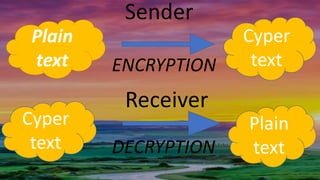
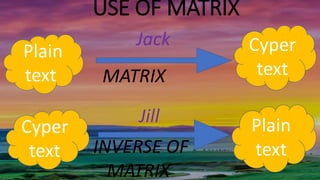
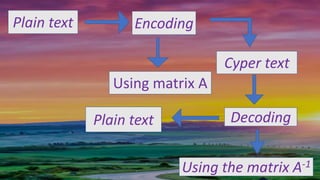
This document discusses how matrices can be used for encryption and decryption in cryptography. It explains that a plaintext message is first converted to numbers and arranged in a matrix. This matrix is then multiplied by a chosen encryption matrix to produce the ciphertext matrix. Decryption involves multiplying the ciphertext matrix by the inverse of the encryption matrix to recover the original plaintext matrix and message. An example is provided to illustrate the encryption of the message "ATTACK NOW" using a 2x2 matrix.




![EXAMPLE:
Message to be Sent
ATTACK NOW Plain text
Encoding A = 1 2
1 3
AT=[1 20] 1 2 = [21 62]
1 3
TA=[20 1] 1 2 = [21 43]
1 3](https://image.slidesharecdn.com/presentation3-240411121542-411119f6/85/Application-of-matrices-in-cryptography-8-320.jpg)
![CK =[3 11] 1 2 = [14 39]
1 3
_N =[27 14] 1 2 = [41 96]
1 3
OW=[15 23] 1 2 = [38 99]
1 3
Encoded
ATTACK NOW= 21 21 14 41 38
62 43 39
cyper text
DECODING A = 3 -2
-1 1](https://image.slidesharecdn.com/presentation3-240411121542-411119f6/85/Application-of-matrices-in-cryptography-9-320.jpg)
![T=[21 62] 3 -2 =[1 20]
-1 1
A=[21 43] 3 -2 =[20 1] Decoded message:
-1 1 1 20 3 27 15
K=[14 29] 3 -2 =[3 11] 20 1 11 14 23
-1 1
N=[41 96] 3 -2 =[27 14]
-1 1
W=[38 99] 3 -2 =[15 23]](https://image.slidesharecdn.com/presentation3-240411121542-411119f6/85/Application-of-matrices-in-cryptography-10-320.jpg)
![[1 20] [20 1] [3 11] [27 14] [15 23]
A T T A C K _ N O W
ATTACK NOW plain text](https://image.slidesharecdn.com/presentation3-240411121542-411119f6/85/Application-of-matrices-in-cryptography-11-320.jpg)