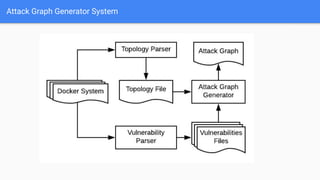
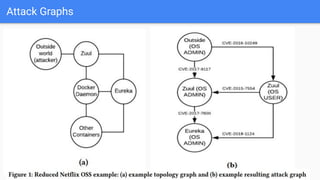
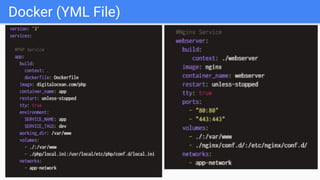
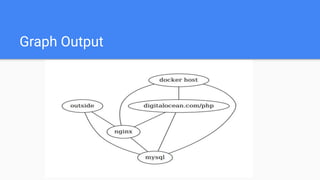
The document discusses microservices architecture, emphasizing its features such as maintainability, testability, and independent deployment. It introduces containers and tools like Docker and Kubernetes for managing application lifecycles, as well as the need for advanced vulnerability scanners due to network-based attacks. Finally, the document highlights attack graphs as a method for analyzing network security weaknesses, providing an overview of their structure and applications.