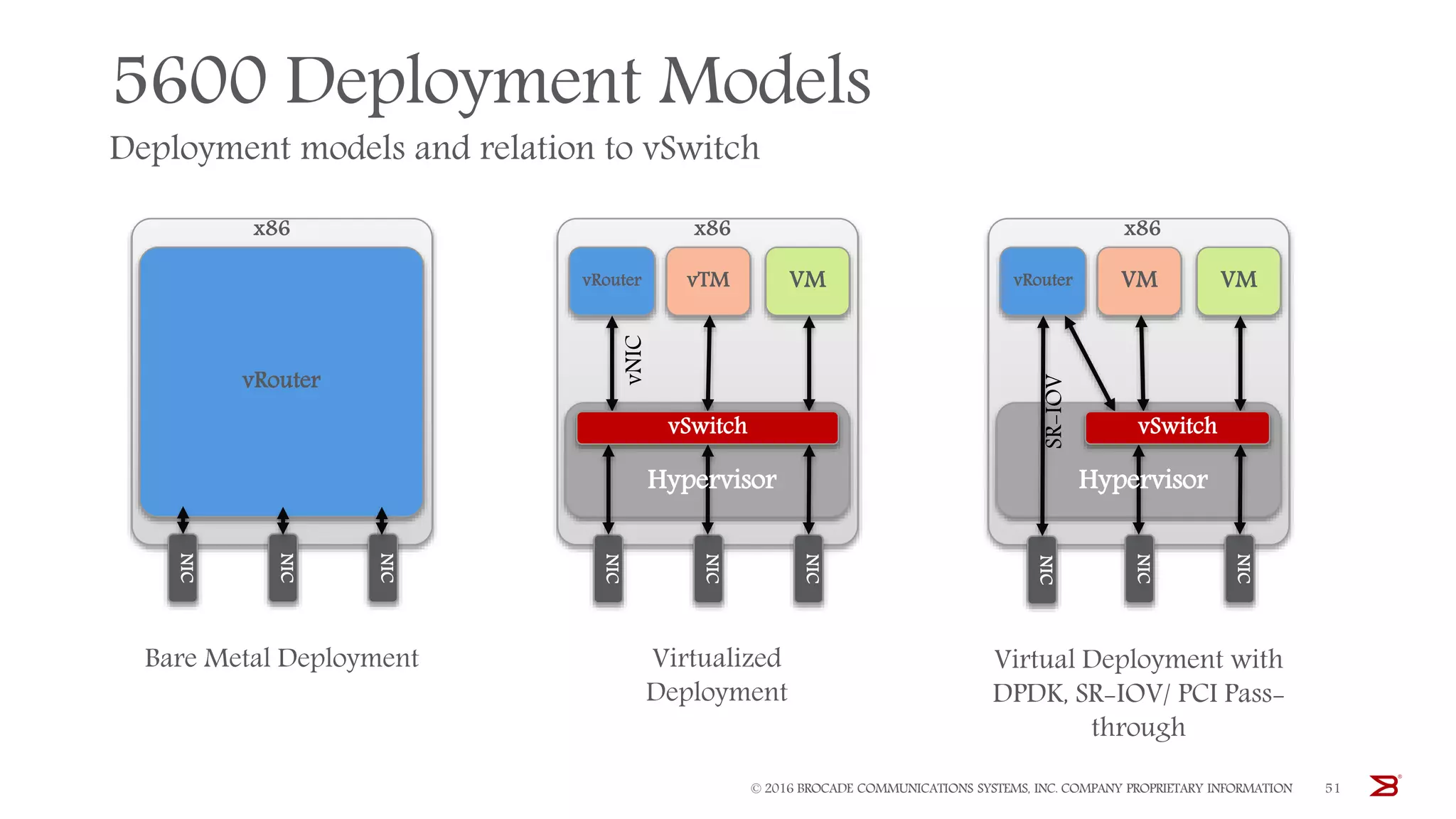
The Brocade vADC portfolio provides a range of application delivery controller solutions including the Traffic Manager load balancer, Web Accelerator, Web Application Firewall, and Services Director licensing manager, which can be deployed as virtual appliances on various hypervisor and cloud platforms and offer features like traffic management, acceleration, security, and flexible licensing.