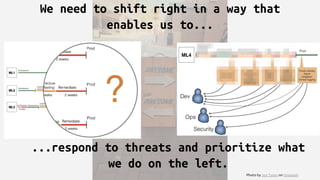
The document discusses the concept of 'shifting left' in software testing, highlighting the importance of integrating security early in the development process according to the devsecops paradigm. It emphasizes the need to also 'shift right' to effectively respond to threats by providing feedback from production to development. The author encourages the establishment of a feedback loop among development, security, and operations for improved optimization and security practices.






![Instrument for security...
Photo by Patrick Fore on Unsplash
We already do this for application performance monitoring
One of the best approaches is to provide rapid
feedback to developers. In the land of
application performance, we found that
running APM tools in production was a way to
help developers find places to optimize their
code. This created a feedback loop from
production (the right) to development (the
left).[1]
Any sensitive /
high risk
transactions.
1. James Wickett, https://labs.signalsciences.com/devsecops-security-shift-right](https://image.slidesharecdn.com/triangledevops-shiftleftshiftright-181108114112/85/Shift-Left-Wait-what-No-Shift-Right-8-320.jpg)
