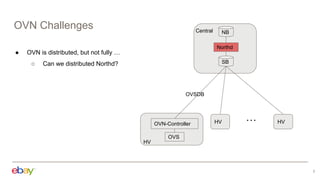
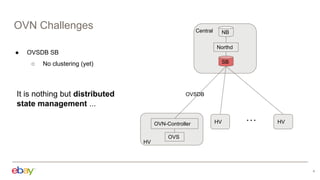
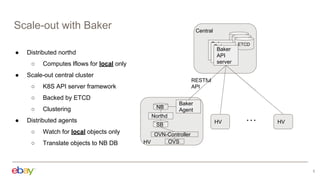
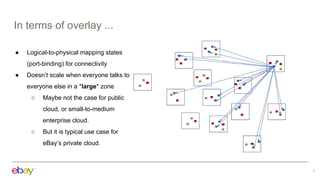
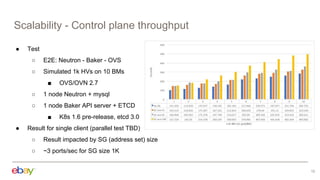
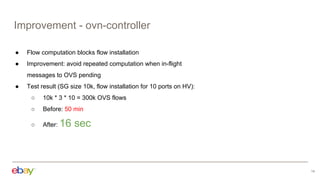
This document discusses using Kubernetes API server framework (Baker) to scale out OVN control plane. It aims to distribute OVN northd and central OVSDB cluster. Challenges include lack of clustering in OVSDB SB and distributed state management. Baker proposes distributed northd, scale-out central cluster backed by ETCD, and distributed agents to watch local objects. This would address connectivity issues in large cloud deployments. The document also discusses addressing segmentation vs connectivity, using ACLs and address sets for L3 segmentation, and evaluating port security and ACL processing on each hypervisor.