This document provides an overview of networking and the internet. It discusses network layering and protocols. The key points are:
- It introduces networking concepts like layered network architecture, protocols, and internet transport protocols TCP and UDP.
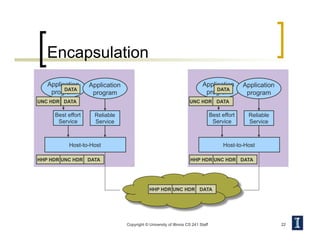
- Layering abstracts the network into logical layers like physical, data link, network, transport, and application. Each layer provides services to the layer above.
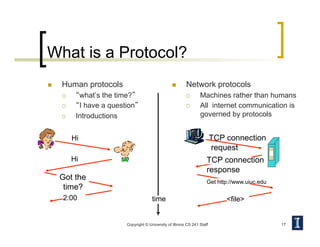
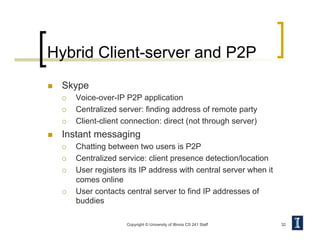
- Protocols define rules for communication between entities at each layer. Examples are network protocols like IP and transport protocols like TCP and UDP.
- TCP provides reliable, connection-oriented communication while UDP is simpler but unreliable datagram transmission. Applications choose the appropriate protocol based on their needs.