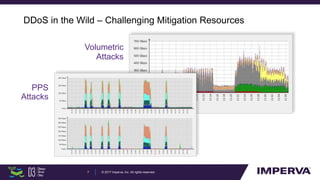
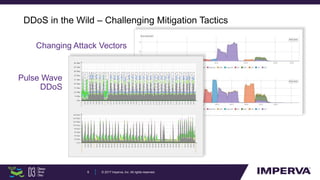
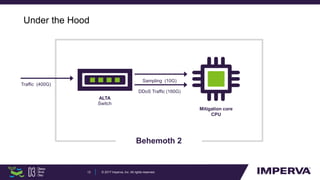
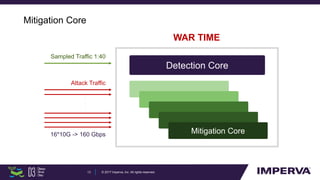
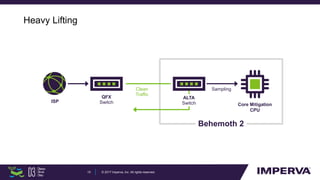
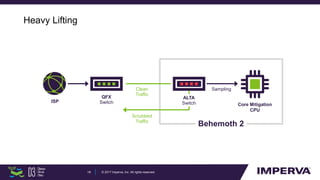
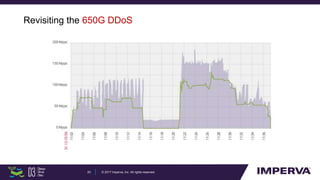
The document discusses advanced DDoS mitigation techniques, highlighting the various types of DDoS attacks, such as application layer and volumetric attacks. It emphasizes the challenges in mitigating such attacks, including the need for rapid response, scalable resources, and agile network infrastructure. The overview concludes with insights into the infrastructure needed for effective DDoS defense, exemplified by the capabilities of the 'Behemoth' mitigation system.