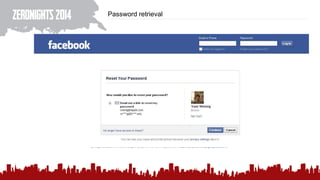
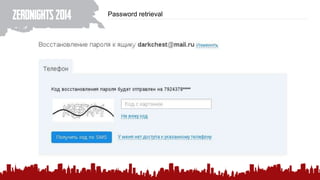
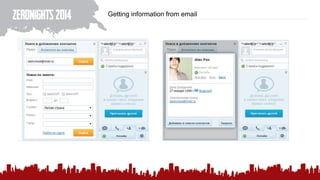
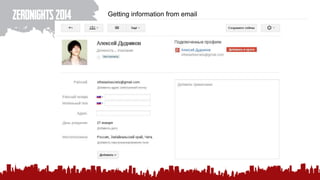
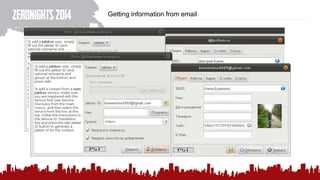
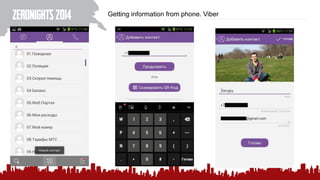
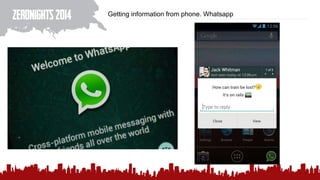
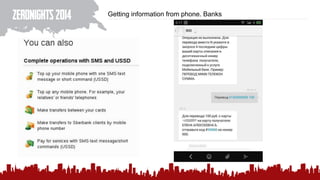
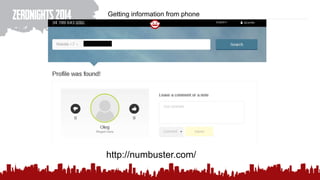
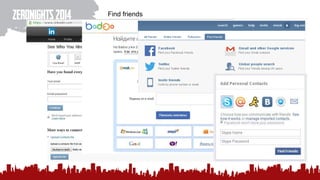
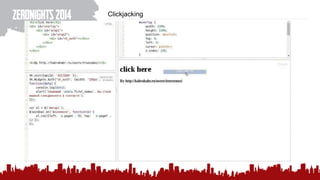
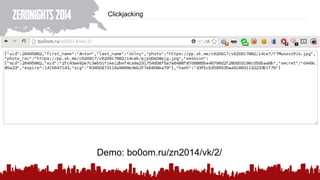
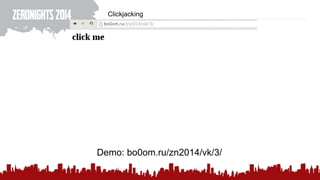
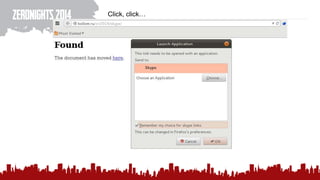
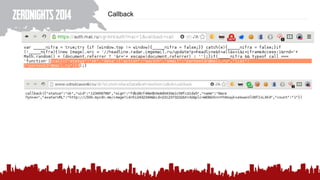
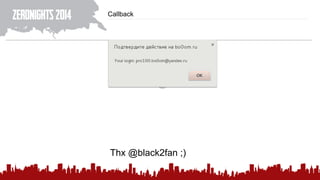
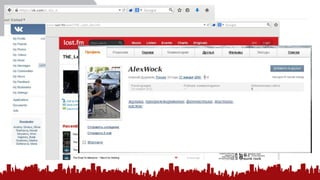
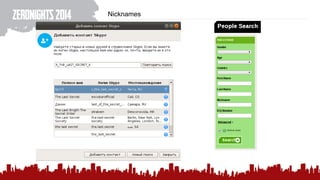
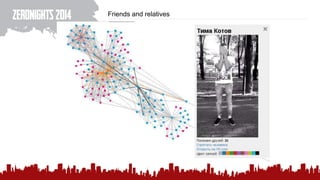
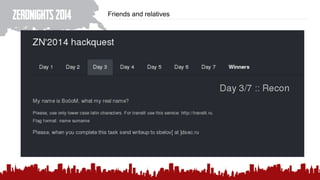
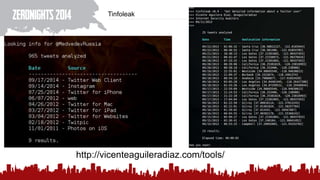
The document discusses various methods of deanonymization and espionage, emphasizing techniques for password retrieval and information gathering from different platforms such as email and messaging apps. It also covers tracking and analytics technologies, including various cookie storage mechanisms and clickjacking. Additionally, the document includes links to demonstrations and tools related to these topics.