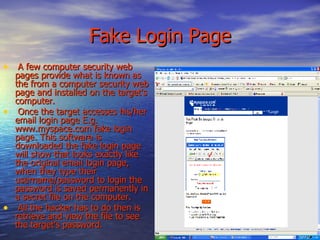
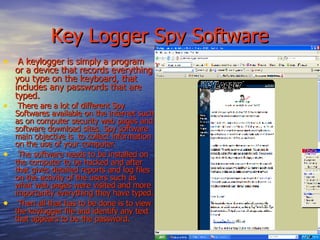
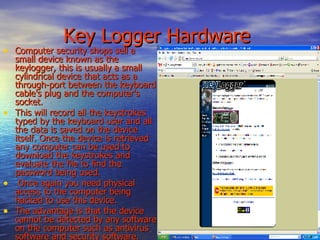
This document provides an overview of hacking, including common techniques used by hackers, steps to avoid being hacked, reasons why hackers hack, and resources for additional information. It describes hacking as illegally entering computer systems to make unauthorized changes. Common hacking techniques mentioned are using fake login pages, keylogger spyware and hardware, and installing backdoors. The document advises avoiding hacking by using antivirus software, firewalls, and only downloading files from trusted sites. Reasons hackers engage in hacking include for jobs, entertainment, because it's their specialty, and to gain classified information for advantage.