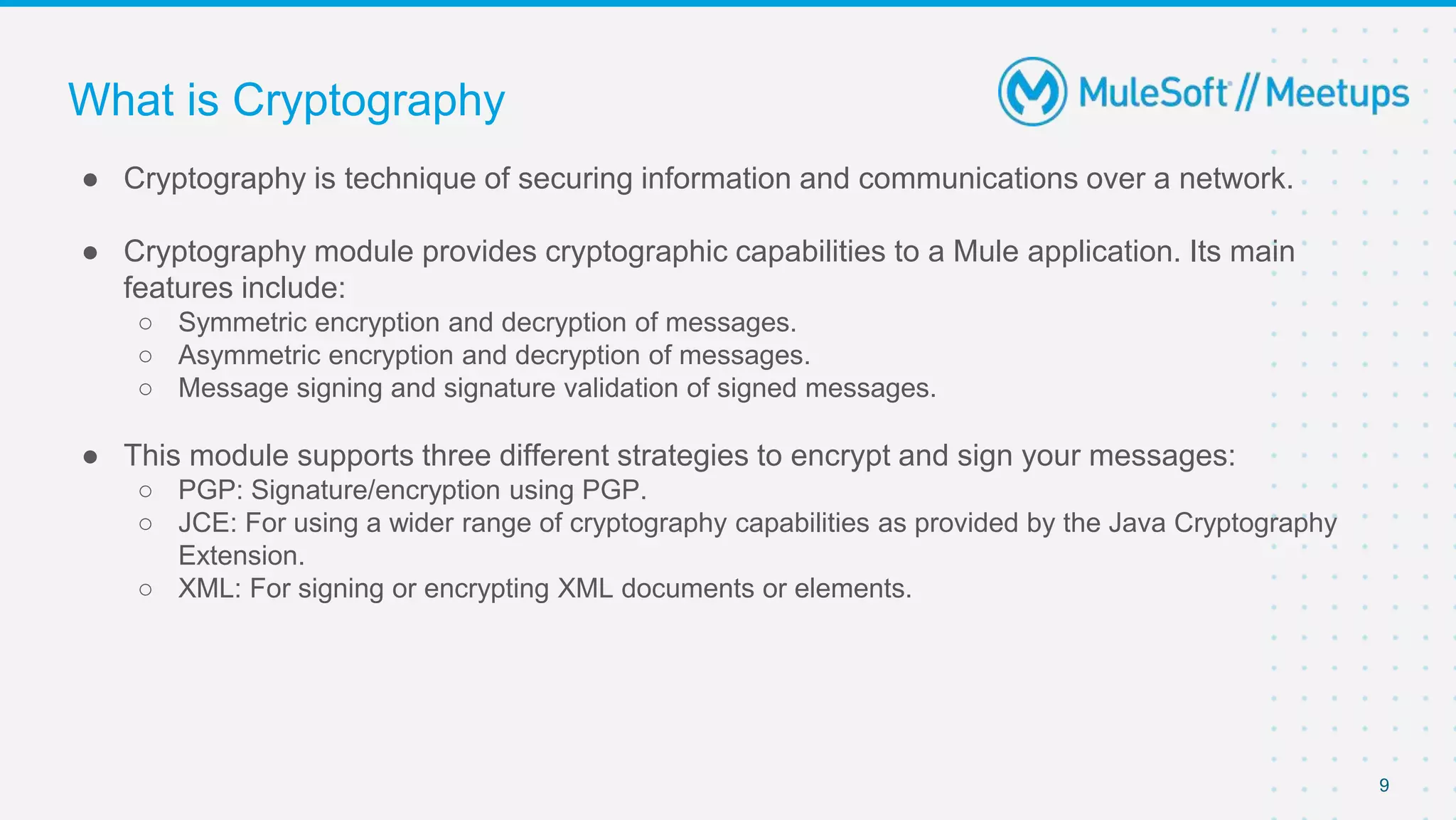
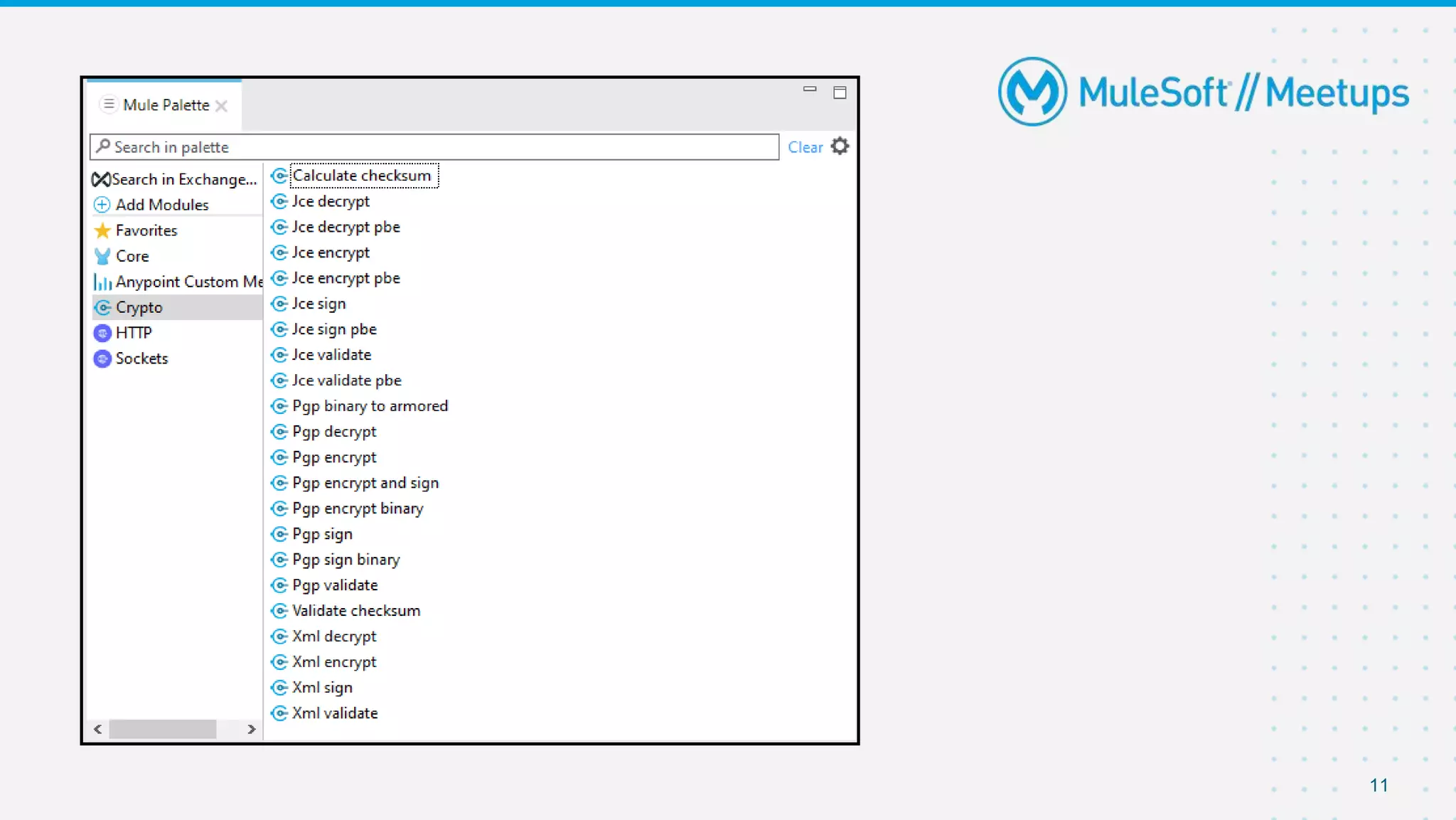
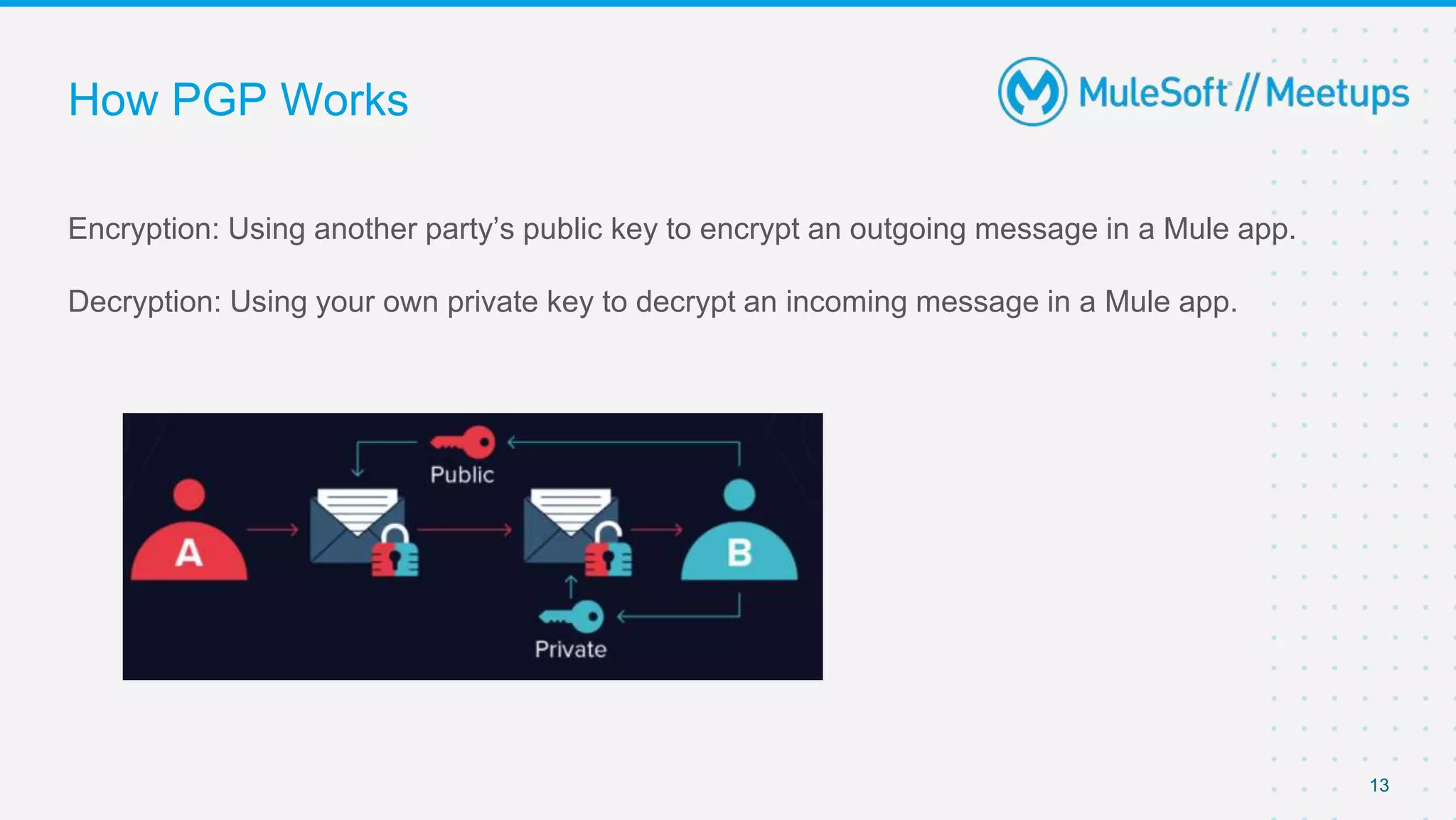
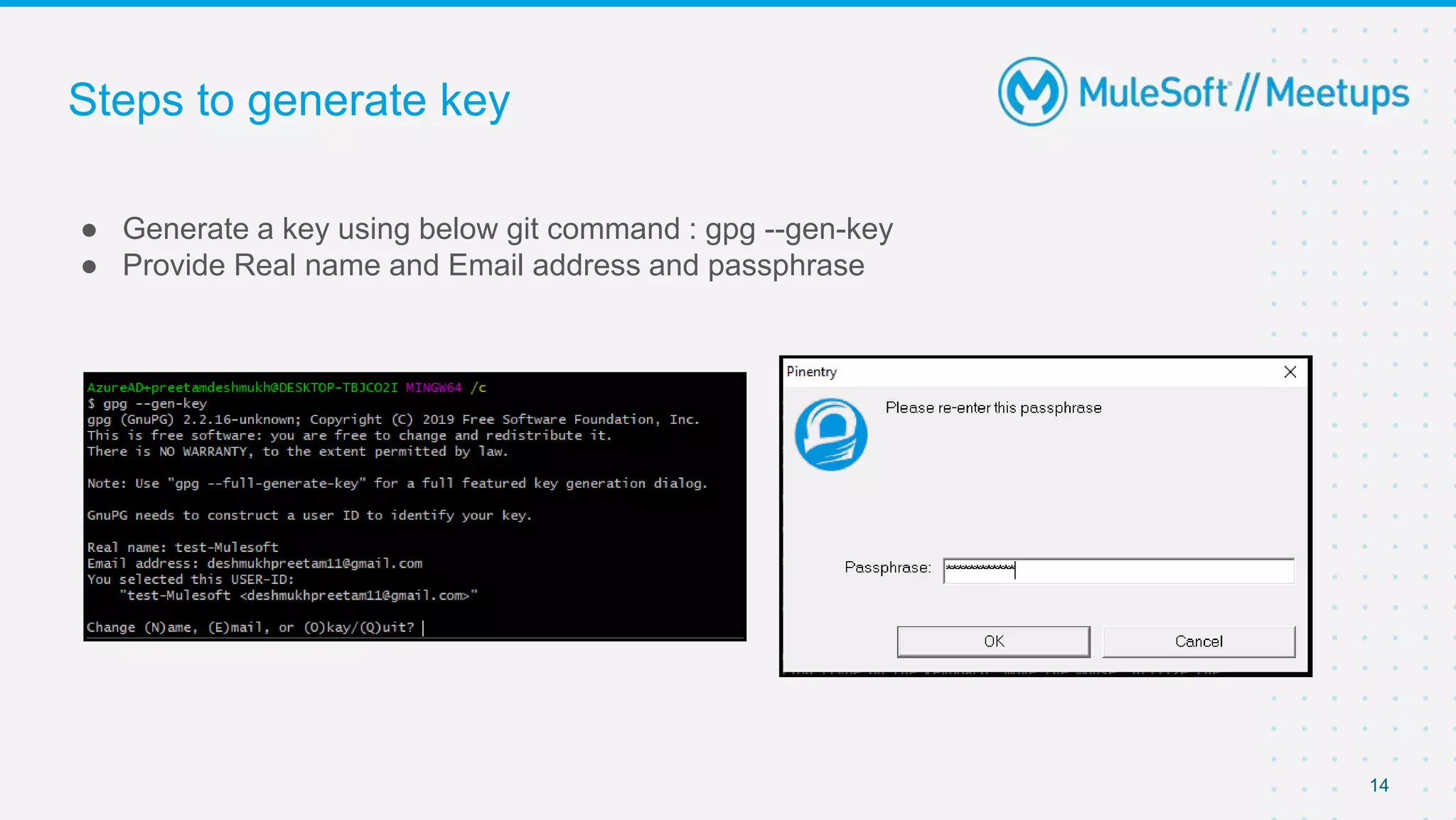
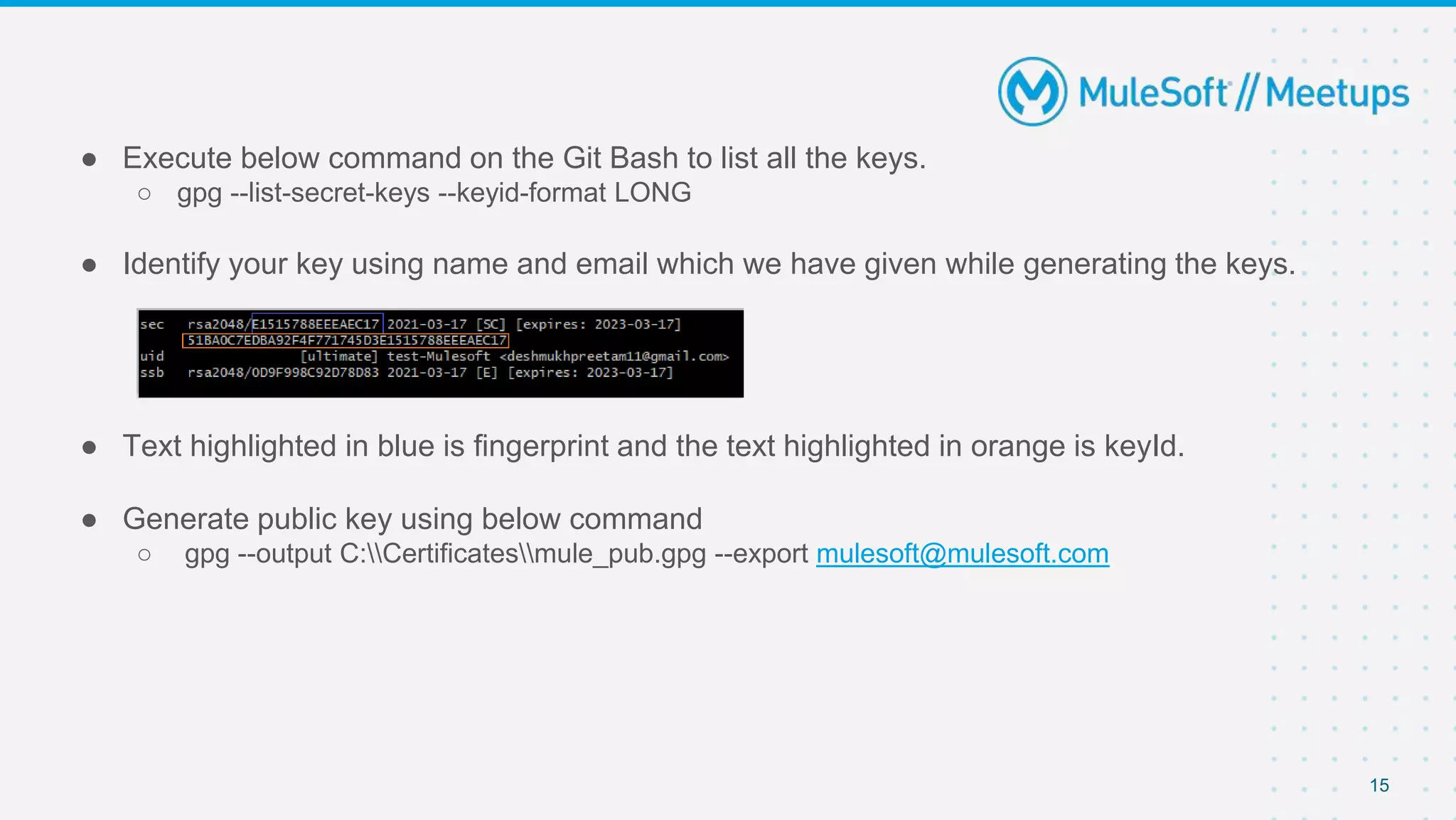
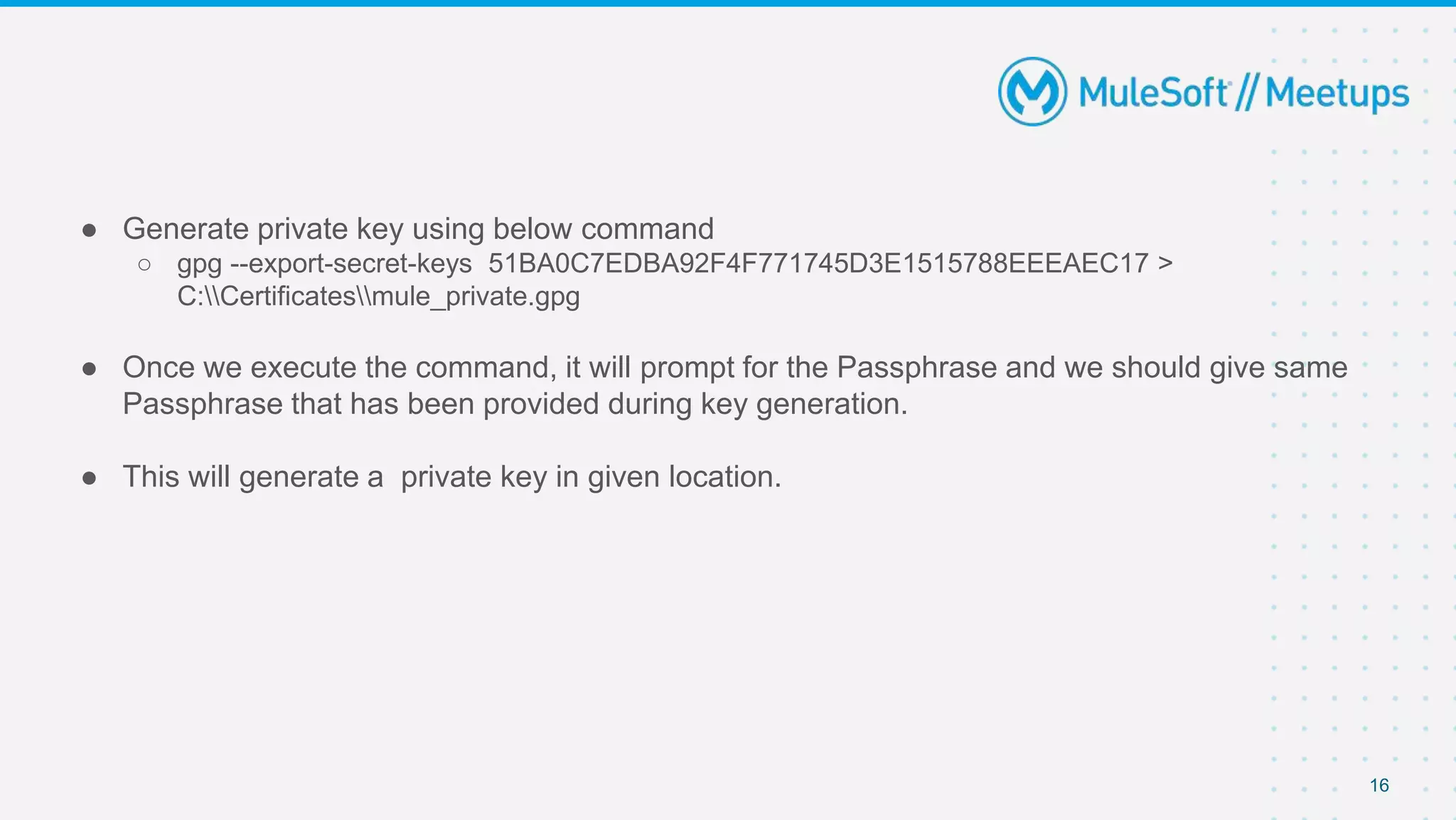
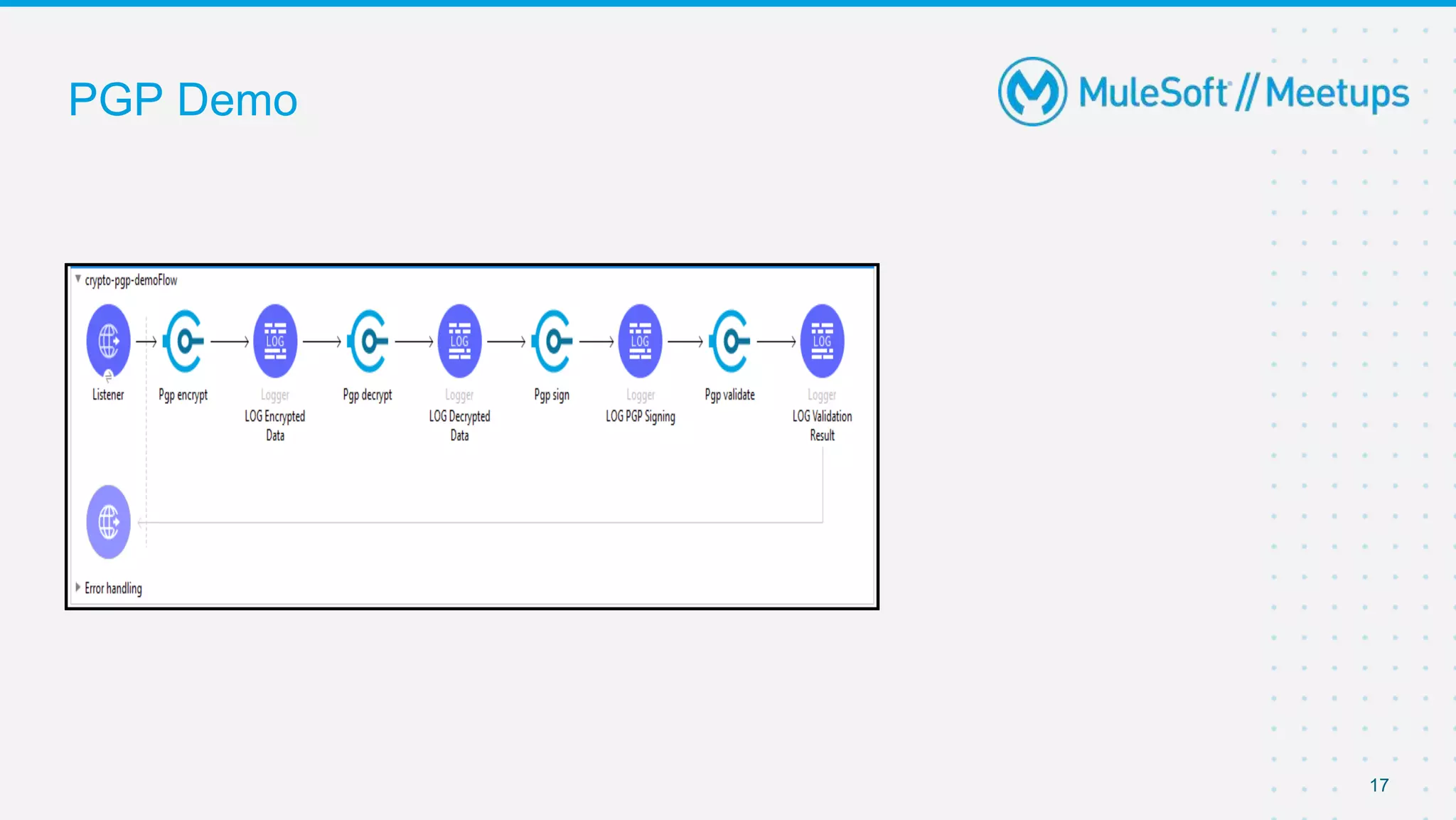
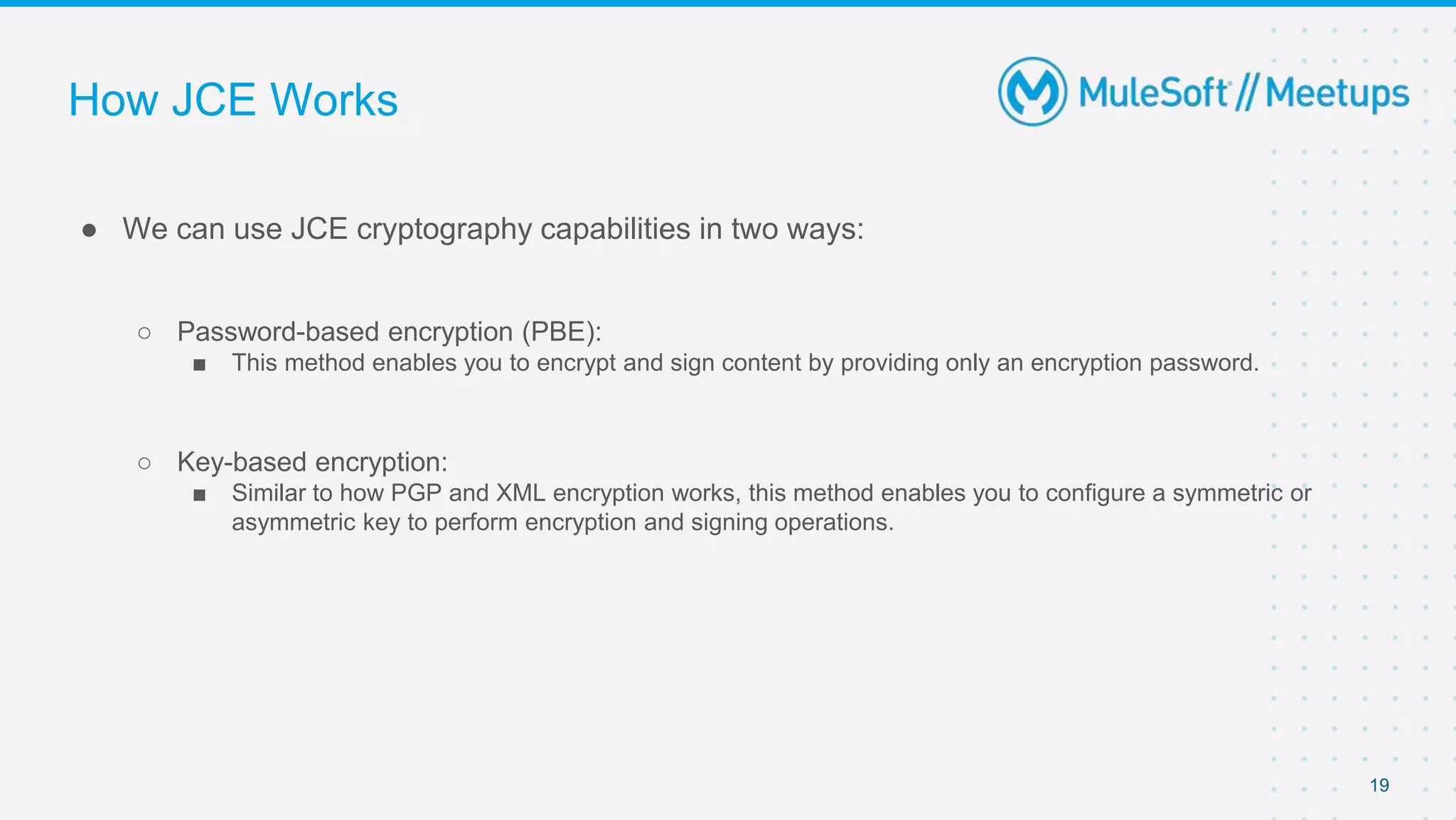
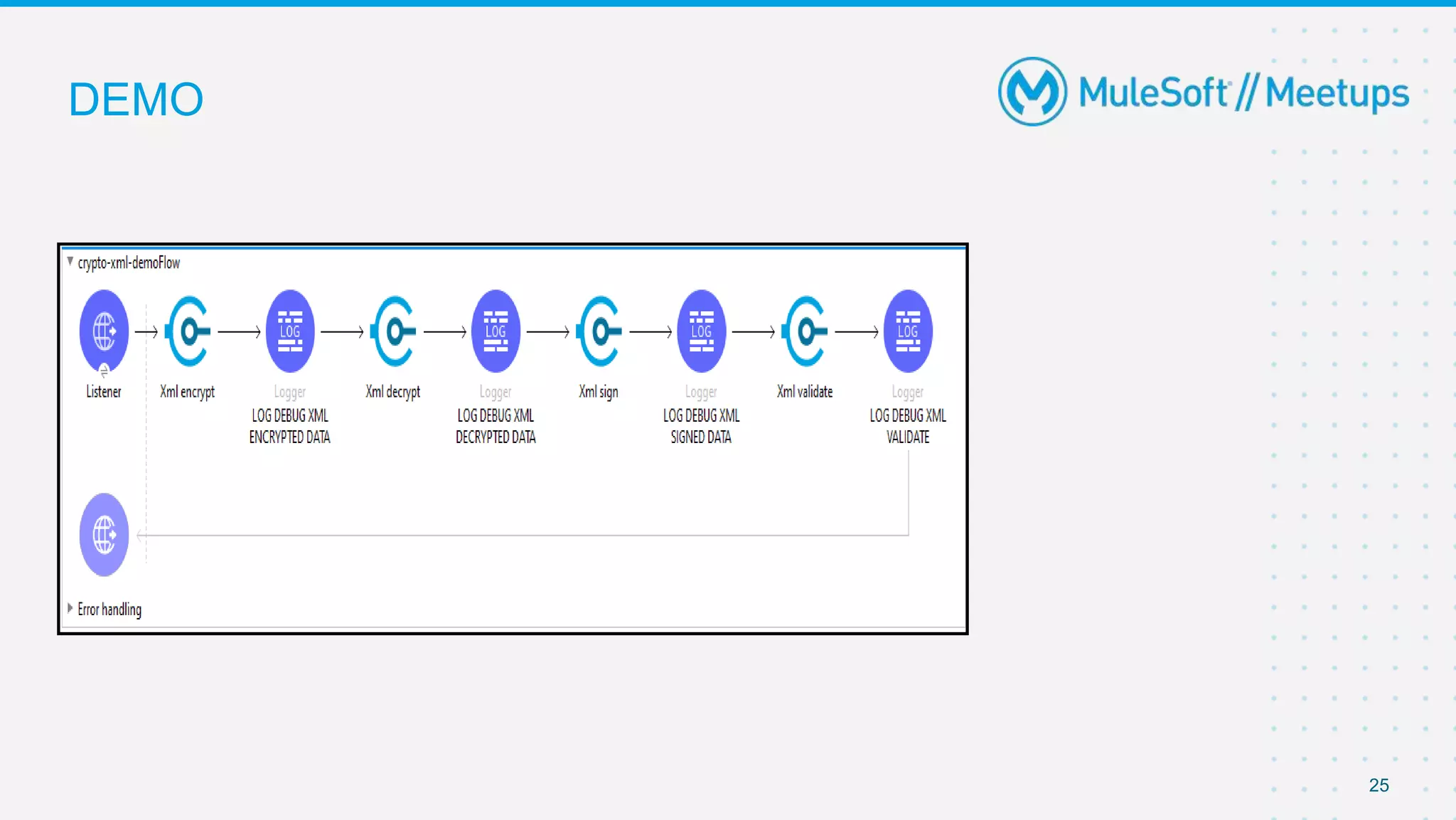
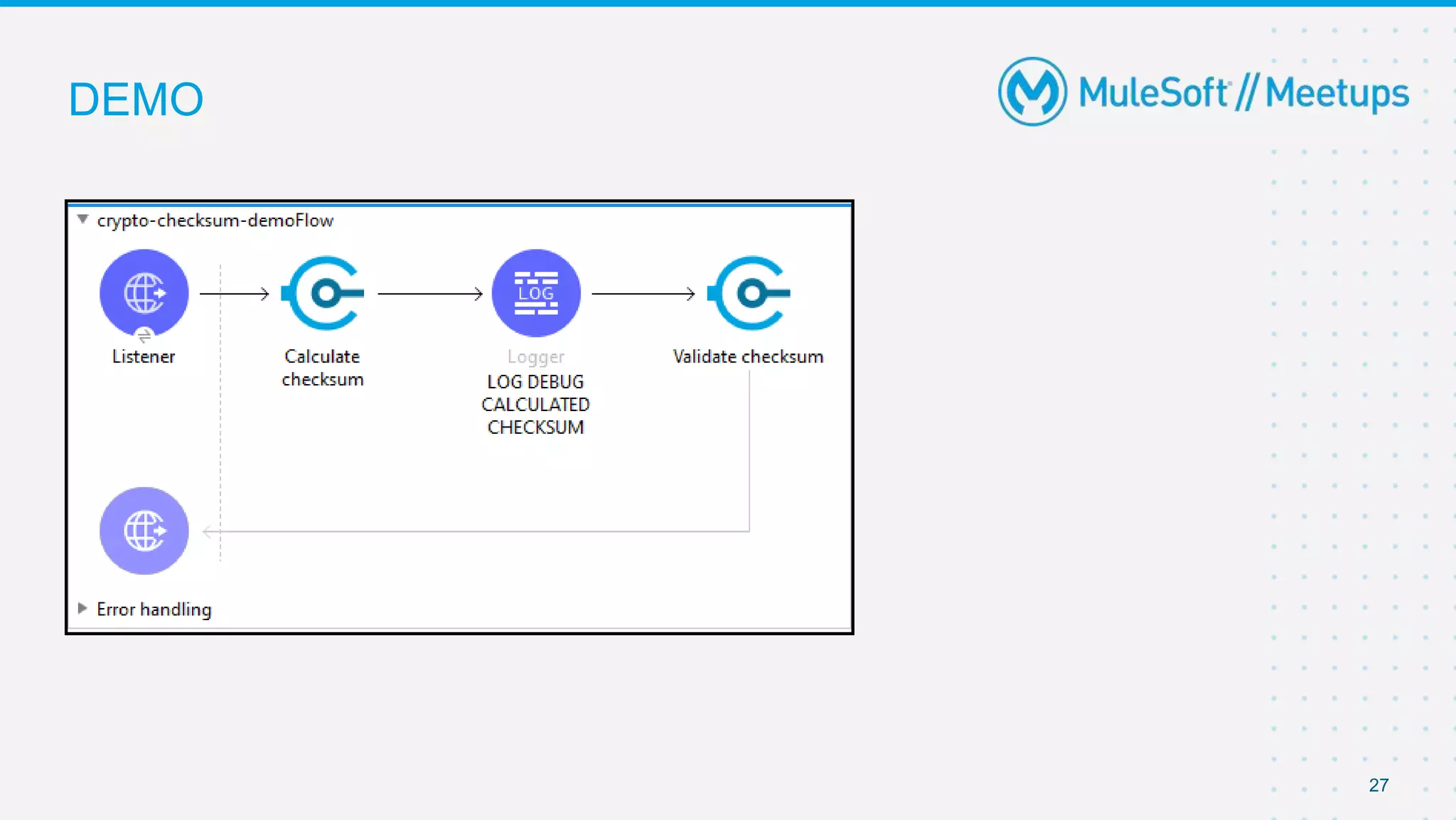
The document summarizes a meetup on the Mule 4 Cryptography Module. The meetup agenda included an overview of cryptography, how to install the cryptography extension in Mule, and demonstrations of PGP, JCE, and XML cryptography. It also covered generating PGP keys, password-based encryption and key-based encryption using JCE, encrypting XML elements, and calculating checksums for message integrity. Attendees were encouraged to provide feedback and suggestions for future meetup topics.