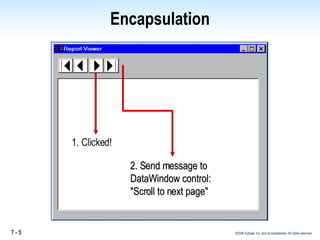
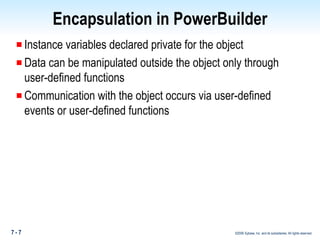
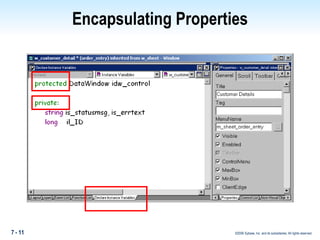
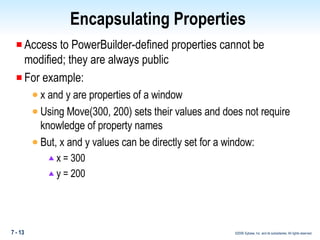
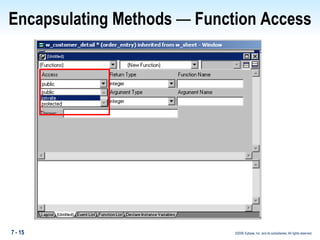
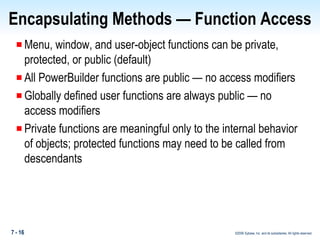
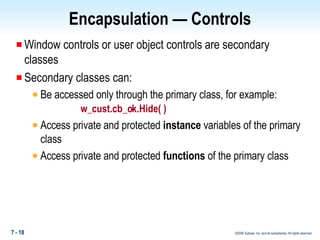
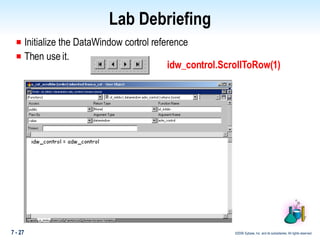
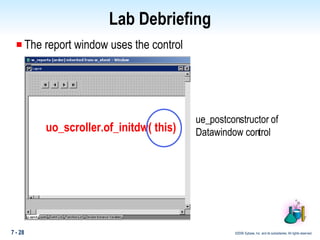
The document discusses encapsulation in PowerBuilder. Encapsulation is the process of incorporating properties and methods together in an object and limiting access to an object's properties and implementation of its behavior through information hiding. PowerBuilder allows assigning access rights to user functions and instance variables to restrict access. Events are always public while operational access rights can fine-tune access to instance variables, such as making variables public but read-only.