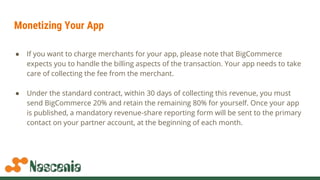
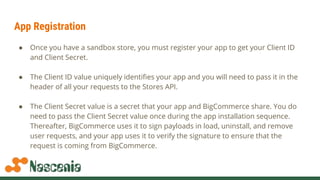
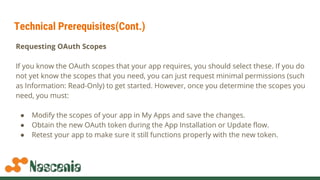
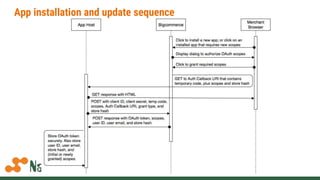
The document discusses building apps for BigCommerce using OAuth authentication. It covers registering an app to get client IDs and secrets, handling billing for paid apps, and the app installation and update sequence which involves exchanging a temporary code for a permanent OAuth token through callback URLs. Code examples show making API requests using the OAuth token to access a store's data on behalf of the authenticated user.












![API Request Example(Ruby on Rails)
connection = Bigcommerce::Connection.build(
Bigcommerce::Config.new(
store_hash: ENV['BC_STORE_HASH'],
client_id: ENV['BC_CLIENT_ID'],
access_token: ENV['BC_ACCESS_TOKEN']
)
)
Bigcommerce::System.time(connection: connection)
=> #<Bigcommerce::System time=1466546702>](https://image.slidesharecdn.com/bigcommerceappdevelopment-170417113415/85/Big-commerce-app-development-18-320.jpg)
