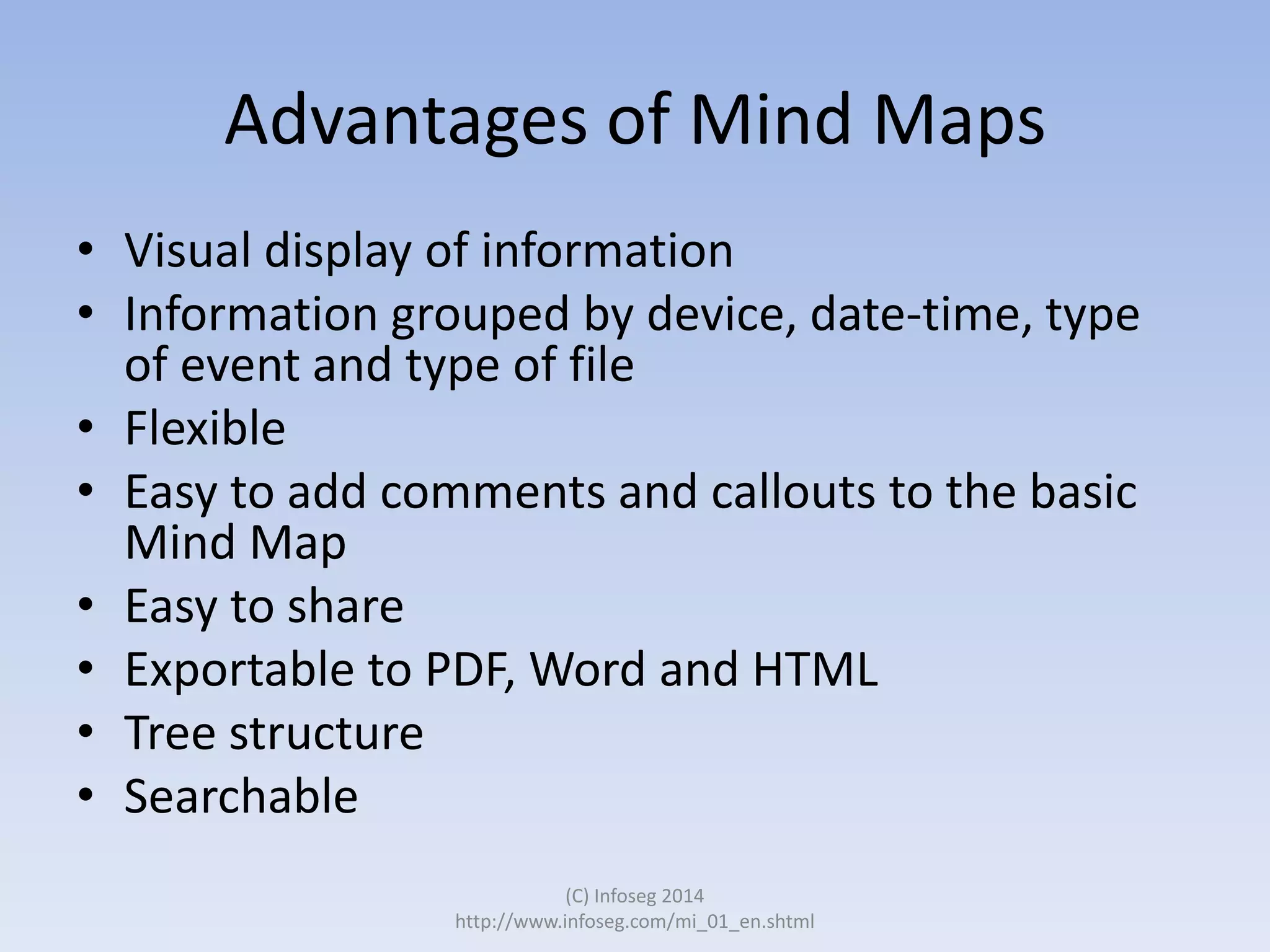
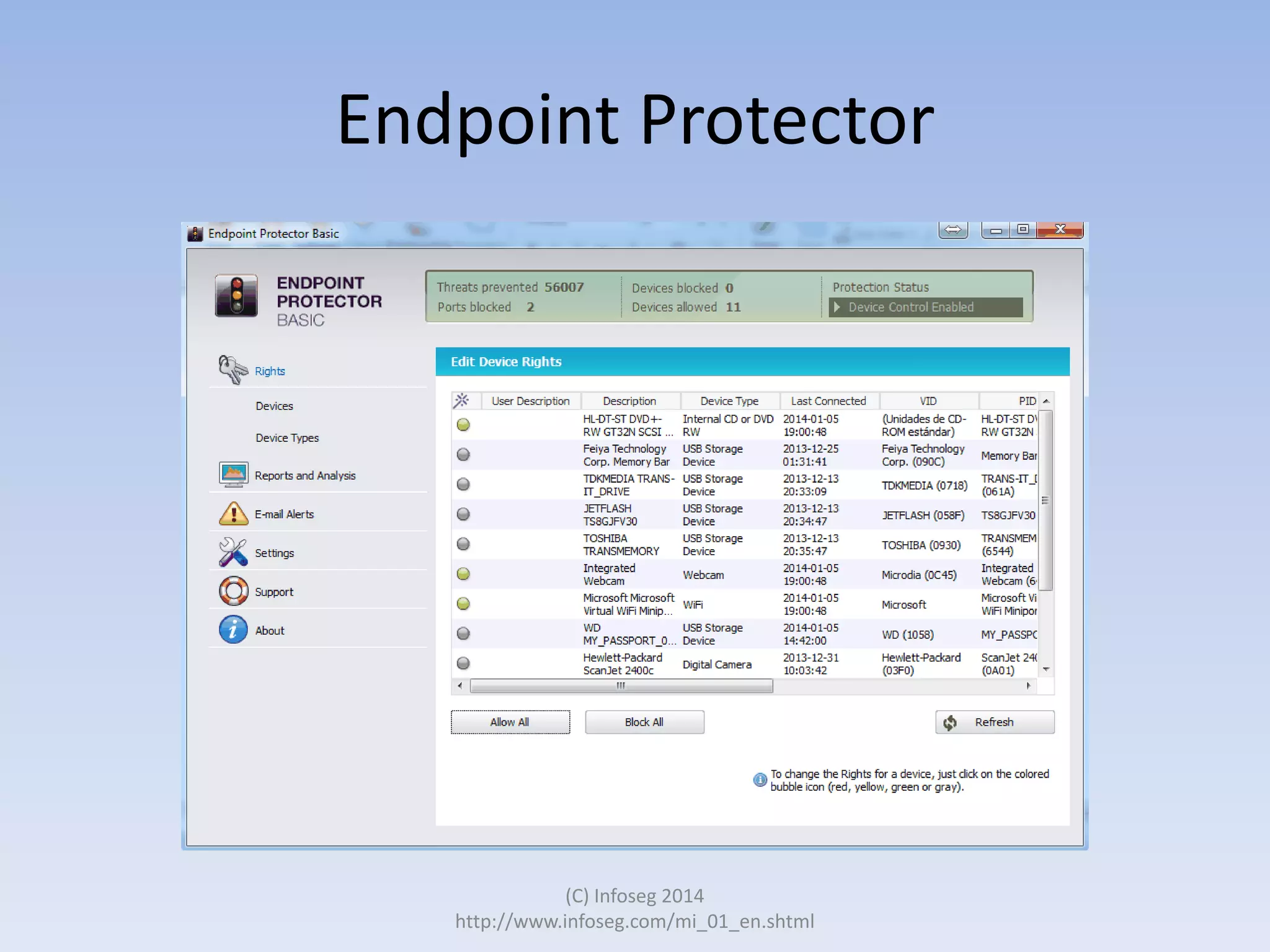
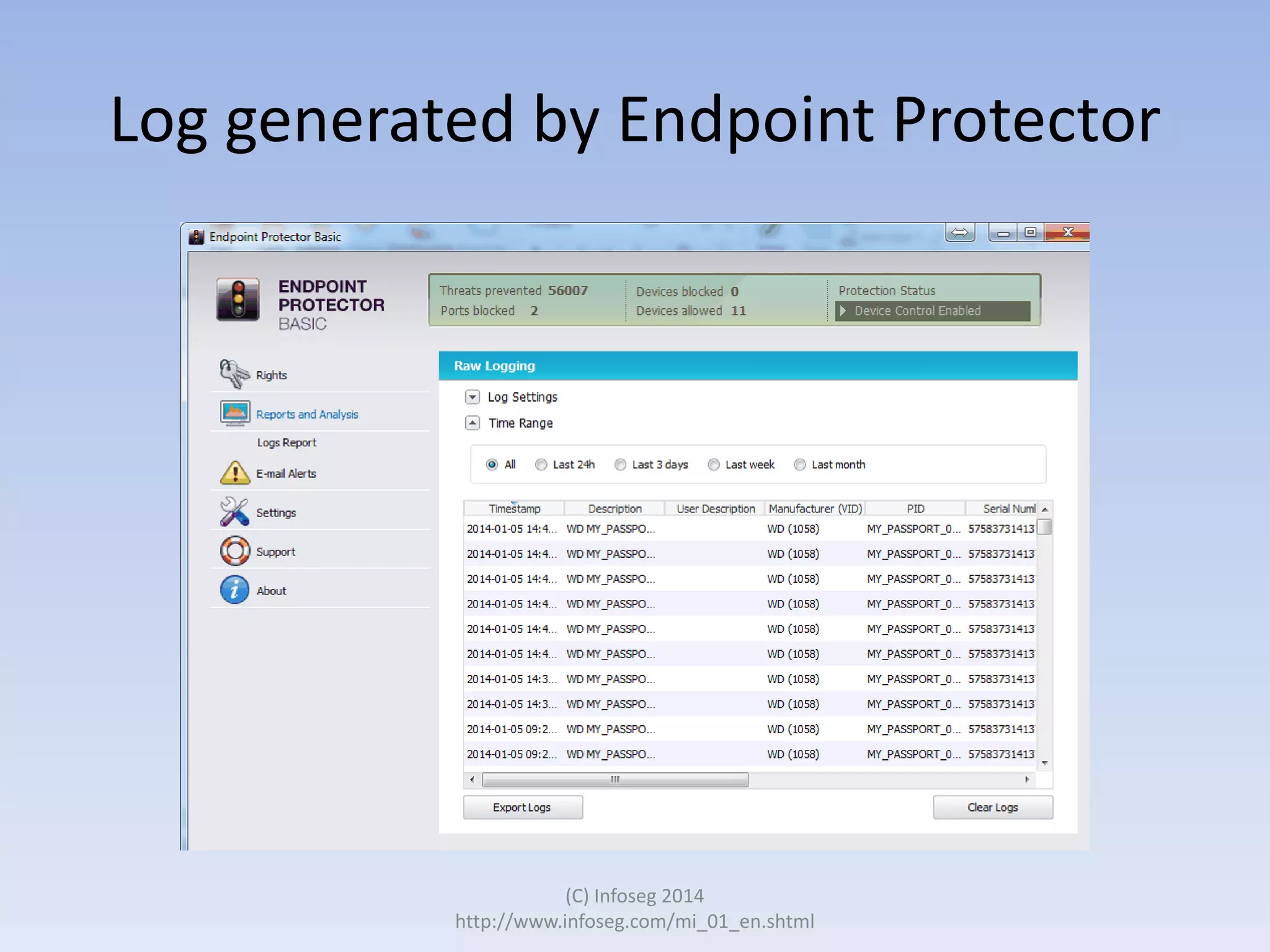
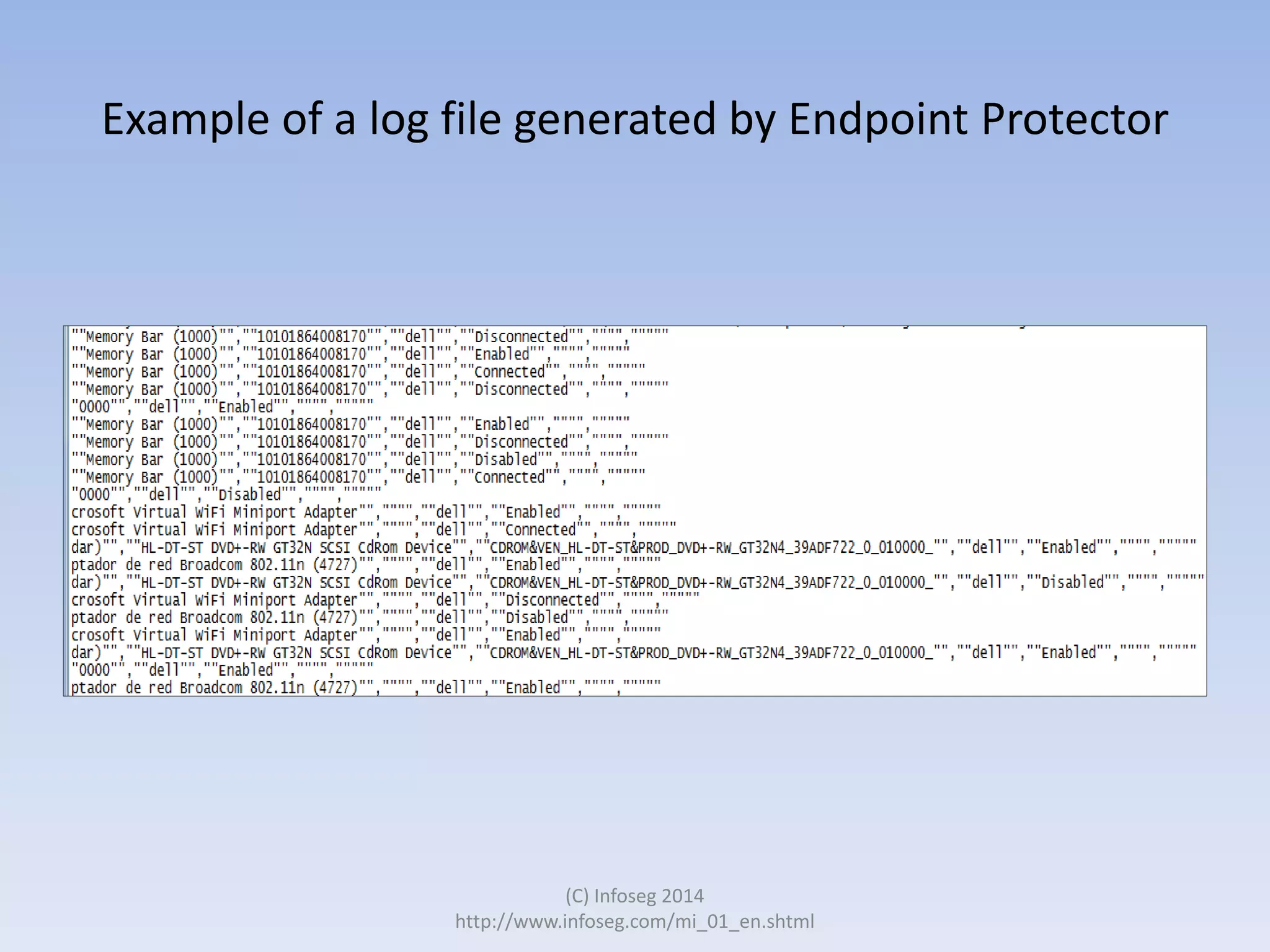
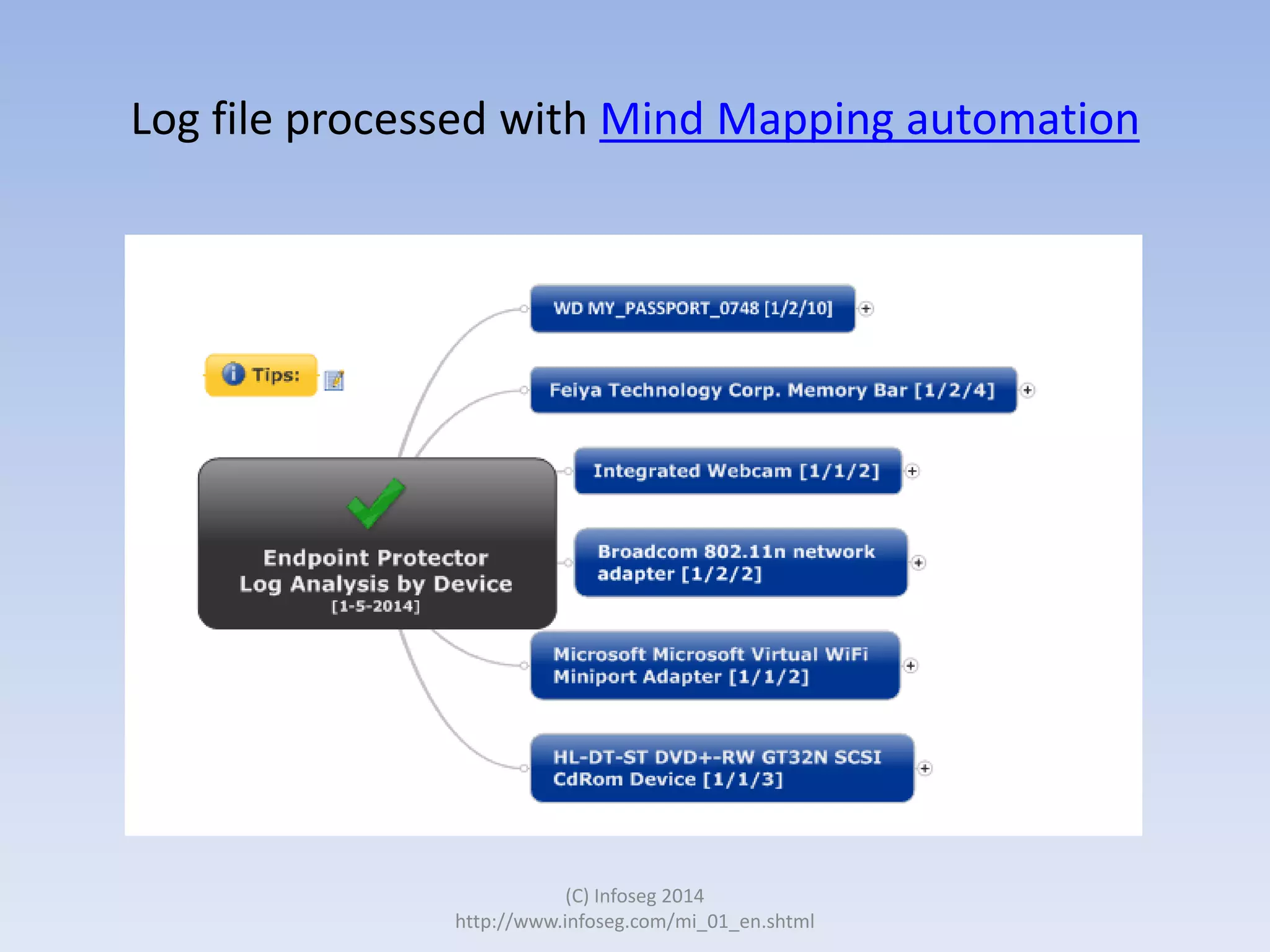
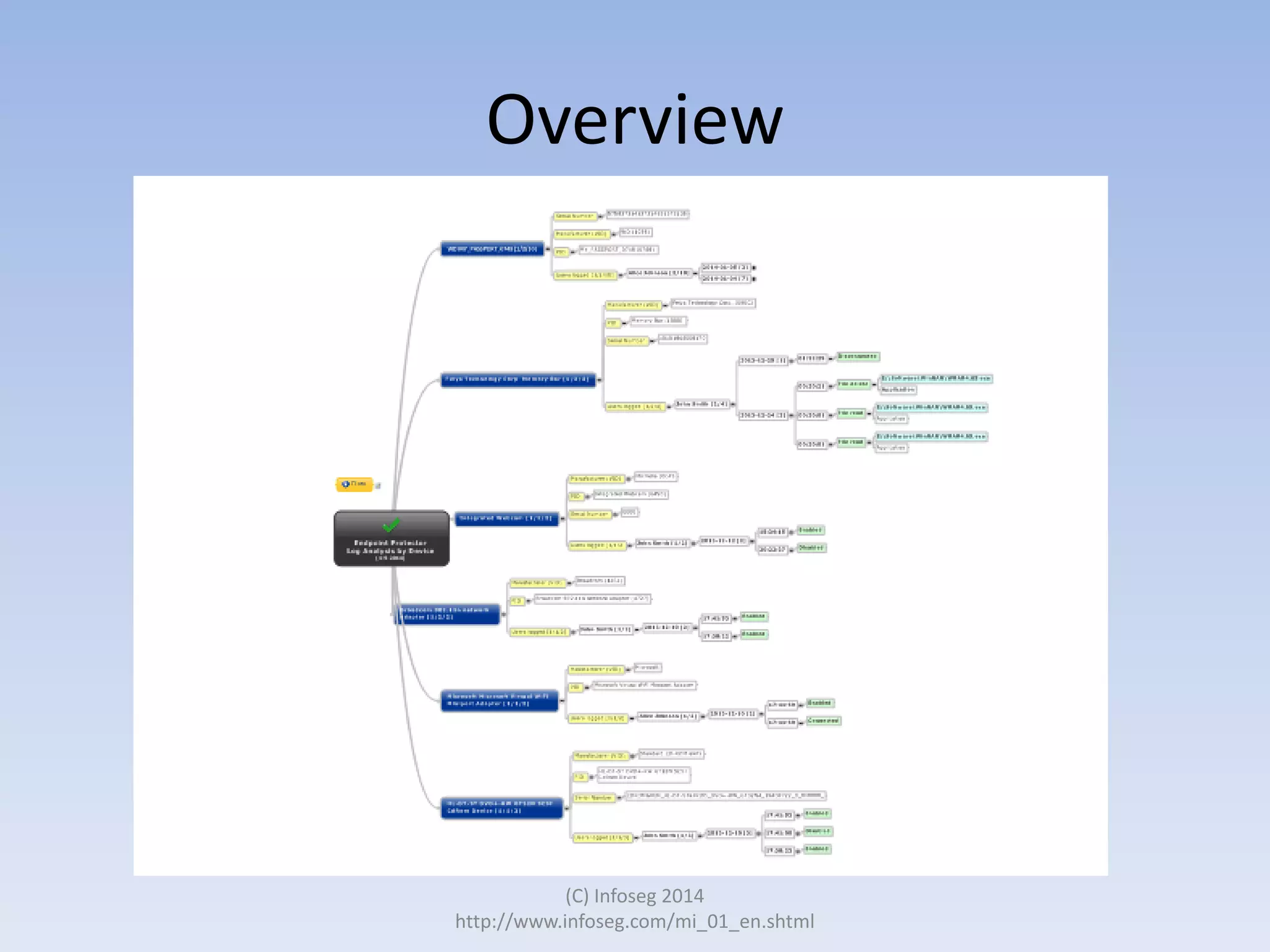
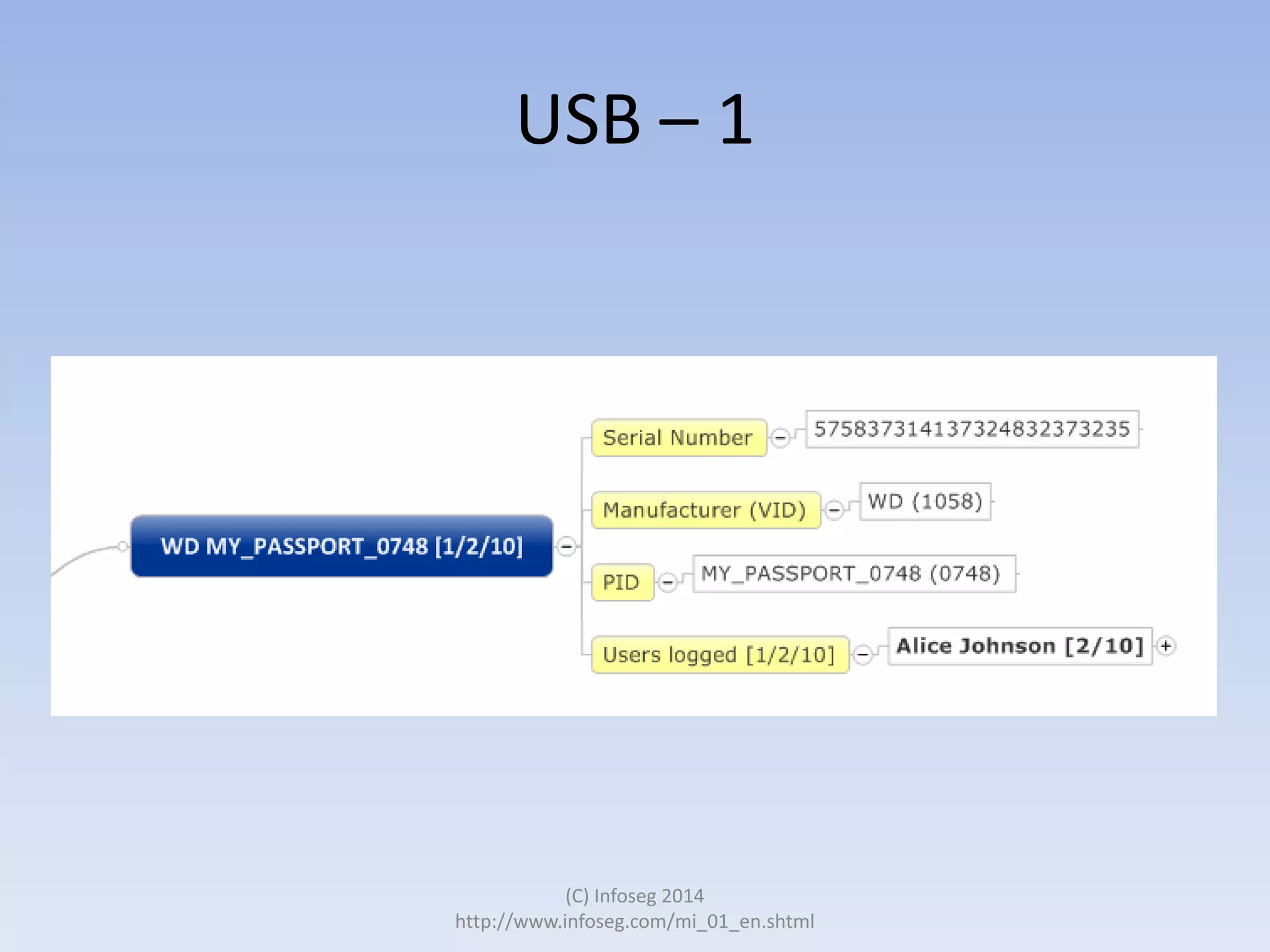
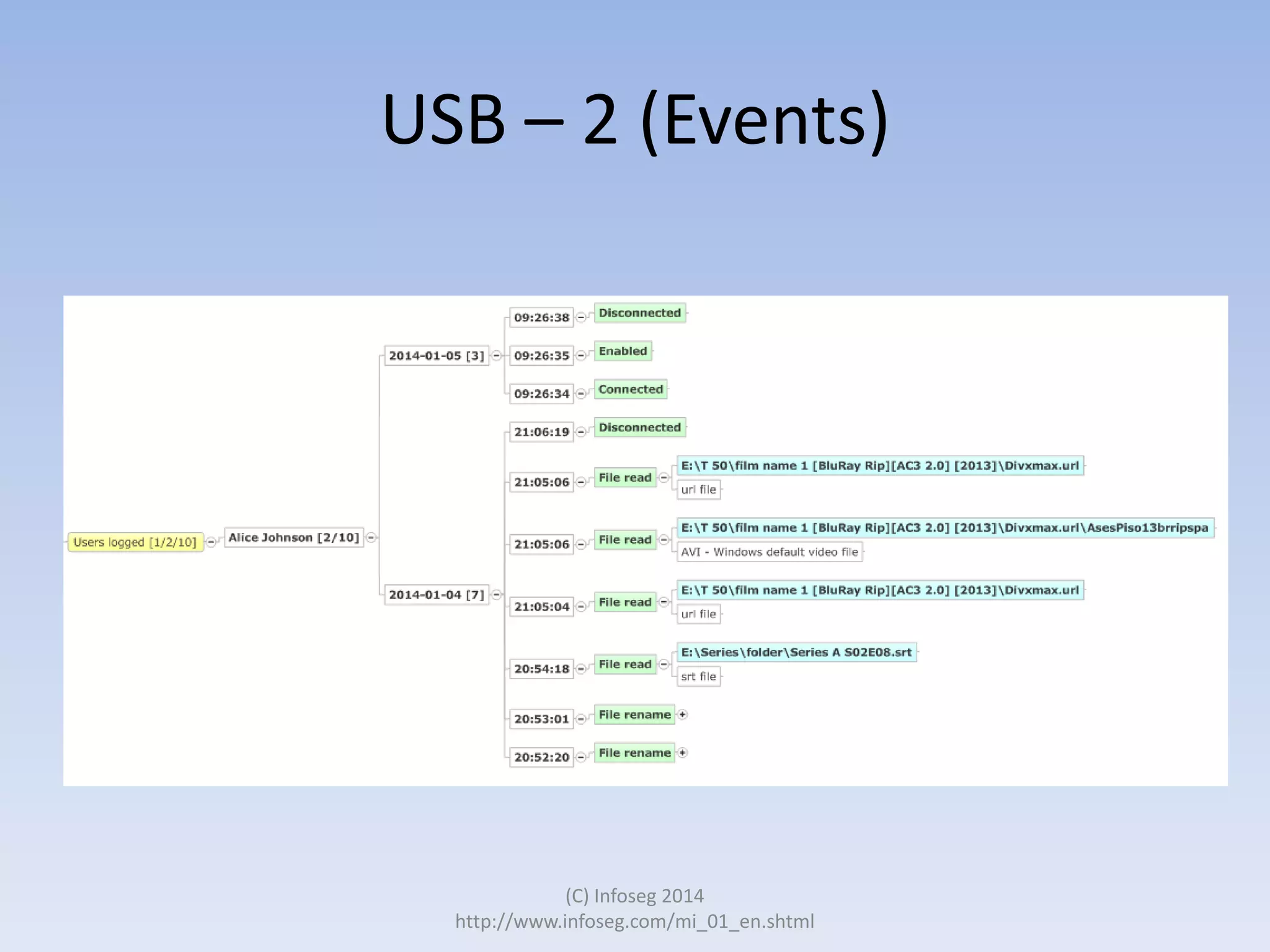
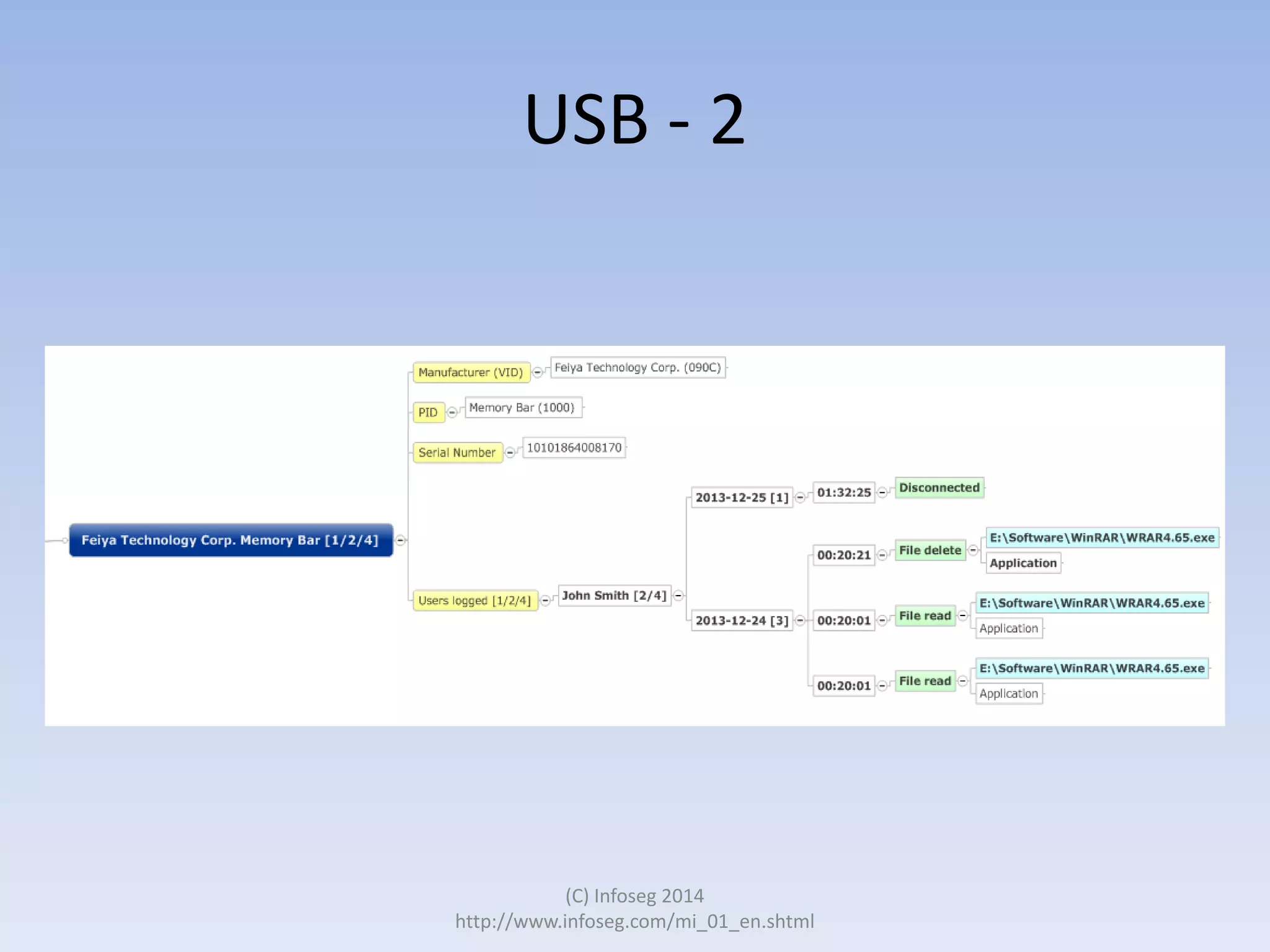
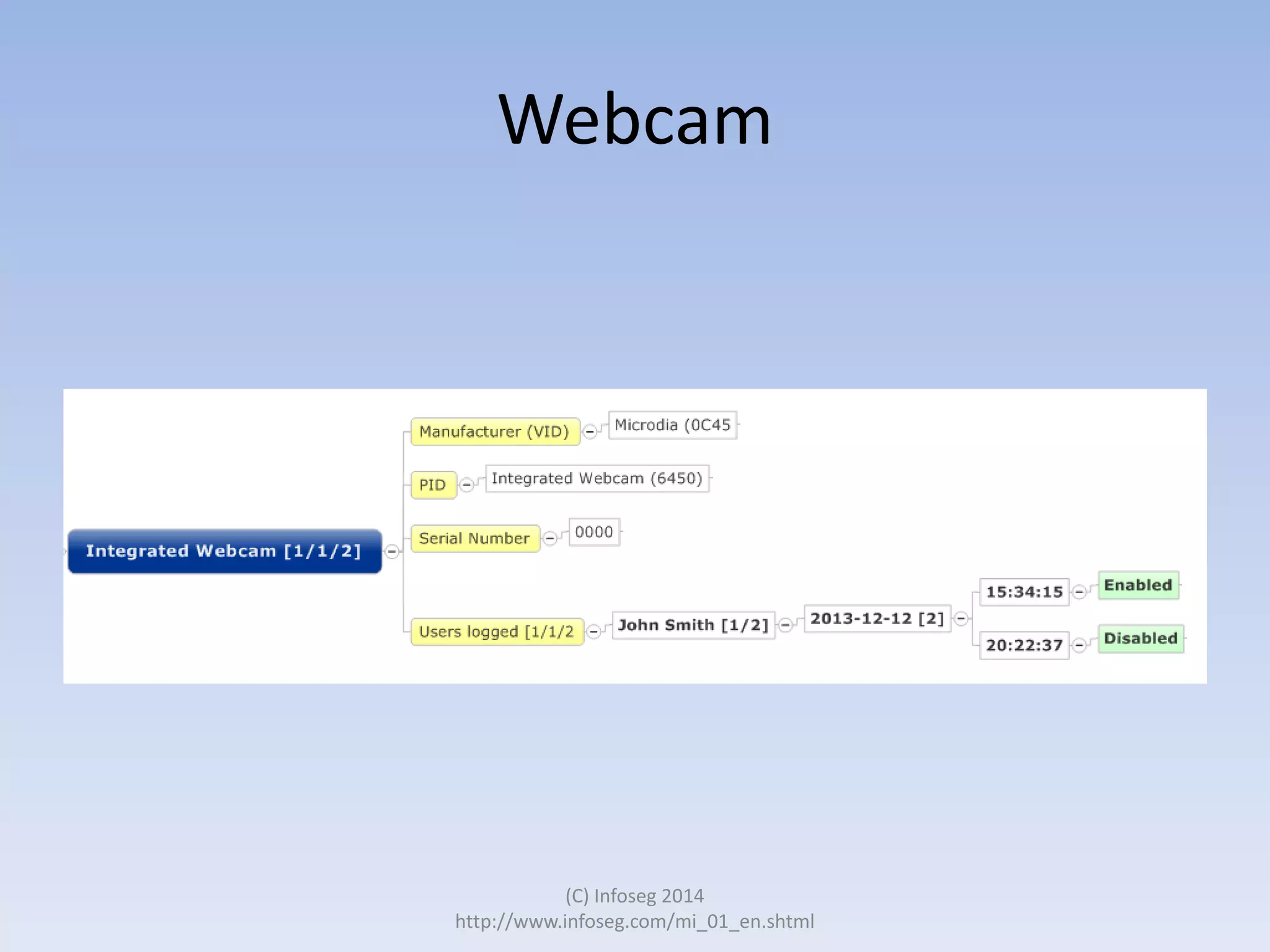
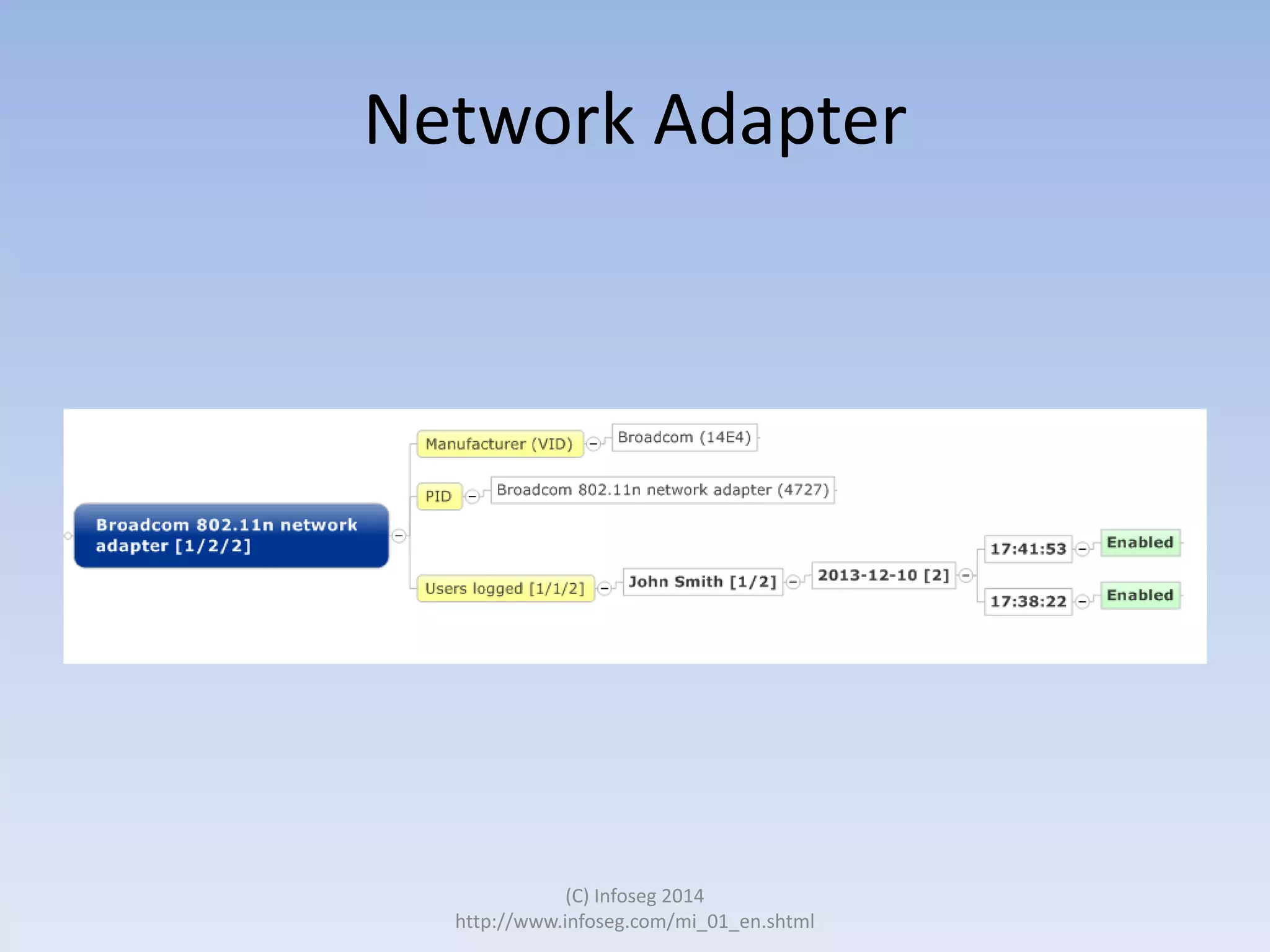
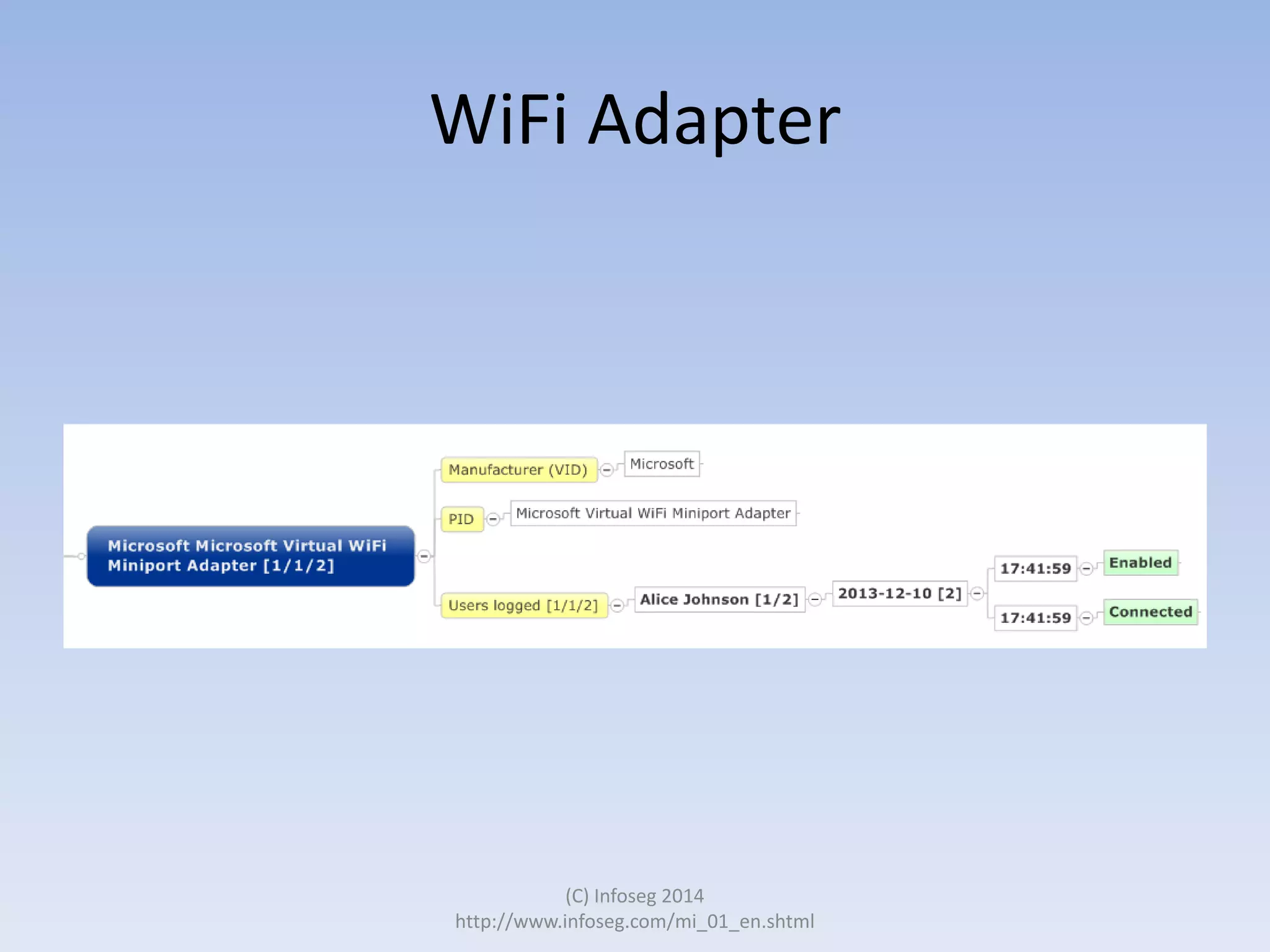
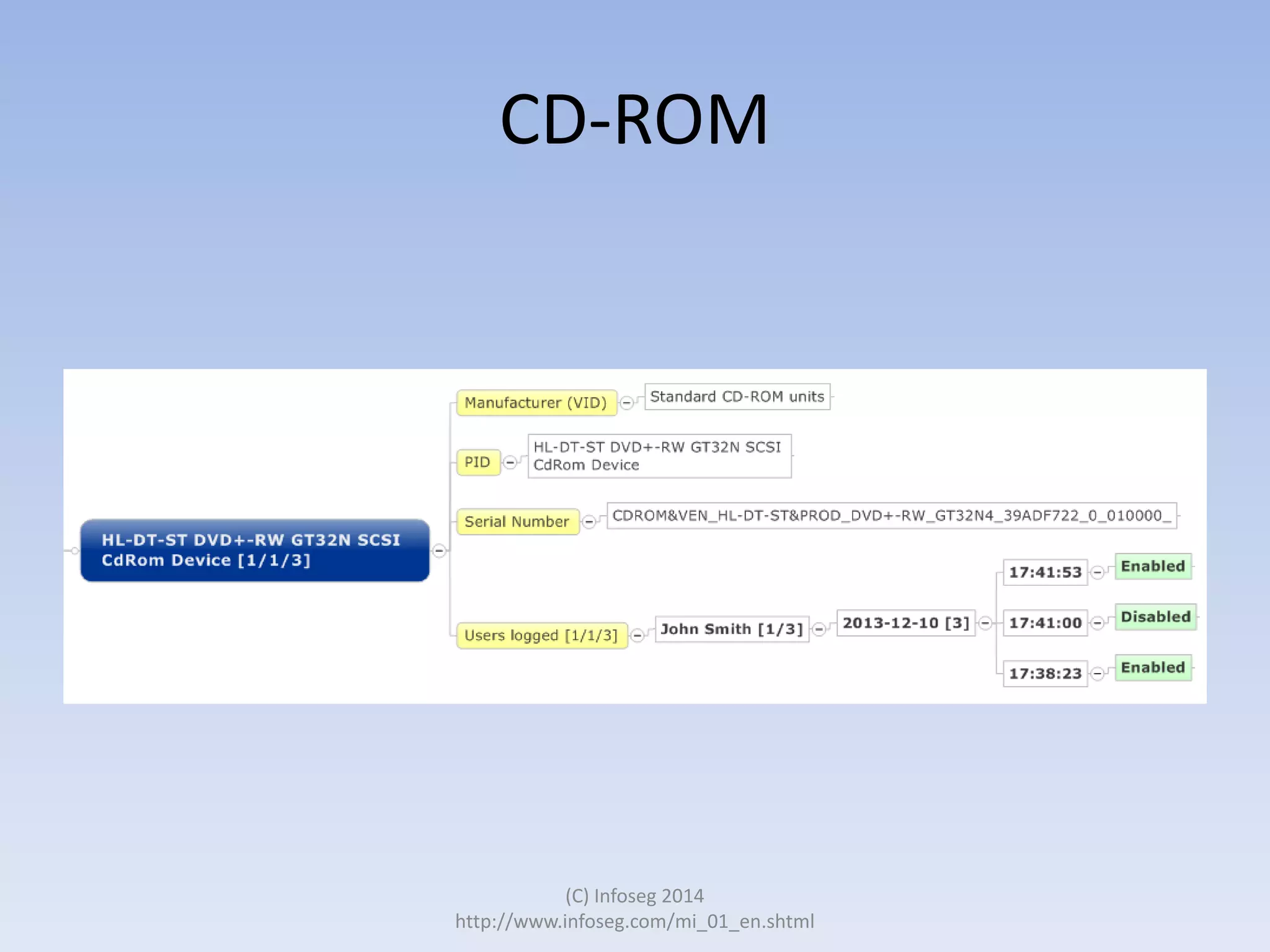
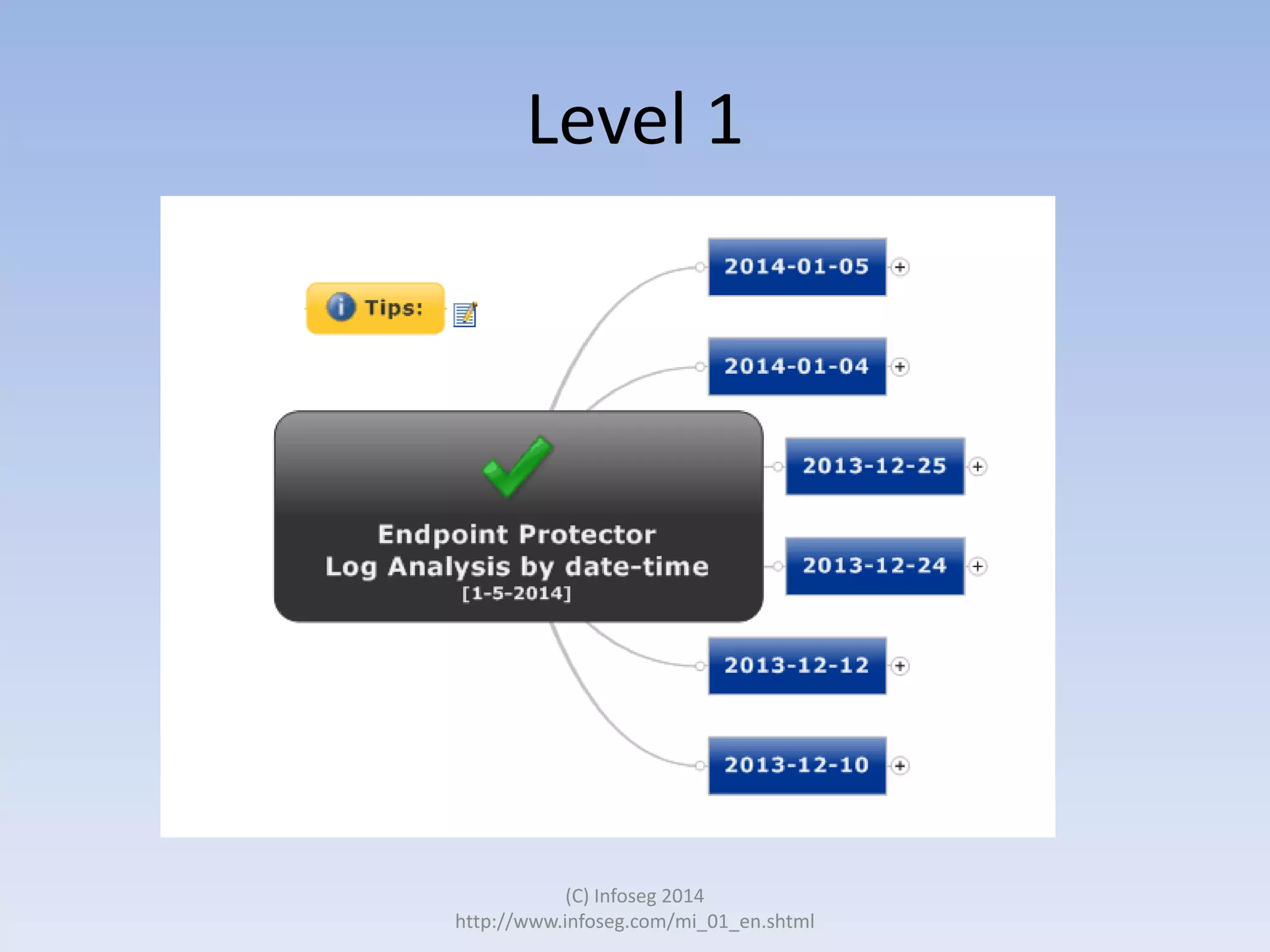
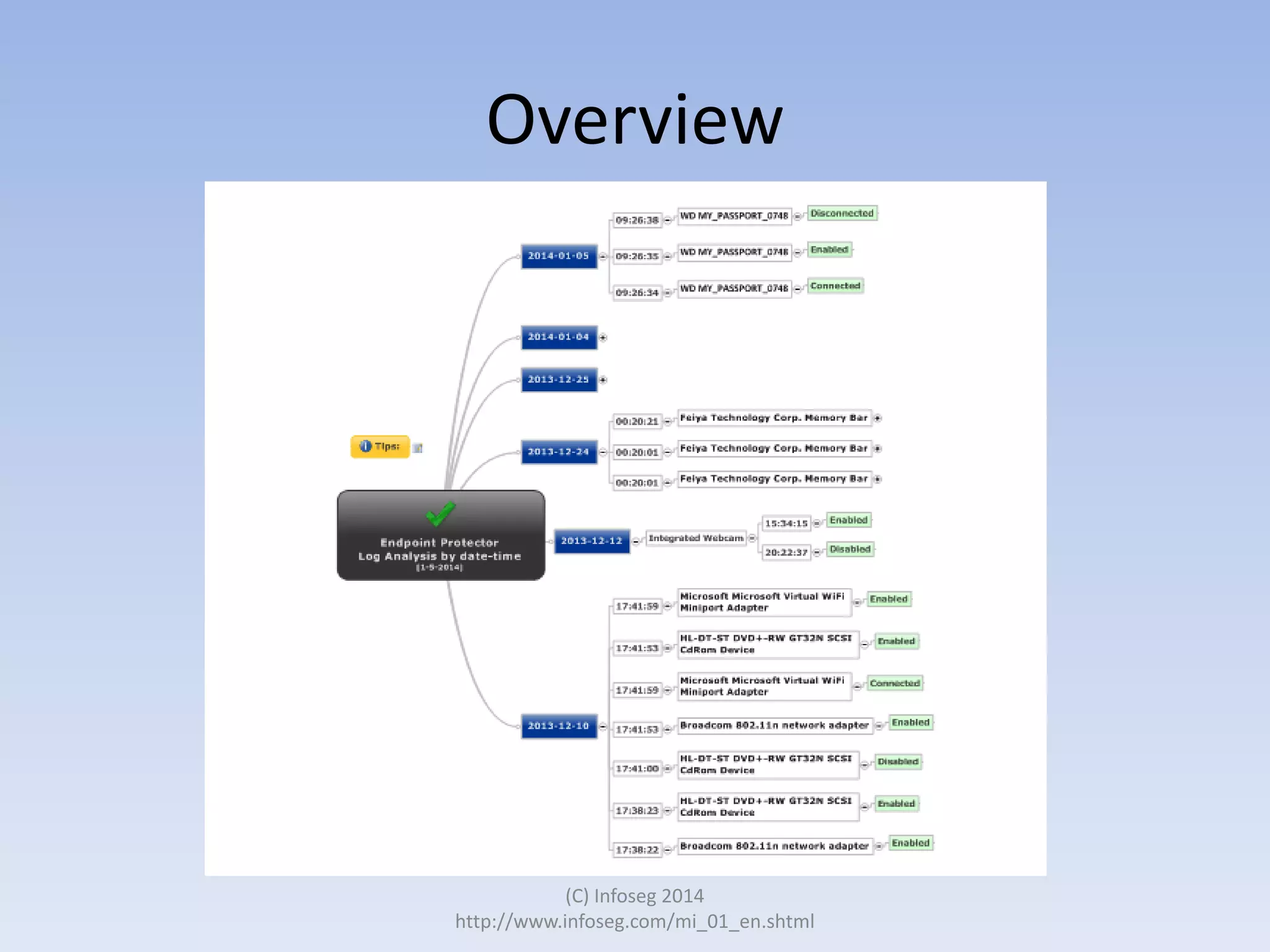
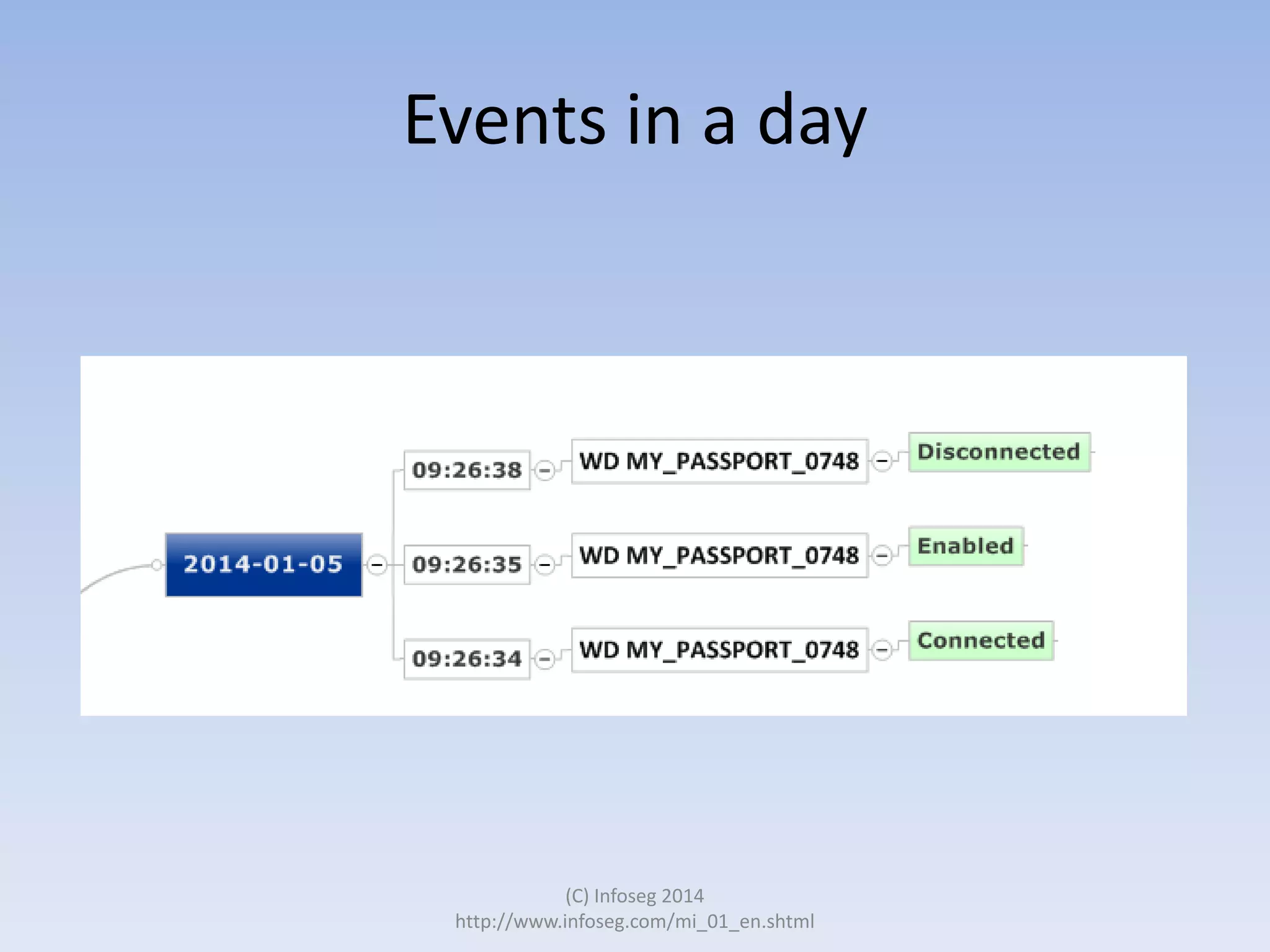
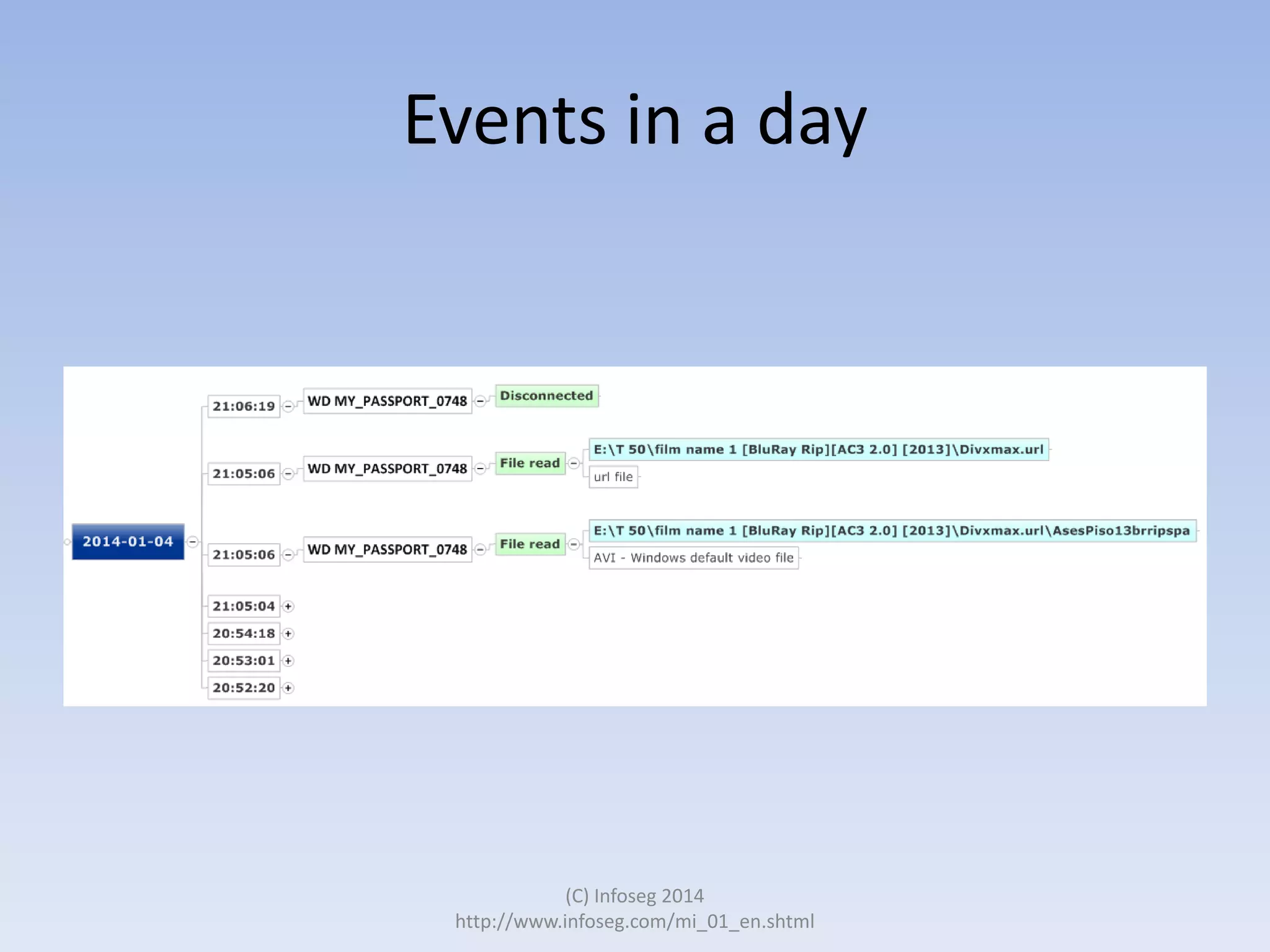
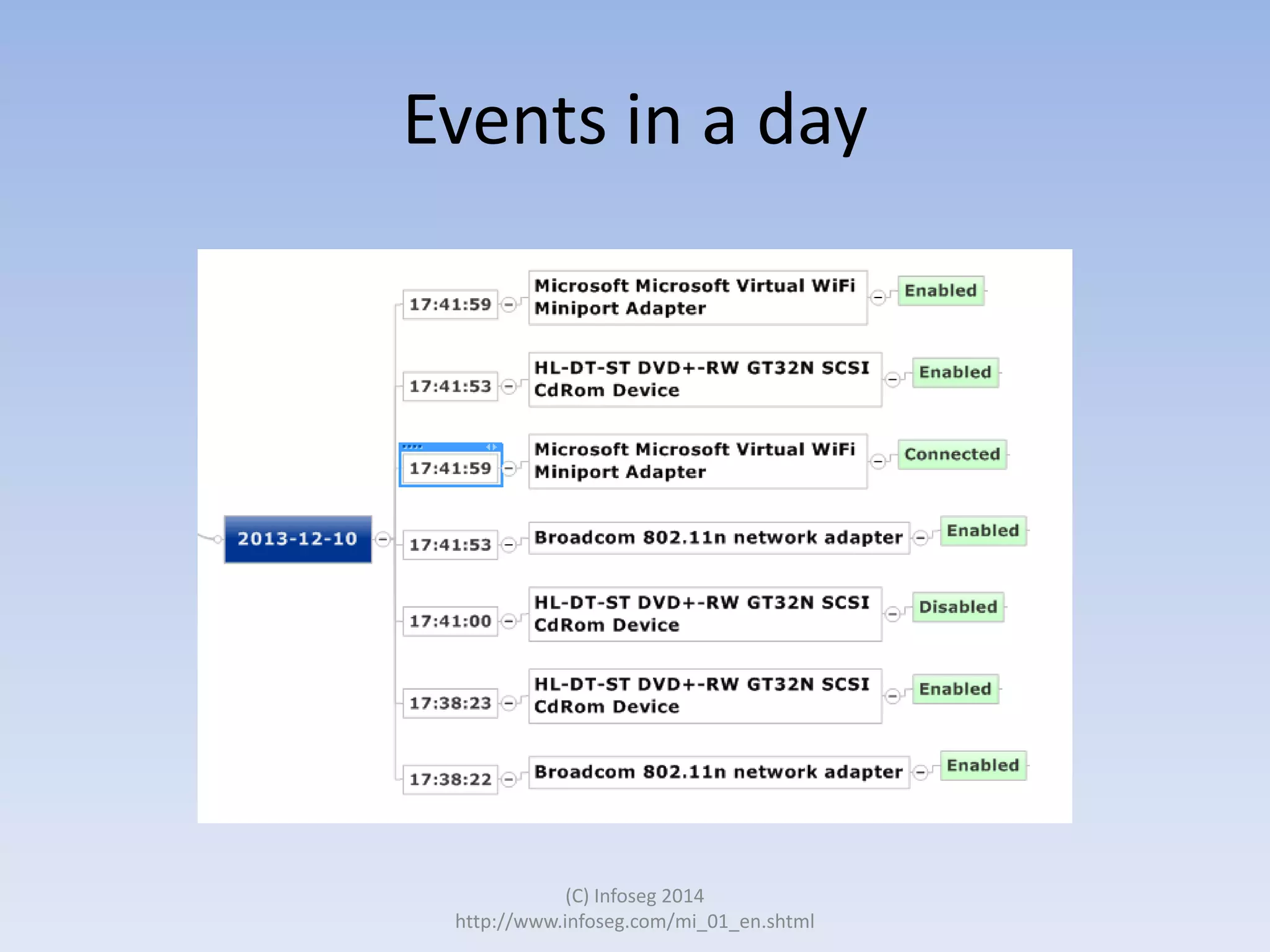
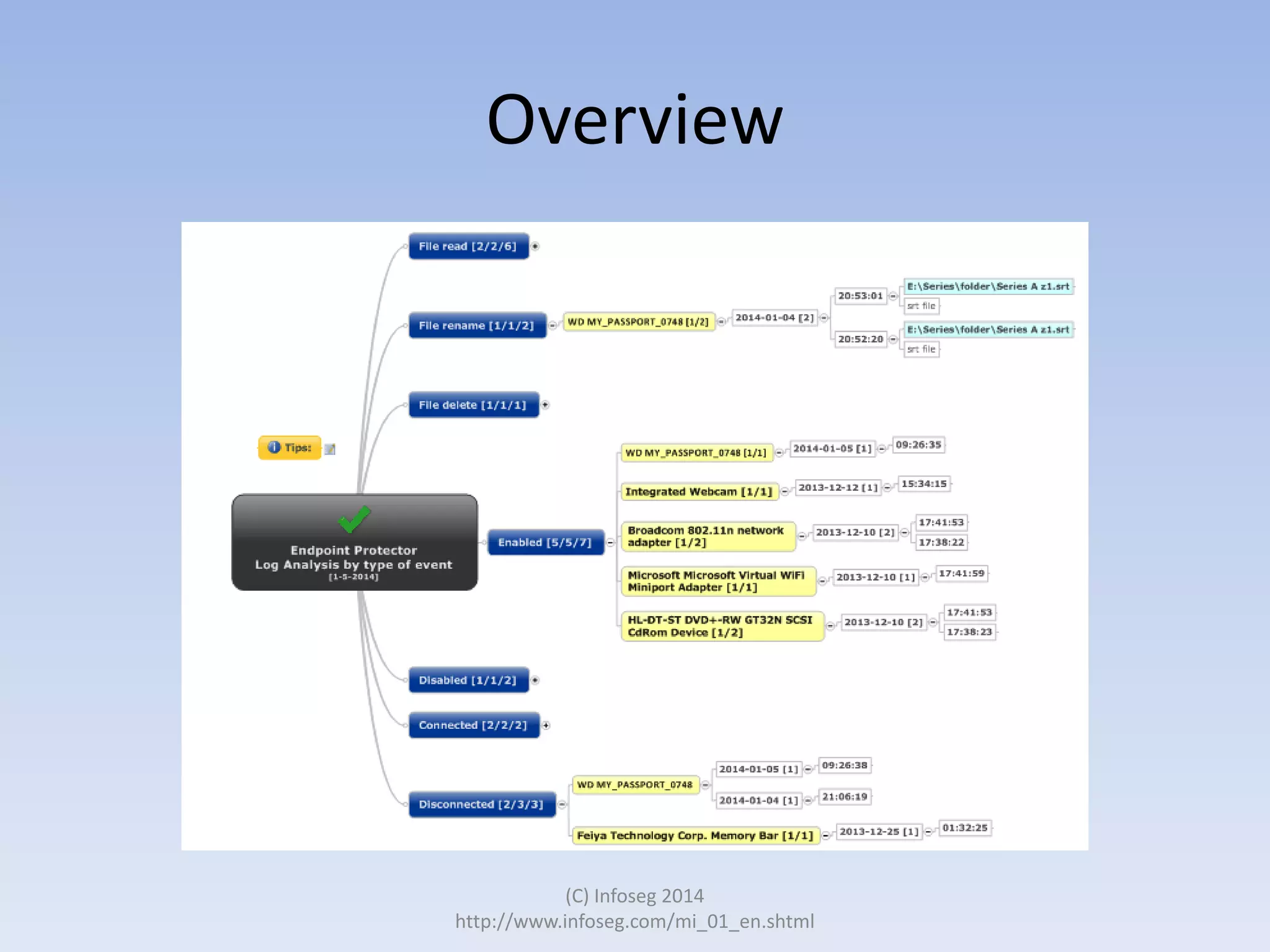
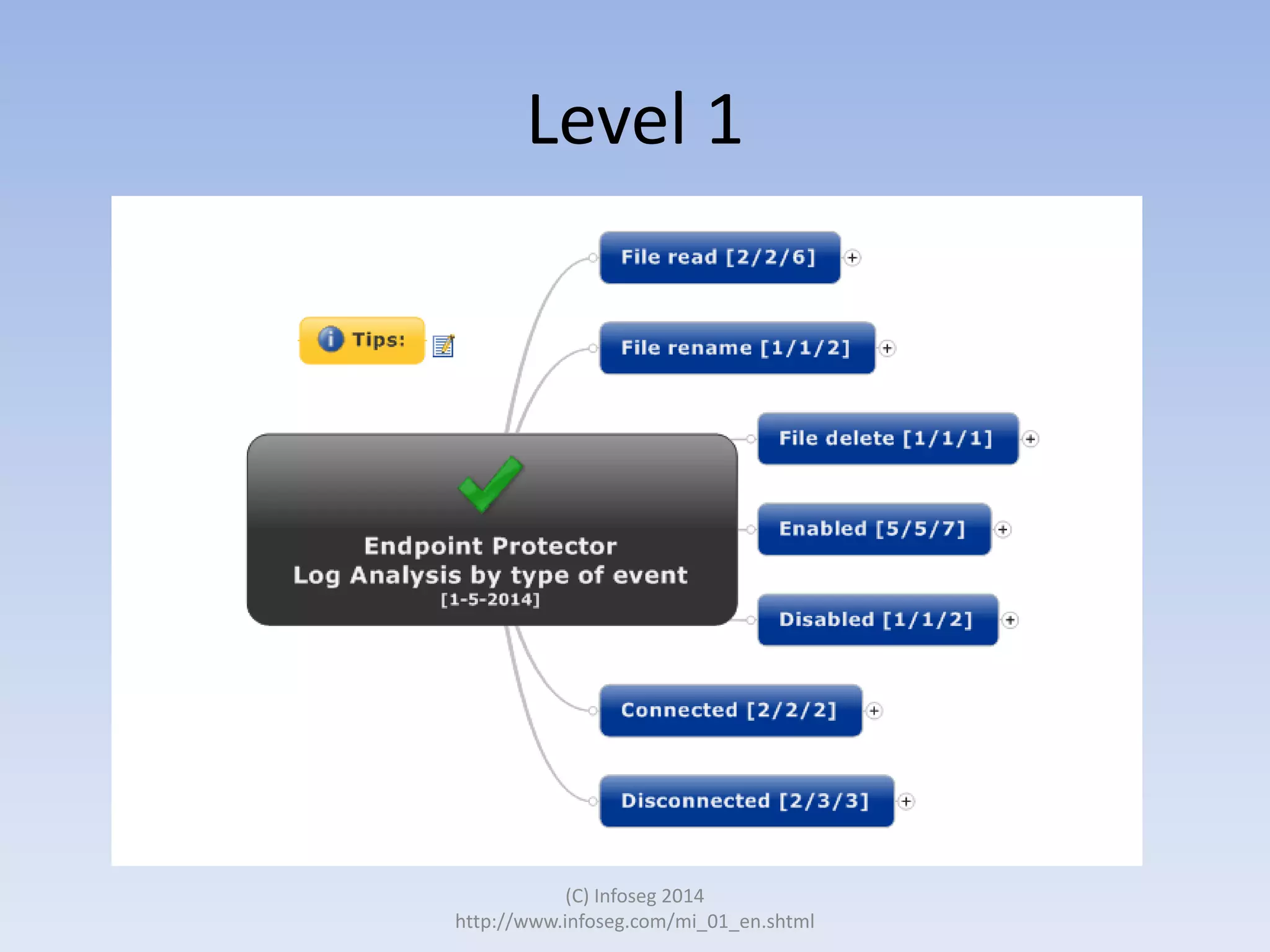
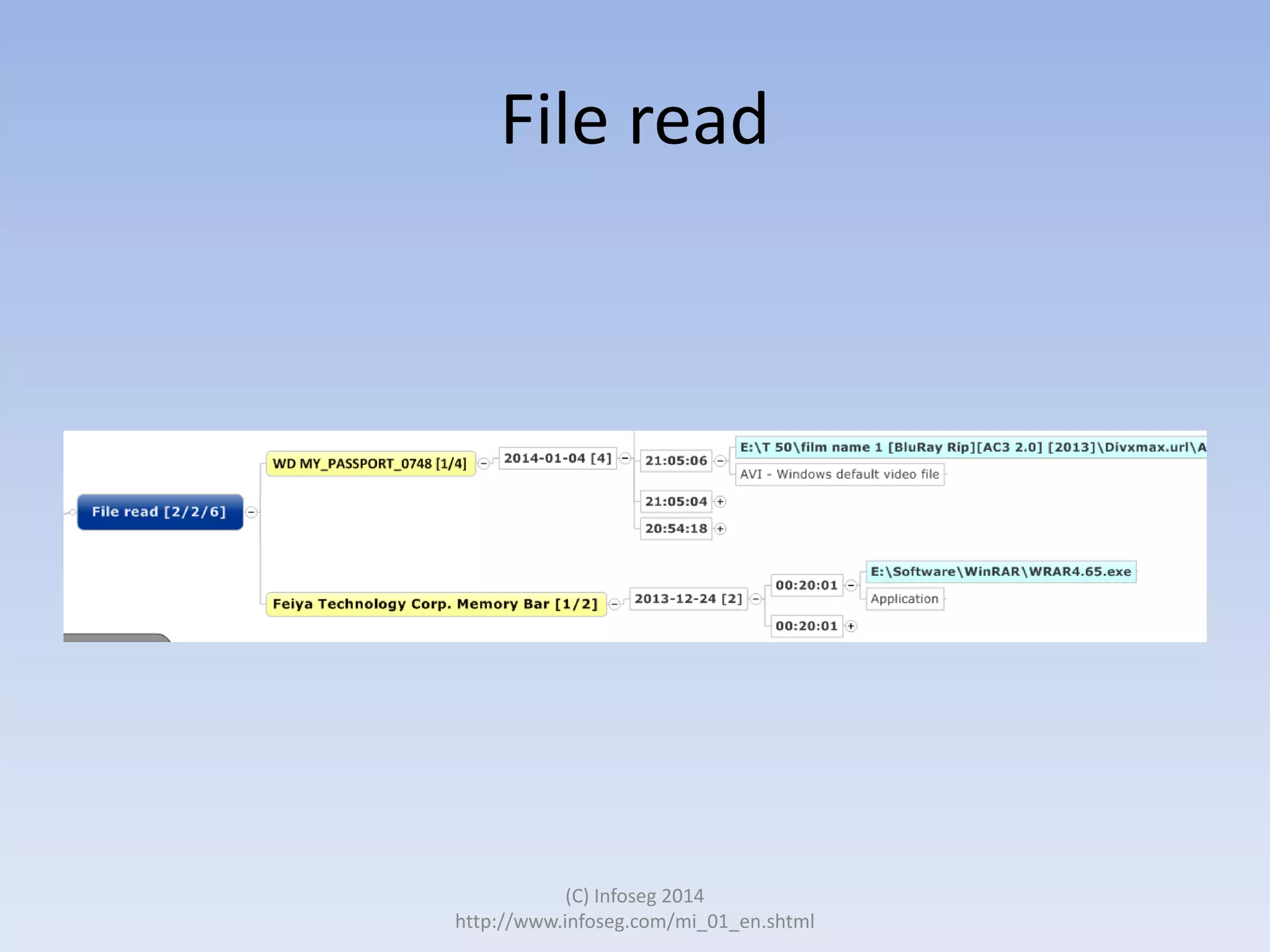
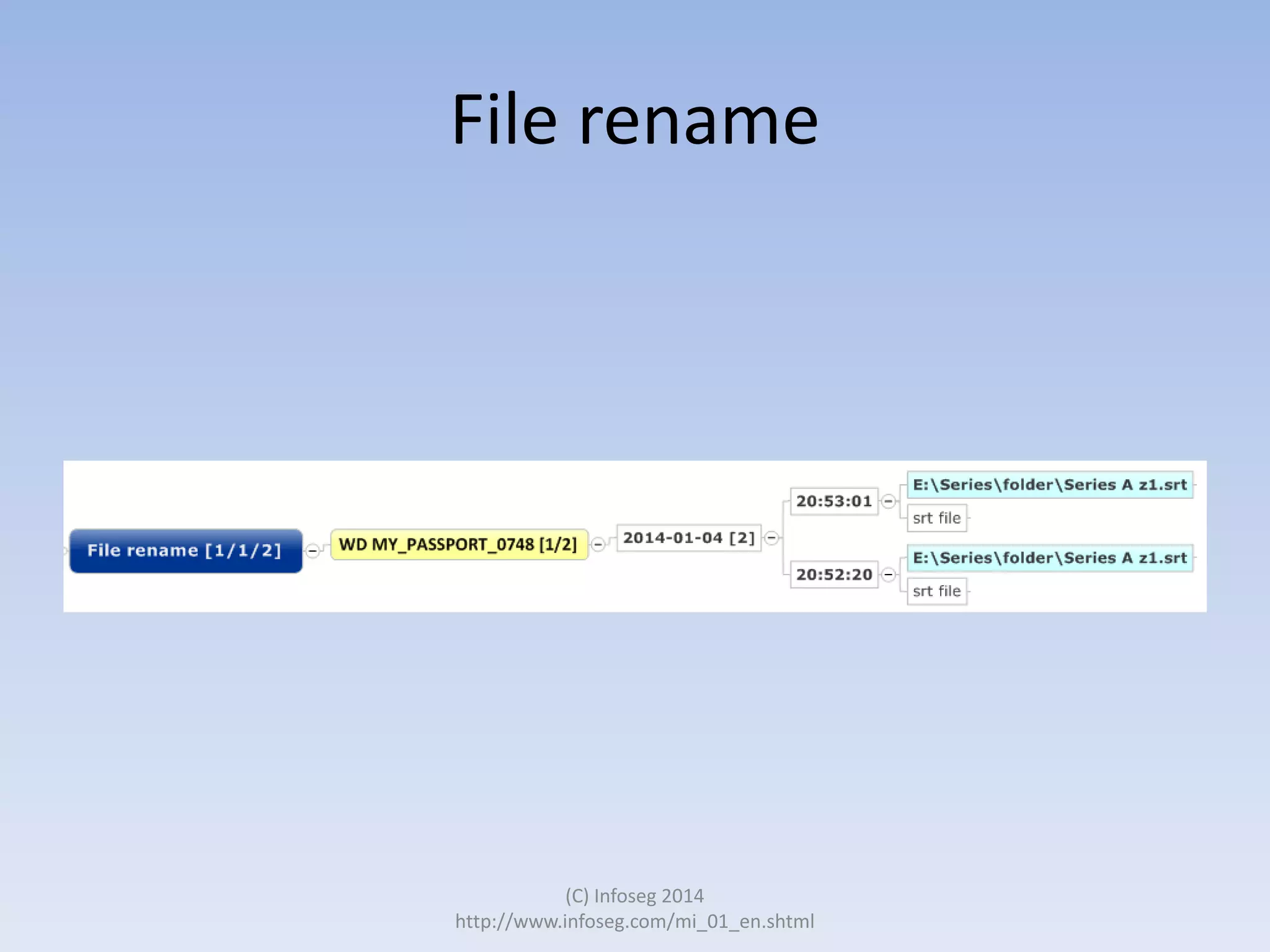
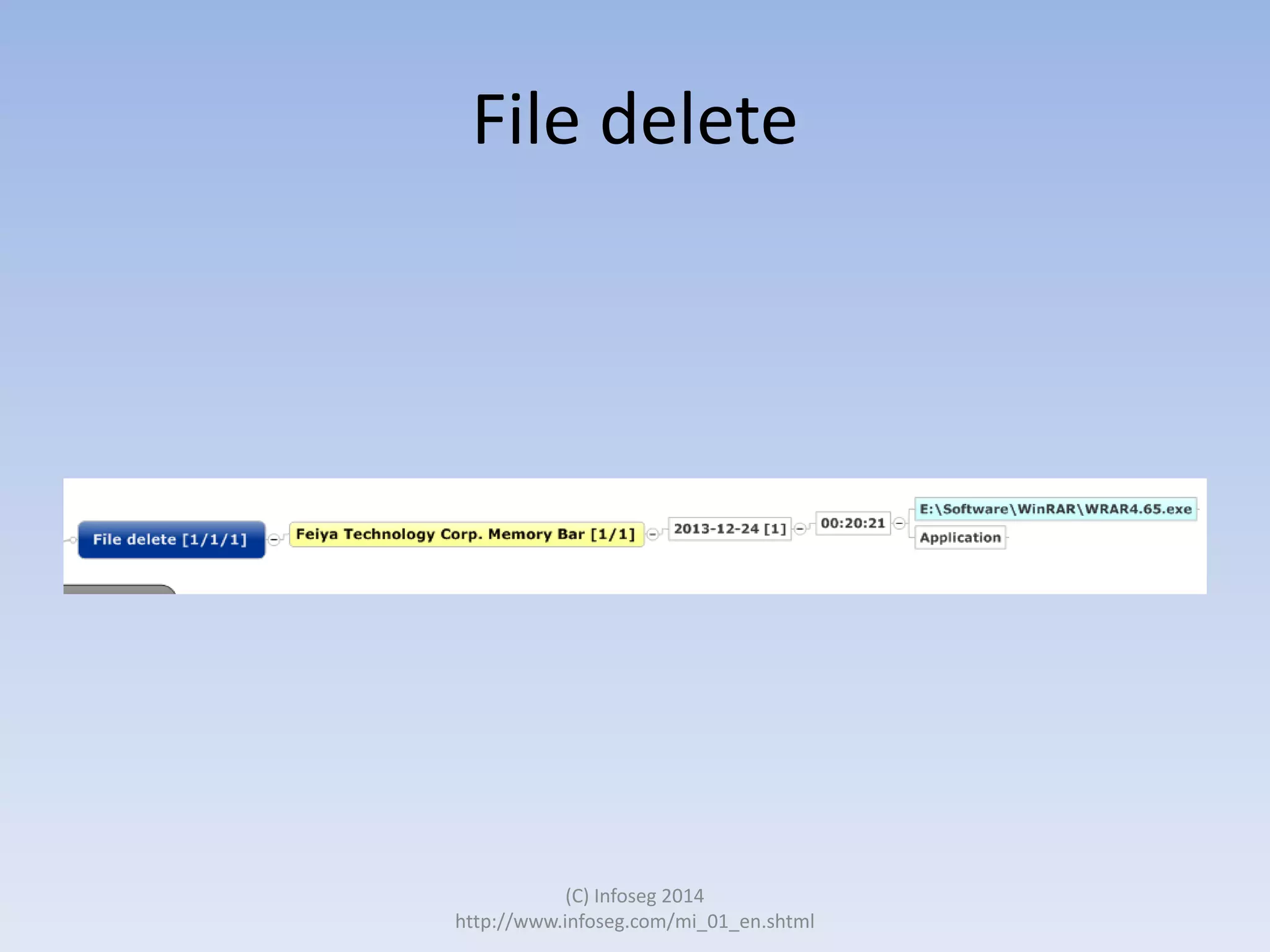
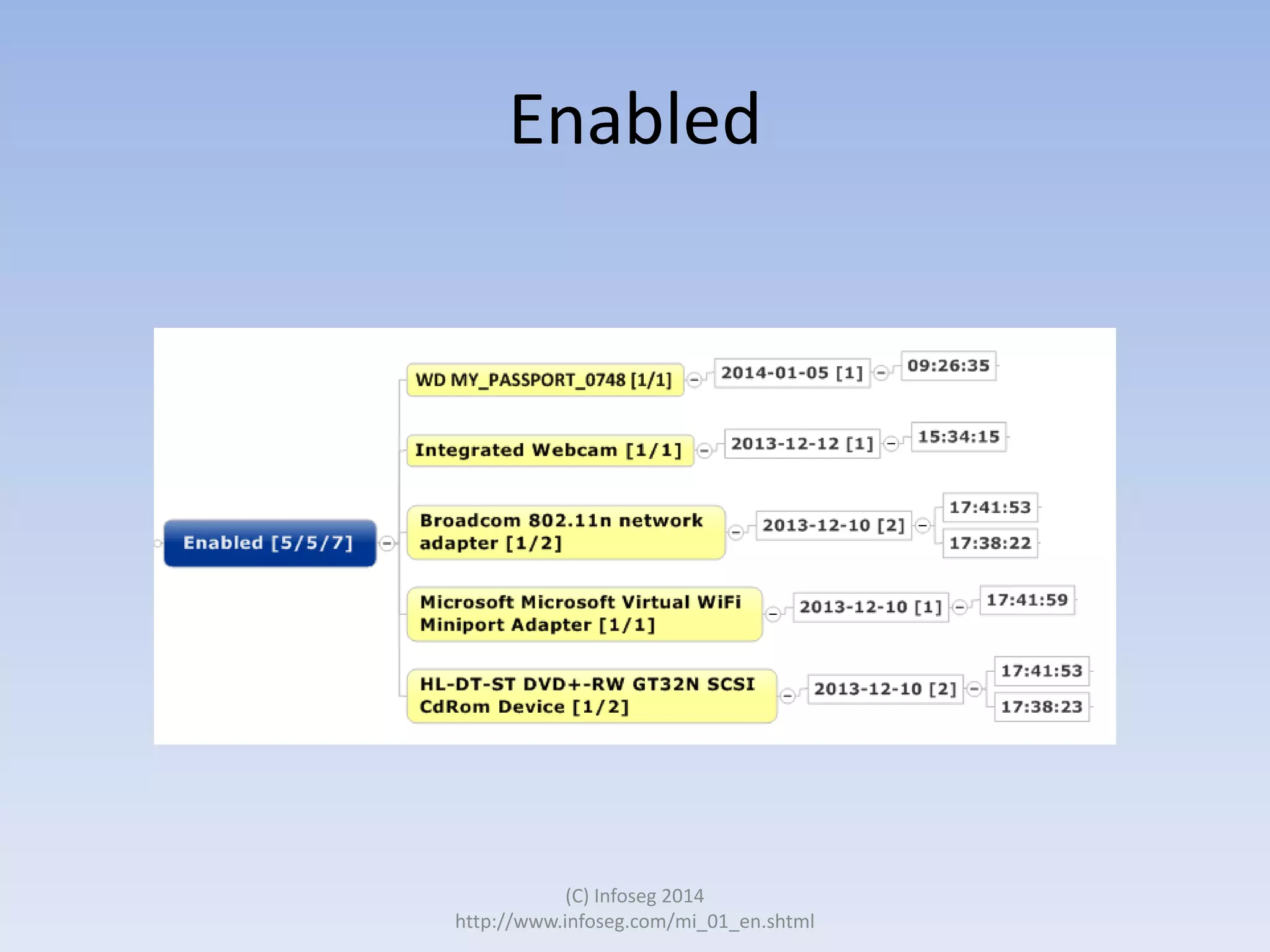
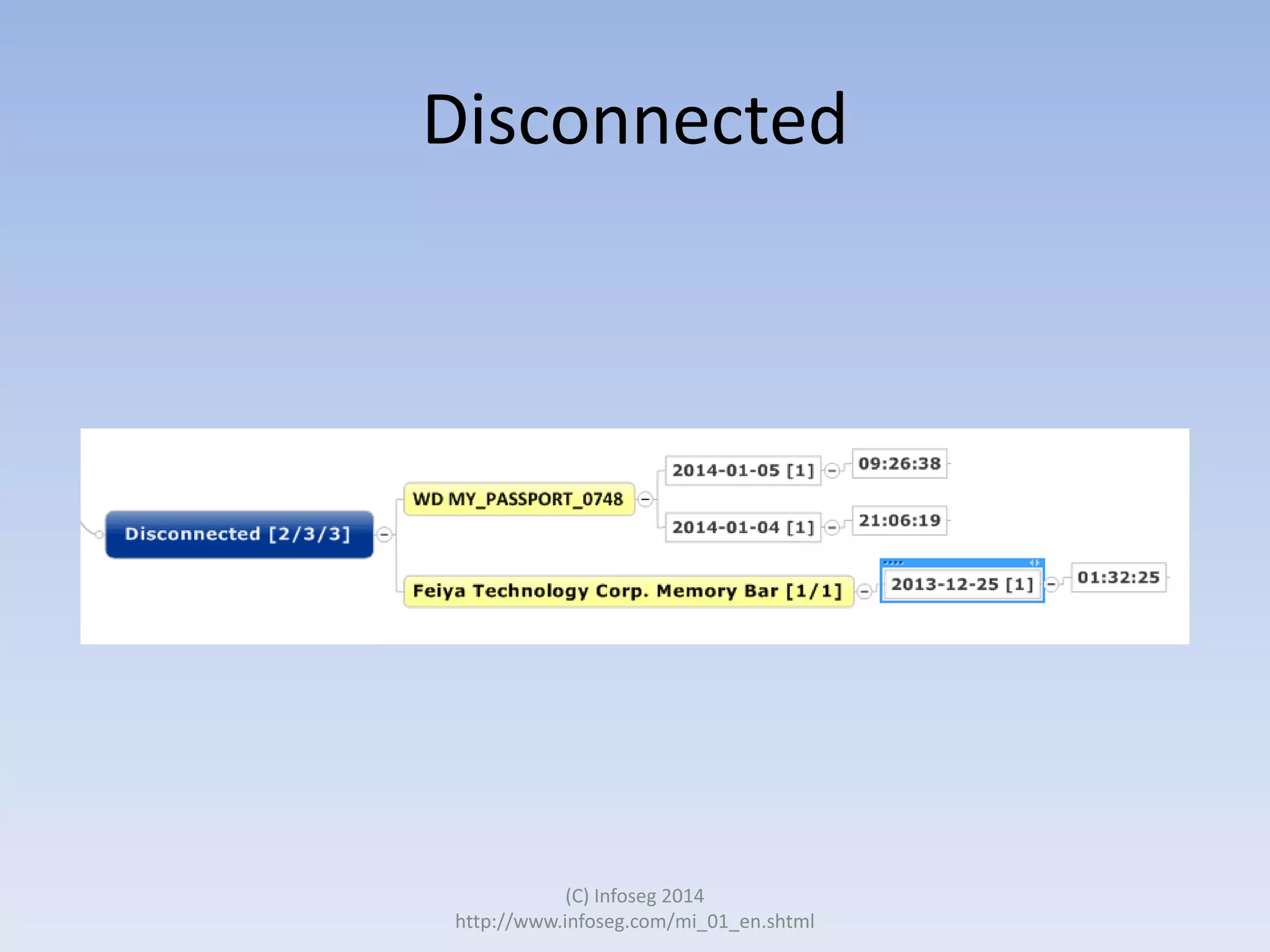
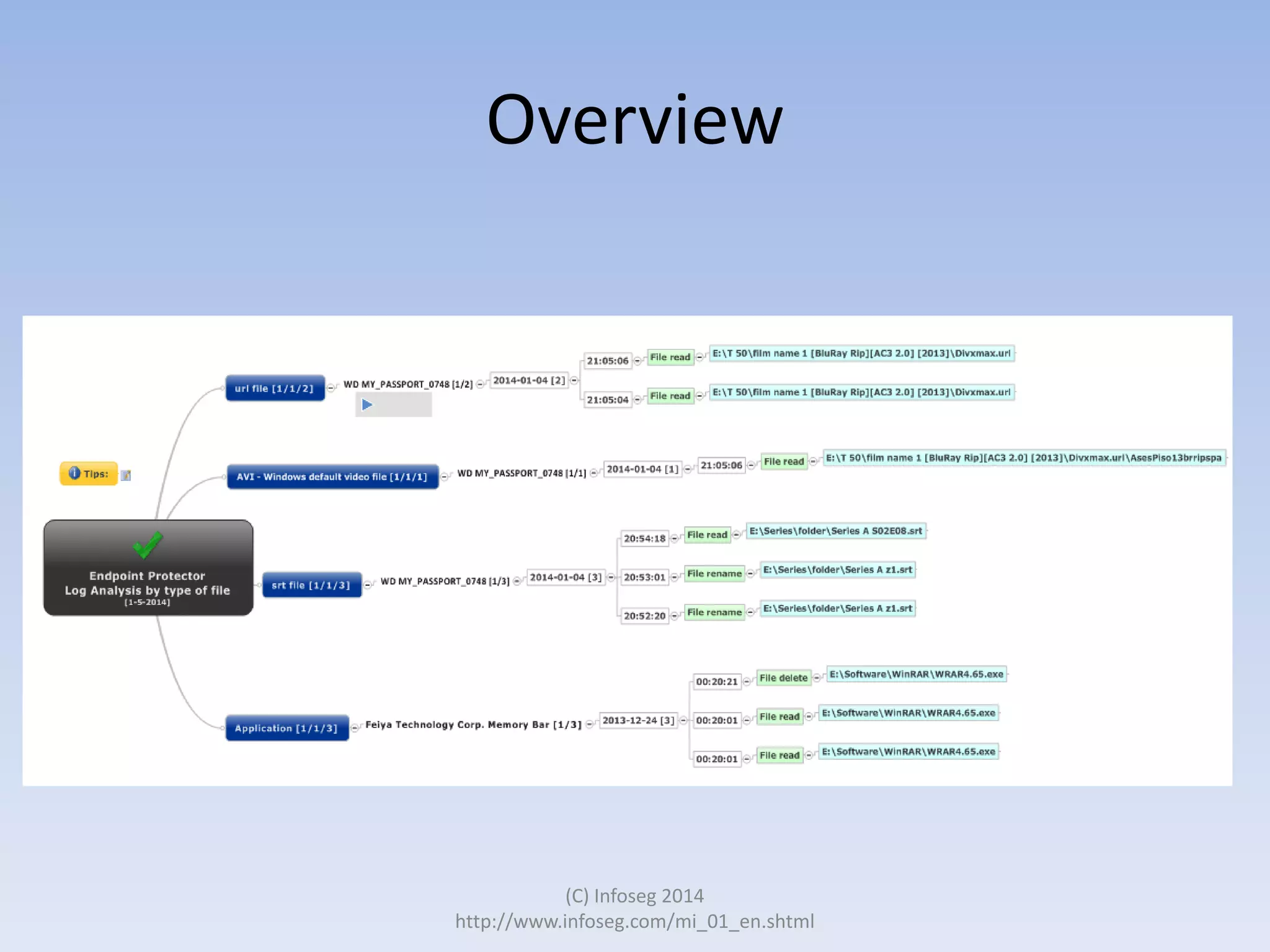
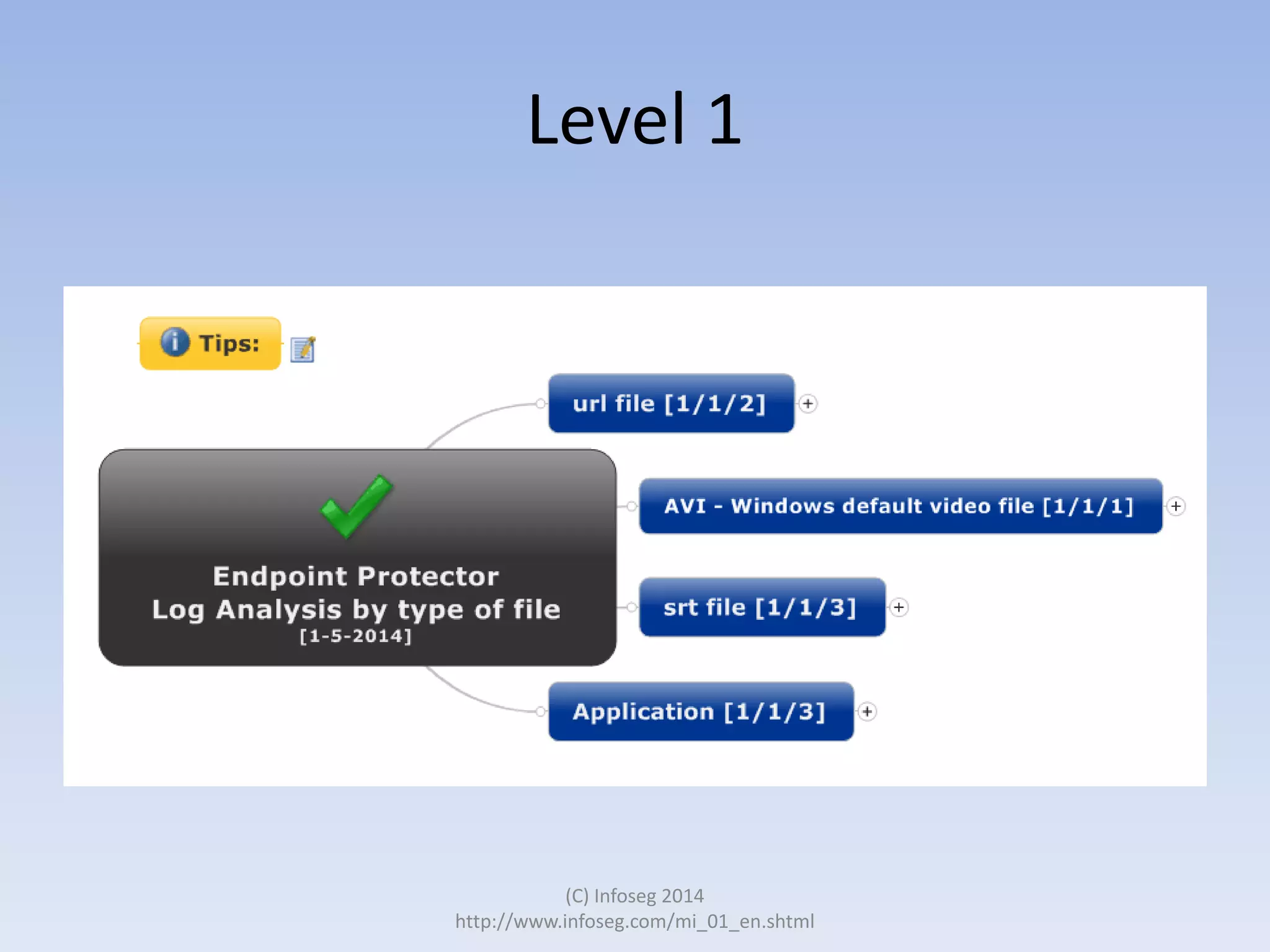
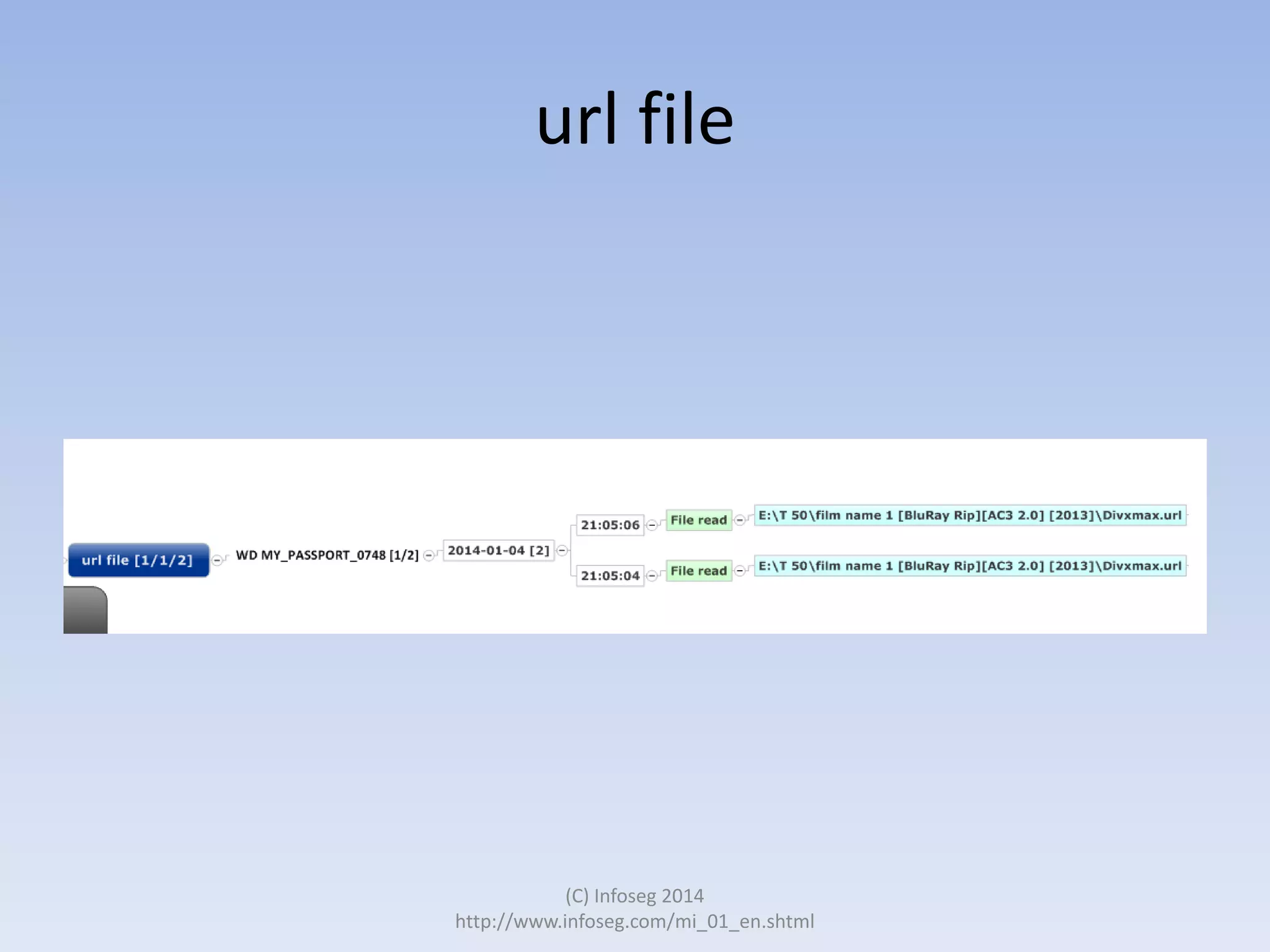
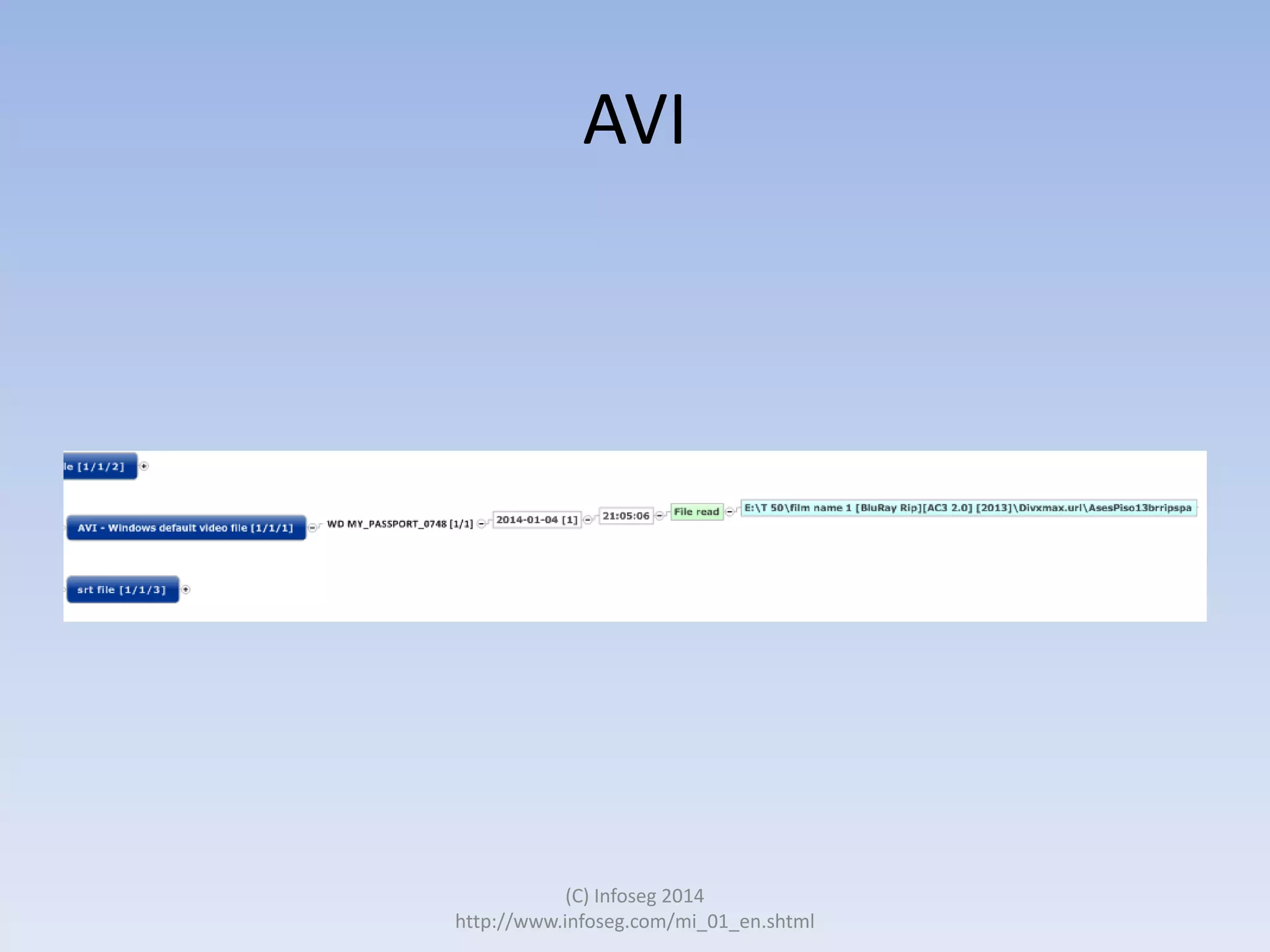
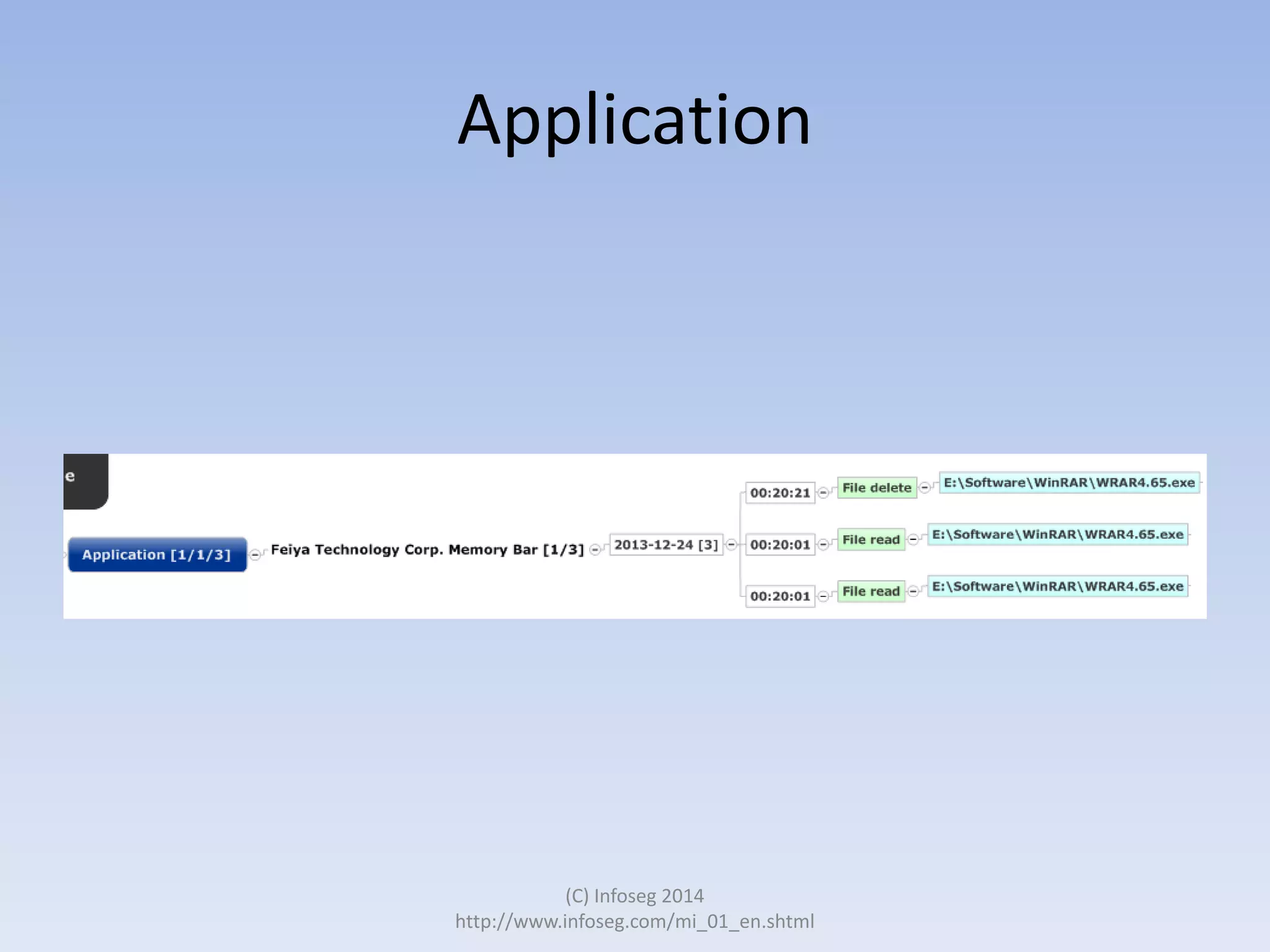
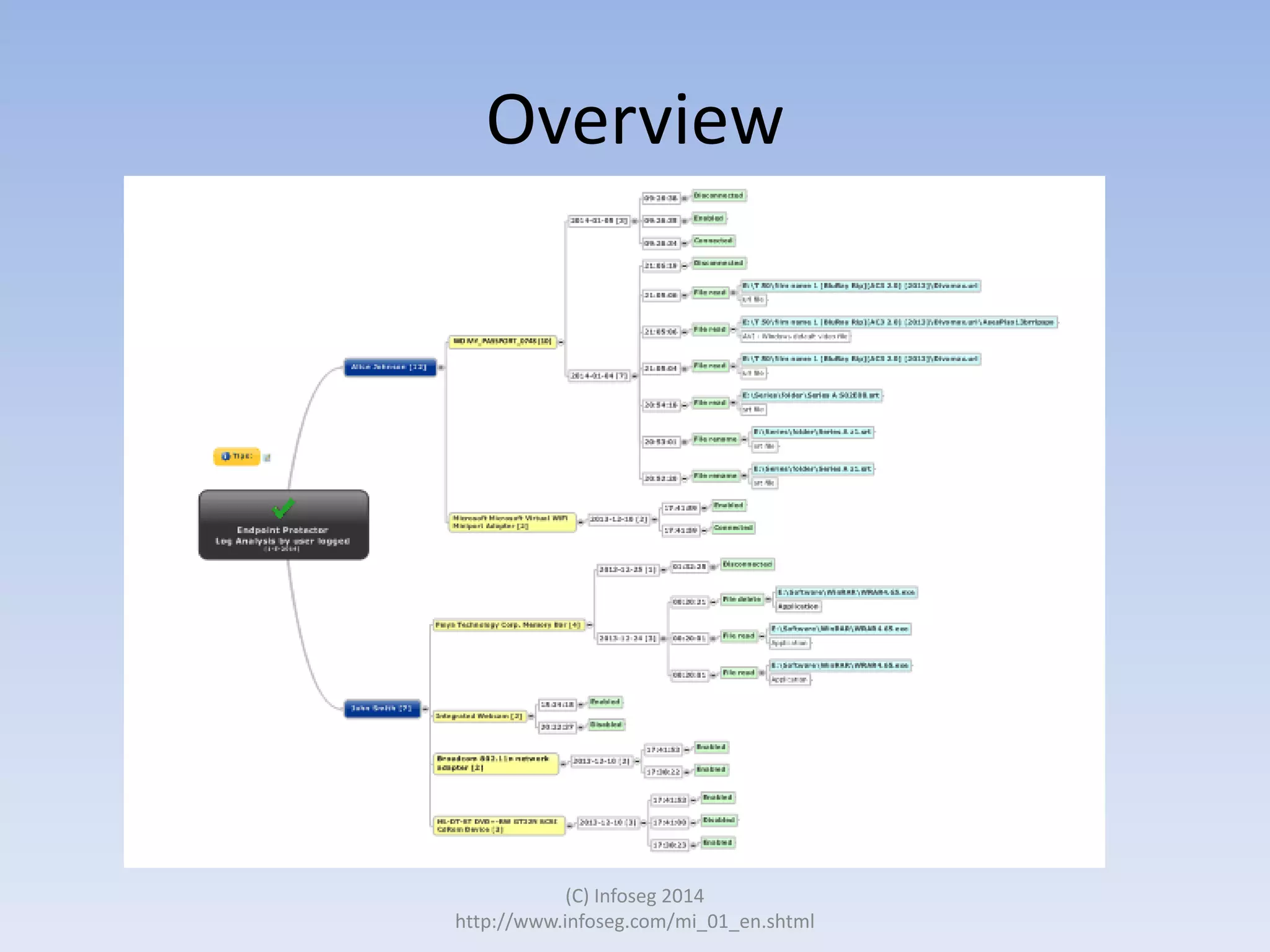
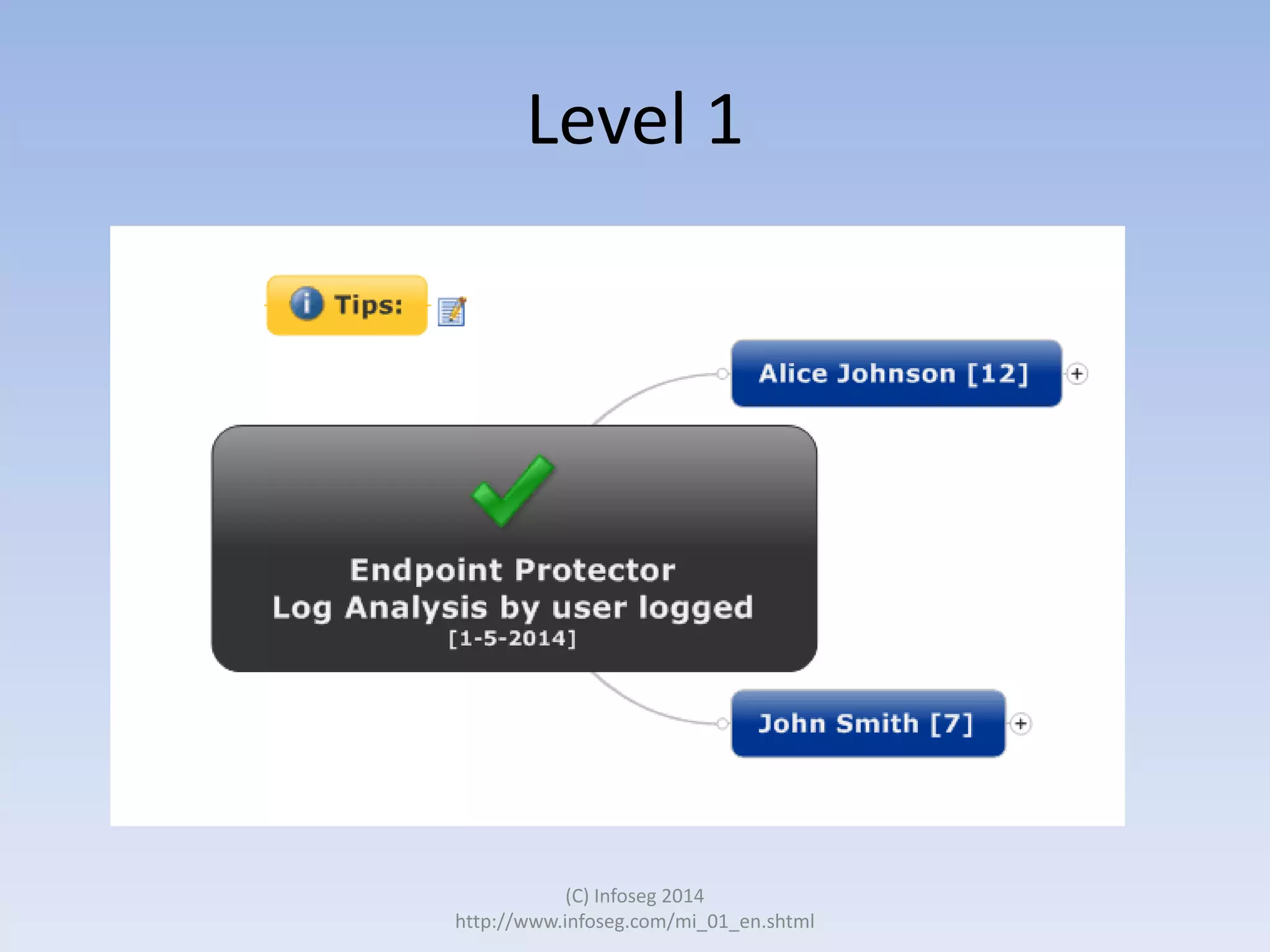
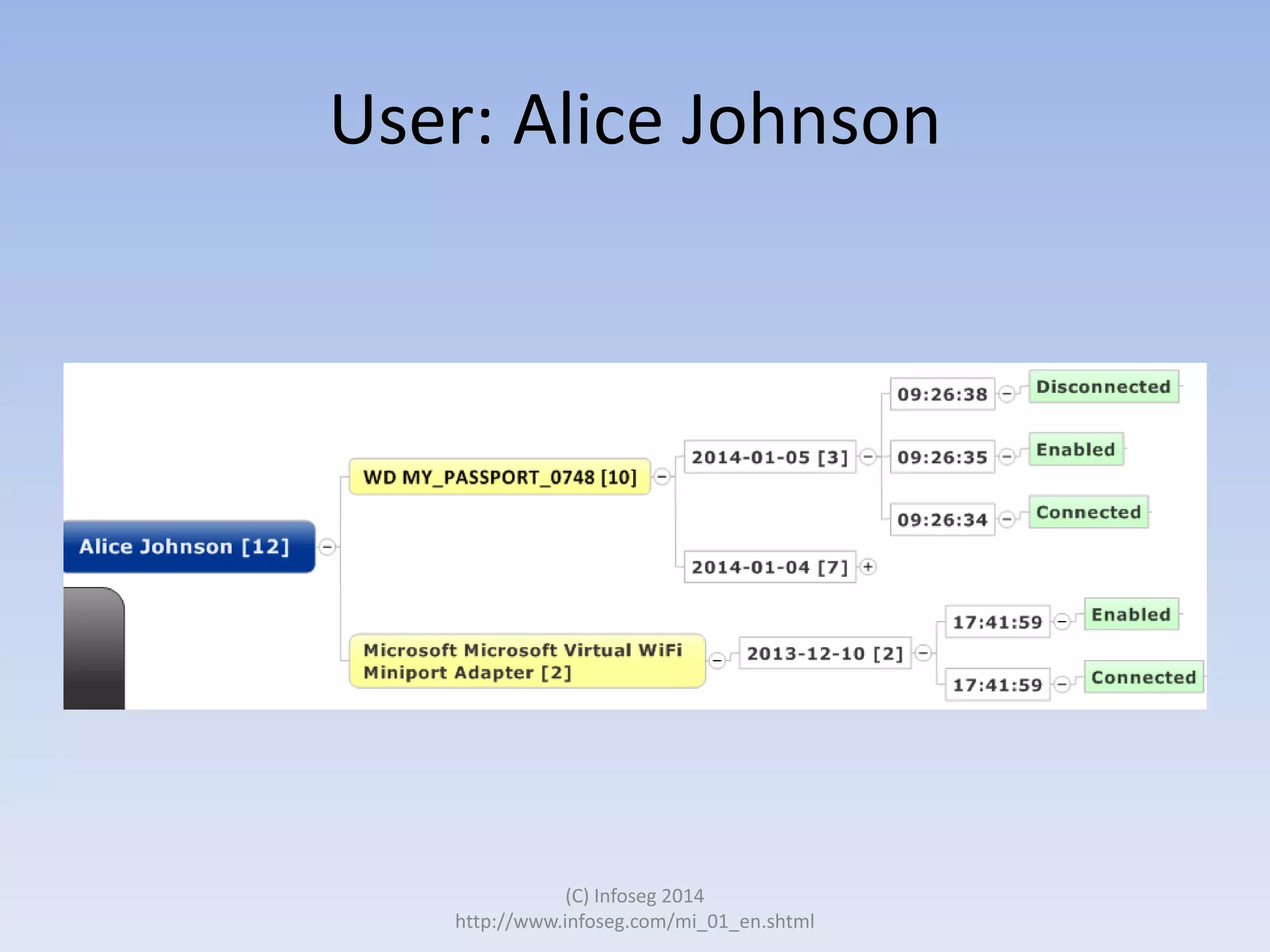
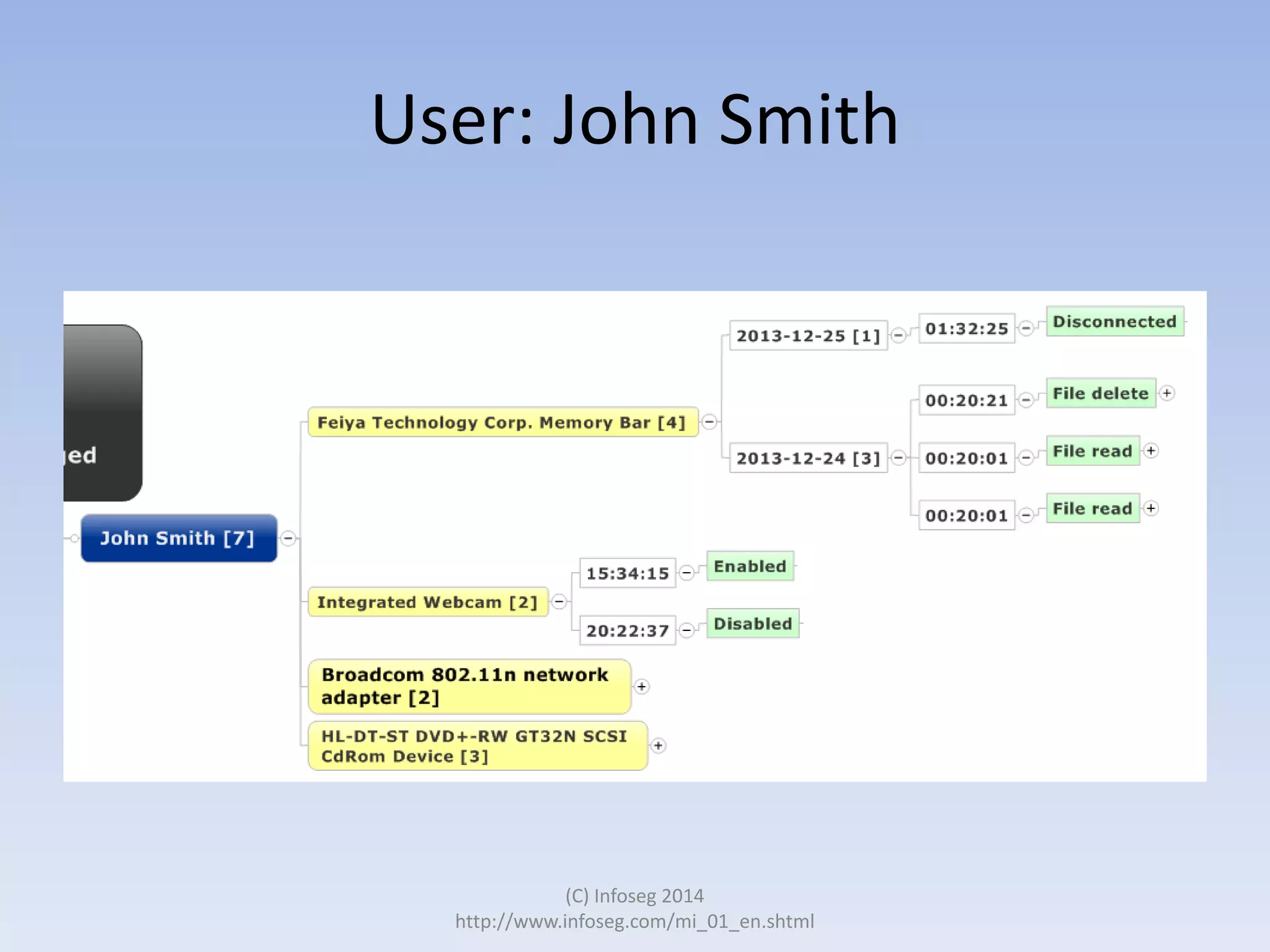
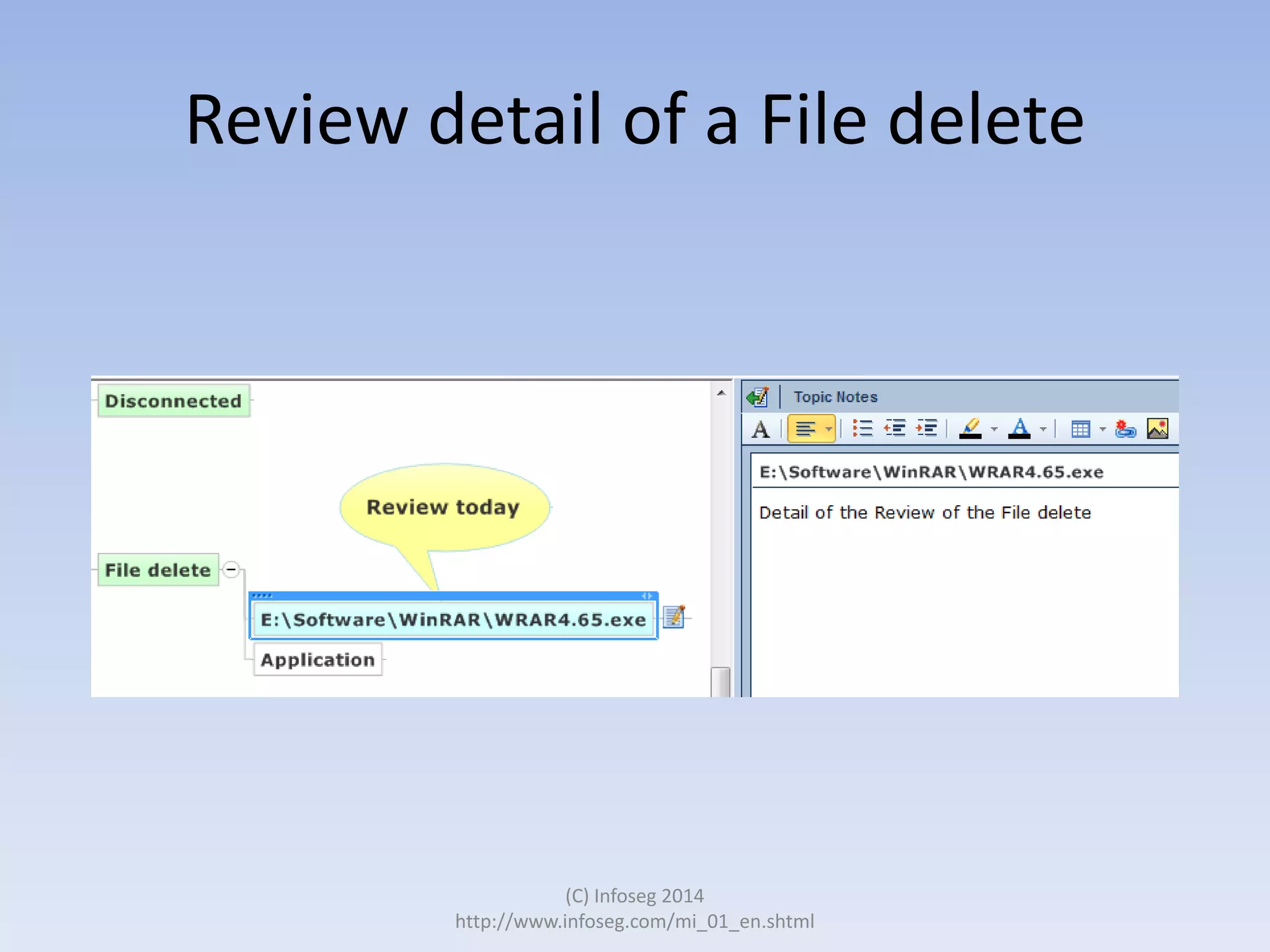
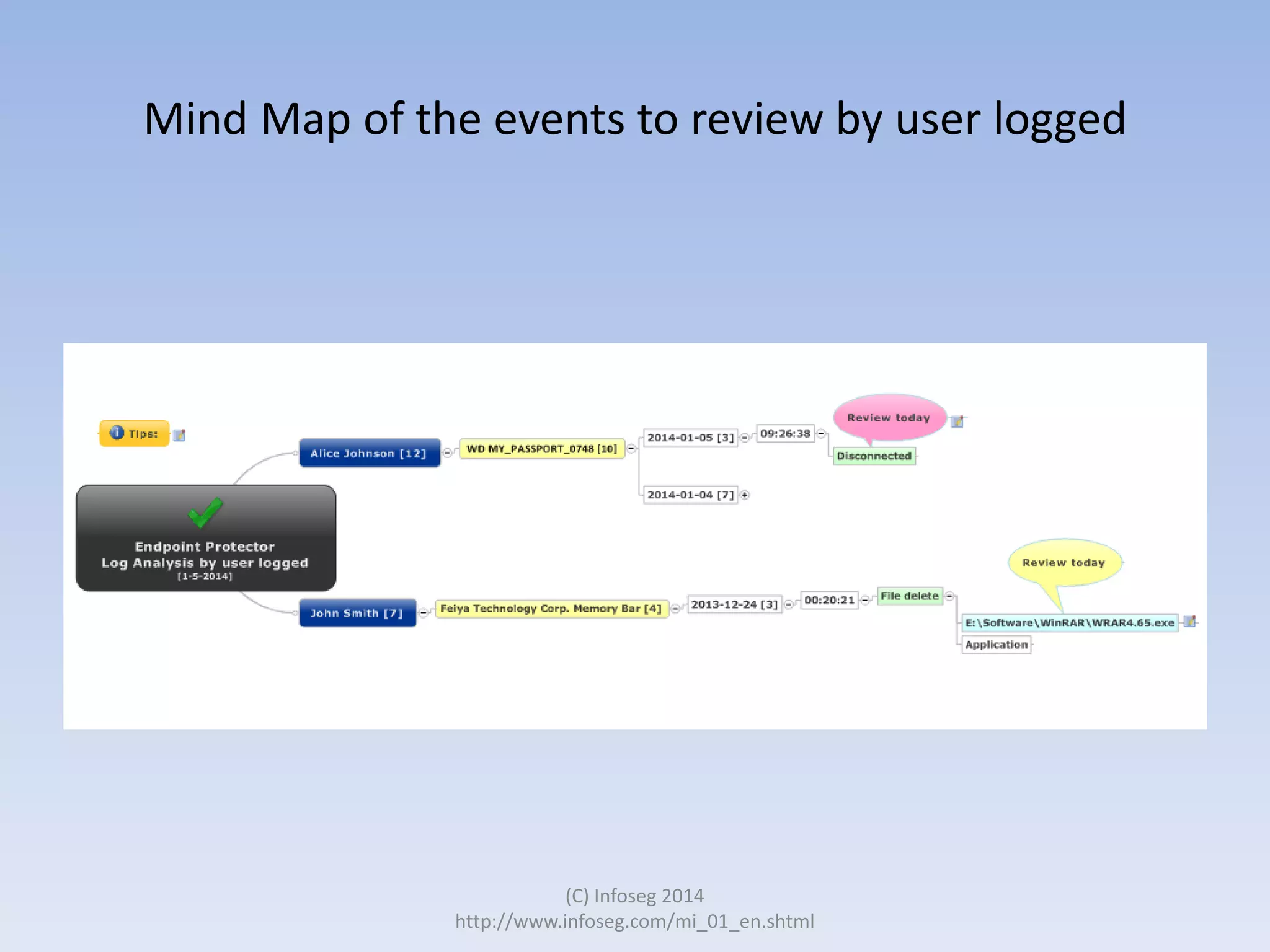
The document discusses the challenges of manually reviewing log files in information security and presents mind mapping automation as a solution to enhance this process. Mind mapping provides a visual representation of data, making it easier to analyze events by various criteria, such as device and user. The summary highlights that mind mapping automation simplifies log analysis, reduces time, and is adaptable to different log types.