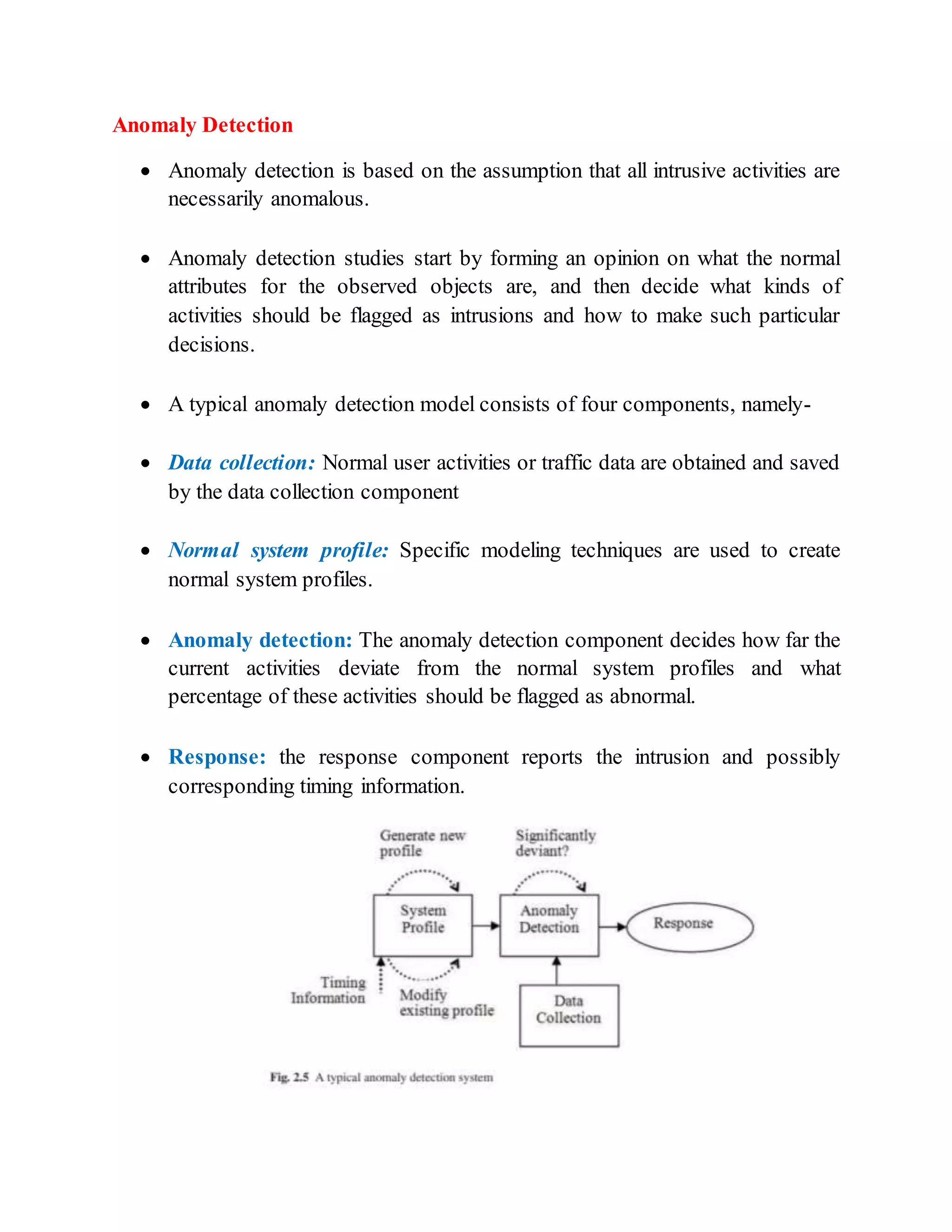
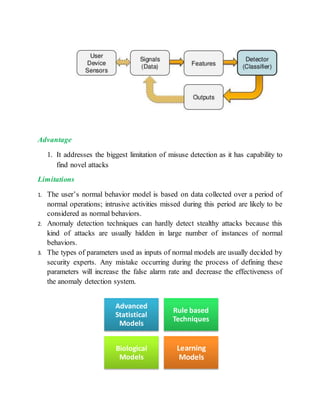
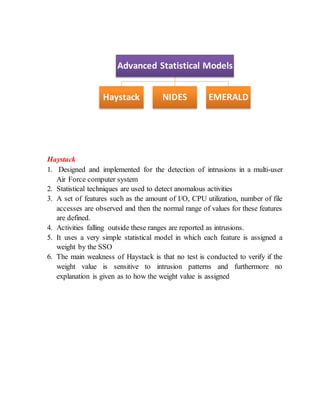
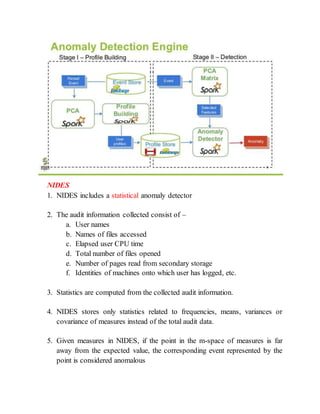
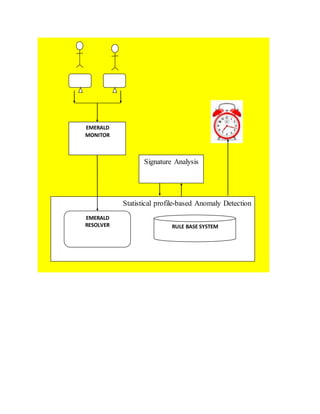
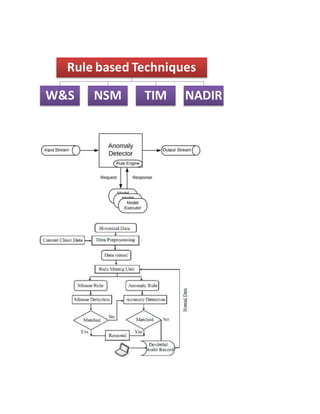
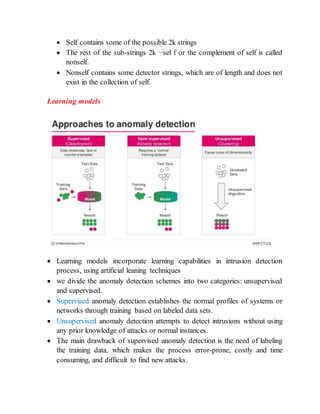
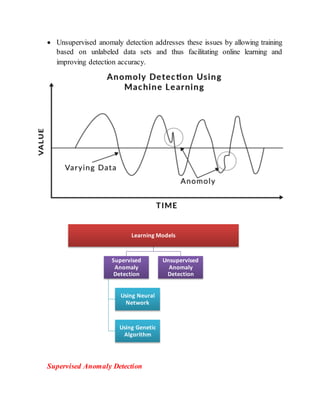
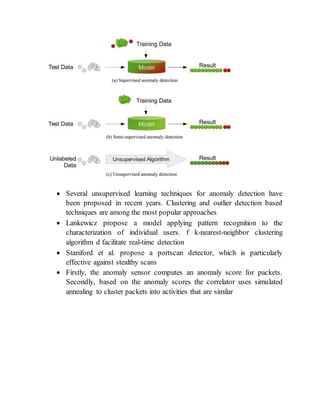
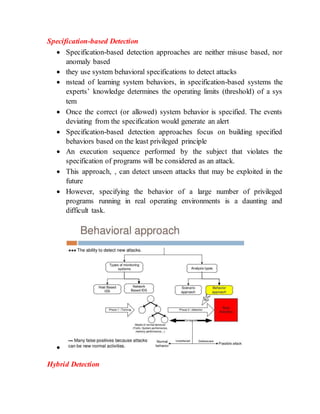
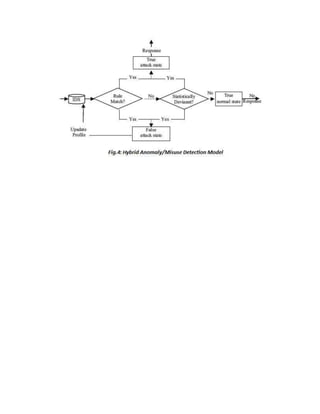
The document discusses different techniques for anomaly detection in intrusion detection systems. It describes four main components of a typical anomaly detection model: data collection, normal system profiling, anomaly detection, and response. It then discusses the advantages and limitations of anomaly detection. The rest of the document summarizes various statistical, rule-based, biological, and learning models used for anomaly detection, including their key principles and examples like Haystack, NIDES, EMERALD, Wisdom & Sense, and Network Security Monitor.