The document discusses compound annual growth rates (CAGRs) that were calculated based on software size data from six products described in previous Impact columns over periods ranging from seven to 22 years. The CAGRs for the six products fell within a surprisingly narrow range of 1.11 to 1.29, providing empirical evidence that software growth averages around 15% per year. The findings suggest that claims about software doubling every two years align with observed growth rates.
















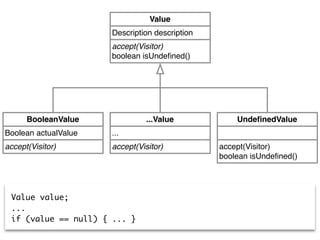
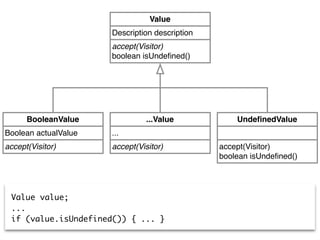
![valueClass := self allModelTypes entityNamed: #'Value'.
valueVariables := valueClass withSubclassHierarchy
flatCollectAsSet: #structuresWithDeclaredType.
valueVariables select: [ :each |
(('*', each name , ' != null*') match:
each belongsTo sourceText) or: [
('*', each name , ' == null*') match:
each belongsTo sourceText ] ]
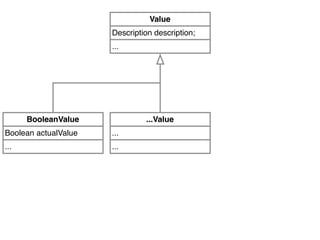
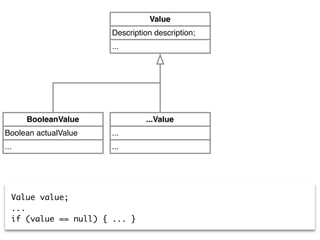
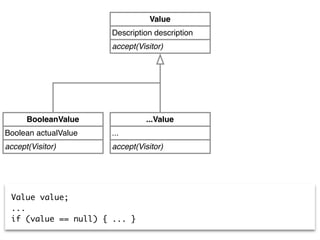
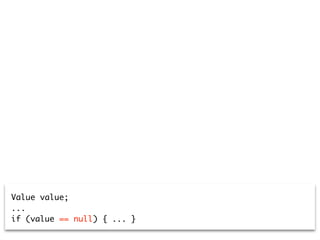
Value value;
...
if (value == null) { ... }](https://image.slidesharecdn.com/2015-12-benevol-software-environmentalism-160501064747/85/Beyond-software-evolution-Software-environmentalism-25-320.jpg)
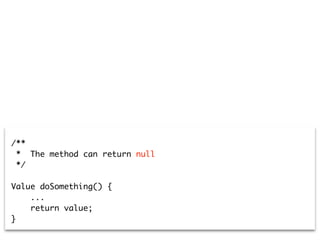
![valueMethods := valueClass withSubclassHierarchy
flatCollectAsSet: #behavioursWithDeclaredType.
valueMethods select: [:each |
each comments anySatisfy: [:c |
'*null*' match: c sourceText ] ]
/**
* The method can return null
*/
Value doSomething() {
...
return value;
}](https://image.slidesharecdn.com/2015-12-benevol-software-environmentalism-160501064747/85/Beyond-software-evolution-Software-environmentalism-27-320.jpg)