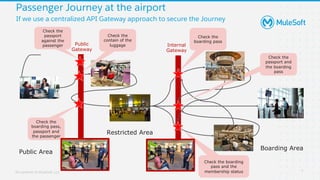
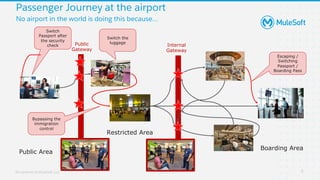
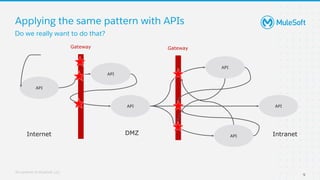
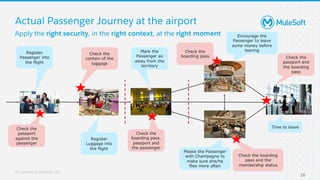
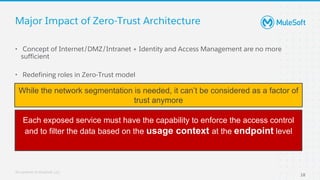
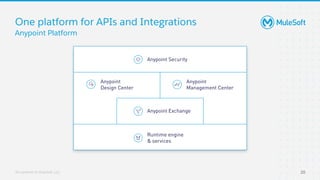
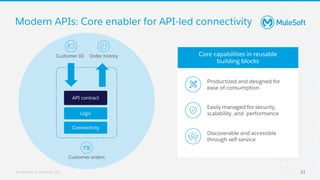
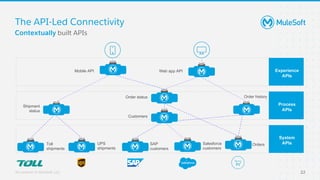
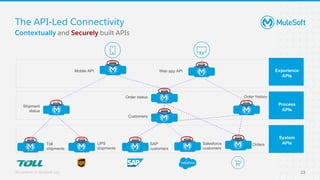
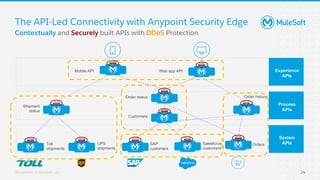
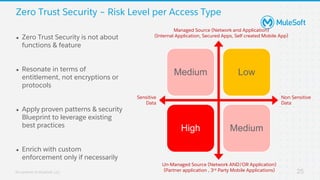
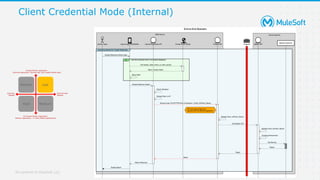
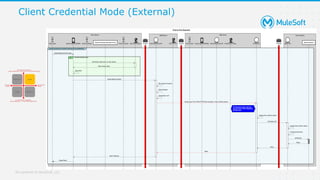
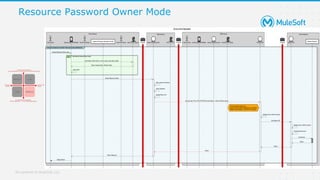
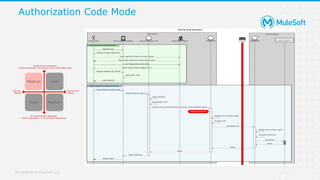
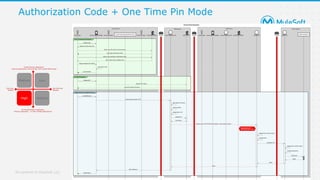
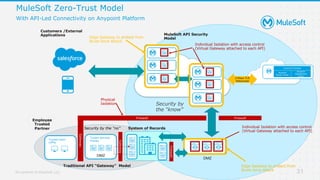
The document discusses applying zero-trust security with API-led connectivity. It begins by describing traditional trust boundary based security and its limitations. It then defines the zero-trust mindset, which assumes nothing and no one can be trusted and everything needs to be verified. The document outlines how adopting a zero-trust model impacts infrastructure, application, and data security layers. It argues a zero-trust architecture is now needed rather than relying only on network segmentation and IAM. The document concludes by describing how MuleSoft's Anypoint Platform enables building APIs in a way that is contextual, secure and aligned with a zero-trust approach.