1. The document proposes a genetic-fuzzy based method for automatic intrusion detection using network datasets. It combines fuzzy set theory with genetic algorithms to extract rules for both discrete and continuous attributes to detect normal and intrusion patterns.
2. The method was tested on KDD99 Cup and DARPA98 network intrusion detection datasets and showed high detection rates with low false alarm rates for both misuse detection and anomaly detection.
3. By extracting many rules to represent normal network behavior patterns, the proposed genetic-fuzzy approach can detect new or unknown intrusions based on anomalies without requiring prior domain expertise on intrusion patterns.





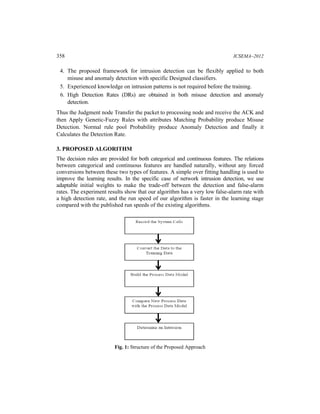


![A Study on Genetic-Fuzzy Based Automatic Intrusion Detection on Network Datasets 361
Test were conducted which are shown in Figure 3a was taken on the training of different
types of trained input versus Attacks were highlighted. The experiment was conducted again
and again which provided a 100% result. Also the experiment was proved in Figure 3b has
a high detection rate.
5. CONCLUSION
A Genetic-Fuzzy rule mining with sub attribute utilization and the classifiers based on the
extracted rules have been proposed, which can consistently use and combine discrete and
continuous attributes in a rule and efficiently extract many good rules for classification.
As an application, intrusion-detection classifiers for both misuse detection and anomaly
detection have been developed and their effectiveness is confirmed using KDD99 Cup
and DARPA98 data. In the misuse detection show that the proposed method shows high
DR and low PFR, which are two important criteria for security systems. In the anomaly
detection, the results show high DR and reasonable PFR even without pre experienced
knowledge, which is an important advantage of the proposed method. In order to analyze
the proposed method in the intrusion-detection problem in detail, Genetic-Fuzzy data
mining is compared with that with crisp data mining, and the result clarifies the necessity
to introduce fuzzy membership functions into Genetic-Fuzzy based data mining. The
important function of the proposed method is to efficiently extract many rules that are
statistically significant and they can be used for several purposes. The matching of a new
connection with the normal rules and the intrusion rules are calculated, respectively, and
the connection is classified into the normal class or intrusion class. When we use the rules
for anomaly detection, only the rules of the normal connections are used to calculate the
deviation of a new connection from the normal data. Therefore, many rules extracted by
Genetic-Fuzzy cover the spaces of the classes widely.
REFERENCES
[1] Shingo Mabu, Ci Chen, Nannan Lu, Kaoru Shimada, and Kotaro Hirasawa “An Intrusion-
Detection Model Based on Fuzzy Class-Association-Rule Mining Using Genetic Network
Programming “, January 2011.
[2] J. G.-P. A. El Semaray, J. Edmonds, and M. Papa, “Applying data mining of fuzzy
association rules to network intrusion detection,” presented at the IEEE Workshop Inf.,
United States Military Academy, West Point, NY, 2006.
[3] W. Hu, W. Hu, and S. Maybank, “Adaboost-based algorithm for network intrusion detection,”
IEEE Trans. Syst.,Man, Cybern. B, Cybern., vol. 38, no. 2, pp. 577–583, Apr. 2008.
[4] Z. Bankovi´c, D. Stepanovi´c, S. Bojani´c, and O. Nieto-Taladriz, “Improving network
security using genetic algorithm approach,” Comput. Elect. Eng., vol. 33, pp. 438–451, 2007.
[5] S.-J. Han and S.-B. Cho, “Evolutionary neural networks for anomaly detection based on the
behaviour of a program,” IEEE Trans. Syst., Man, Cybern. B, Cybern., vol. 36, no. 3, pp. 559–
570, Jun. 2006.
[6] J. Zhang, M. Zulkernine, and A. Haque, “Random-forestsbased network intrusion detection
systems,” IEEE Trans. Syst., Man, Cybern. C, Appl. Rev., vol. 38, no. 5, pp. 649–659, Sep. 2008.](https://image.slidesharecdn.com/icsema2012-190624160130/85/A-Study-on-Genetic-Fuzzy-Based-Automatic-Intrusion-Detection-on-Network-Datasets-9-320.jpg)
![362 ICSEMA–2012
[7] K. Shimada, K. Hirasawa, and J. Hu, “Genetic network programming with class association
rule acquisition mechanisms from incomplete databases,” in Proc. SICE Annu, Conf.,
Kagawa, Japan, 2007, pp. 2708–2714.
[8] K. Shimada, K. Hirasawa, and J. Hu, “Class association rule mining from incomplete
database using genetic network programming,” (in Japanese),IEEJ Trans. EIS, vol. 128, no. 5,
pp. 795– 803, 2008.
[9] S. Mabu, K. Hirasawa, and J. Hu, “A graph-based evolutionary algorithm: Genetic Network
Programming (GNP) and its extension using reinforcement learning,” Evol. Comput, vol. 15,
no. 3, pp. 369– 398, 2007
[10] T. Eguchi, K. Hirasawa, J. Hu, and N. Ota, “A study of evolutionary multiagent models
based on symbiosis,” IEEE Trans. Syst.,Man, Cybern. B, Cybern., vol. 36, no. 1, pp. 179–193,
Feb. 2006.
[11] K. Hirasawa, T. Eguchi, J. Zhou, L. Yu, and S. Markon, “A doubledeck elevator group
supervisory control system using genetic network programming,” IEEE Trans. Syst., Man,
Cybern. C, Appl. Rev., vol. 38, no. 4, pp. 535–550, Jul. 2008.
[12] K. Hirasawa, M. Okubo, H. Katagiri, J. Hu, and J. Murata, “Comparison between Genetic
Network Programming (GNP) and Genetic Programming (GP),” in Proc. Congr. Evol.
Comput., 2001, pp. 1276–1282.
[13] K. Shimada, K. Hirasawa, and J. Hu, “Genetic network programming with acquisition
mechanisms of association rules,” J. Adv. Comput. Intell. Intell. Inf., vol. 10, no. 1, pp. 102–111,
2006.
[14] C. C. Aggarwal and P. Yu, “Outliers detection for high dimensional data,” in Proc. ACM
SIGMOD Conf., 2001, pp. 37–46.
[15] K. Shimada, K. Hirasawa, and J. Hu, “Class association rule mining with chi-squared test
using Genetic Network Programming,” in Proc. IEEE Int. Conf. Syst., Man, Cybern., 2006,
pp. 5338–5344.
[16] W. Lee and S. J. Stolfo, “A framework for constructing features and models for intrusion
detection systems,” ACM Trans. Inf. Syst. Secur., vol. 3, no. 4, pp. 227–261, 2000.
[17] Tcptrace Software Tool. [Online]. Available: www.tcptrace.org.
[18] Z. Bankovi´c, D. Stepanovi´c, S. Bojani´c, and O. Nieto-Taladriz, “Improving network
security using genetic algorithm approach,” Comput. Elect. Eng., vol. 33, pp. 438–451, 2007.
[19] K. Shimada, K. Hirasawa, and J. Hu, “Genetic network programming with class association
rule acquisition mechanisms from incomplete databases,” in Proc. SICE Annu. Conf.,
Kagawa, Japan, 2007, pp. 2708– 2714.
[20] K. Shimada, K. Hirasawa, and J. Hu, “Class association rule mining from incomplete
database using genetic network programming,” (in Japanese), IEEJ Trans. EIS, Vol. 128, No. 5,
pp. 795–803, 2008.](https://image.slidesharecdn.com/icsema2012-190624160130/85/A-Study-on-Genetic-Fuzzy-Based-Automatic-Intrusion-Detection-on-Network-Datasets-10-320.jpg)