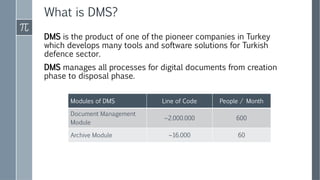
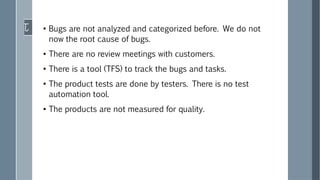
The document discusses a case study of a document management system (DMS) used in the Turkish defense industry. It notes that software quality assurance is important to prevent defects that could have financial or safety impacts, especially in critical domains like defense. The DMS discussed manages digital documents from creation to disposal. Initial findings found that a lack of software quality management in the DMS's development led to bugs like non-transparent watermarks obscuring map coordinates, compromising military operations. Establishing proper software quality management practices could help reduce bugs, ensure security and authorization, decrease delivery times, and improve the system's quality for defense users.











![●
A lot of bugs may occur in the DMS about
usage, permission and authorization system
however they can be avoided before the
disasters by using proper software quality
management.
●
We can diminish the software delivery time
by using software quality management.
●
There are other case studies in literature in
other domains. [1]
Results
[1] Madadipouya, Kasra. "Importance of software quality assurance to
prevent and reduce software failures in medical devices: Therac-25 case study."](https://image.slidesharecdn.com/presentationsevalcapraz-200507123150/85/A-Document-Management-System-in-Defense-Industry-Case-Study-15-320.jpg)