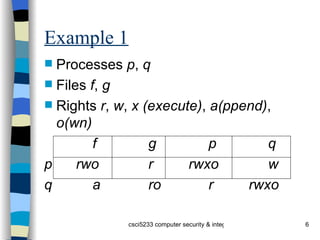
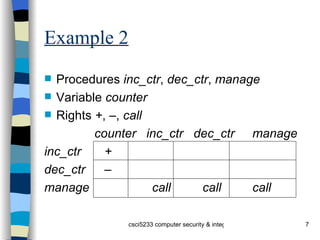
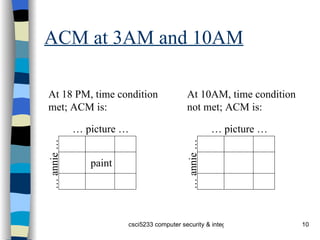
The document discusses an access control matrix (ACM) model for representing access privileges. The ACM captures relationships between subjects (users, processes) and objects (files, variables). It consists of a matrix where each entry specifies rights a subject has to an object. The document outlines how to represent state transitions that change the ACM using primitive operations like creating/destroying subjects/objects and adding/deleting rights. Conditional commands allow transitions if certain conditions are met.




![Description Subjects S = { s 1 ,…, s n } Objects O = { o 1 ,…, o m } Rights R = { r 1 ,…, r k } Entries A [ s i , o j ] R A [ s i , o j ] = { r x , …, r y } means subject s i has rights r x , …, r y over object o j A [ s n , o m ] objects (entities) subjects s 1 s 2 … s n o 1 … o m s 1 … s n](https://image.slidesharecdn.com/acm-091104060312-phpapp01/85/Acm-5-320.jpg)


![Access Controlled by History Database: name position age salary Celia teacher 45 $40,000 Heidi aide 20 $20,000 Holly principal 37 $60,000 Leo teacher 50 $50,000 Matt teacher 33 $50,000 O 1 = {Celia, Leo, Matt} O 3 = {Celia, Leo} Check out [Dobkins/Jones, 1979].](https://image.slidesharecdn.com/acm-091104060312-phpapp01/85/Acm-12-320.jpg)
![Primitive Operations create subject s Creates new row, column in ACM; create object o creates new column in ACM destroy subject s Deletes row, column from ACM destroy object o deletes column from ACM enter r into A [ s , o ] Adds r rights for subject s over object o delete r from A [ s , o ] Removes r rights from subject s over object o](https://image.slidesharecdn.com/acm-091104060312-phpapp01/85/Acm-14-320.jpg)
![Create Subject Precondition: s S Primitive command: create subject s Postconditions: S ´ = S { s }, O ´ = O { s } ( y O ´)[ a ´[ s , y ] = ], ( x S ´)[ a ´[ x , s ] = ] ( x S )( y O )[ a ´[ x , y ] = a [ x , y ]]](https://image.slidesharecdn.com/acm-091104060312-phpapp01/85/Acm-15-320.jpg)
![Create Object Precondition: o O Primitive command: create object o Postconditions: S ´ = S , O ´ = O { o } ( x S ´)[ a ´[ x , o ] = ] ( x S )( y O )[ a ´[ x , y ] = a [ x , y ]]](https://image.slidesharecdn.com/acm-091104060312-phpapp01/85/Acm-16-320.jpg)
![Add Right Precondition: s S , o O Primitive command: enter r into a [ s , o ] Postconditions: S ´ = S , O ´ = O a ´[ s , o ] = a [ s , o ] { r } ( x S ´ – { s })( y O ´ – { o }) [ a ´[ x , y ] = a [ x , y ]]](https://image.slidesharecdn.com/acm-091104060312-phpapp01/85/Acm-17-320.jpg)
![Delete Right Precondition: s S , o O Primitive command: delete r from a [ s , o ] Postconditions: S ´ = S , O ´ = O a ´[ s , o ] = a [ s , o ] – { r } ( x S ´ – { s })( y O ´ – { o }) [ a ´[ x , y ] = a [ x , y ]]](https://image.slidesharecdn.com/acm-091104060312-phpapp01/85/Acm-18-320.jpg)
![Destroy Subject Precondition: s S Primitive command: destroy subject s Postconditions: S ´ = S – { s }, O ´ = O – { s } ( y O ´)[ a ´[ s , y ] = ], ( x S ´)[ a ´[ x , s ] = ] ( x S ´)( y O ´) [ a ´[ x , y ] = a [ x , y ]]](https://image.slidesharecdn.com/acm-091104060312-phpapp01/85/Acm-19-320.jpg)
![Destroy Object Precondition: o o Primitive command: destroy object o Postconditions: S ´ = S , O ´ = O – { o } ( x S ´)[ a ´[ x , o ] = ] ( x S ´)( y O ´) [ a ´[ x , y ] = a [ x , y ]]](https://image.slidesharecdn.com/acm-091104060312-phpapp01/85/Acm-20-320.jpg)
![Creating File Process p creates file f with r and w permission command create•file ( p , f ) create object f ; enter own into A [ p , f ]; enter r into A [ p , f ]; enter w into A [ p , f ]; end](https://image.slidesharecdn.com/acm-091104060312-phpapp01/85/Acm-21-320.jpg)
![Mono-Operational Commands Single primitive operation in a command Example: Make process p the owner of file g command make•owner ( p , g ) enter own into A [ p , g ]; end](https://image.slidesharecdn.com/acm-091104060312-phpapp01/85/Acm-22-320.jpg)
![Conditional Commands Let p give q r rights over f , if p owns f command grant•read•file•1 ( p , f , q ) if own in A [ p , f ] then enter r into A [ q , f ]; end Mono-conditional command Single condition in this command](https://image.slidesharecdn.com/acm-091104060312-phpapp01/85/Acm-23-320.jpg)
![Multiple Conditions Let p give q r and w rights over f , if p owns f and p has c rights over q command grant•read•file•2 ( p , f , q ) if own in A [ p , f ] and c in A [ p , q ] then enter r into A [ q , f ]; enter w into A [ q , f ]; end](https://image.slidesharecdn.com/acm-091104060312-phpapp01/85/Acm-24-320.jpg)



