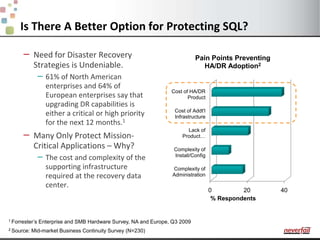
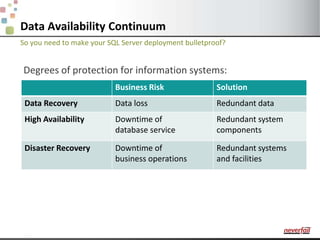
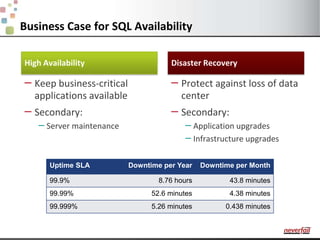
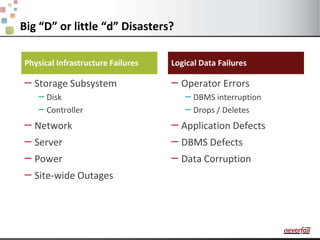
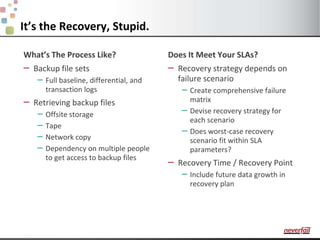
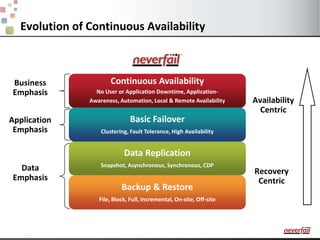
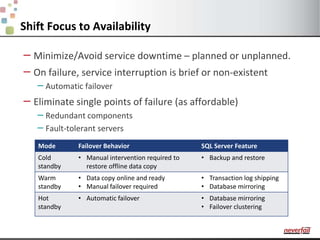
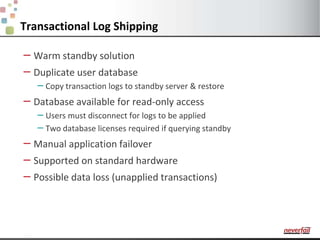
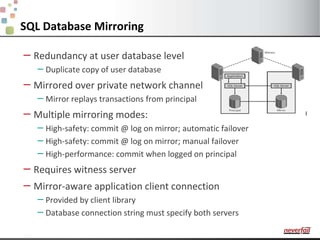
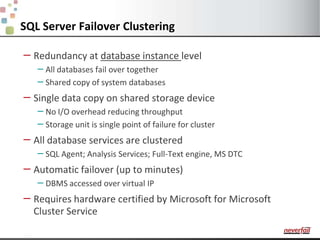
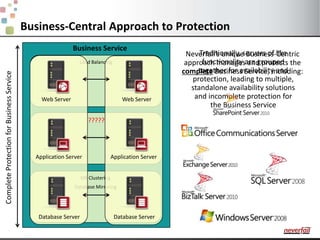
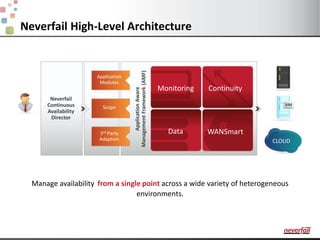
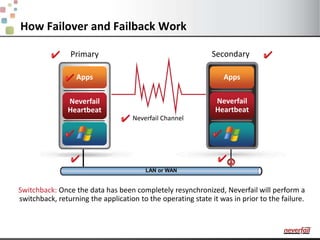
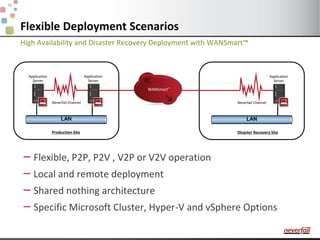
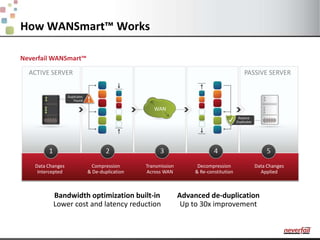
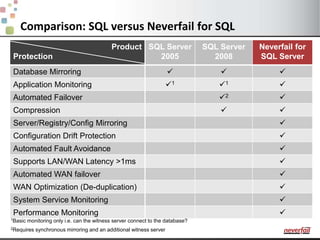
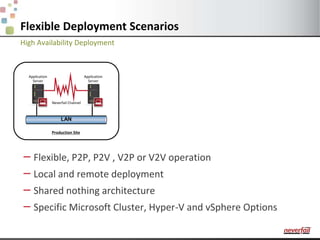
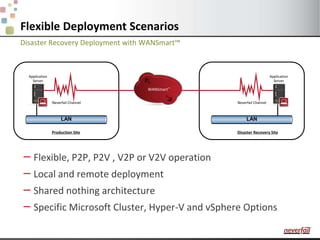
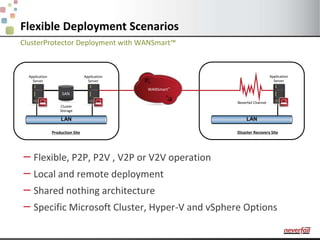
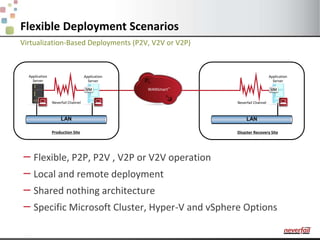
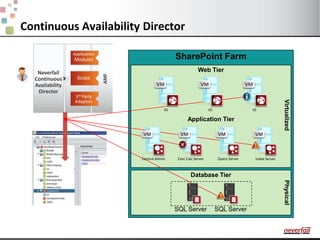
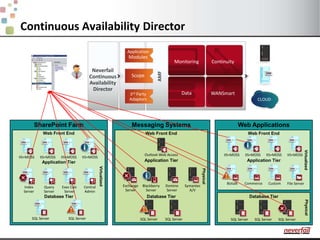
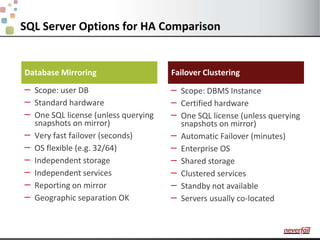
This document discusses various options for providing high availability and disaster recovery for SQL Server deployments. It describes database mirroring and failover clustering which provide redundancy at the database or instance level. It also discusses third party solutions like Neverfail which provide end-to-end protection of multi-tier applications and entire business services across local and remote sites. Neverfail leverages application awareness and automation to minimize downtime from both planned and unplanned outages.