This document summarizes an article from the International Journal of Computer Engineering and Technology that proposes a new Dynamic Expiration Enabled Role Based Access Control (DEERBAC) model for cloud computing environments. The DEERBAC model aims to provide fine-grained temporal access control policies and address security concerns in the cloud. It differentiates between activating roles and activating individual user roles. The model considers inheritance-only, activation-only, and inheritance-activation hierarchies with both restricted and unrestricted types. While non-minimal, the DEERBAC model aims to provide flexibility with minimum complexity for defining constraints and efficient role assignments at large scales. The model is evaluated on Amazon Cloud and results show it can achieve scalable and

![International Journal of Computer Engineering and Technology (IJCET), ISSN 0976-6367(Print),
ISSN 0976 - 6375(Online), Volume 4, Issue 5, September - October (2013), © IAEME
facilitate a rapid and highly efficient system with minimum resource management activities and least
interaction of service providers.
In cloud computing one of the predominant security issues is the access control of
information and system security. In order to control the various time-sensitive activities numerous
cloud applications like management of workflow and real-time operational databases, the access
control specifications are required to be enhanced with the optimum temporal constraints. The
presented research work has been motivated by the requirement of a highly robust and effective
access control approach that could meet and can alleviatethe security concerns in cloud environment
with raised trust level for numerous cloud based applications and service segments. One of the
predominant and efficient approach for accomplishing cloud security requirements in organization is
ܴ ݈݁െ ܾܽ ݈ݎݐ݊ܿ ݏݏ݁ܿܿܽ ݀݁ݏሺܴܥܣܤሻ that fulfills various security requirements [1], [2], [3], [4].
As compared to the existing traditional approaches of discretionary and mandatory access control
ሺܥܣܯ ݀݊ܽ ܥܣܦሻ system [5], [2], [6], [7], [8] the ܴ ܥܣܤmechanism can be much fruitful and
effective solution. In case of cloud environment of heterogeneous nature like Internet [9], [11],
ܴ ܥܣܤsystem framework might be much effective solution for secure interpolation purposes.
On the other hand the time factor plays a vital role for management of time-sensitive
access controls. The user creation with role assignment and its optimization is also a key
aspect of cloud computing which is required to be optimized. Meanwhile, a better example
for time management could be the management of workflow which do encompasses the
critical deadlines for completion of invocations. In order to meet such requirements the
time-based or period oriented techniques are suggested [12] [13], [14], [15]. On the other hand in
order to manage the roles and the user permission a highly effective and efficient system
is required that could manage the users with their respective roles assignment and cloud security.
In order to achieve these all expectations here in this paper we have proposed
a ݈݁݀ܯ ݈ݎݐ݊ܿ ݏݏ݁ܿܿܣ ݀݁ݏܾܽ ݈݁ݎ ݈ܾ݀݁ܽ݊݁ ݊݅ݐܽݎ݅ݔ݁ ܿ݅݉ܽ݊ݕܦሺܥܣܤܴܧܧܦሻ model that
emphasizes on the highly effective and responsible system constraints as well as time oriented user
creation and role assignment system that could meet the requirement of highly efficient and
productive system model for competitive cloud environment. These all considered constraints
characterize themselves effective with the implementation of orthogonally with every aspects of role
based Access control mechanism such as role creation, user definition, role assignment, activation of
specific roles, defining roles for users, assignment of role permissions.
Specifically, the proposed ܥܣܤܴܧܧܦsystem differentiates between the activation or
enabling of roles and the activation of individual roles. In this approach a specific role is defined and
is activated only in the circumstance when a particular user is permitted to get it. An activated role
becomes functional when the user is permitted for access in the duration of defined session. The
roles could not be activated by the users in case of disabled role session. Hence, the considered or
specified model does specify the roles on after enabling or disabling when it can/cannot be assumed
by users.
In the proposed system model we have considered three dominant kinds of hierarchy that
strengthens the system model with higher efficiency and security enhancement. These are
inheritance-only hierarchy ሺ ܫെ ݄݅݁ݕ݄ܿݎܽݎሻ, activation-only hierarchy ሺ ܣെ ݄݅݁ݕ݄ܿݎܽݎሻ and
݄݅݊݁ ݁ܿ݊ܽݐ݅ݎെ ܽܿ ݕ݄ܿݎܽݎ݄݁݅ ݊݅ݐܽݒ݅ݐሺ ܣܫെ ݄݅݁ݕ݄ܿݎܽݎሻ. The first hierarchy permits the semantics
for permission-inheritance while the second refers semantics for activation of roles only and the last
considered and developed hierarchy permits both the role activation as well as permission
inheritance. Considering these all, here in this system model we have implemented these all three
hierarchies which have been further divided into two categories called as restricted and unrestricted
kind of hierarchy [16], [17].
In general issues allied with any access control model or frameworks with rich constraint
language are the factor of minimality and its expressiveness where the minimality refers the
116](https://image.slidesharecdn.com/50120130405015-131024062024-phpapp02/85/50120130405015-2-320.jpg)
![International Journal of Computer Engineering and Technology (IJCET), ISSN 0976-6367(Print),
ISSN 0976 - 6375(Online), Volume 4, Issue 5, September - October (2013), © IAEME
minimum status of set of constraints and it is a vital criterion that determines the effectives of the
minimal model over the nonminimal models. Here in this paper we have proposed and developed a
highly robust framework that addresses the existing problems of minimality, expressiveness, user
creation, role generation and respective role-permission with the expected minimum expiration
period in ܴ ܥܣܤframework. The proposed ܥܣܤܴܧܧܦmodel has performed better in terms of highly
efficient role creation and multiple role assignments per user in defined minimum time even without
violating the security aspects in comparison with ܥܣܤܴܶܩmodel [17]. Considering the power of
expressiveness, here in this work we have illustrated that the numerous sets of model constraints
could be used for generating a family of ܥܣܤܴܧܧܦsystem model with similar expressive power.
Even being a non-minimal set of constraints in ܥܣܤܴܧܧܦcloud framework here in this work has
established itself as more beneficial in terms of numerous advantages like least complexity, better
manageability and the feasibility in the characterization of policies of access control management. It
has illustrated that the constraints of timing for individual role assignments for users could be easily
substituted by the temporal constraints for effective role enabling activities.
The proposed and developed system architecture ܥܣܤܴܧܧܦcan be significant for examining
and investigating the performance of the model with minimality factor, expressiveness, and
complexity, feasibility in user creation, highly efficient and optimum user creation, role generation
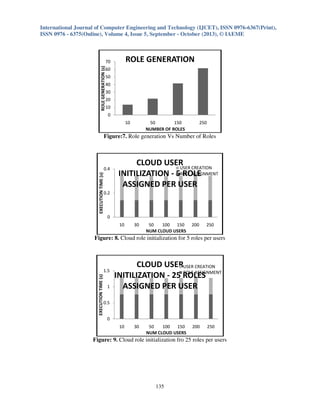
and role-permission assignments for cloud environment without compromising with the security. The
results obtained for various user sizes and respective role generation with role assignments in the
proposed model and framework architecture establishes itself as the best system forhighly efficient
user managements, role creation and role assignments system for cloud computing environment.
The other sections of the manuscript have been presented as follows: Section II presents the
related work of the considered technologies which is ascended by section III that states ܥܣܤܴܧܧܦ
model and its introduction for functionalities. Section IV presents expressiveness of ܥܣܤܴܧܧܦ
model and its modeling. This section also presents the operations on periodicity expressions
algorithms, various developed algorithms and the system complexity along with its design
constraints. Section V presents the results obtained and its analysis which is ascended by Section VI
that discusses the conclusions of the developed system model.
II. RELATED WORKS
Considering the requirement of a highly robust and effective solution for access control and
role management in cloud computing environment a number of researches have been induced and
many of them have performed well also. In this way to research process the first scientist group
Bertino et al. introduced TRBAC framework that emphasizes on the dominant constraints of RBAC
system model [14]. The shortcomings of that system model were rooted with the use of temporal
constraints for performing role enabling that limited its performance for multiple service
requirements in cloud environments. At the next phase the predominant work was for ܥܣܤܴܶܩ
model [17] the extended form of ܴܶ ܥܣܤmodel with the difference of inclusion of few extensive set
of constraints.
ܶ ܥܣܤmodelwas introduced in [14] that mainly support the temporal authorization and key
deviation principles [14] but still lacks in addressing the roles and its effective assignments. A
number of other researchers have advocated for the implementation of certain significant supporting
constraints in anܴ ܥܣܤmodel and few dominant works have been done in [18], [13], [5], [17], [19],
[8]. Then while, those research efforts could not address the problem of time-based access
restrictions and effective user creation with role assignment of multiple sizes. This shortcoming was
illuminated in our work. In certain work [15] the researcher came out with a system architecture
based on a logic-oriented constraint specification language that might be employed for specifying the
constraints on individual roles, users and the role-assignments on the users. In [13] a temporal data
117](https://image.slidesharecdn.com/50120130405015-131024062024-phpapp02/85/50120130405015-3-320.jpg)
![International Journal of Computer Engineering and Technology (IJCET), ISSN 0976-6367(Print),
ISSN 0976 - 6375(Online), Volume 4, Issue 5, September - October (2013), © IAEME
authorization model ሺܶܯܣܦሻwas proposed that could represent the access control policies on the
basis of temporal behaviour of the data [13]. Considering these research gaps and requirements here
in this paper we have proposed a ܥܣܤܴܧܧܦmodel that emphasizes on the characteristic of
permission by implementing the dynamic assignments of role-permission with the help of constraints
of periodicity, session constraint and Event dependencies.
In this research work we have tried to implement the unique and highly robust system model
that considers all of the key aspects like minimality, session constraints, expressiveness, user
management and allied role permission facility with optimum performance level and the usability of
access control and management.
III. DEERBCA MODELING AND TEMPORAL ROLE HIERARCHY
3.1 IntroducingDEERBCA Model
In the highly robust and complicated systems of cloud computing the proposed dynamic
expiration enabled role based access control model, ܥܣܤܴܧܧܦplays a significant role in cloud
computing environment and its resource management. The mechanism of ܥܣܤܴܧܧܦalso
accommodates the individual concepts of role provisioning, its activation and even the provision of
environment constraints as well as the event expressions allied with it.
In the proposed ܥܣܤܴܧܧܦapproach the system architecture characterizes a number of set of
constraints. These are as follows:
1. Temporal role enable/disable constraints
Temporal role enabling/disabling constraints are those constraints that permit the characteristics
of intervals and that time durations in which the role of users are enabled. In case of defined
duration constraints the constraint enabling event ignites or initiates the enabling or disabling of a
particular role. This initiation takes place either by enabling functions or by a specific administrator
initiated runtime process.
2. Provision of temporal restraints on individual user’s role and the assignment of its rolepermission
Such kind of restraints permits the characteristics of function intervals and the time duration
in which the role for a specific user or its permission is allotted or issued.
3. Activation constraints
Activation constraints are those constraints that permit the nature of employed restrictions
functional of the activation of a user’s role. These constraints encompasses, the characterization of
the complete time interval for which a defined user can initiate a role or the count
ofcontemporaneous activations of the role defined at a specific time.
4. Runtime proceedings
A combination of runtime events permits the supervisor to vigorouslycommence the
ܥܣܤܴܧܧܦprocedures, or facilitate the period or commencementrestraints.
Few others combination of runtime procedures permits the users to make certain request for
activating or deactivating the roles.
5. Constraint permissible expressions
The proposed ܥܣܤܴܧܧܦmechanism encompasses the events which enables or disables the
aforesaidtime duration and activation constraints for individual roles.
6. Event dependencies
The event dependencies in the proposed ܥܣܤܴܧܧܦsystem represent the expressions of the
inter-dependencies among all the encompassing events.In the development of DEERBAC system
model a number of system constraints have been used. The key constraints are periodicity
constraints, duration constraints, time based role activation constraints, Cardinality constraint on role
118](https://image.slidesharecdn.com/50120130405015-131024062024-phpapp02/85/50120130405015-4-320.jpg)
![International Journal of Computer Engineering and Technology (IJCET), ISSN 0976-6367(Print),
ISSN 0976 - 6375(Online), Volume 4, Issue 5, September - October (2013), © IAEME
activation, Event dependencies and constraints of run time request. In expression the periodicity
constraints for user role assignment is given by (݃ݏܣ :ܽݎܲ ,ܵ ,ܦ /݃ݏܣܦ ܴ ݁ ݐሻ while for role
enabling and role permissionሺ ,)ܴ ݃ݏܣܦ/:ܽݎܲ ,ܵ ,ܦሺ݃ݏܣ :ܽݎܲ ,ܲ ,ܫ௪ /݃ݏܣܦ௪ ܴ ݐሻ expressions are
employed respectively.
For
duration
constraint
the
expressions
ሺሾሺܵ ,ܦሻ|ܯሿ, ܯோ ܴܲ ܾܦ/݊ܧ :ݎሻ
and ሺሾሺܵ ,ܦሻ|ܯሿ, ܯ ܲ݃ݏܣܦ :ݎ /݃ݏܣܦ ܴ ݁ ݐሻare used for user-role assignment (ܩோ ) and rolepermission assignmentܩோ௪ respectively. The sporadic expression implemented in the expressions of
the considered constraints is represented in the form of ሺܵ ,ܦሻ [20], in which the variable or entity
ܵrefers the expression representing an infinite combination of periodictime moments, and the
variable entity D refers ܦൌ ሾܾ݁݃݅݊, ݁݊݀ሿ is a time duration representing the lower and upper bounds
which are inflicted on instants inentityܵ. On the other hand the expression ݈ܵሺܵ ,ܦሻis employed for
stating all the encompassed time durations in composite function ሺܵ ,ܦሻ.
In this paper, we have also implemented a function ܲ ݈ܵሺܵ ,ܦሻthat represents the collection
of the end points present in the intervals in ሺܵ ,ܦሻthat states that in case the entity or function ሺܵ ,ܦሻ
is represented in the form of a set of durations ሼሺݐ௨ଵ , ݐ௧ଵ ሻ, ሺݐ௨ଶ , ݐ௧ଶ ሻ, … , ݐ௨ , ݐ௧ ሽthen; the function can
be given as follows:
ܲ ݈ݏሺܵ ,ܦሻ ൌ ሼሺݐ௨ଵ , ݐ௧ଵ ሻ, ሺݐ௨ଶ , ݐ௧ଶ ሻ, … , ݐ௨ , ݐ௧ ሽ
In these mathematical modeling or expressions the variable ܦdenotes the time interval for a
defined constraint.
3.2 Temporal Role Hierarchies
The overview of the temporal hierarchies of the proposed ܥܣܤܴܧܧܦsystem model has been
discussed in this section.Table-1 illustrates the predicate notations employed for representing the
semantics of the considered hierarchies. The considered entities like predicate enabled, assigned have
been given be presentation ݊ܧሺܴ, ݐሻ, ݃ݏܣሺ݁, ܴ, ݐሻ and ݃ݏܣሺݐ ,ܴ ,ݓሻ. These all notations denote the
status of the roles, roles of user and assignment of role permission at time t, respectively.
The activation of ሺ݁, ܴ, ݐሻby means of predicate signifies that the specific user ݁might
activate specific role ܴ at certain time period .ݐAnd further it states that the specific user u is
unconditionally or unequivocally allotted to that specific roleܴ. The other entity ݐܿܣሺ݁, ݐ ,ܴ ,ݑሻstates
the role ܴ is in active state in the specific user’s session or duration ܵ at time instant t, while another
entity ݍܿܣሺ݁, ݐ ,ݑ ,ݓሻ illustrates towards the acquisition of permission by ݁ at the session.ݑThe
predominant relationships among the predicates are in general considered and emphasized by the
axioms as mentioned in Table 1. Even these axioms do identify the acquisition of permission and the
role activation in the proposed ܥܣܤܴܧܧܦsystem model.
Predicate
݊ܧሺܴ, ݐሻ
ሺ݁_ ݃ݏܣሺ݁, ܴ, ݐሻሻ
ሺ ݃ݏܣ_ݓሺݐ ,ܴ ,ݓሻሻ
ܿܽ݊_ݐܿܣሺ݁, ܴ, ݐሻ
ܿܽ݊_ ݍܿܣሺ݁, ݐ ,ݓሻ
ܿܽ݊_ܾ݁_ ݍܿܣሺݐ ,ܴ ,ݓሻ
TABLE 1: Status Predicates
Meaning
Role ܴ is enable at time ݐ
User ݁ is assigned to role ܴ at time ݐ
Permission ݓis assigned to role ܴ at time ݐ
User ݁ can active role ݎat time ݐ
User ݁ can acquire permission ݓat time ݐ
Permission ݓcan be acquire through role ܴ at time ݐ
ݐܿܣሺ݁, ܴ, ݐ ,ݑሻ
Role ܴ is active in user ݁’ ݑsession ݑat time ݐ
ݍܿܣሺ݁, ݐ ,ݑ ,ݓሻ
User ݁’ acquires permission ݓin session ݑat ݐ
119](https://image.slidesharecdn.com/50120130405015-131024062024-phpapp02/85/50120130405015-5-320.jpg)
![International Journal of Computer Engineering and Technology (IJCET), ISSN 0976-6367(Print),
ISSN 0976 - 6375(Online), Volume 4, Issue 5, September - October (2013), © IAEME
The axiom 1"݃ݏܣሺݐ ,ܴ ,ݓሻ ՜ ܿܽ݊_ܾ݁_ݍܿܣሺݐ ,ܴ ,ݓሻ"indicates that in case any person is
allotted to perform a specific role, then the same can be accomplished with the help of that specific
role.Similarly, the second axiom 2 “ ݃ݏܣሺ݁, ܴ, ݐሻ ՜ ܿܽ݊_ݐܿܣሺ݁, ܴ, ݐሻ" denotes that all of the
consisting users are facilitated a specific role so that they may activate that specific roles and
function. Axiom 3ܿܽ݊_ݐܿܣሺ݁, ܴ, ݐሻ ݍܿܣ_ܾ݁_݊ܽܿ רሺݐ ,ܴ ,ݓሻ ՜ ܿܽ݊_ ݍܿܣሺ݁, ݐ ,ݓሻ”, it is stated that
in case a particular user u is provided a role ܴ then all the encompassing functionalities or roles r
could be accomplished with the help of that user .ݑ
Inthe same way, the ascending axiom 4 ݐܿܣሺ݁, ܴ, ݐ ,ݓሻ ݍܿܣ_ܾ݁_݊ܽܿ רሺݐ ,ܴ ,ݓሻ ՜
ݍܿܣሺ݁, ݐ ,ݑ ,ݓሻsay that in case a user session or duration in which one has to activate a specific
roleR, in that circumstances the user ݁ accomplishes then all the permissions that could be collected
through the role ܴ. It must be noted that the axioms presented in 1 and 2 illustrates towards the
permission-acquisition and role-activation semantics which are in general governed by overt userrole and the person or privilege of the role assignment.
In general, a particular hierarchy of role ܴ lengthens the extent of the permission-acquisition
and the semantics of the role-activation further than the preciseallocations by means of hierarchical
relations which are predefined among permitted or considered roles. In our proposed ܥܣܤܴܧܧܦ
model or framework the predominant three hierarchies are considered. These are: permissioninheritance-only
hierarchy
which
is
also
known
as ܫെ ݄݅݁,ݕ݄ܿݎܽݎ
݈݁ݎെ ݐܿܣെ ݕ݄ܿݎܽݎ݄݁݅ ݕ݈݊or ܣെ ݄݅݁ ,ݕ݄ܿݎܽݎand the third and the last hierarchy are referred to
as ܿ ݁ܿ݊ܽݐ݅ݎ݄݁݊݅ ܾ݀݁݊݅݉െ ݕ݄ܿݎܽݎ݄݁݅ ݐܿܣor ܣܫെ ݄݅݁ .]71[ ,]61[ ݕ݄ܿݎܽݎThese all framework
hierarchy might be of any kind, either of restricted or unrestricted kinds.
Among these hierarchies the restricted one might be further classified into two types, weakly
and strongly restricted. The hierarchy of unrestricted type ܫെ ݄݅݁ ܽݕ݄ܿݎܽݎ௧ ߚthat states that in
case there exists a ୲ β, then the role permission or even acquisition permission could be
accomplished with the help of role ݔwhich encompasses all the approvals or acknowledgements that
could be gained with the help of specific role .ݕIn other way, the permissions of the ascenders roles
are in general inherited or ascended by the roles with higher priority. Meanwhile, the condition
which is in relation to the unrestricted A-hierarchy states that in case a user ݁ activates a specific role
ݔwith the condition ݔ௧ ߚ, then that user ݁might also initiate the role ߚwhether being not assigned
toߚ. Furthermore, the user ݁might not get theߚ’ ݏpermissions only by initiatingܽ. On the other hand,
the permission-inheritance nature is not permitted in an unrestricted A-hierarchy framework. It can
be found that the ܣܫെ ݄݅݁ݕ݄ܿݎܽݎis the specific and of course alone framework that encompasses
both kind of inheritance, like permission inheritance as well as role-activation kind of semantics. The
weakly restricted hierarchy permits the inheritance or the activation semantics in the non-overlapping
activation sessionof the systematically allied roles, on the other hand the hierarchies restricted
strongly permits the inheritance and the activation semantics only in the overlapping causing
sessions.
As per the considered condition for ܫെ ݄݅݁ݕ݄ܿݎܽݎሺ ܽ݀݁ݐܿ݅ݎݐݏ݁ݎ ݕ݈݇ܽ݁ݓ௧ ߚሻ is presented,
then only the role is required to be activated at time ݐso as to implement the inheritance semantics.
The roles or defined role ݕmight or even might not be activated at that specific time then while, in
case of ܫെ ݄݅݁ ݕ݄ܿݎܽݎwhich is a kind of strongly restricted hierarchy framework, if ܽ ௨ ௧ ߚ is
stated then the entities, ܽ and ߚis required to be activated at the specific time ݐso as to employ the
inheritance semantics. The hierarchies like restricted Aand IA are defined in the same way.
IV. EXPRESSIVENESS OF ࡰࡱࡱࡾ MODEL AND ITS MODELING
The overall system has been introduced in the previous section and has been discuss that the
proposed ܥܣܤܴܧܧܦmodelpermits the characterization of a huge set time-related constraints.
Observing these factors a significant question arises that whether this kind of exhaustive set of
120](https://image.slidesharecdn.com/50120130405015-131024062024-phpapp02/85/50120130405015-6-320.jpg)











![International Journal of Computer Engineering and Technology (IJCET), ISSN 0976-6367(Print),
ISSN 0976 - 6375(Online), Volume 4, Issue 5, September - October (2013), © IAEME
REFERENCES
[1]
[2]
[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
D.F. Ferraiolo, D.M. Gilbert, and N. Lynch, “An Examination of Federal and Commercial Access
Control Policy Needs,” Proc. NISTNCSC Nat’l Computer Security Conf., pp. 107-116, Sept. 1993.
J.B.D. Joshi, A. Ghafoor, W. Aref, and E.H. Spafford, “Digital Government Security Infrastructure
Design Challenges,” Computer, vol. 34, no. 2, pp. 66-72, Feb. 2001.
M. Nyanchama and S. Osborn, “The Role Graph Model and Conflict of Interest,” ACM Trans.
Information and System Security, vol. 2, no. 1, pp. 3-33, 1999.
R. Sandhu, E.J. Coyne, H.L. Feinstein, and C.E. Youman, “RoleBased Access Control Models,”
Computer, vol. 29, no. 2, pp. 38-47, Feb. 1996.
J.B.D. Joshi, W.G. Aref, A. Ghafoor, and E.H. Spafford, “Security Models for Web-Based
Applications,” Comm. ACM, vol. 44, no. 2, pp. 38-72, Feb. 2001.
S. Osborn, R. Sandhu, and Q. Munawer, “Configuring Role-Based Access Control to Enforce
Mandatory and Discretionary Access Control Policies,” ACM Trans. Information and System
Security, vol. 3, no. 2, pp. 85-106, May 2000.
R. Sandhu, “Separation of Duties in Computerized Information Systems,” Database Security IV:
Status and Prospects, pp. 179-189, 1991.
R. Simon and M.E. Zurko, “Separation of Duty in Role-Based Environments,” Proc. 10th IEEE
Computer Security Foundations Workshop, June 1997.
E. Ferrari and B. Thuraisingham, “Security and Privacy for Web Databases and Services,” Proc. Int’l
Conf. Extending Database Technology, pp. 17-28, 2004.
J.S. Park, R. Sandhu, and G.J. Ahn, “Role-Based Access Control on the Web,” ACM Trans.
Information and System Security (TISSEC), vol. 4, no. 1, pp. 37-71, Feb. 2001.
B.M. Thuraisingham, C. Clifton, A. Gupta, E. Bertino, and E. Ferrari, “Directions for Web and ECommerce Applications Security,” Proc. Int’l Workshops Enabling Technologies: Infrastructures for
Collaborative Enterprises, pp. 200-204, 2001.
J. Joshi, E. Bertino, U. Latif, and A. Ghafoor, “Generalized Temporal Role Based Access Control
Model,” IEEE Trans. Knowledge and Data Eng., vol. 17, no. 1, pp. 4-23, Jan. 2005.
V. Atluri and A. Gal, “An Authorizaion Model for Temporal and Derived Data: Securing Information
Portals,” ACM Trans. Information and System Security, vol. 5, no. 1, pp. 62-94, Feb. 2002.
E. Bertino, P.A. Bonatti, and E. Ferrari, “TRBAC: A Temporal Role-Based Access Control Model,”
ACM Trans. Information and System Security, vol. 4, no. 4, 2001.
E. Bertino, E. Ferrari, and V. Atluri, “The Specification and Enforcement of Authorization
Constraints in Workflow Management Systems,” ACM Trans. Information and System Security, vol.
2, no. 1, pp. 65-104, 1999.
J.B.D. Joshi, E. Bertino, and A. Ghafoor, “Temporal Hierarchy and Inheritance Semantics for
GTRBAC,” Proc. Seventh ACM Symp. Access Control Models and Technologies, June 2002.
J. Joshi, E. Bertino, U. Latif, and A. Ghafoor, “Generalized Temporal Role Based Access Control
Model,” IEEE Trans. Knowledge and Data Eng., vol. 17, no. 1, pp. 4-23, Jan. 2005.
G. Ahn and R. Sandhu, “Role-Based Authorization Constraints Specification,” ACM Trans.
Information and System Security, vol. 3, no. 4, Nov. 2000.
A. Kumar, N. Karnik, and G. Chafle, “Context Sensitivity in RoleBased Access Control,” ACM
SIGOPS Operating Systems Rev., vol. 36, no. 3, pp. 53-66, July 2002.
M. Niezette and J. Stevenne, “An Efficient Symbolic Representation of Periodic Time,” Proc. First
Int’l Conf. Information and Knowledge Management, 1992.
GK Srinivasa Gowda, CV Srikrishna and Kashyap Dhruve, “Measurement of End to End Delays in
Ad Hoc 802.11 Networks”, International Journal of Computer Engineering & Technology (IJCET),
Volume 4, Issue 4, 2013, pp. 100 - 115, ISSN Print: 0976 – 6367, ISSN Online: 0976 – 6375.
Ruksar Fatima, Dr.Mohammed Zafar Ali Khan, Dr. A. Govardhan and Kashyap Dhruve, “Detecting
In-Situ Melanoma using Multi Parameter Extraction and Neural Classification Mechanisms”,
International Journal of Computer Engineering & Technology (IJCET), Volume 4, Issue 1, 2013,
pp. 16 - 33, ISSN Print: 0976 – 6367, ISSN Online: 0976 – 6375.
137](https://image.slidesharecdn.com/50120130405015-131024062024-phpapp02/85/50120130405015-23-320.jpg)