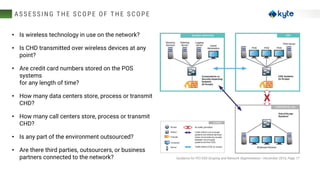
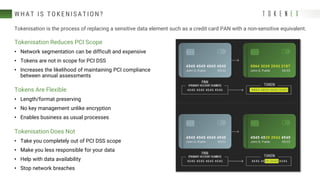
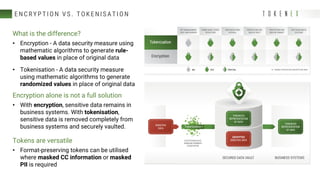
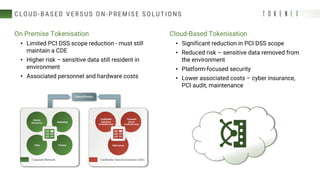
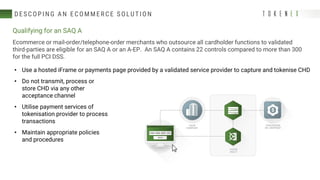
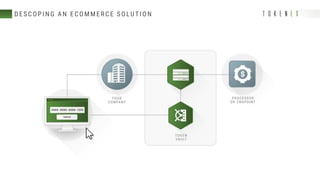
The document discusses best practices for reducing the scope of PCI compliance by addressing misconceptions and emphasizing effective techniques like network segmentation, tokenization, and encryption. It highlights the requirements of the PCI Data Security Standard (DSS) and explains the differences between tokenization and encryption, particularly in relation to PCI compliance and data protection. Additionally, the document explores how tokenization aligns with GDPR's pseudonymization requirements, providing insights on data protection by design and the legal implications for data controllers.