Embed presentation










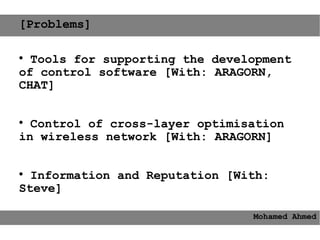

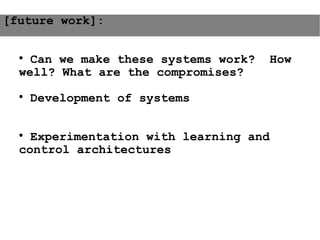
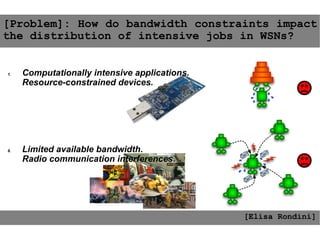
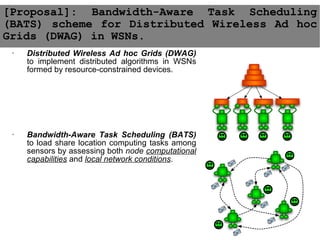
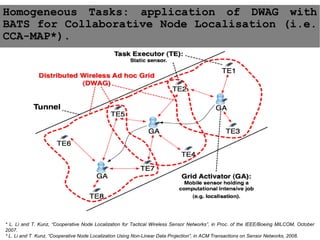

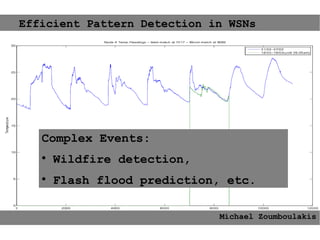
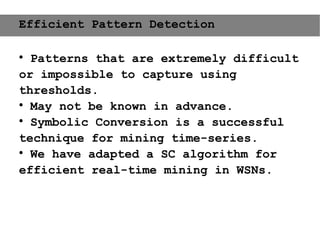
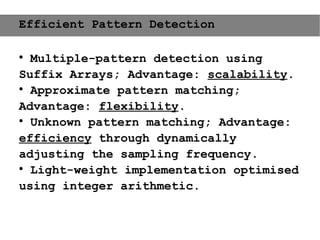
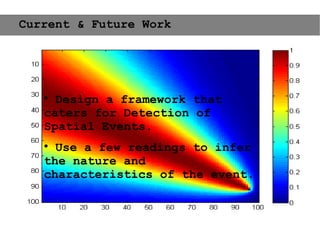

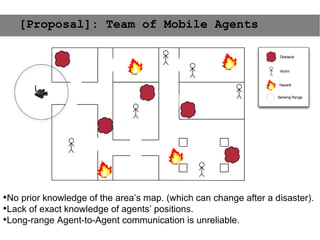
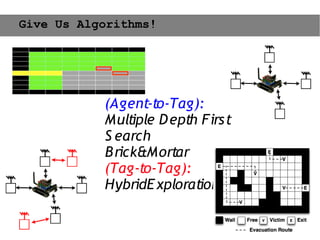


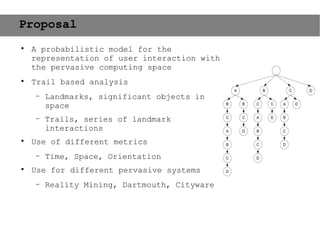
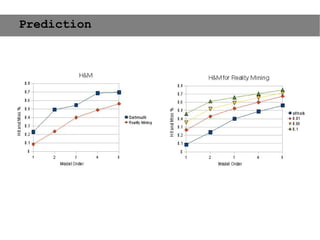
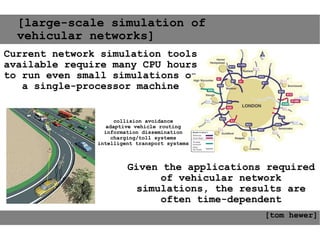
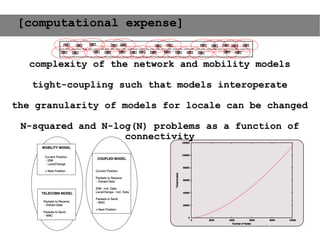
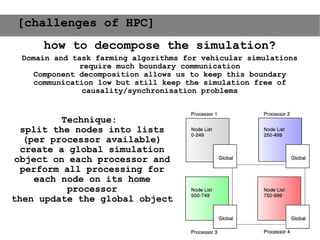
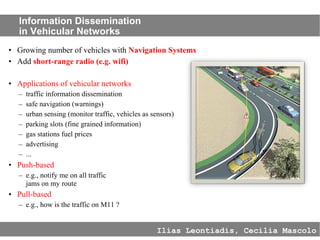
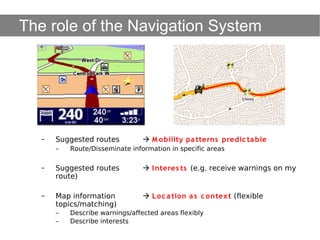
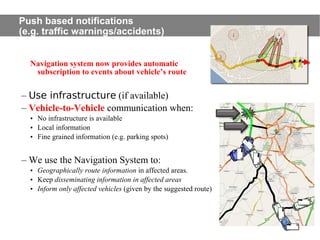
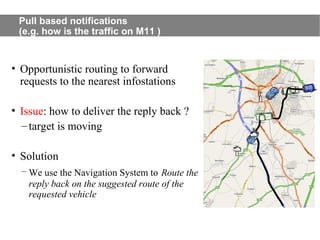


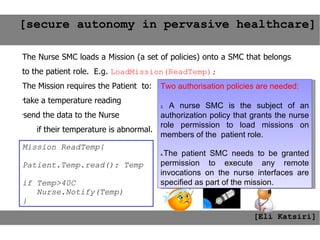
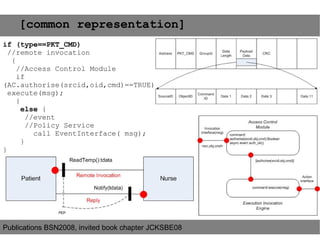
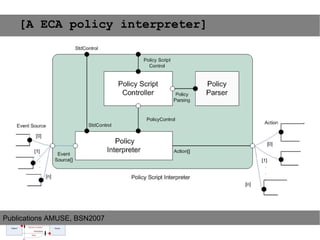
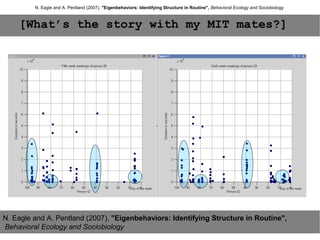
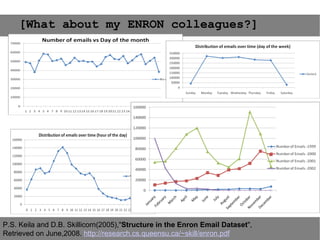
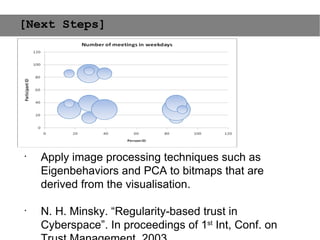
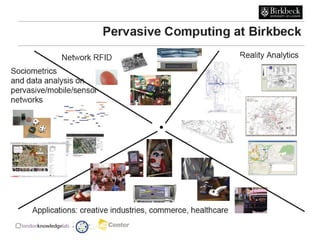

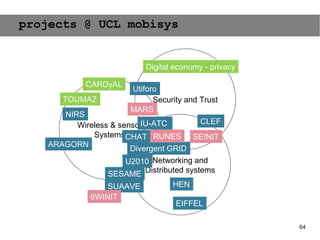

This document provides an agenda for the MOBISYS seminar, listing the speakers and their topics. It includes snippets of conversations between the speakers as they introduce themselves and their topics. The document discusses research related to pervasive computing, wireless networks, and mobile systems.































































