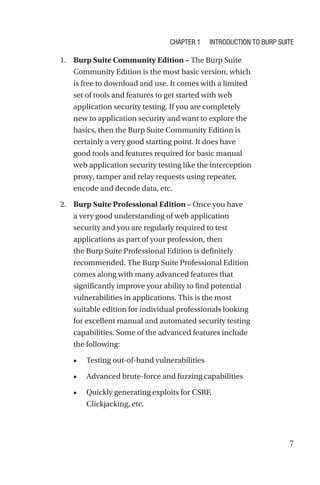
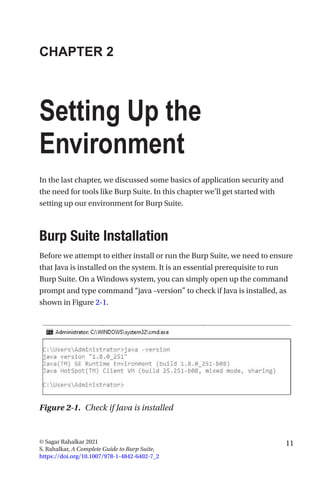
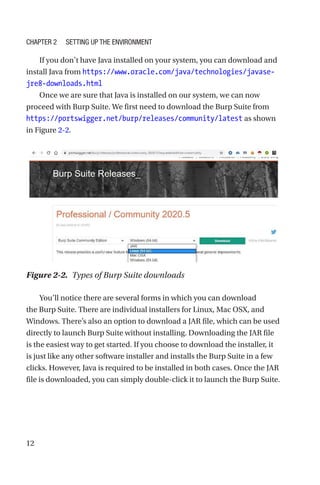
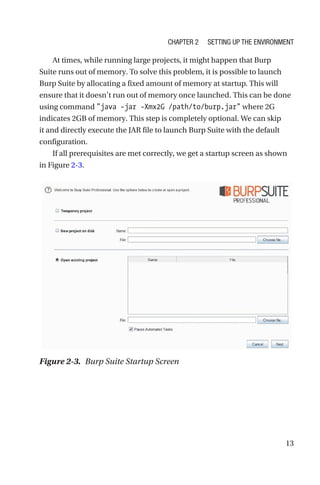
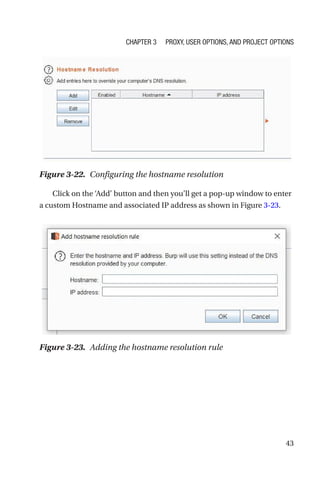
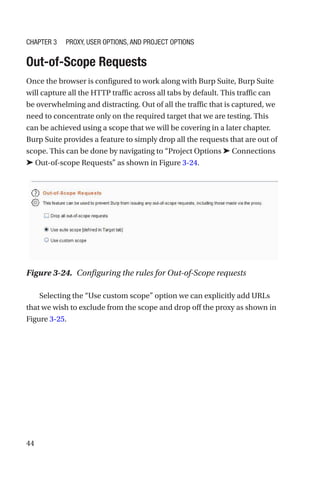
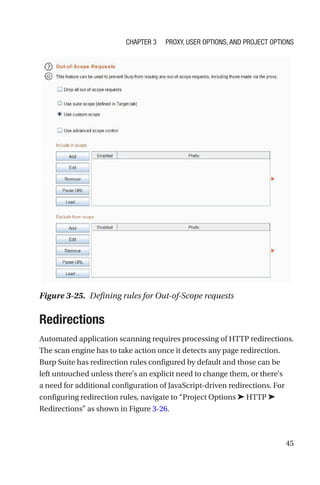
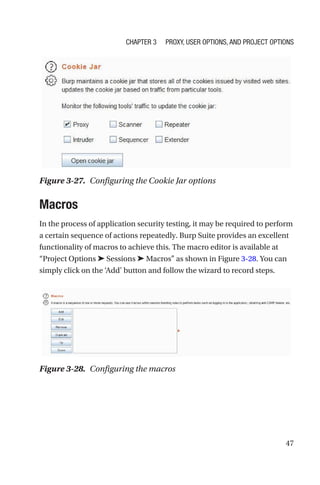
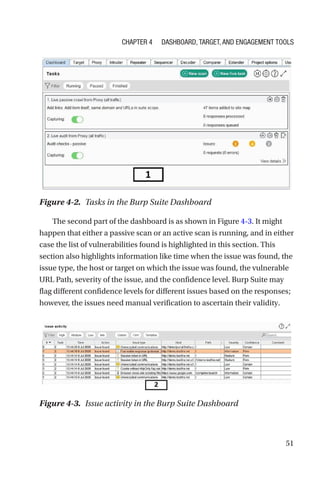
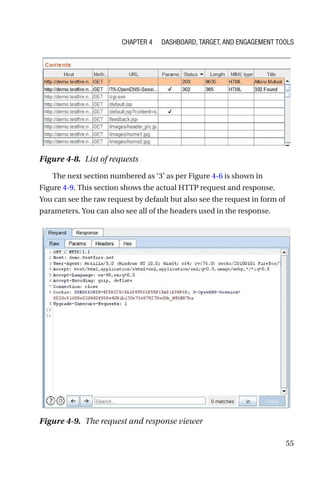
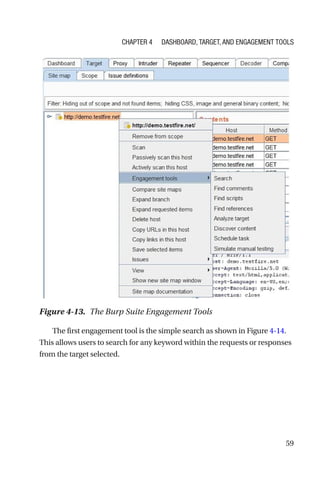
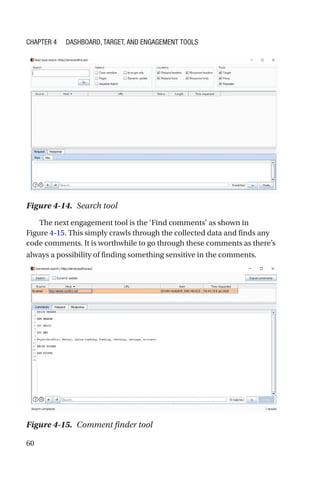
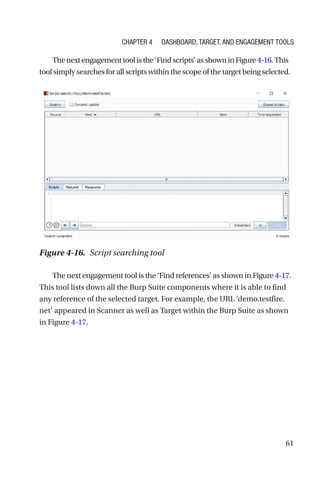
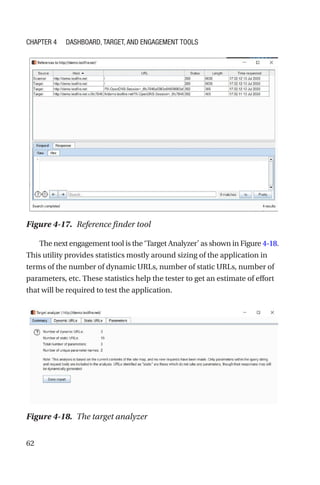
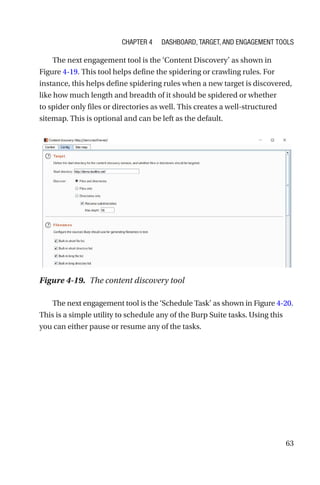
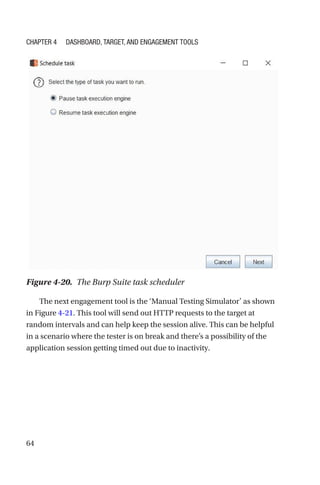
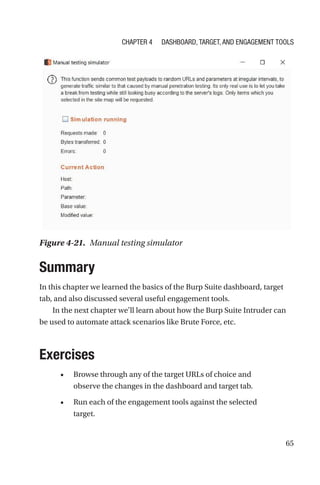
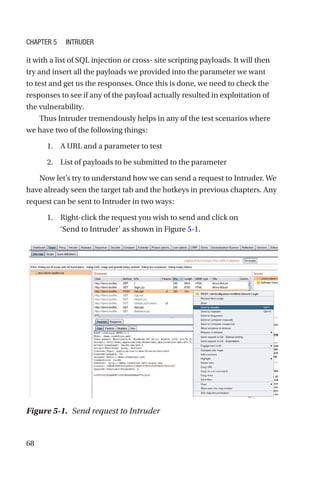
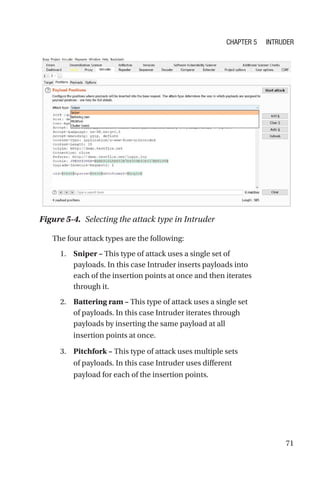
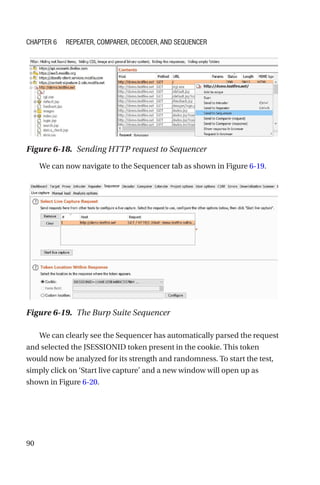
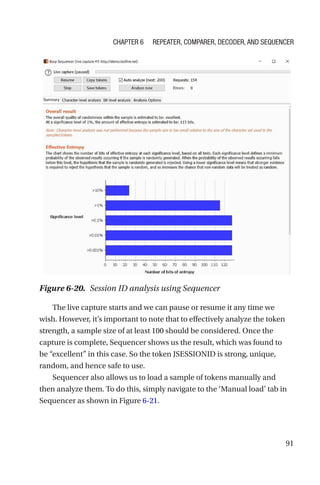
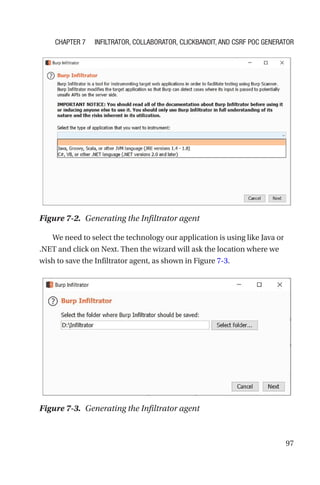
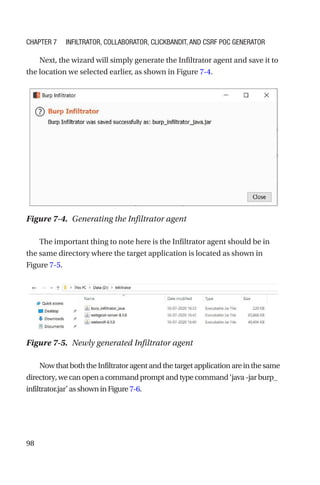
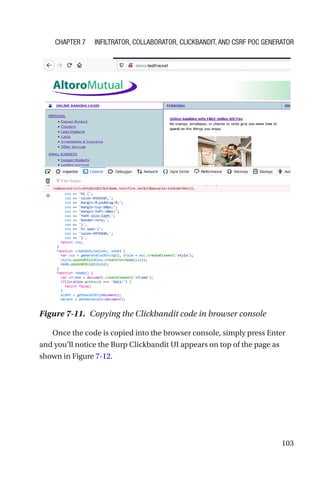
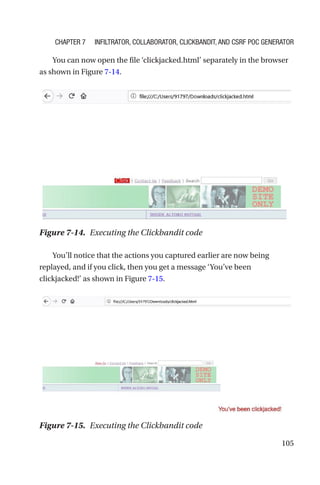
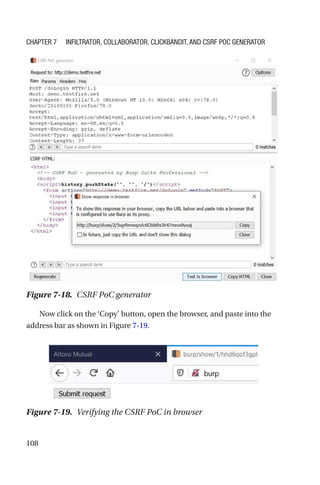
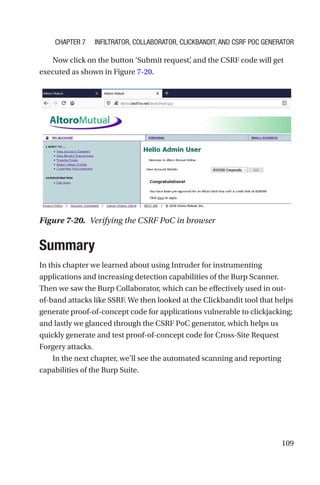
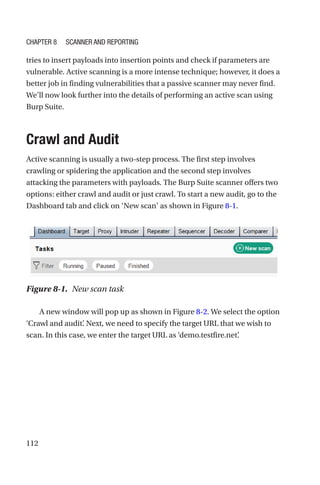
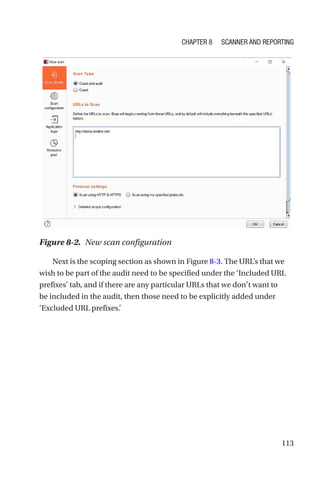
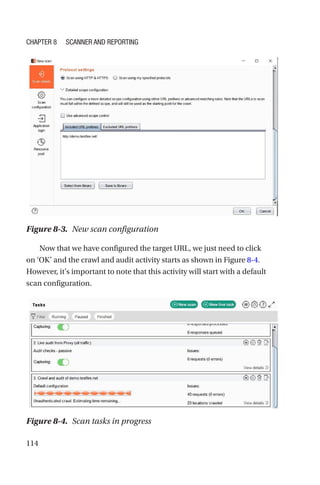
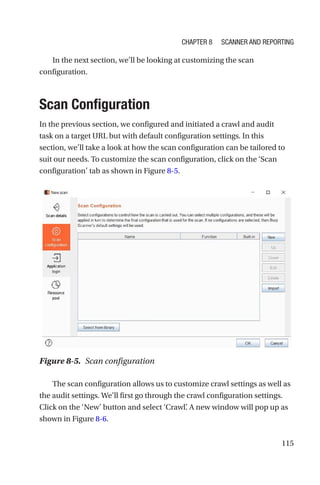
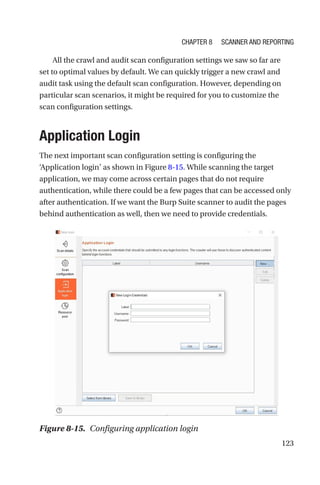
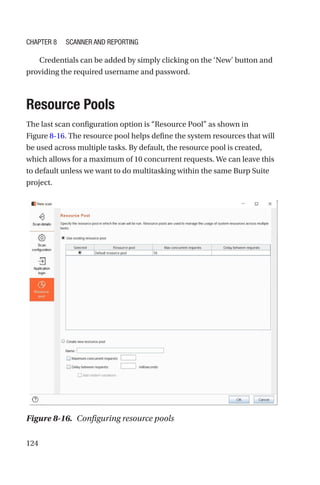
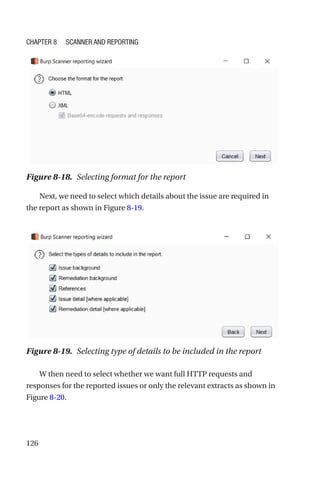
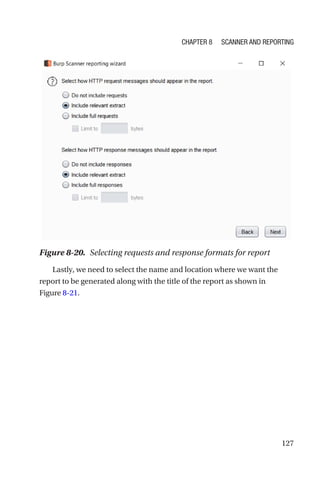
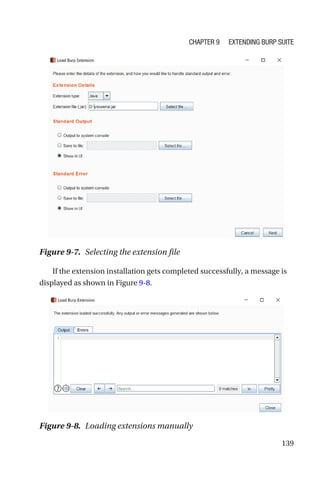
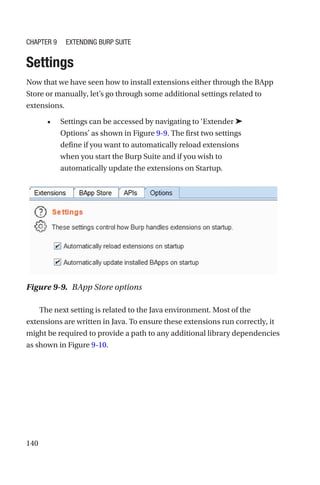
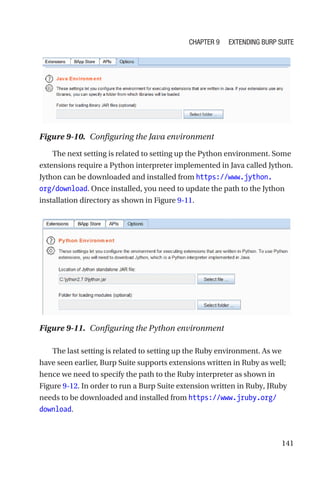
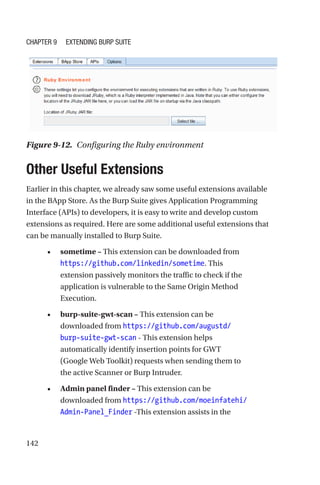
This document is a comprehensive guide to Burp Suite, a widely used tool for application security testing. It covers the basics of application security, setting up the testing environment, and provides in-depth explanations of various features and components of Burp Suite, including intruder, repeater, and scanner functionalities. The book also addresses the importance of identifying application vulnerabilities in today's complex ecosystem of web applications, APIs, and mobile apps.