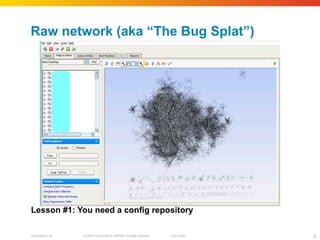
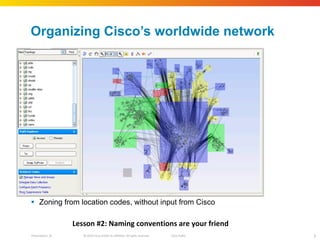
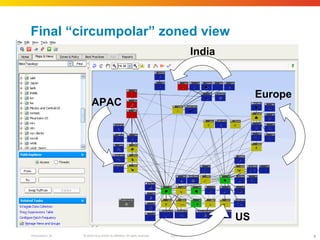
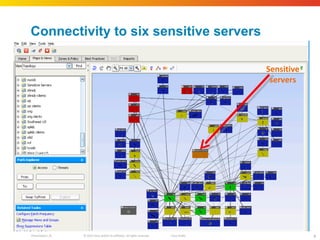
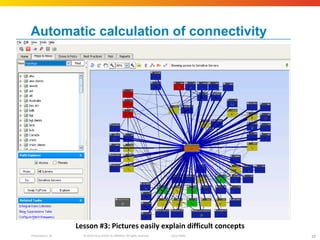
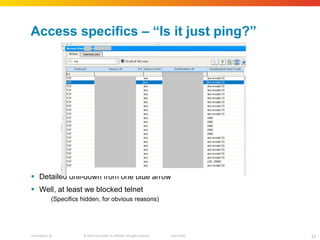
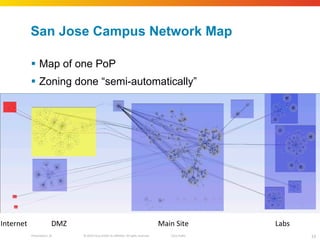
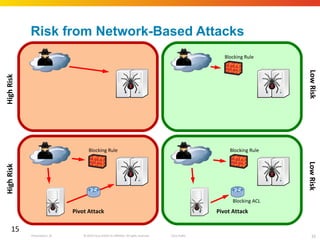
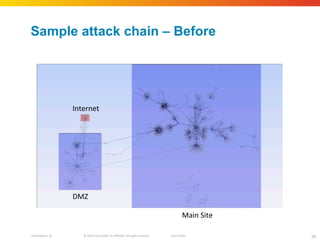
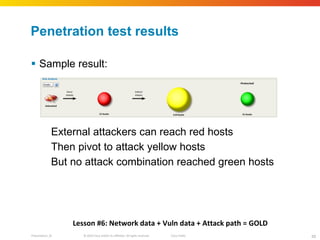
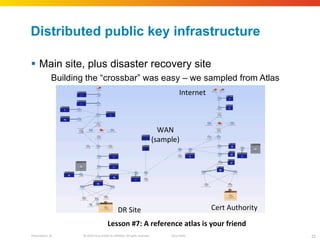
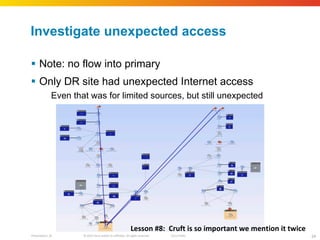
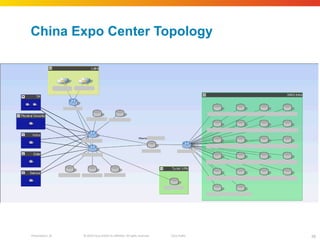
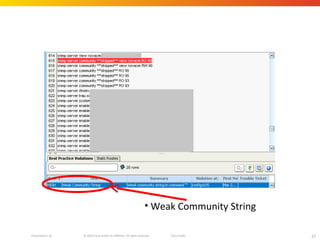
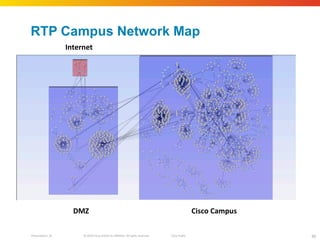
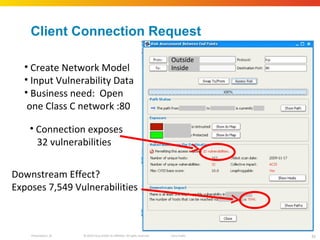
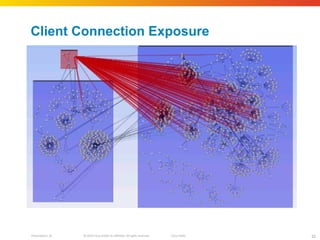
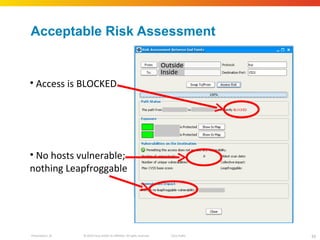
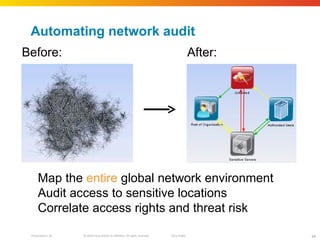
The document discusses how network security assessments have traditionally been done manually, which is time-consuming and error-prone. It then describes how Cisco used automation to map their entire global network infrastructure in two weeks. Several case studies are presented that show how automation can efficiently analyze network topology and access, detect vulnerabilities and policy violations, and evaluate proposed configuration changes. Automation provides a consistent, repeatable process for network security that improves visibility, prioritization of issues, and decision making.