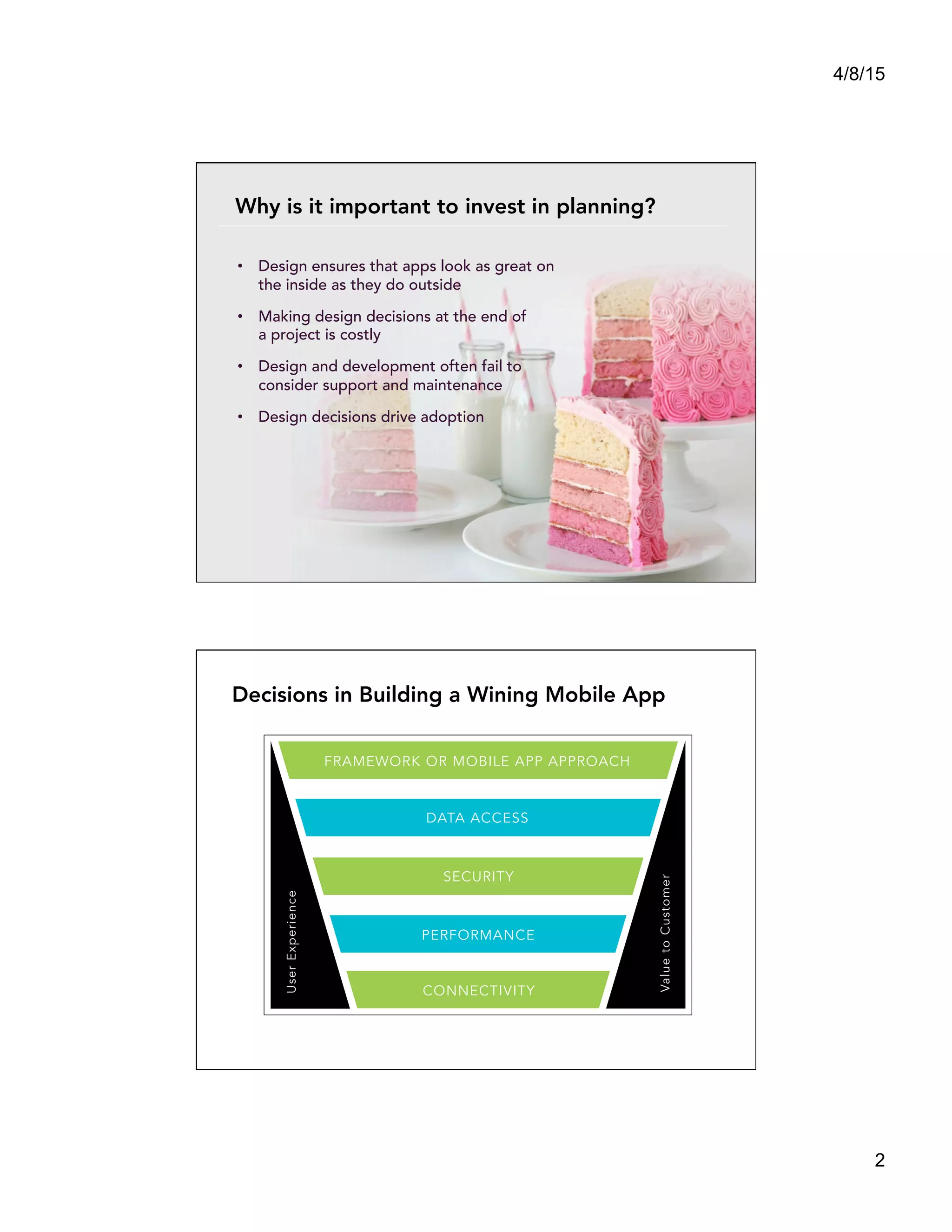
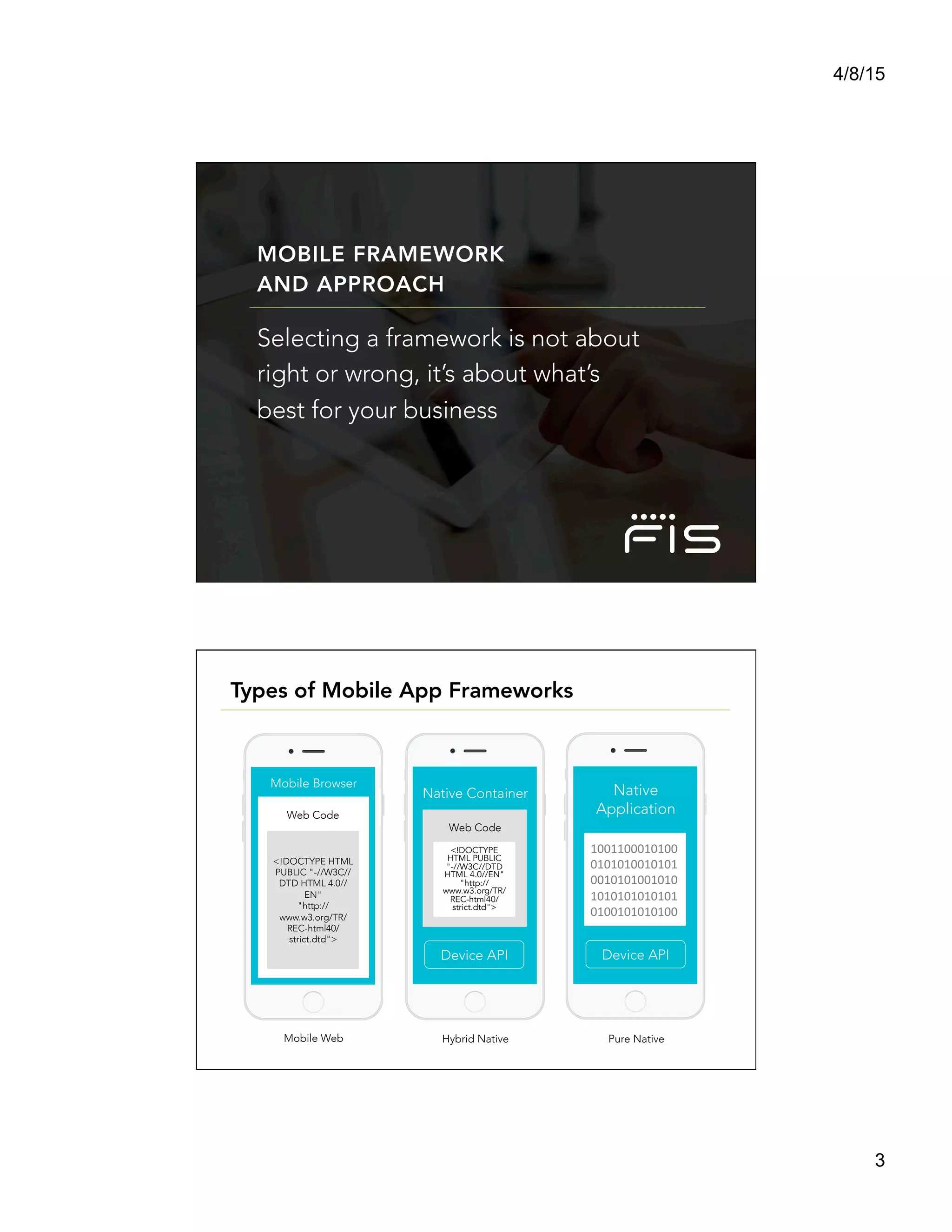
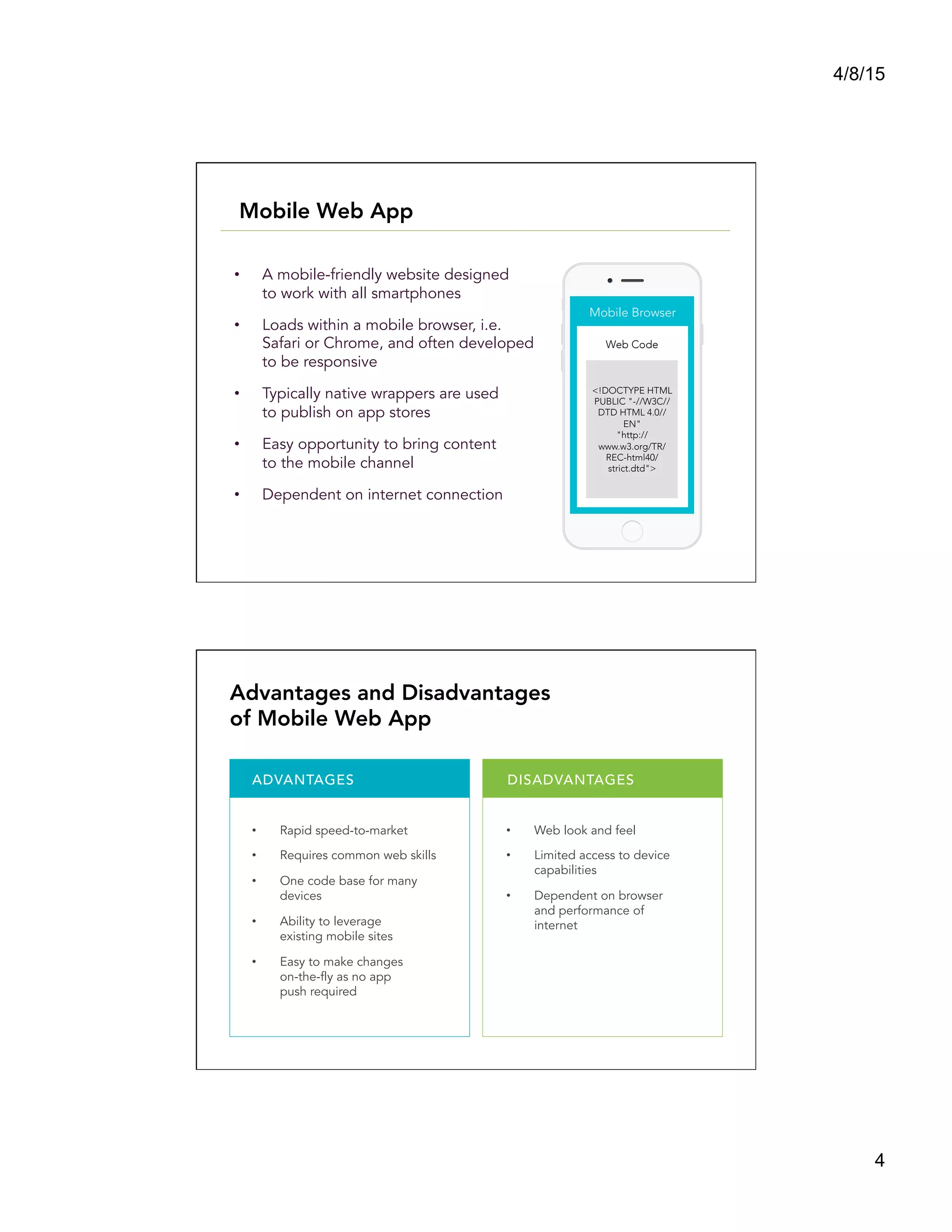
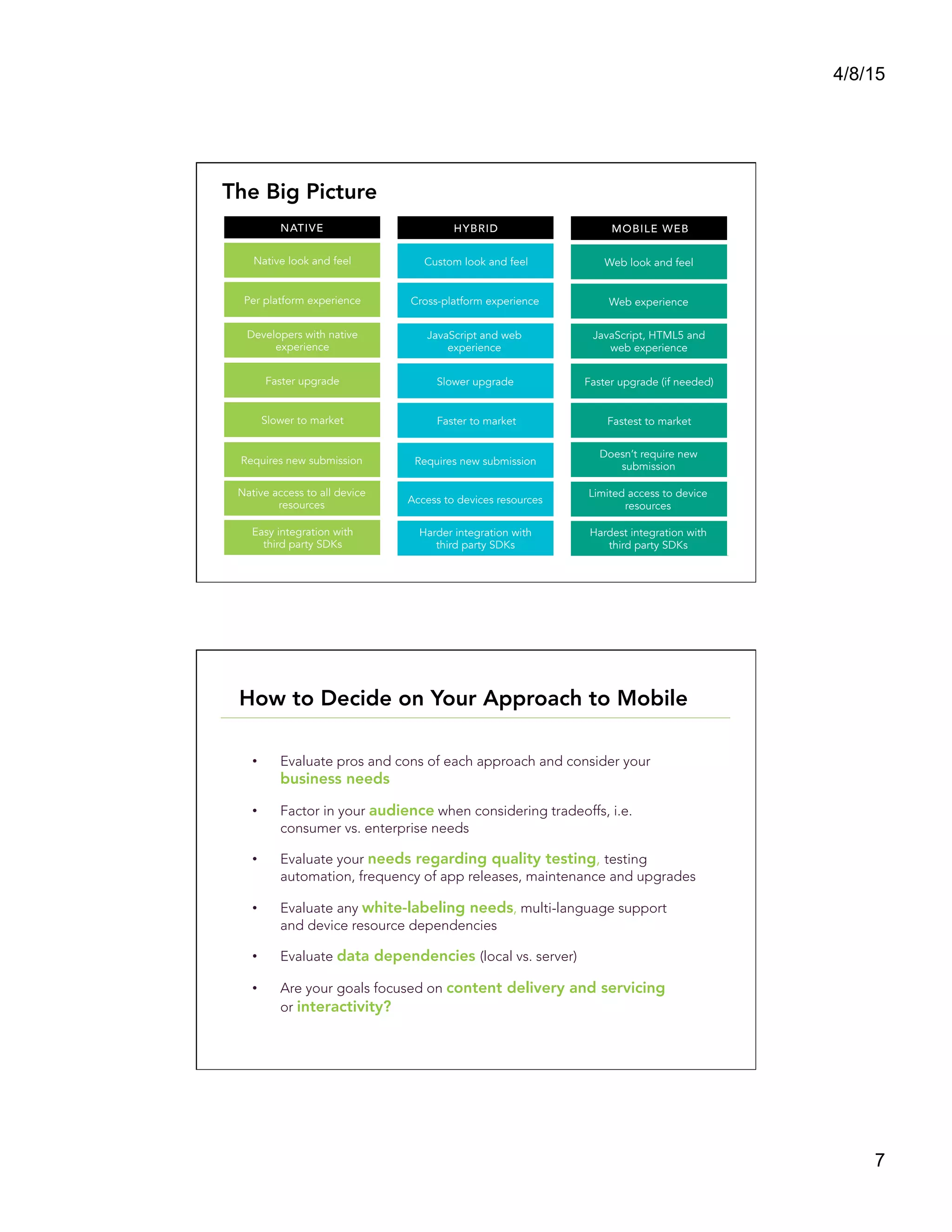
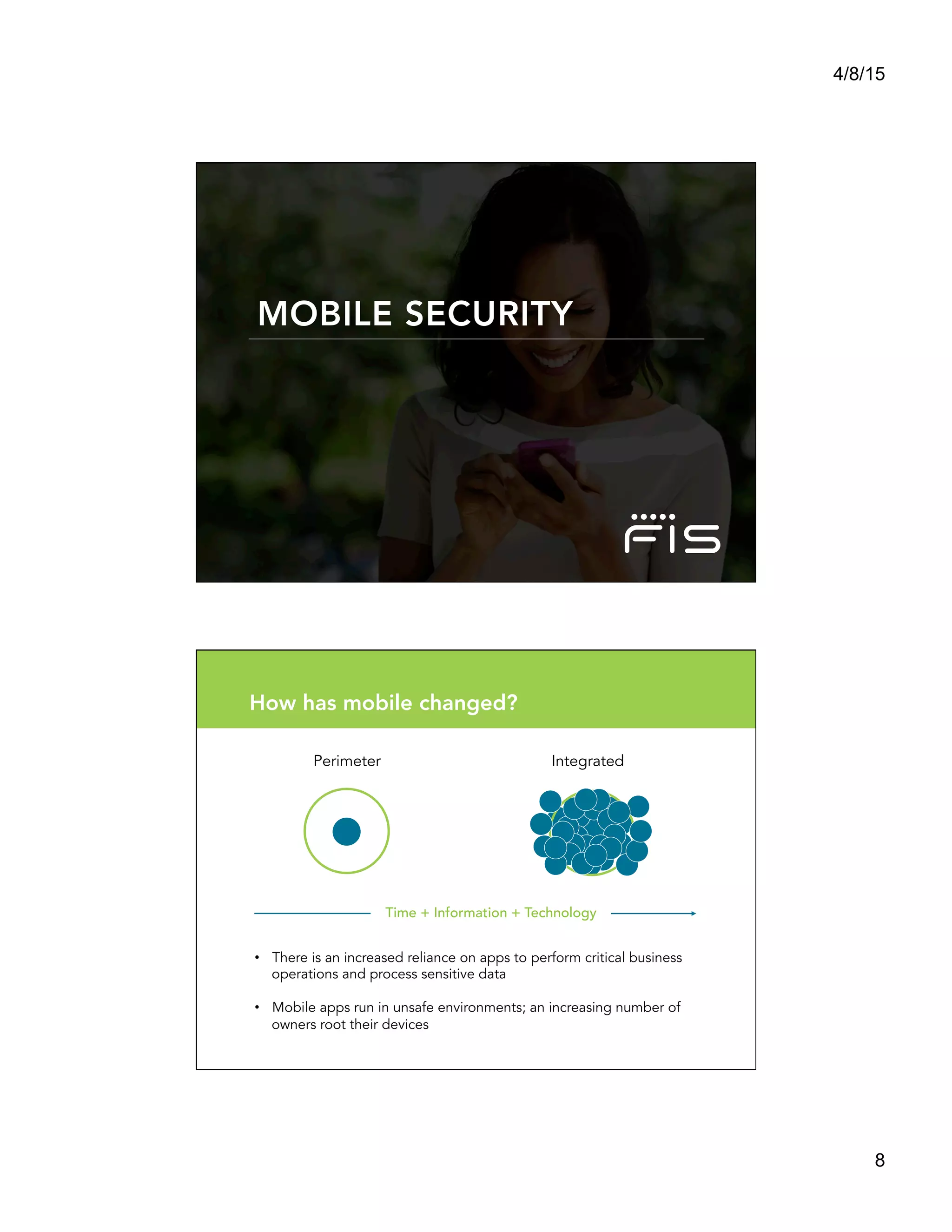
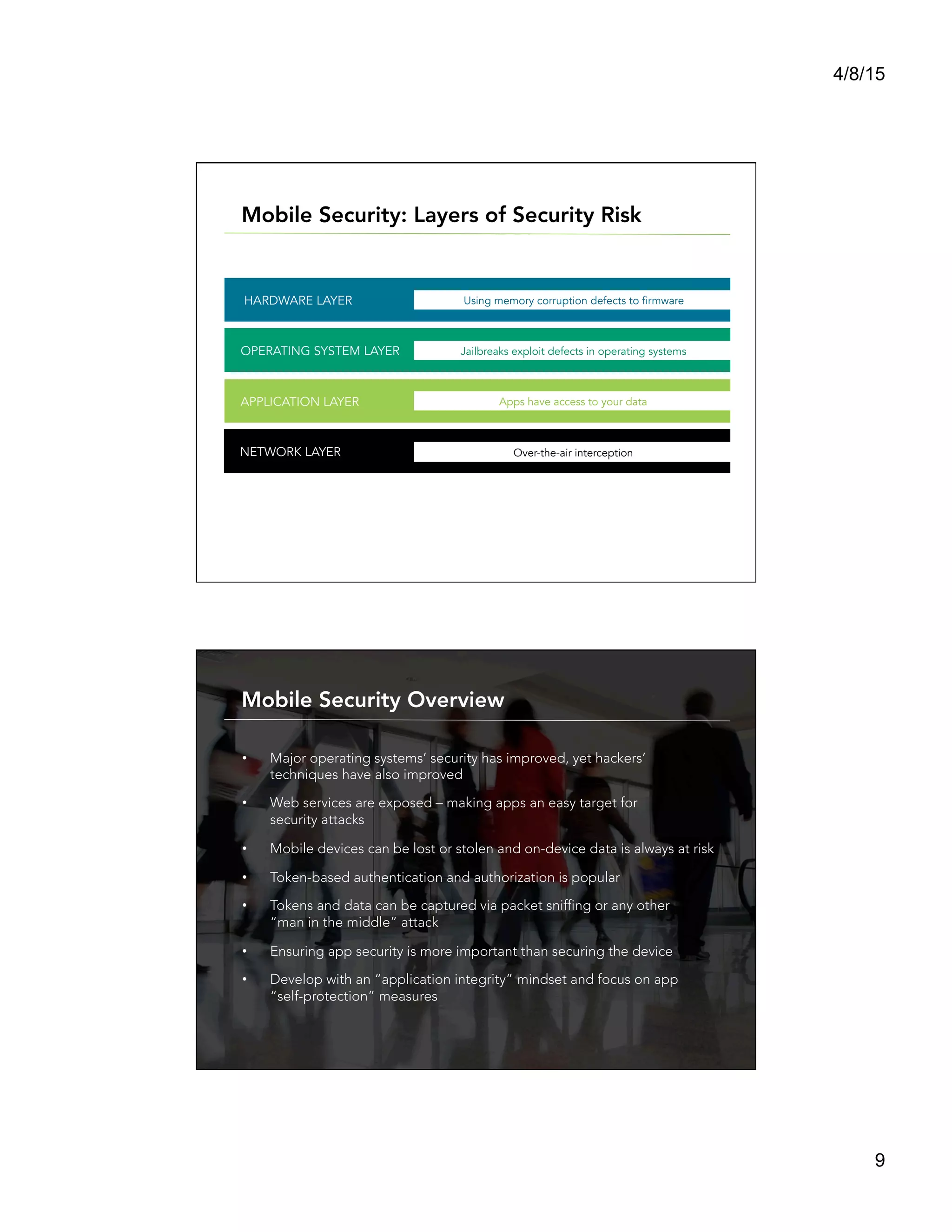
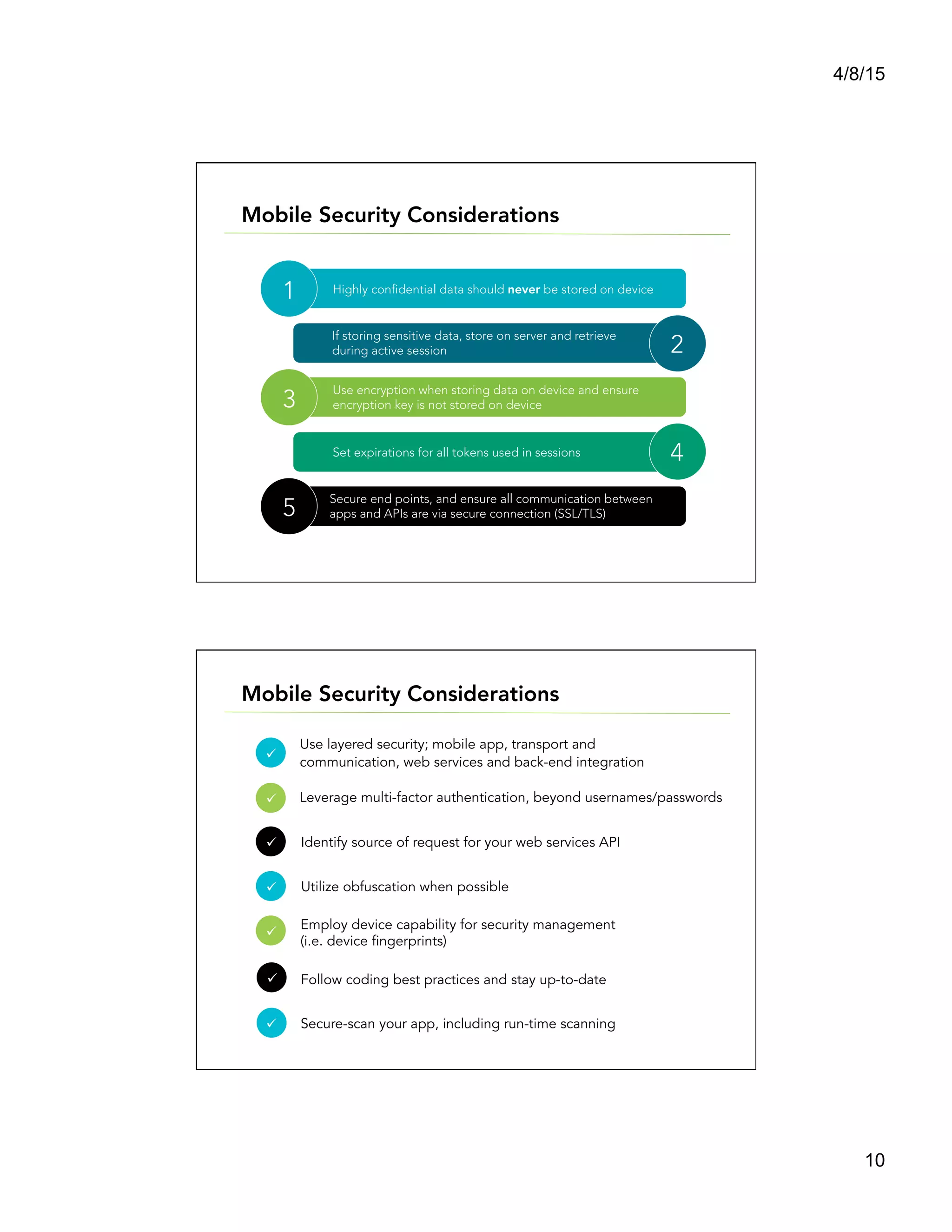
This document summarizes a presentation titled "Architect a Winning Mobile Application" given by Shadi Saifan of FIS Mobile. The presentation covered key topics for developing successful mobile applications such as selecting a mobile development approach, security considerations, performance, data access, and connectivity. It compared native, web, and hybrid mobile app frameworks and outlined advantages and disadvantages of each. The presentation emphasized starting with the right architecture and making design decisions early that consider user experience, value, security, and long-term maintenance needs.