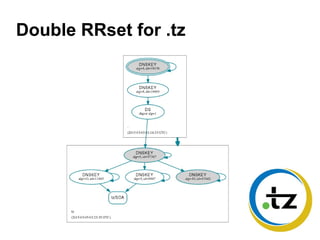
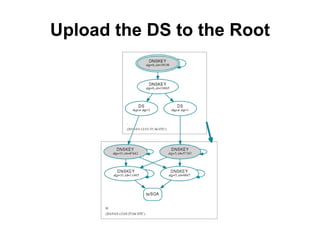
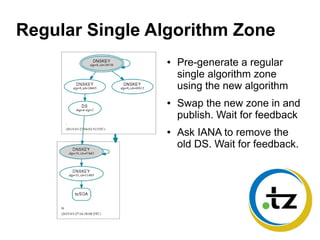
The document discusses the key signing key (KSK) algorithm rollover process for the .tz domain. It implemented a "double RRset" rollover method, where it generated a signed zone file with signatures from both the old and new KSK, submitted the new DS record to IANA, and waited for caches to expire before removing the old DNSKEY and DS records. This process allowed the .tz registry to upgrade its software while rolling over its KSK to a new algorithm, addressing security recommendations against the SHA1 algorithm. It required a manual process using dnssec-signzone due to limitations in OpenDNSSEC's support for multiple concurrent algorithms and offline KSKs.