The document discusses insider threats and proposes implementing the Hitachi ID Identity Manager solution. It provides background on insider threats, including sources like maliciousness, disregard of security practices, carelessness, and ignorance. It analyzes vulnerabilities in telecommunications, credit cards, and healthcare. It then summarizes Hitachi ID features like role-based access control, automatic deactivation of terminated users, and centralized access management. Implementing Hitachi ID could reduce productivity losses, save costs, and help comply with regulations by better controlling access.

![ Impact on Confidentiality due to Insider Attacks
An insider is anyone with access to an organization's protected
assets
Insider attack is someone using that access to violate protocol
or cause harm intentionally or unintentionally
Protocol violations with good intentions are still considered
threats
We have already identified a variety of fields that have
vulnerabilities due to Insider Attacks
A Telecommunications Company and it’s employees having
default access to sensitive test data
A Credit Card Company and it’s employees having access to
customer credit card numbers
A Health Care Company and the diverse collection of
people/employees that have access to user health data [2]
Introduction and Background](https://image.slidesharecdn.com/insiderattackp3-221114040951-2778544f/85/InsiderAttack_p3-ppt-2-320.jpg)
![ There are four basic sources of insider security
problems:
Maliciousness – that results in compromise or destruction of
information, or disruption of services to other insiders
Disdain of Security Practices – that results in compromise or
destruction of information, or disruption of services to other
insiders.
Carelessness – in the use of an information system and/or the
protection of company information
Ignorance – of security policy, security practices and
information system use
Current state of work:
Basic User ID/ password validation – missing role based
access, department based access. If you know the User ID/
Password then you have pretty much every thing
Policy and procedures – Not strictly enforced [3]](https://image.slidesharecdn.com/insiderattackp3-221114040951-2778544f/85/InsiderAttack_p3-ppt-3-320.jpg)
![ Develop stronger authentication
mechanisms – Some apps do have generic
User ID/ Password
Implement role based access control –
Provide just what they are eligible to see
Provide access to the information based on
their department’s business need – Provide
just what they need
Enforce the security policy – tie the
violations to job performance
[5]](https://image.slidesharecdn.com/insiderattackp3-221114040951-2778544f/85/InsiderAttack_p3-ppt-4-320.jpg)

![Architectural view of Hitachi ID Integration
[1]](https://image.slidesharecdn.com/insiderattackp3-221114040951-2778544f/85/InsiderAttack_p3-ppt-6-320.jpg)
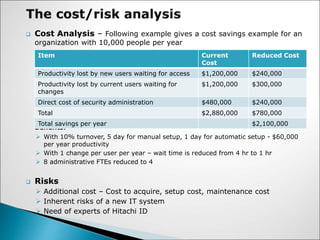

![ Benefits of Hitachi ID versus Sun Identity Server
More platform-neutral solution for their IDM products
as opposed to Sun that is tied to Oracle
Recognized by industry as more scalable and reliable
Integrates equally well with all the major databases,
operating systems, web servers and ERP applications
User provisioning is open to allow easy integration
Lower lifetime support costs for deployed systems
since the customer has a stronger bargaining position
at maintenance renewal time, since replacing one
product is much easier than replacing many. [1]](https://image.slidesharecdn.com/insiderattackp3-221114040951-2778544f/85/InsiderAttack_p3-ppt-9-320.jpg)




![Risk
Assessment
Outcomes
Threats
Prioritized
Risks Select
Countermeasures
System
Design
Policies Requirements
Available
Countermeasures
Security
Components Develop
Security
Architecture
Security Architecture
[4]](https://image.slidesharecdn.com/insiderattackp3-221114040951-2778544f/85/InsiderAttack_p3-ppt-14-320.jpg)

![What
How
[4]](https://image.slidesharecdn.com/insiderattackp3-221114040951-2778544f/85/InsiderAttack_p3-ppt-16-320.jpg)
