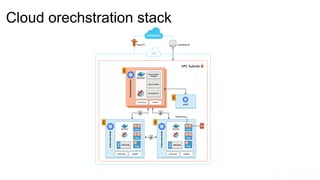
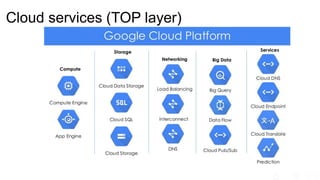
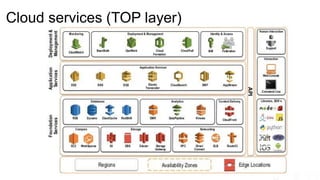
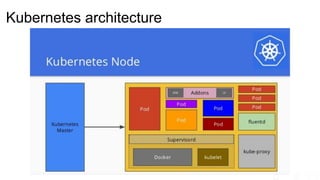
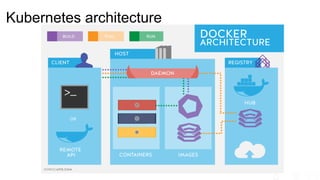
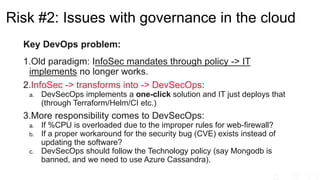
The document outlines significant risks associated with cloud orchestration, including compromises in cloud security, governance issues, and segregation challenges. It emphasizes the difficulty of recovering from compromises and highlights the importance of using automation tools, proper access management, and implementing security best practices. Additionally, it discusses the transition from traditional infosec practices to a DevSecOps approach, while stressing the need for thorough monitoring, compliance checks, and avoiding hardcoded credentials.