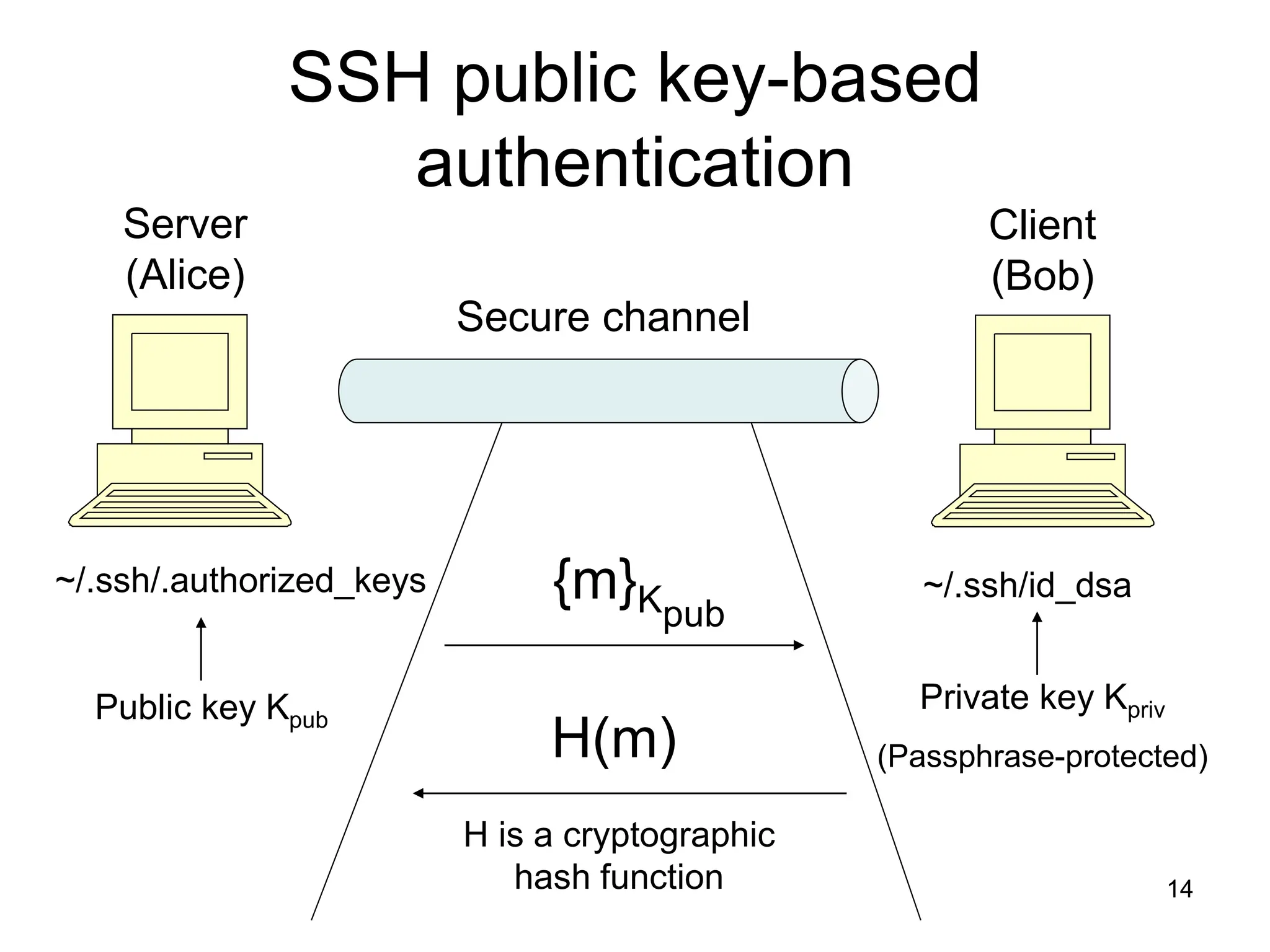
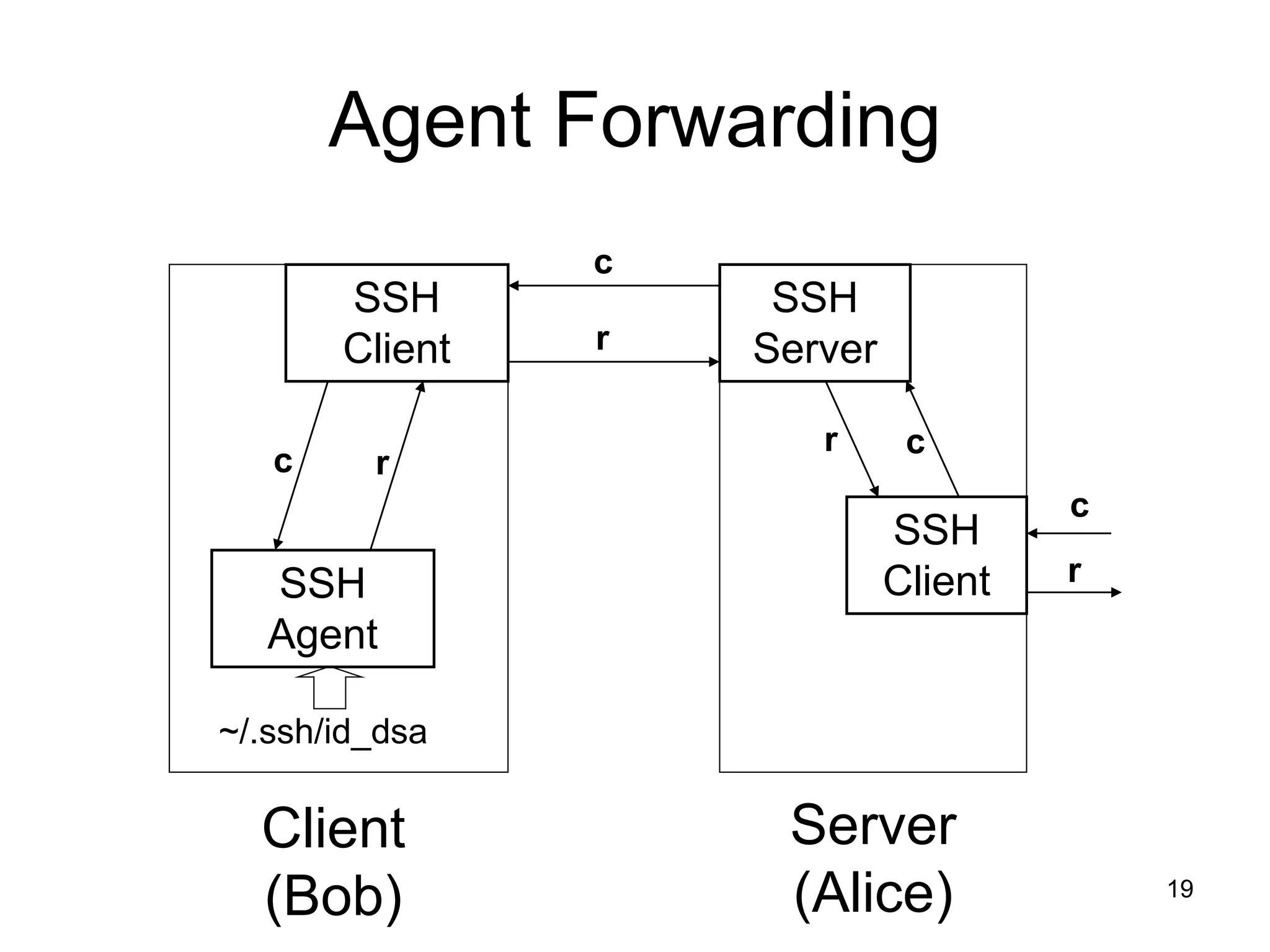
The document discusses authentication and authorization in cybersecurity, outlining the processes of verifying identity and determining access permissions. It covers various methods of authentication, including simple password verification and challenge-response protocols, emphasizing the importance of using secure methods like public key cryptography and SSH for secure communication. Additionally, it highlights the use of an SSH agent to manage private keys securely, enabling seamless user authentication without repeatedly entering passphrases.