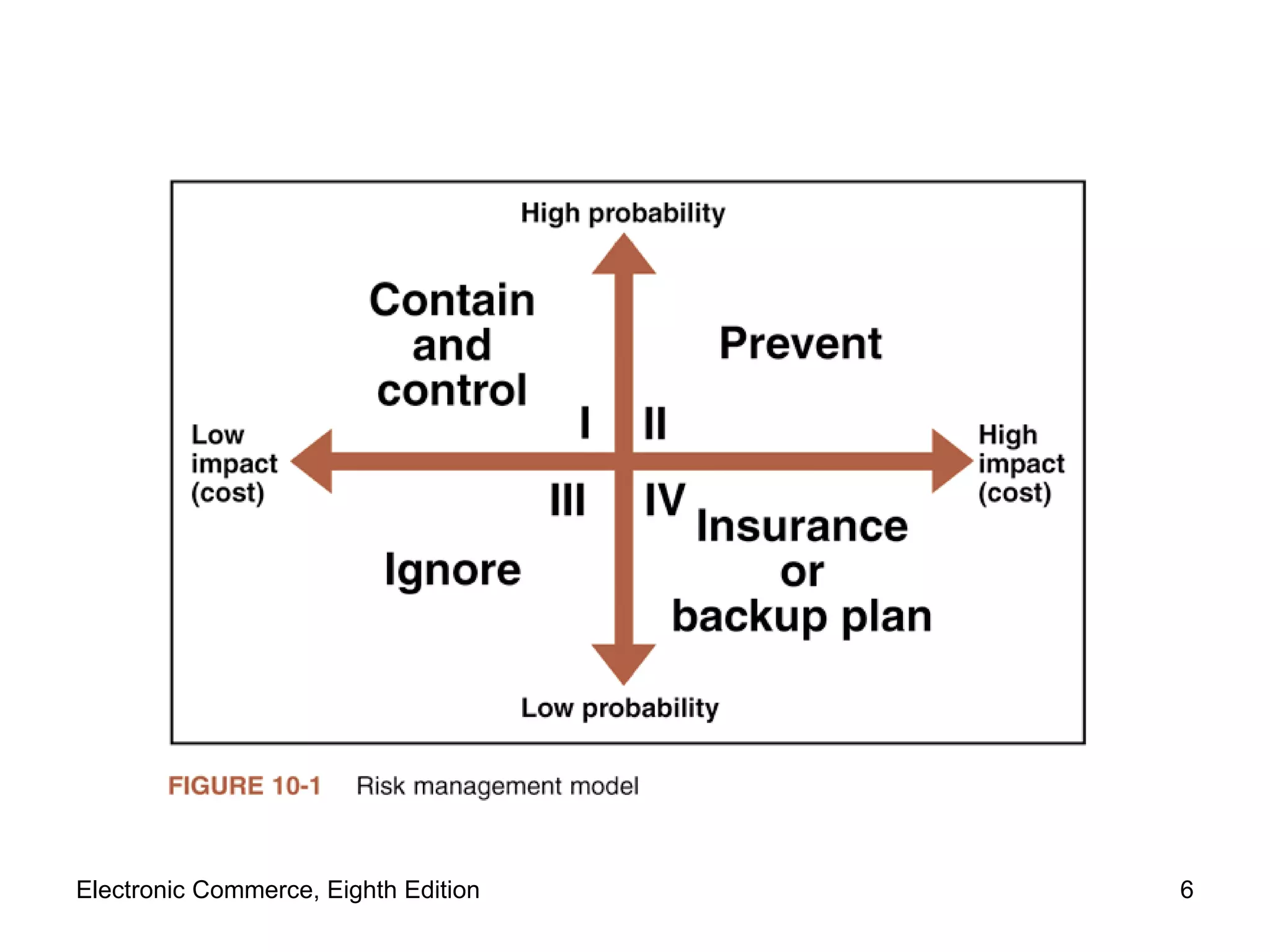
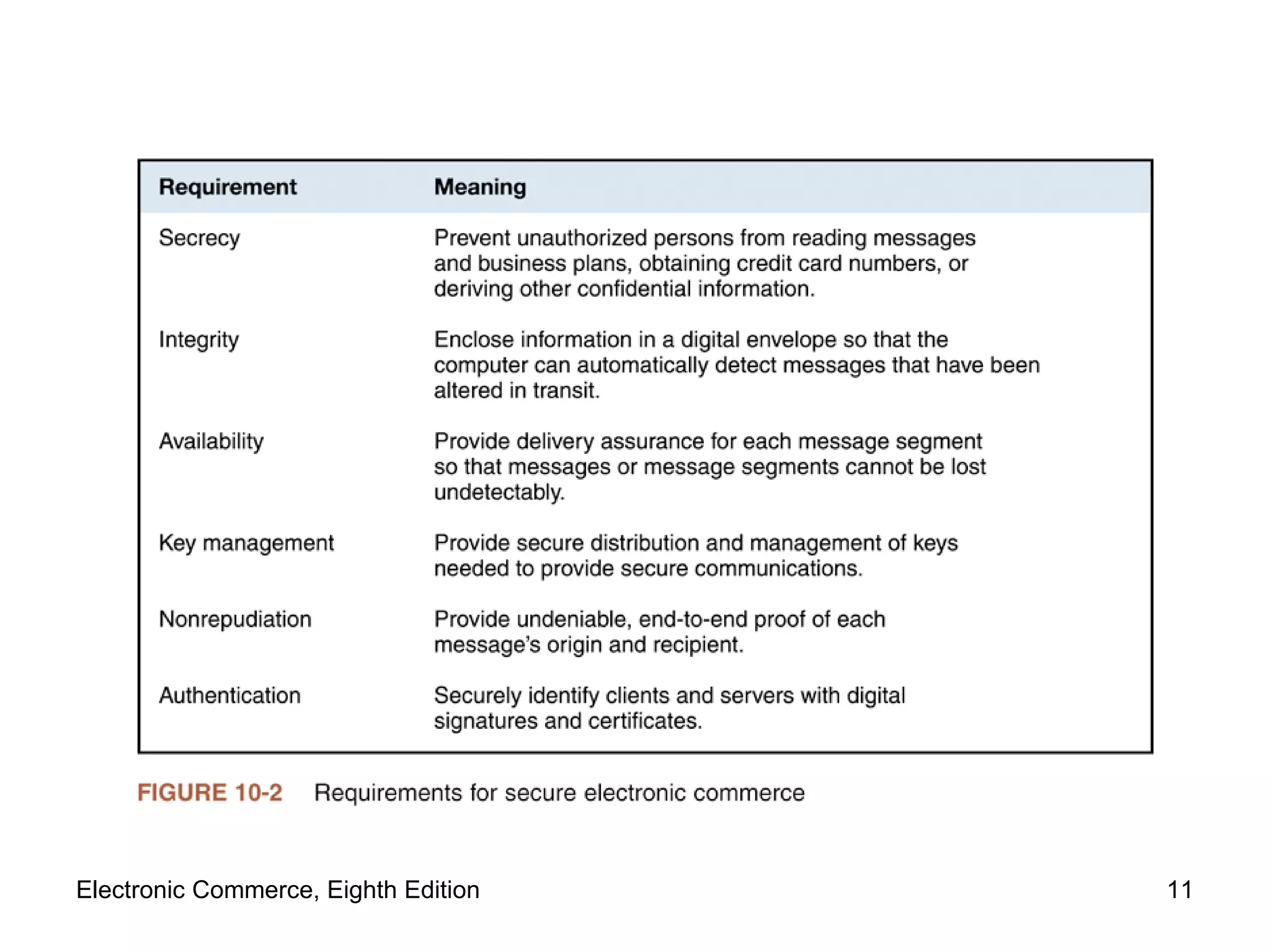
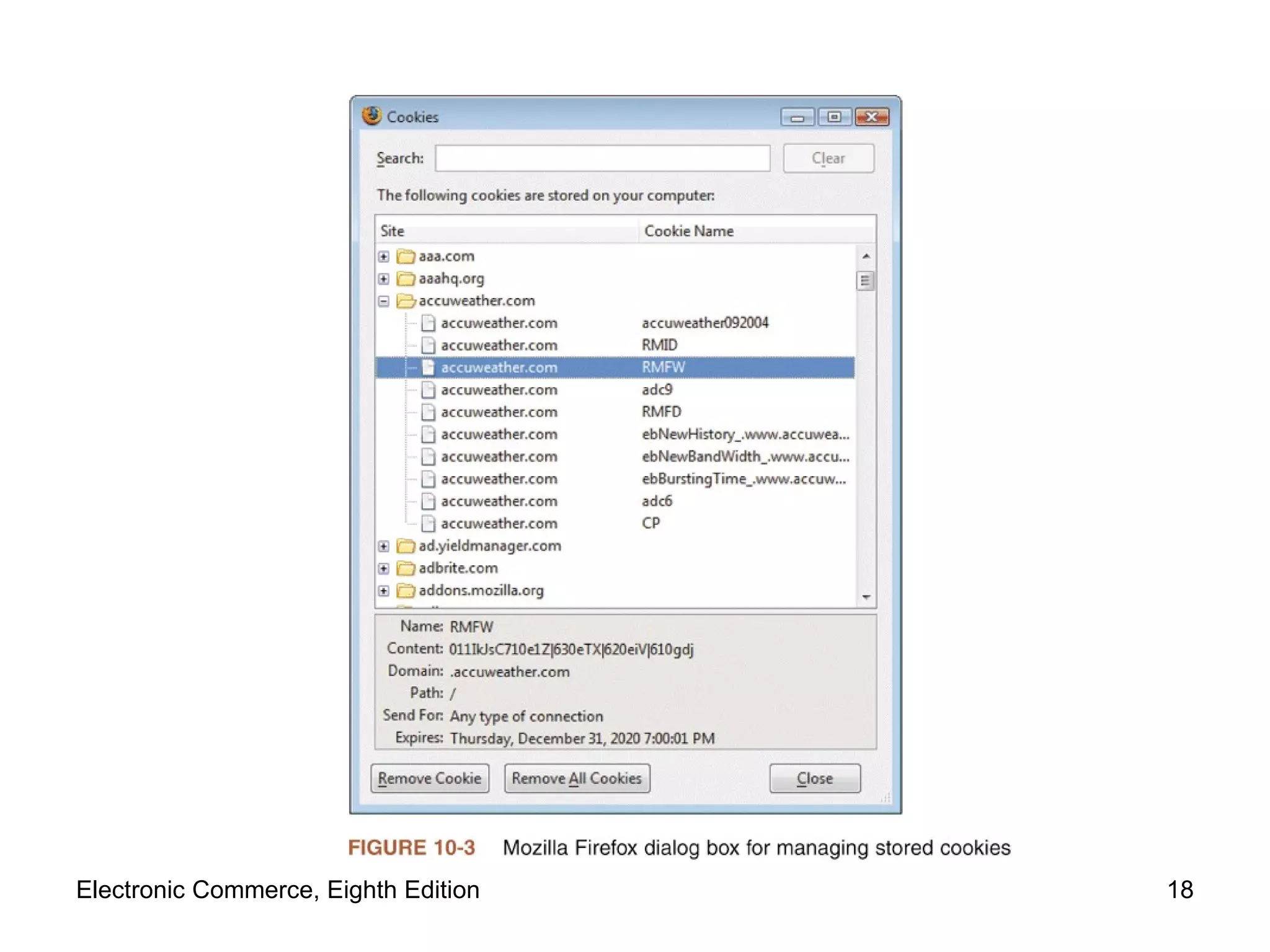
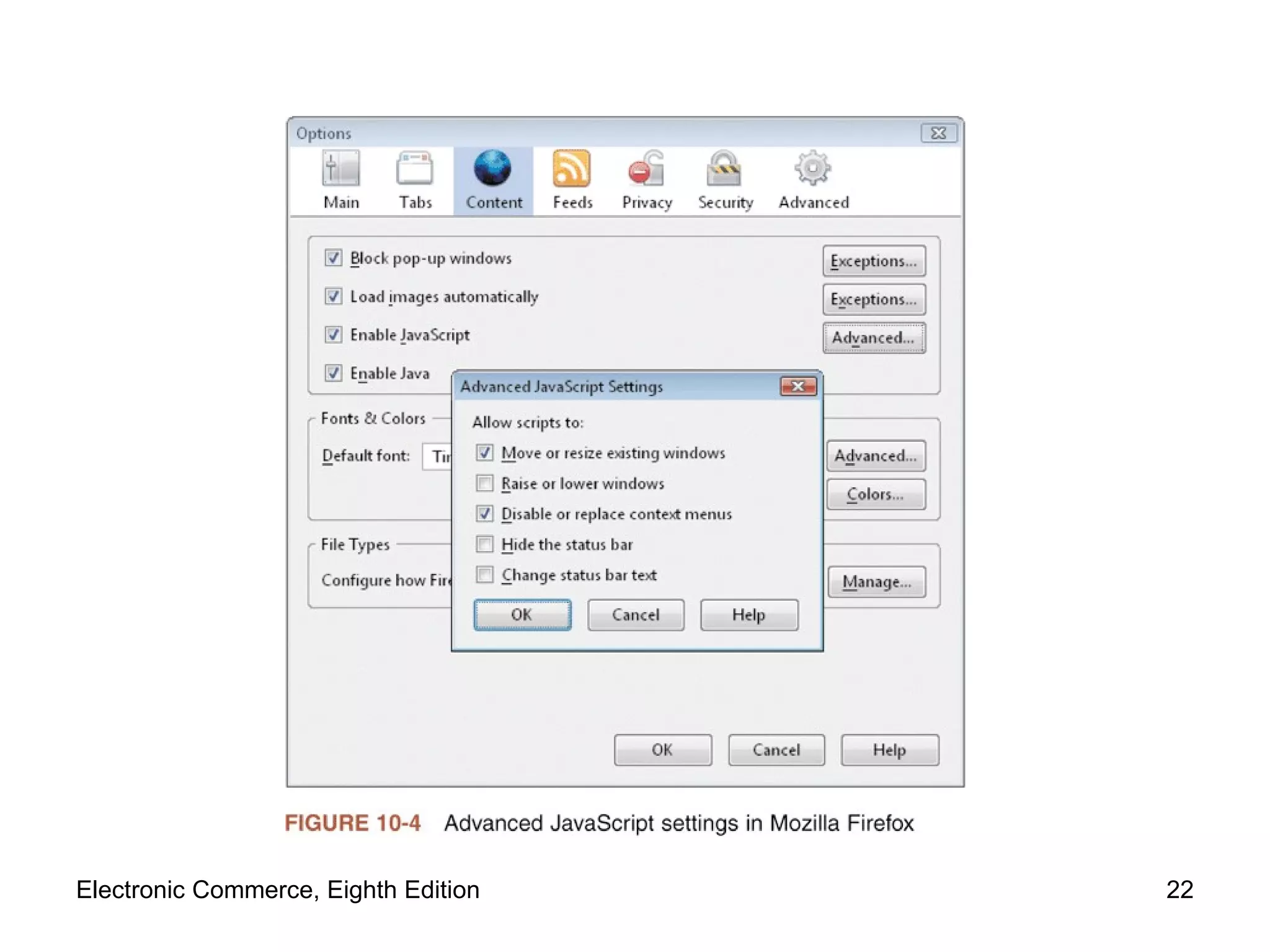
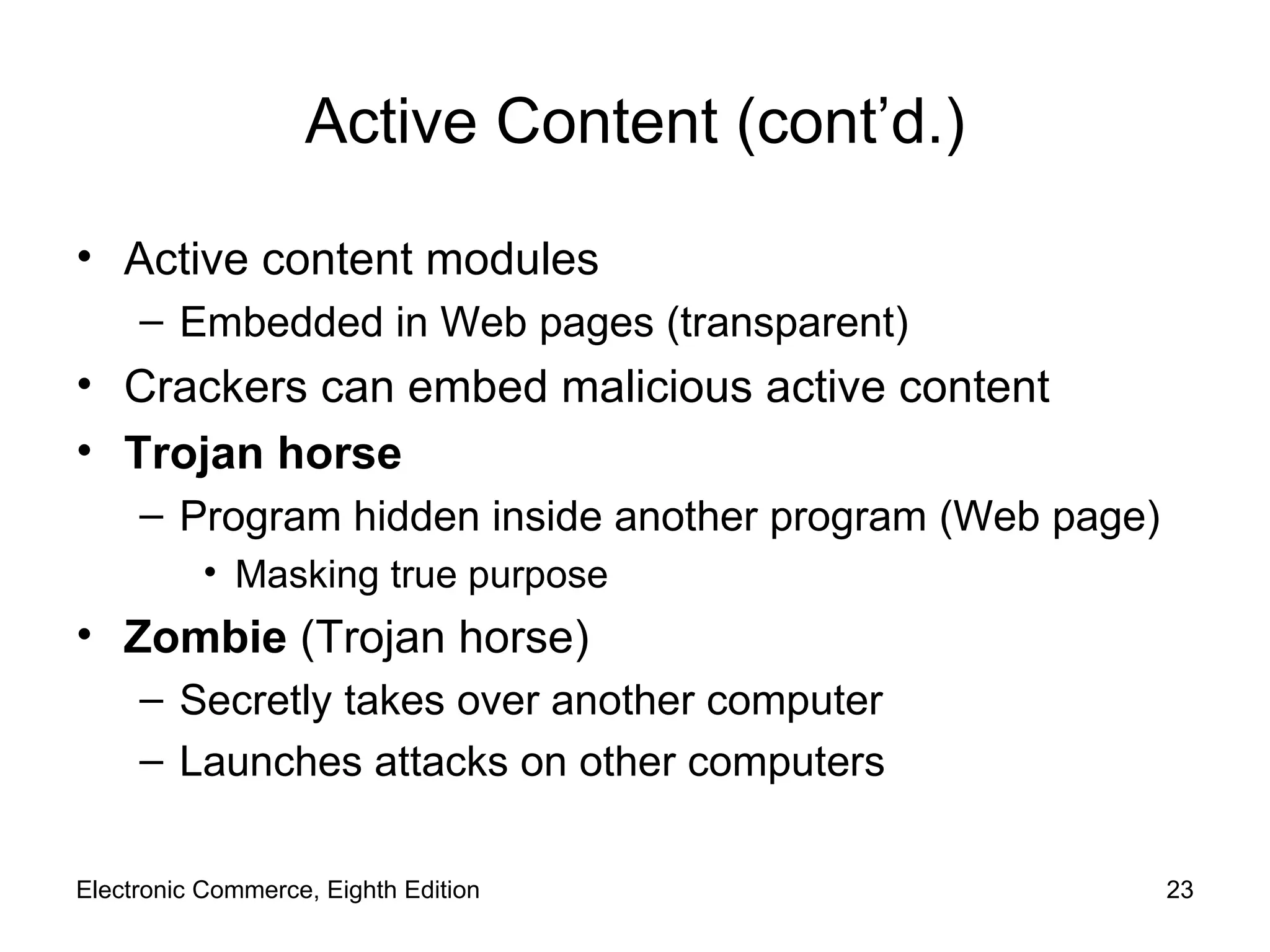
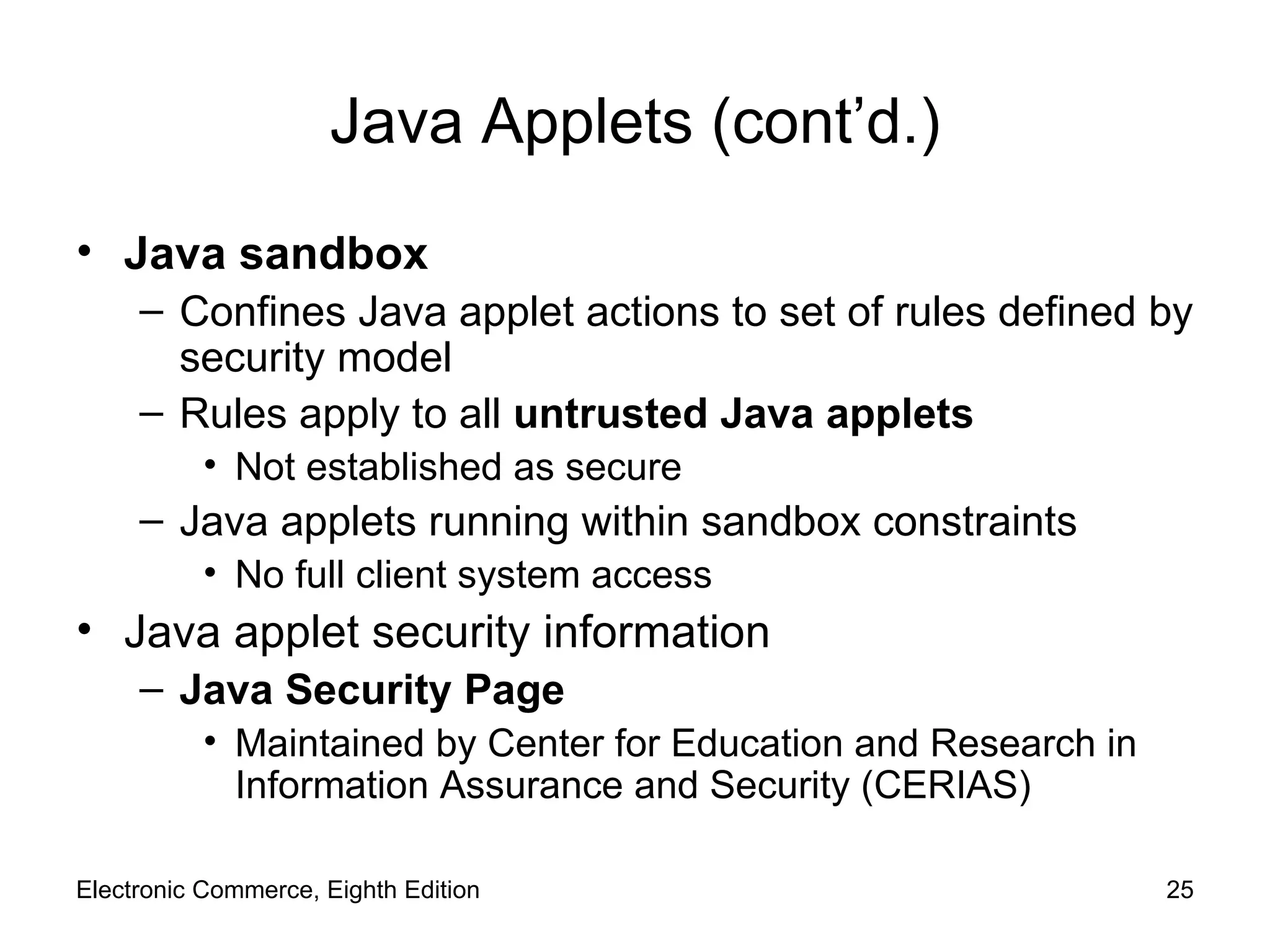
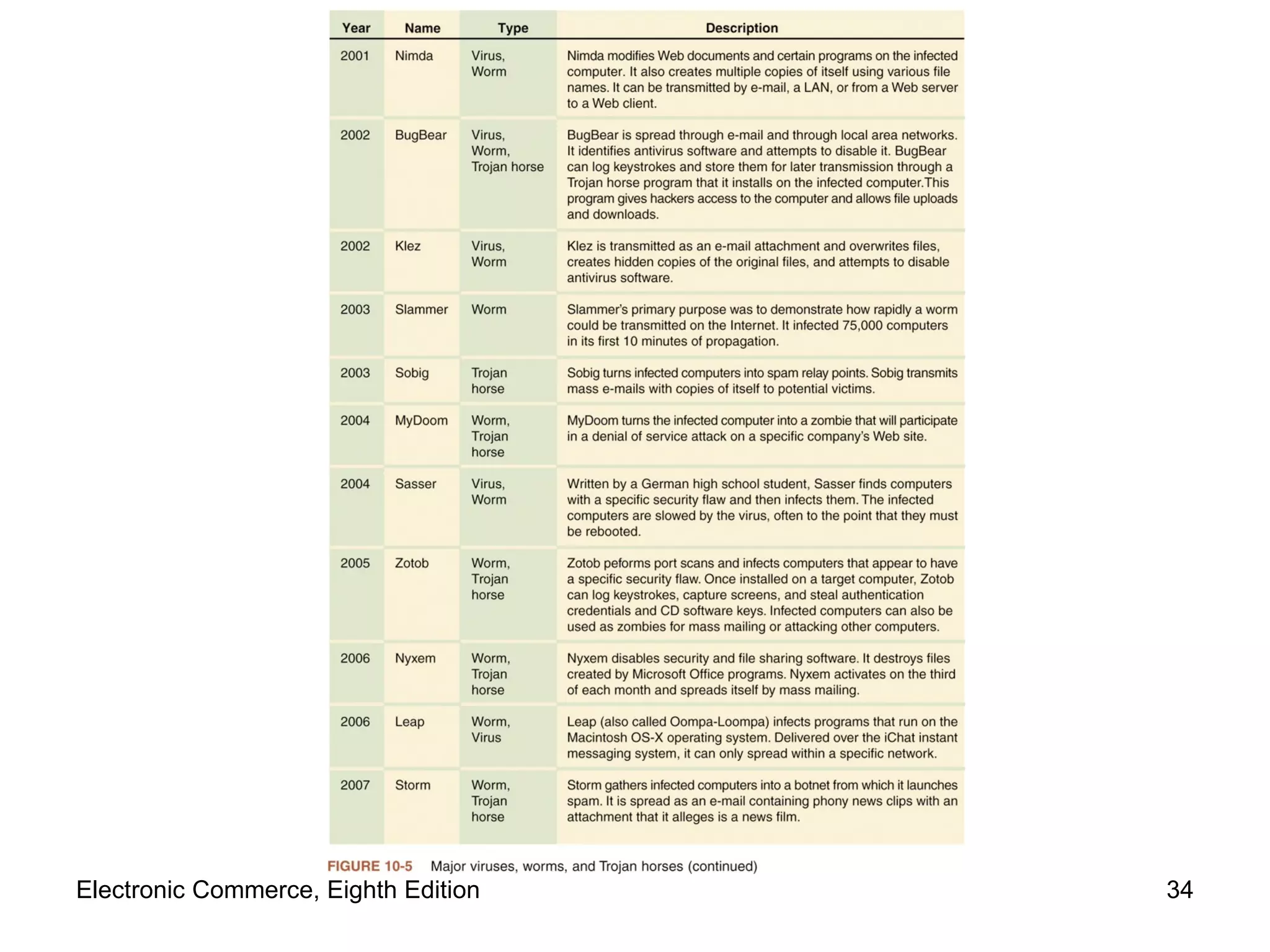
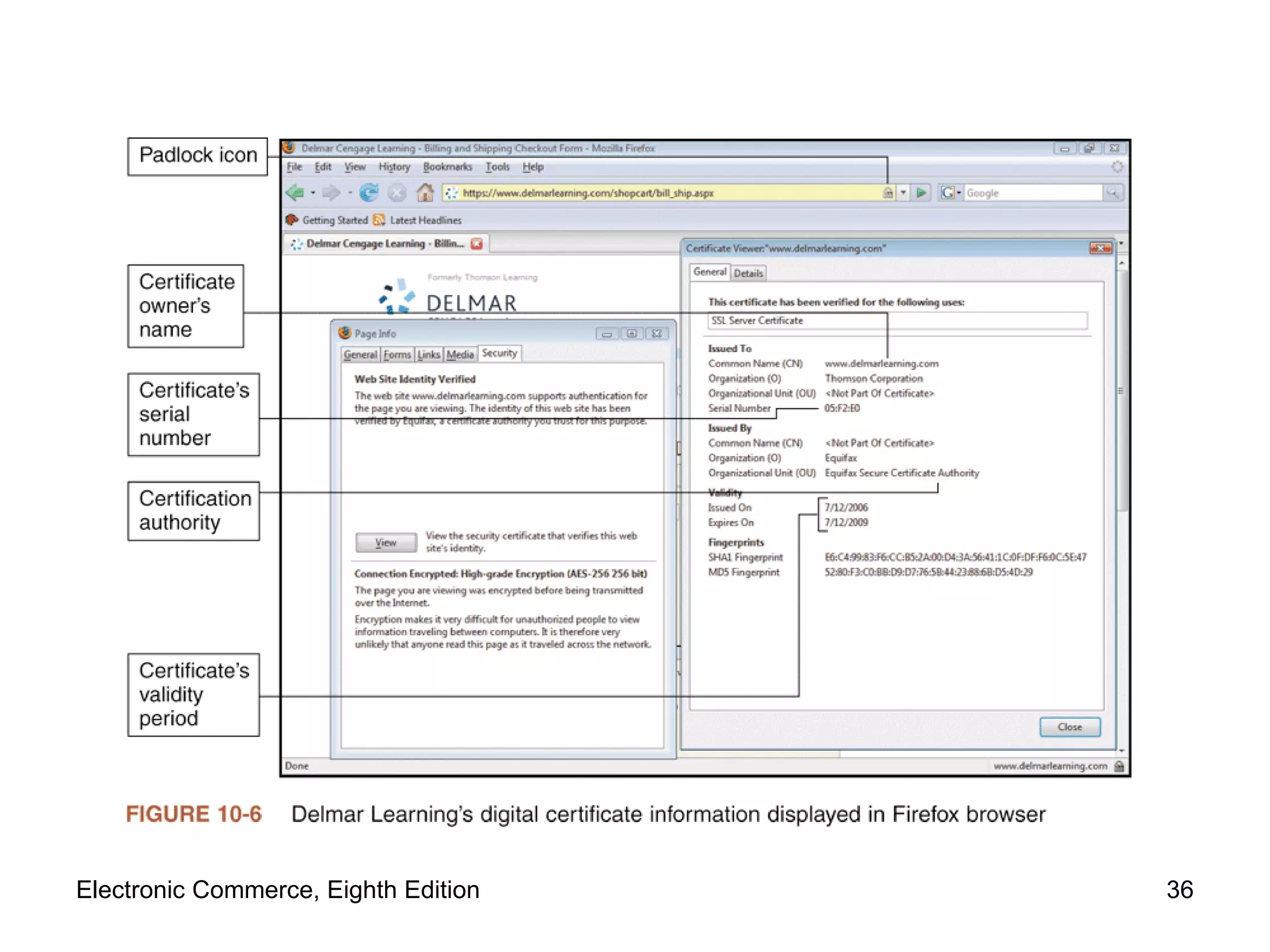
The document discusses security issues for electronic commerce including security for client computers, communication channels, and server computers. It covers topics like online security threats, managing risk, elements of computer security like secrecy and integrity, security policies, and specific threats from cookies, web bugs, active content like Java applets and scripts, graphics/plugins, and viruses/worms. Security aims to protect assets from unauthorized access, disclosure, modification or denial through measures that recognize and reduce threats.