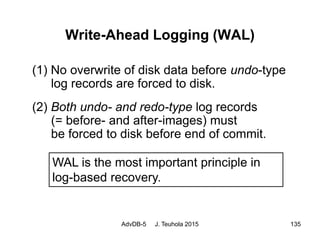
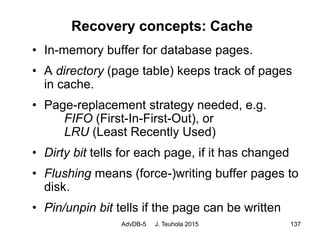
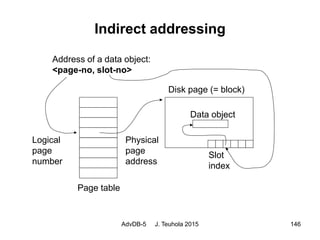
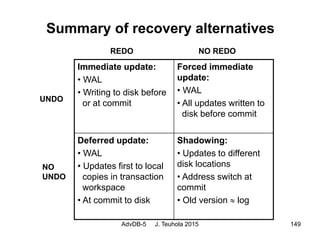
The document discusses database recovery techniques, including the use of logs, backups, caching, and rollback. It covers log-based recovery concepts like write-ahead logging (WAL), as well as alternative update and recovery approaches such as deferred updating, immediate updating, shadow paging, and different combinations of undo/redo operations. Recovery from catastrophic failures can use backups to reload the database and then apply redo log operations to reconstruct the effects of committed transactions.