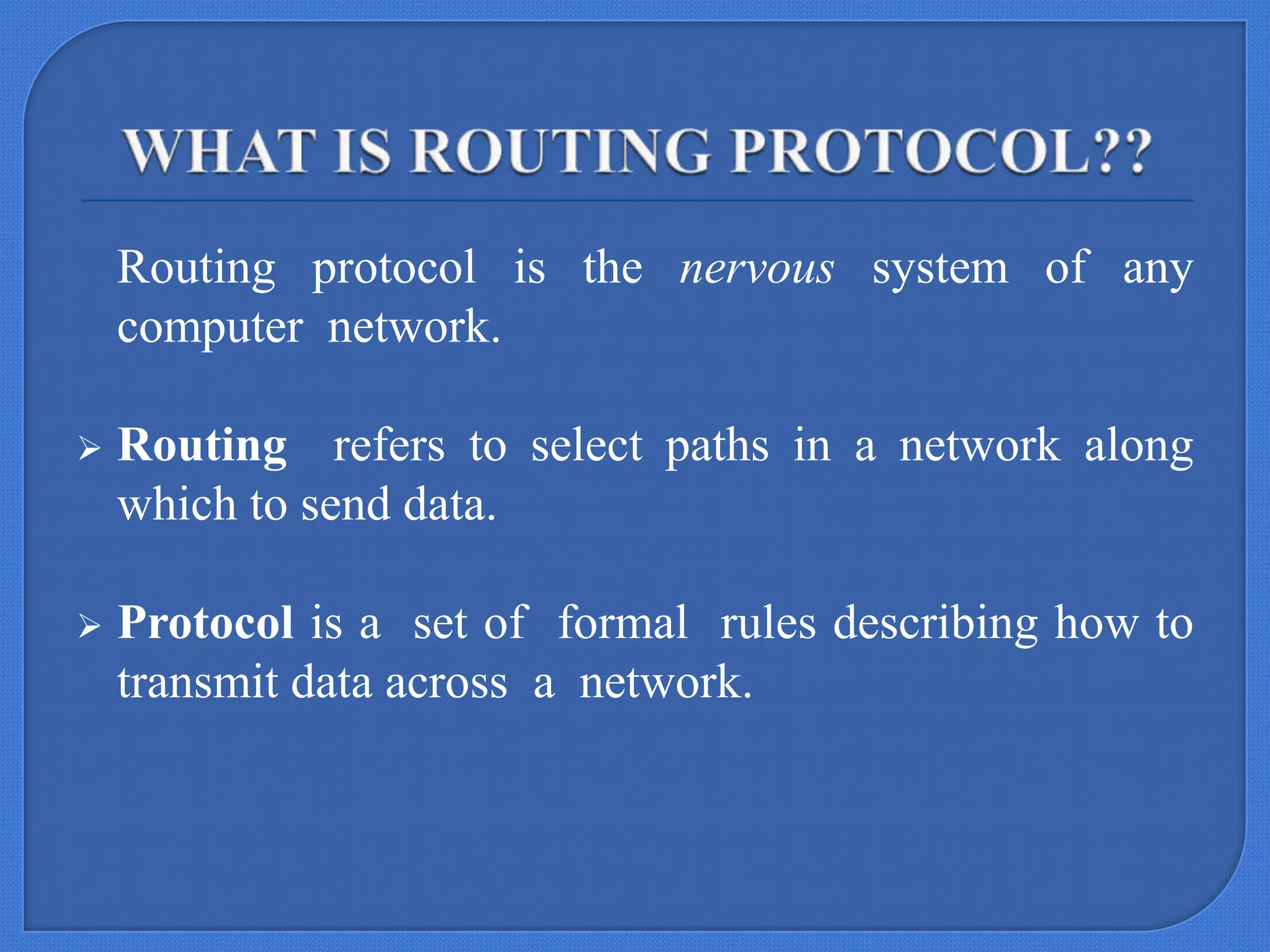
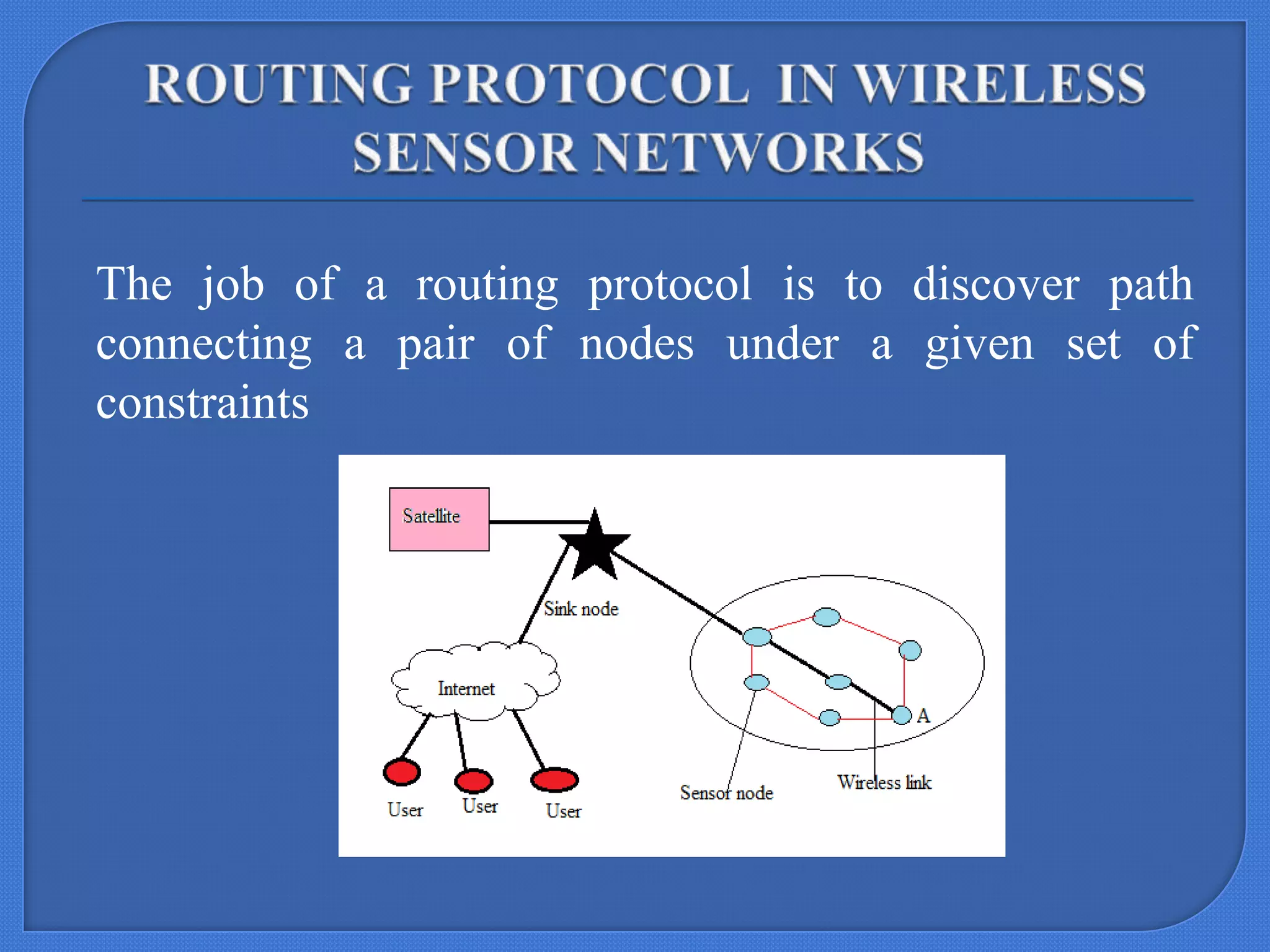
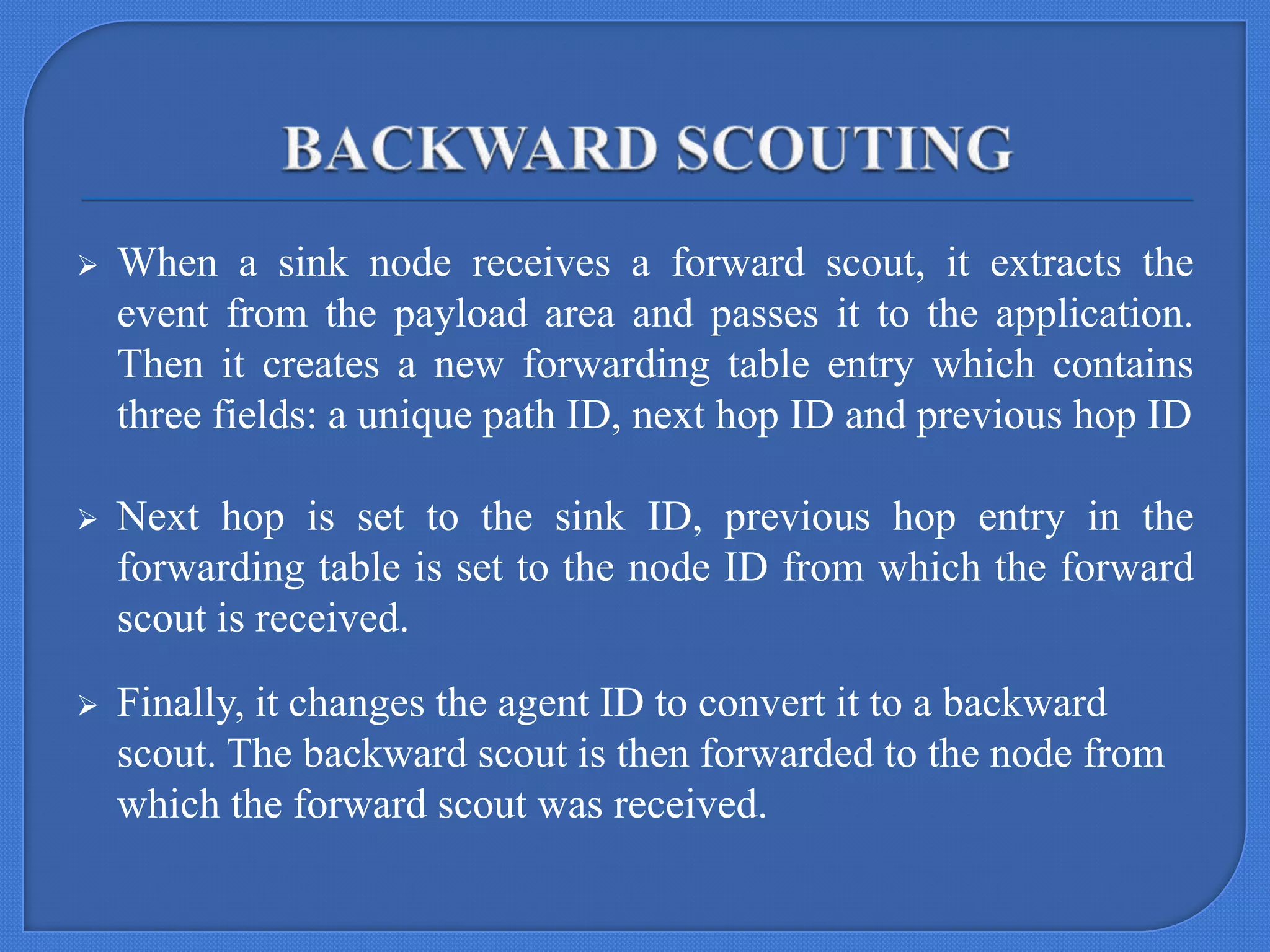
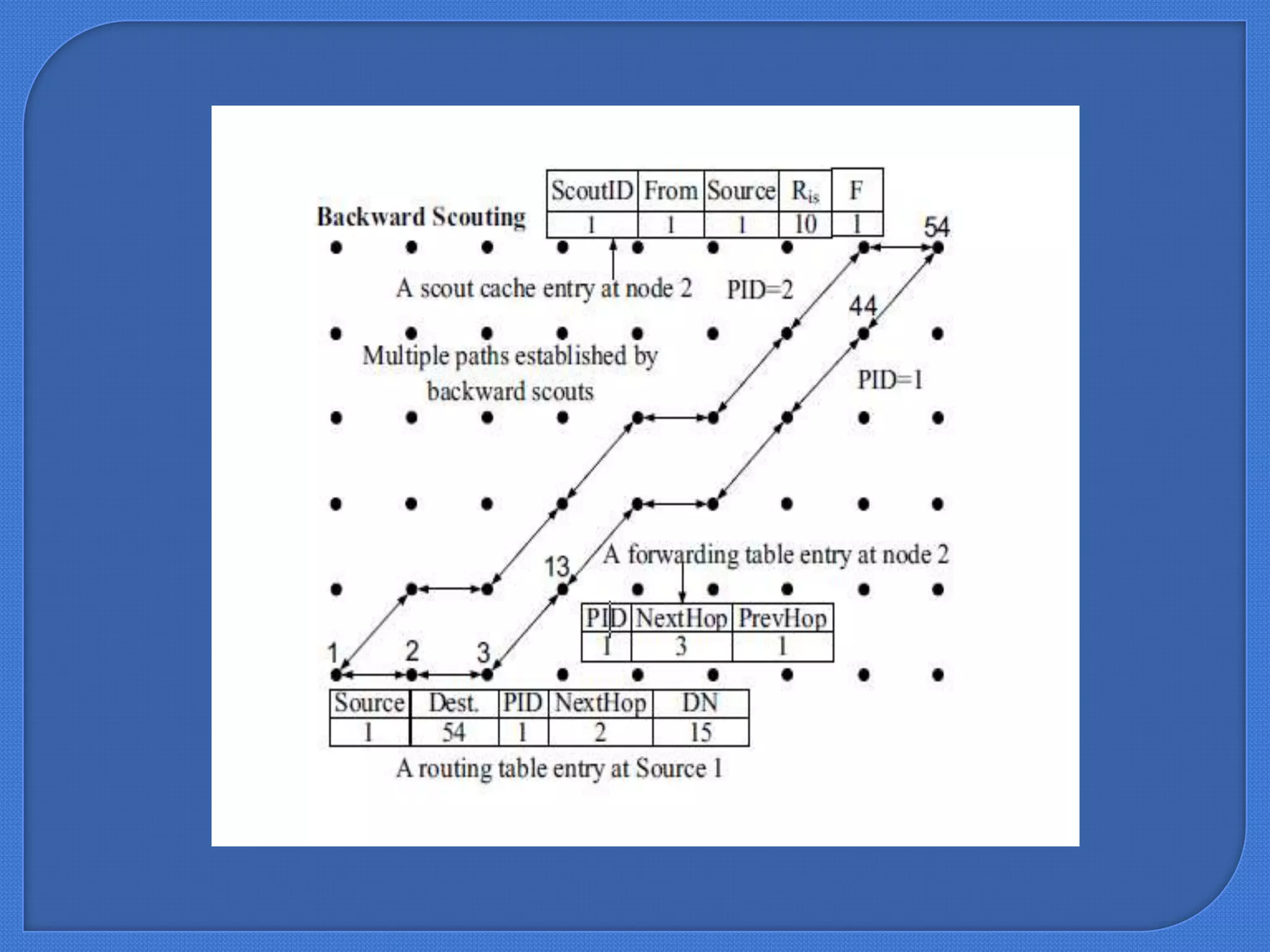
This document describes a seminar submitted by Sonam Jain for their Master's degree. The seminar focuses on BeeSensor, a routing protocol for wireless sensor networks inspired by bee communication behaviors. It discusses how bees communicate through dances to share information, and how this inspired the design of BeeSensor. The document outlines the key components of BeeSensor, including the different agent roles, protocol phases, and how it evaluates performance metrics like energy efficiency and packet delivery when compared to other routing protocols like AODV.















![[1]A.Moussa and N El-Sheimy, localization of wireless sensor
network using bees optimization algorithm,IEEE ,2011
[2]Karima Aksa, Mohammed Benmohammed, A Comparison
Between Geometric and Bio-Inspired Algorithms for Solving
Routing Problem in Wireless Sensor Network, International
Journal of Networks and Communications 2012, 2(3): 27-32
[3]K. Akkaya, M. Younis, A survey on routing protocols for
wireless sensor networks, Elsevier Ad Hoc Networks 3 (3)
(2005) 325–349.
[4]Nikolaos A. Pantazis, Stefanos A. Nikolidakis and Dimitrios
D. Vergados, Senior Member, IEEE, Energy-Efficient Routing
Protocols in Wireless Sensor Networks: A Survey ,IEEE
COMMUNICATIONS SURVEYS & TUTORIALS, VOL. 15,
NO. 2, SECOND QUARTER 2013](https://image.slidesharecdn.com/sss-131015040057-phpapp02/75/BeeSensor-routing-protocol-for-wireless-sensor-network-22-2048.jpg)
![[5]Muhammad Saleem, Gianni A. Di Caro, Muddassar Farooq
Swarm intelligence based routing protocol for wireless
sensor networks: Survey and future directions ,Elsevier
Information Sciences 181 (2011) 4597–4624
[6]Muhammad Saleem, Israr Ullah, Muddassar Farooq
BeeSensor: An energy-efficient and scalable routing protocol
for wireless sensor networks, Elsevier Information Sciences
200 (2012) 38–56](https://image.slidesharecdn.com/sss-131015040057-phpapp02/75/BeeSensor-routing-protocol-for-wireless-sensor-network-23-2048.jpg)
