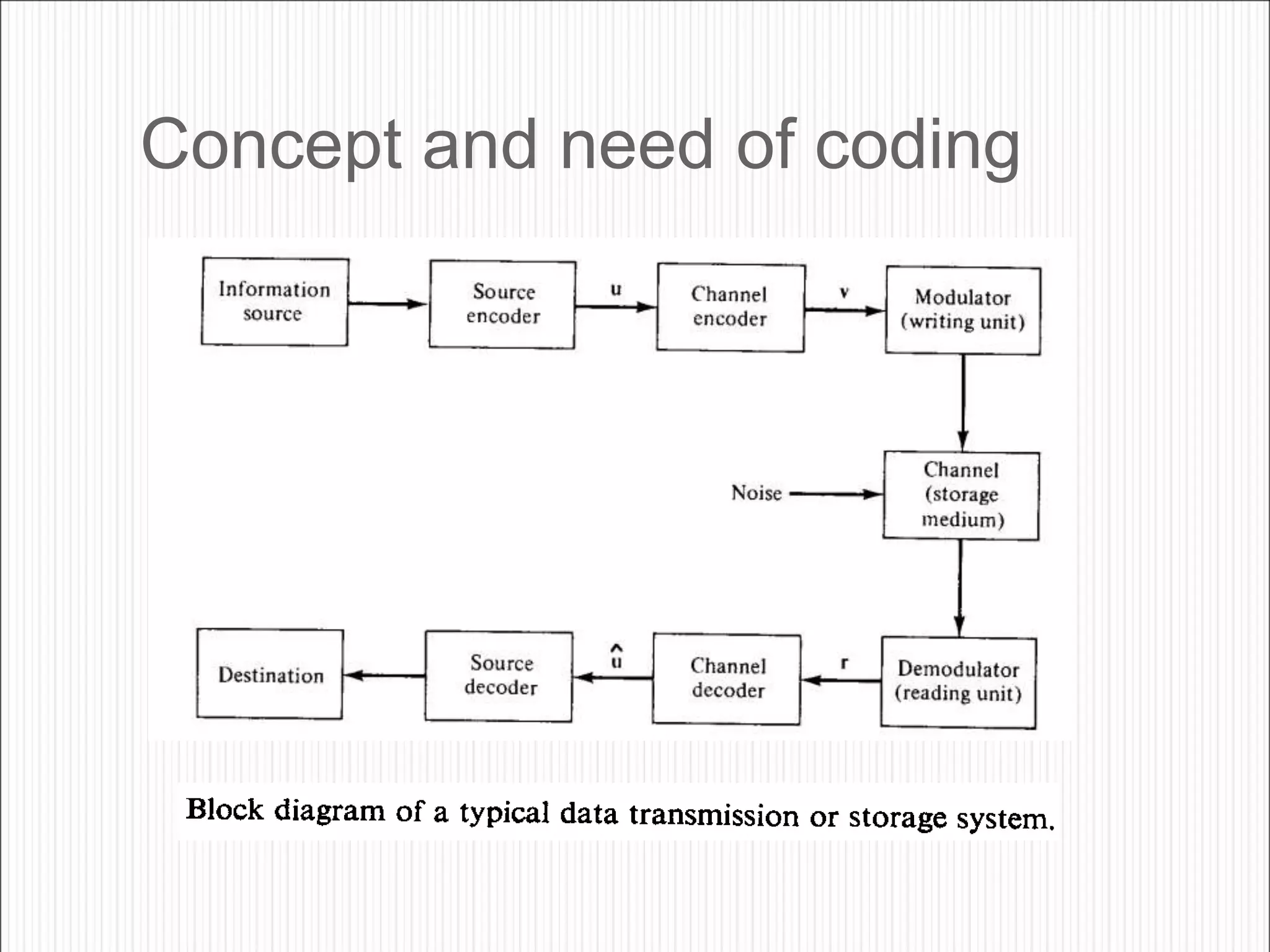
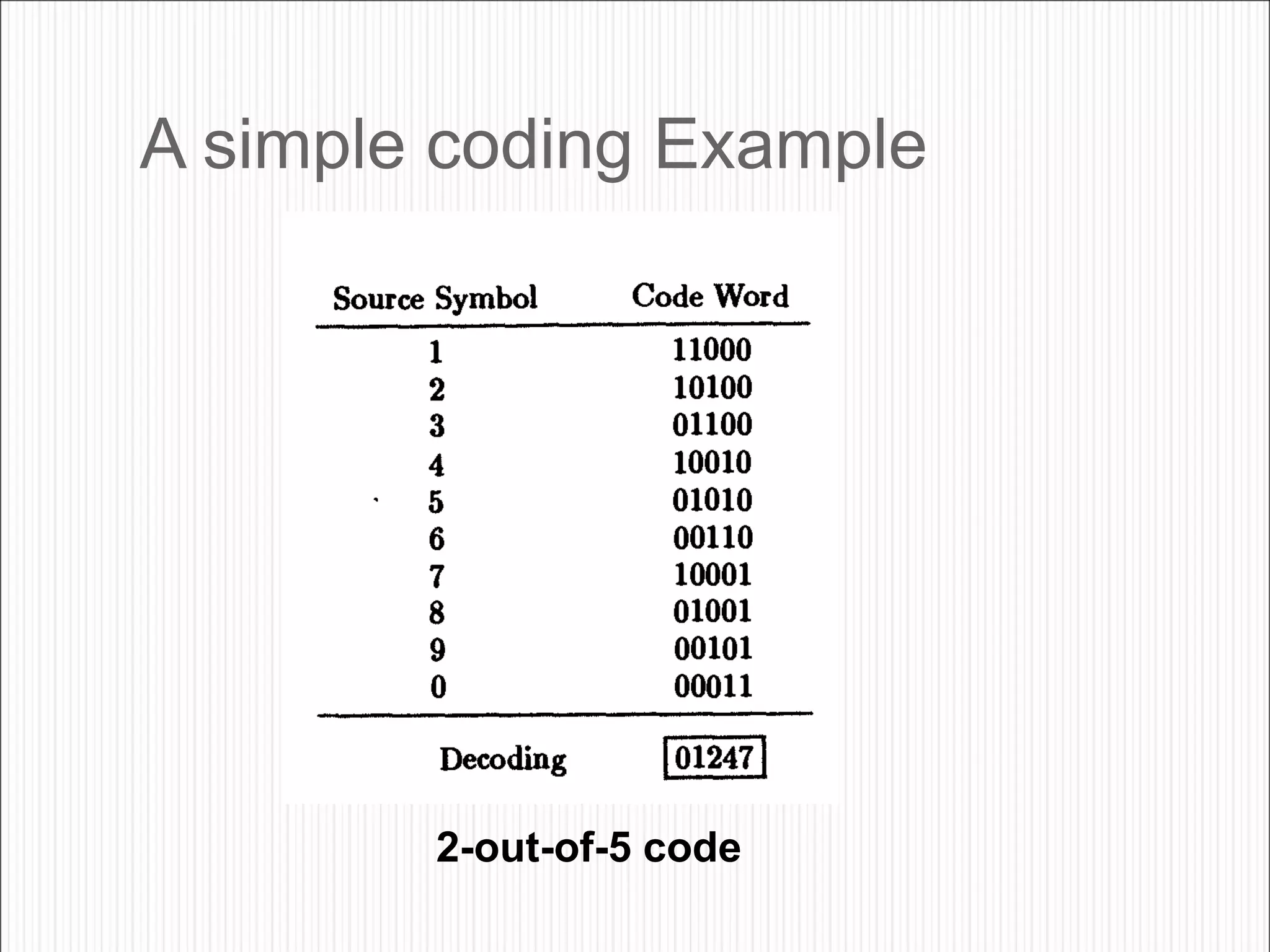
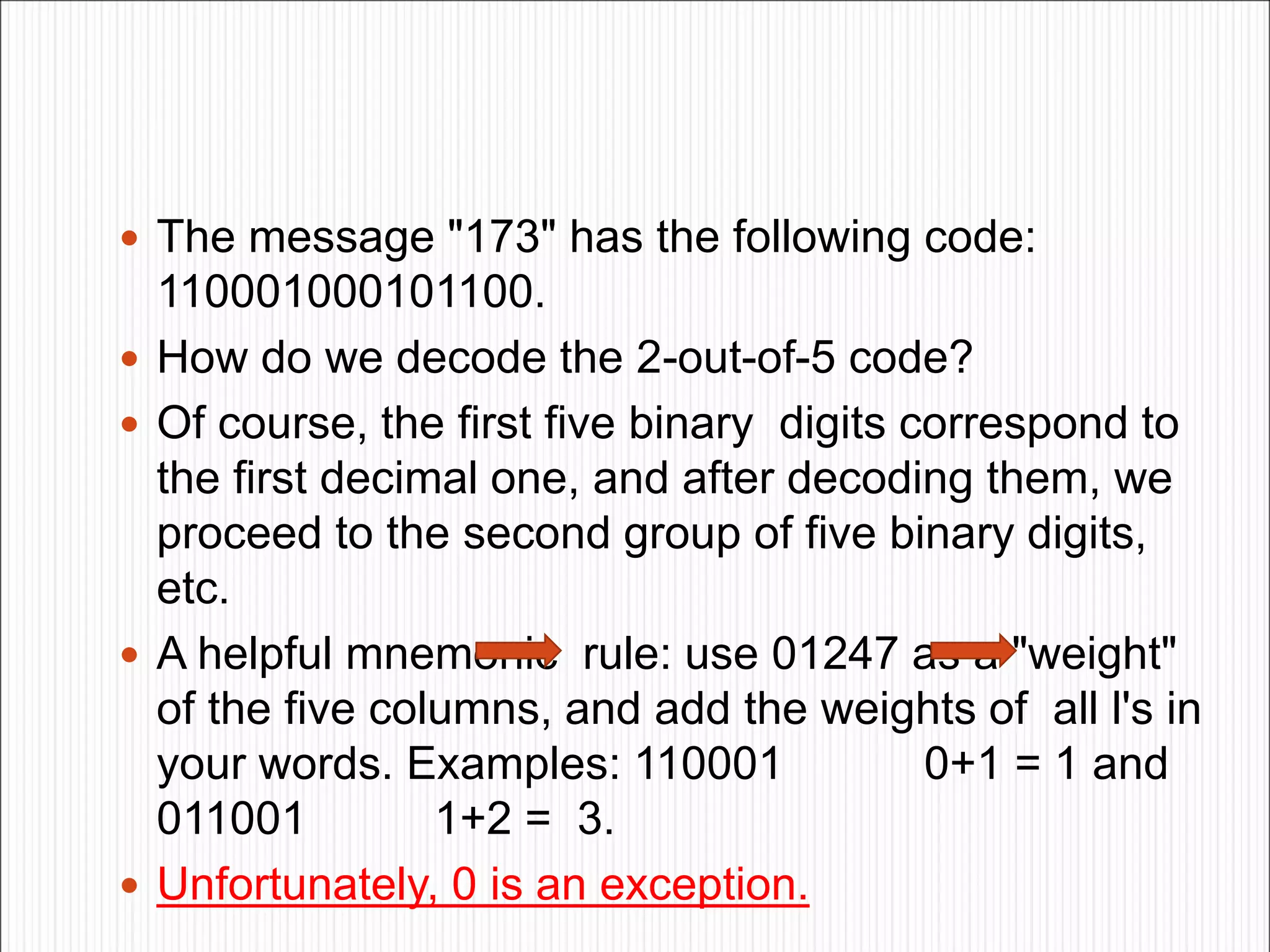
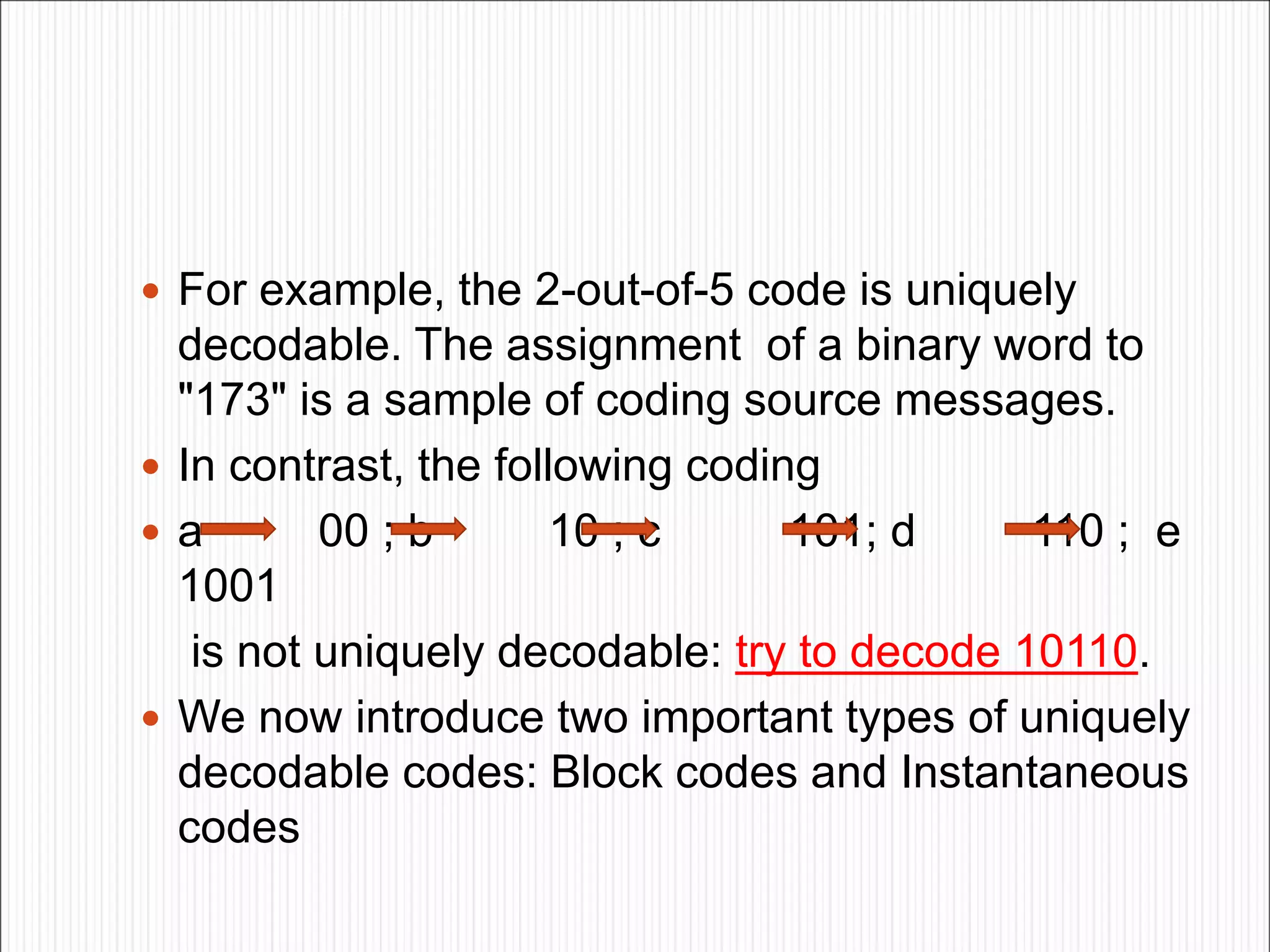
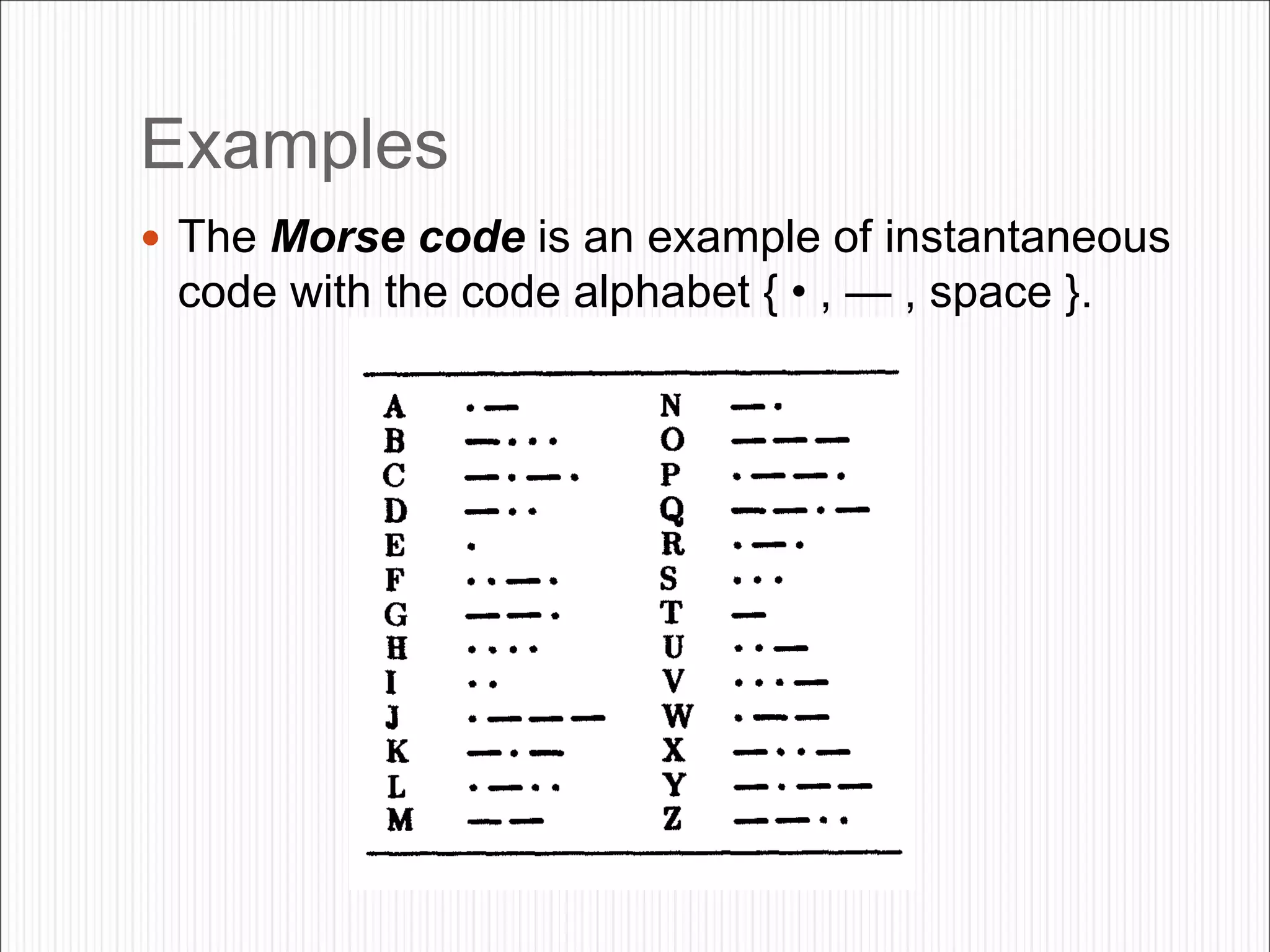
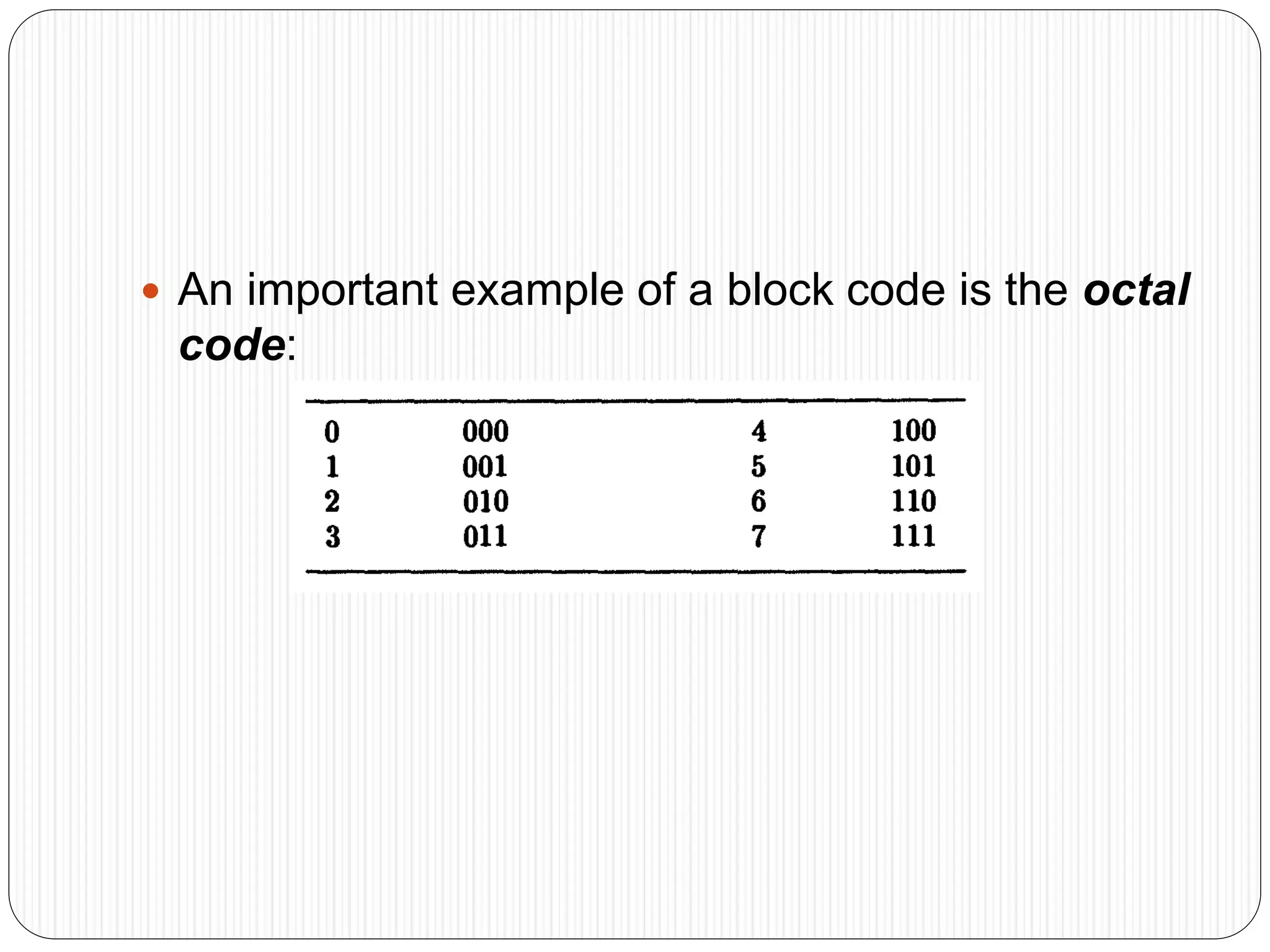
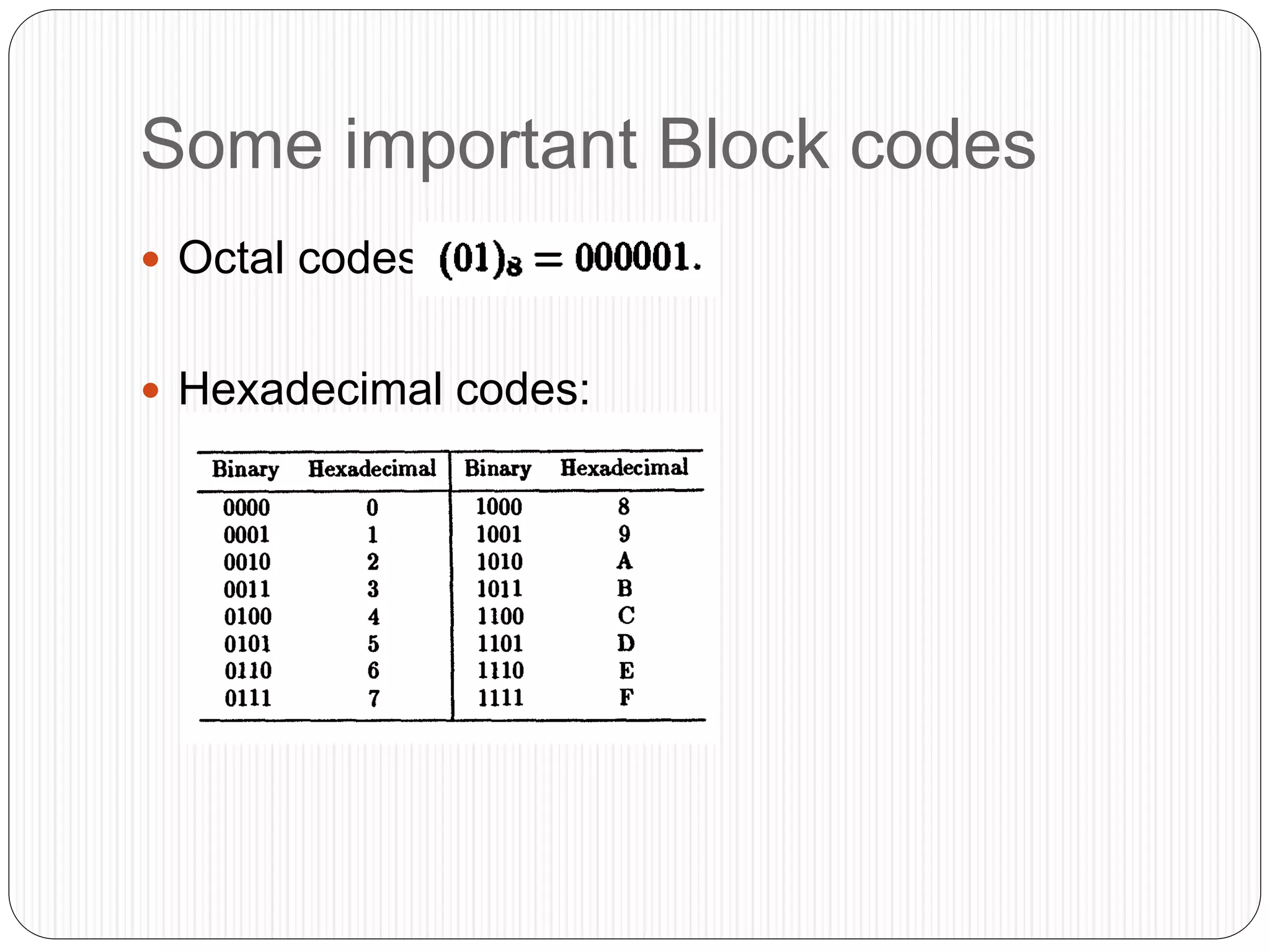
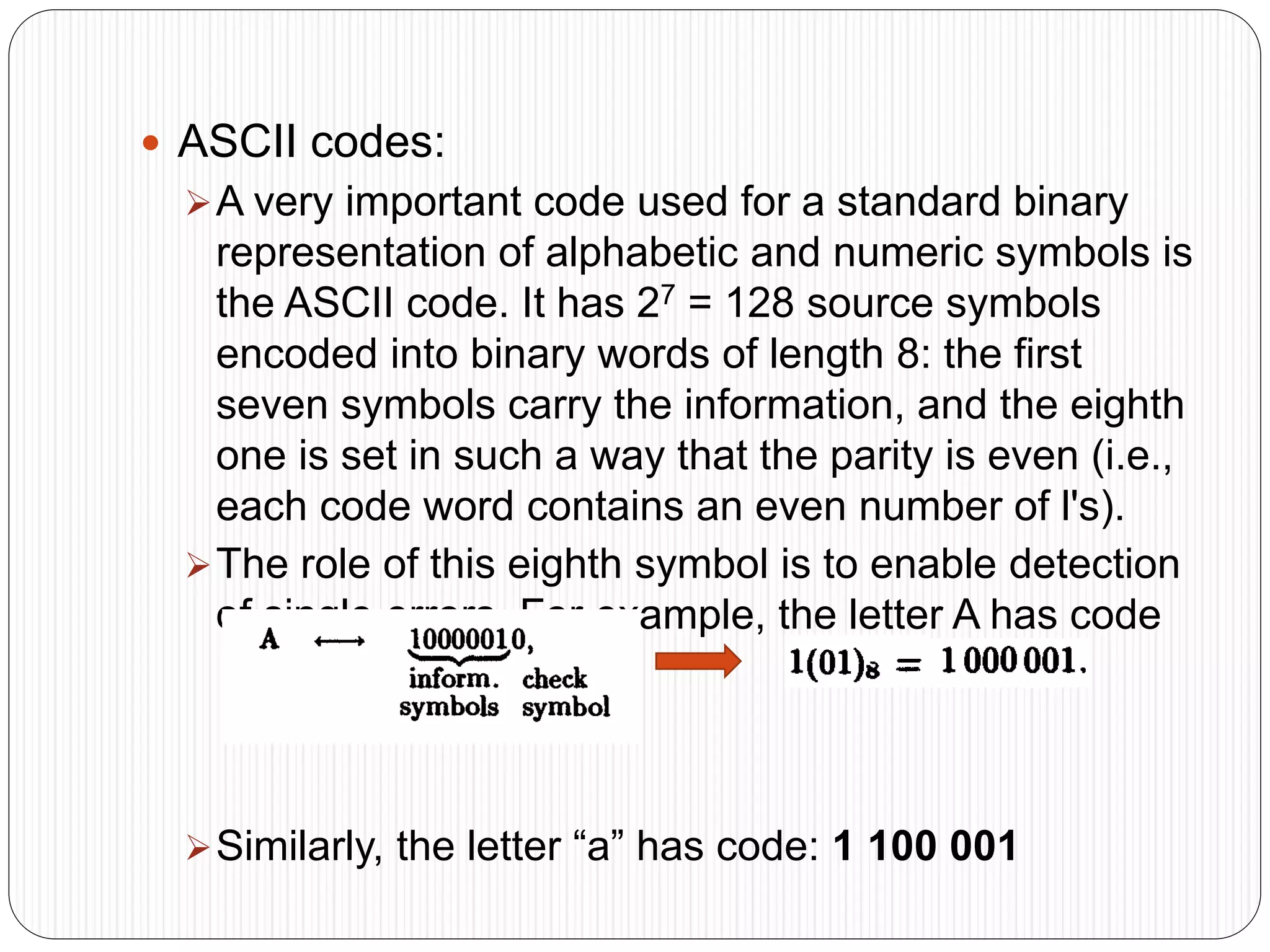
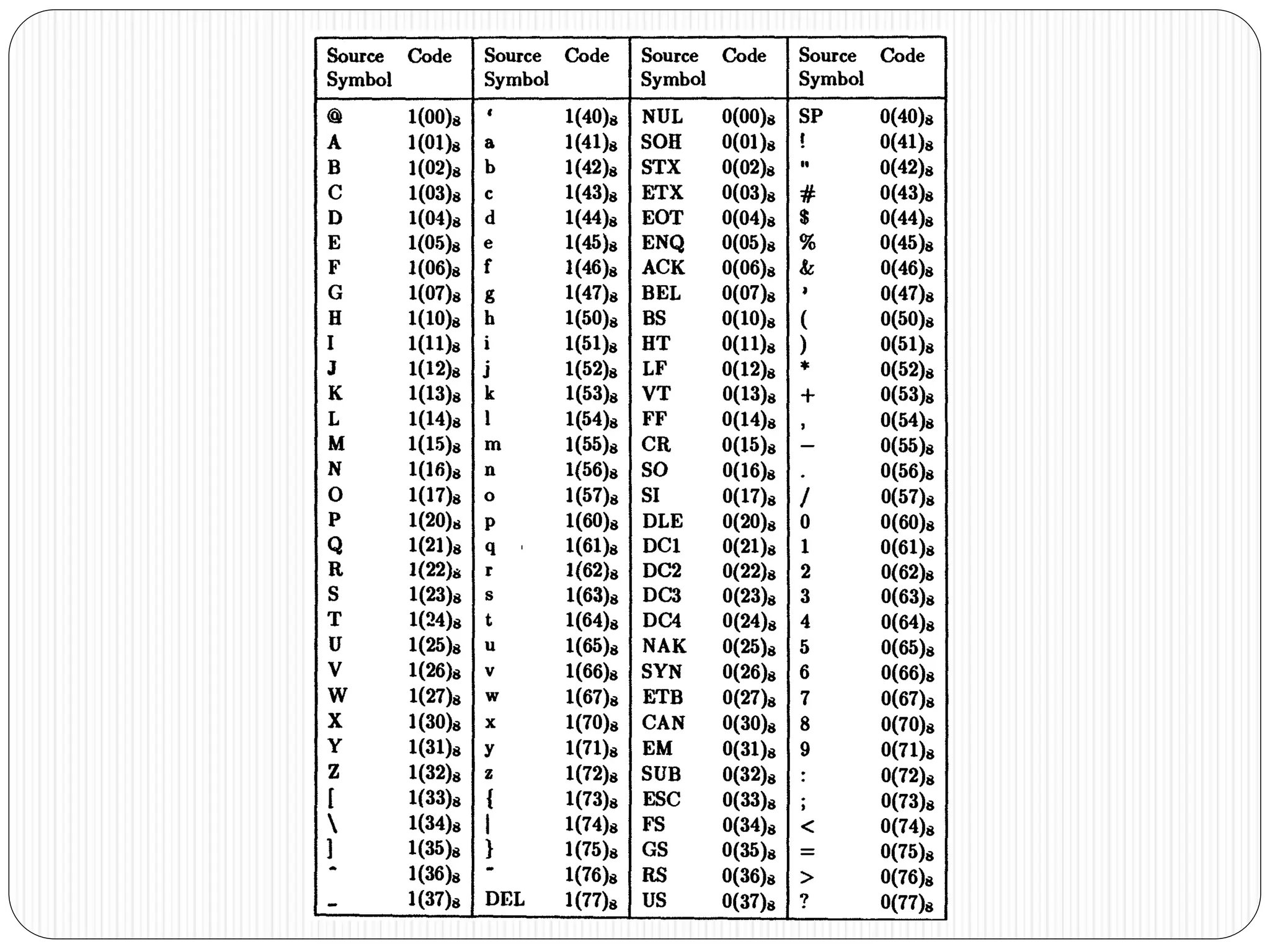
The document discusses the contents of an information theory and coding course, including source coding, channel coding, and cryptography. Source coding techniques that will be covered include Huffman coding, Shannon-Fano coding, arithmetic coding, and lossless vs. lossy compression. Channel coding techniques include linear block codes, cyclic codes, Hamming codes, BCH codes, Reed-Solomon codes, and convolutional coding decoding algorithms. The document provides examples of source coding, including a 2-out-of-5 block code to encode the message "173" and definitions of uniquely decodable and instantaneous codes. Important block codes like octal codes, hexadecimal codes, and ASCII codes are also mentioned.