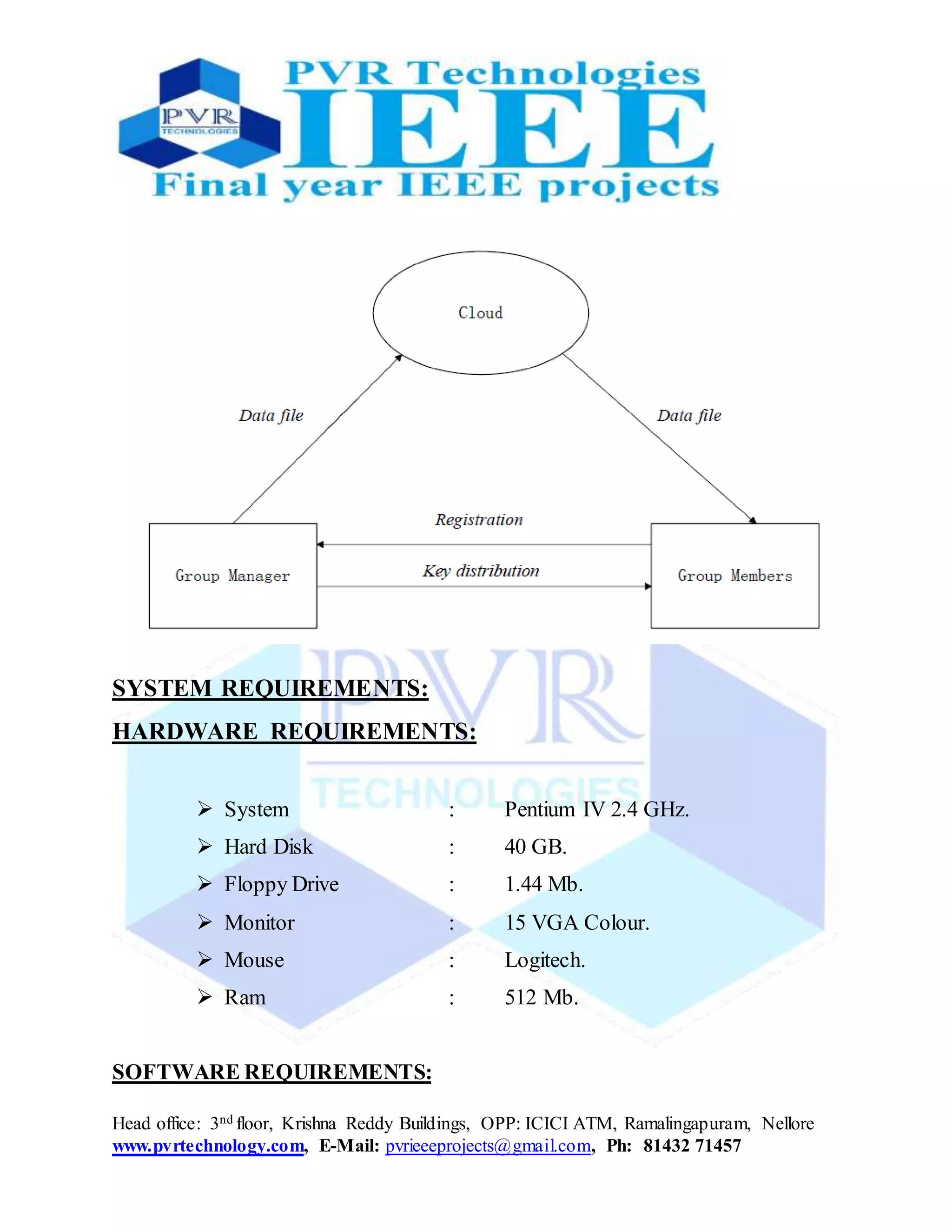
This document proposes a secure data sharing scheme for dynamic groups in the cloud. It allows group members to securely access and share data files stored in the cloud. The scheme provides secure key distribution without requiring secure communication channels. It also enables fine-grained access control and prevents collusion attacks between revoked users and the cloud. When users join or leave the group, other users do not need to update their private keys. The scheme aims to address limitations of existing approaches that require updating file-block keys for revocations and have overhead linearly increasing with member/revocation changes.