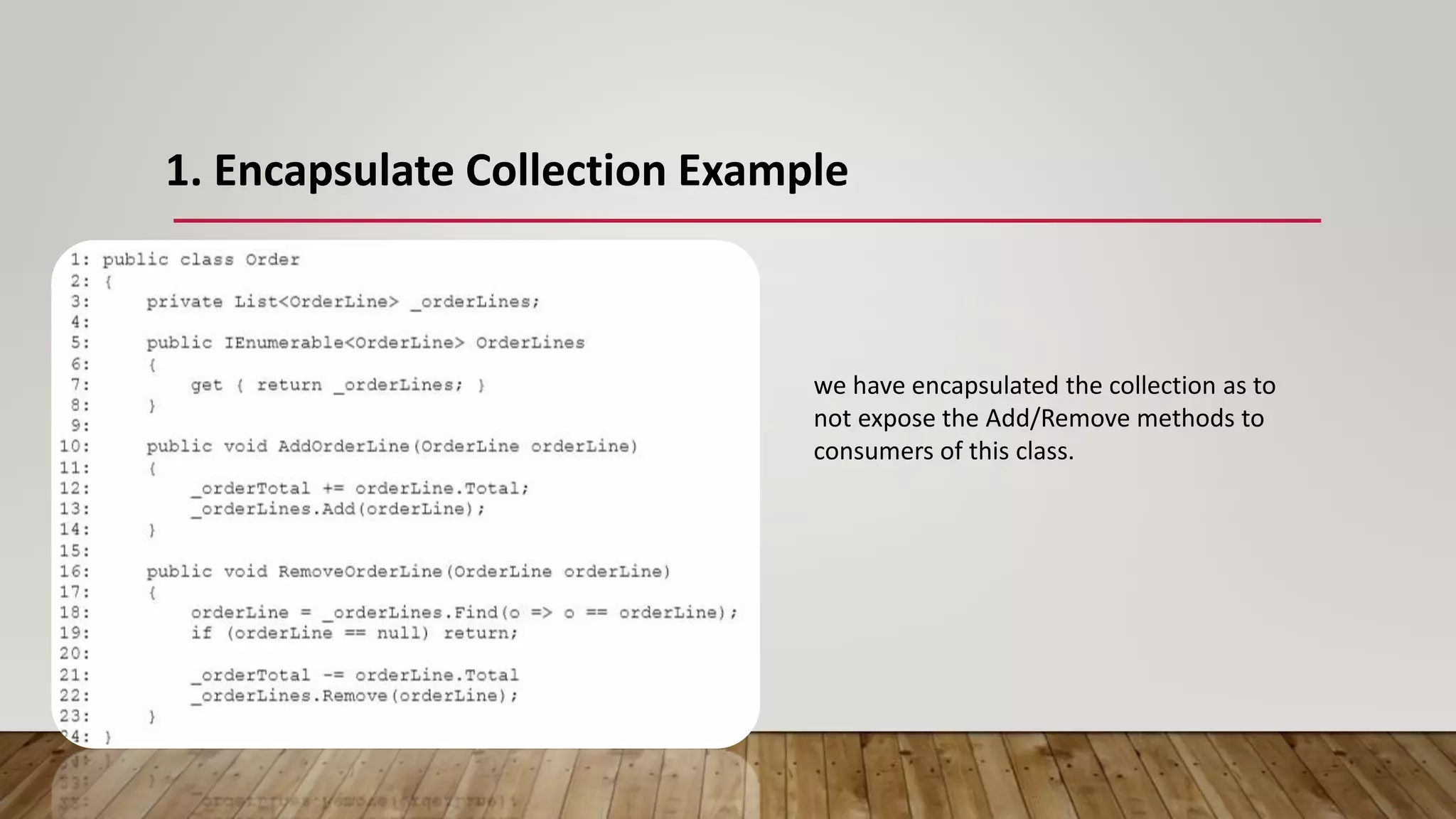
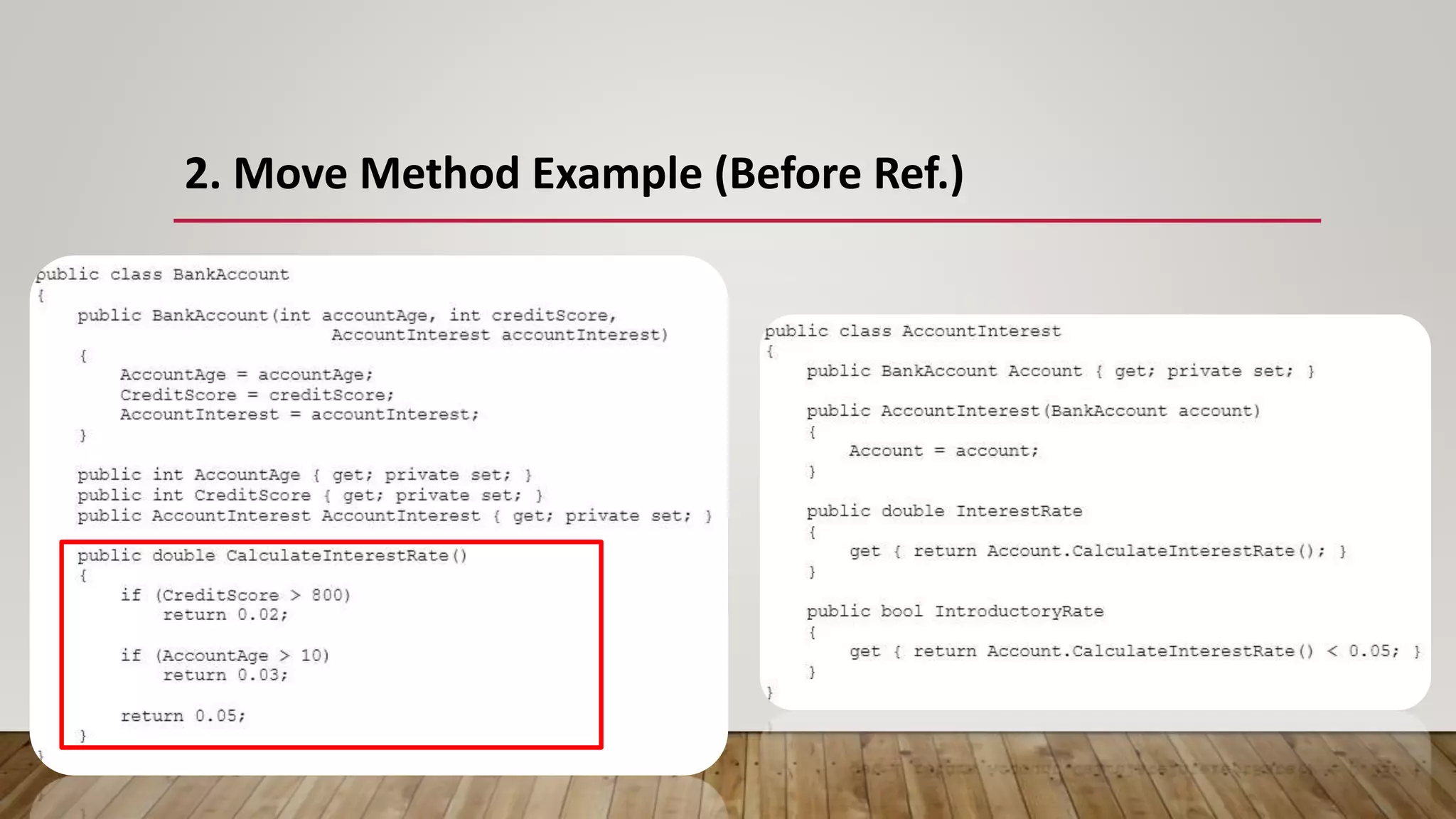
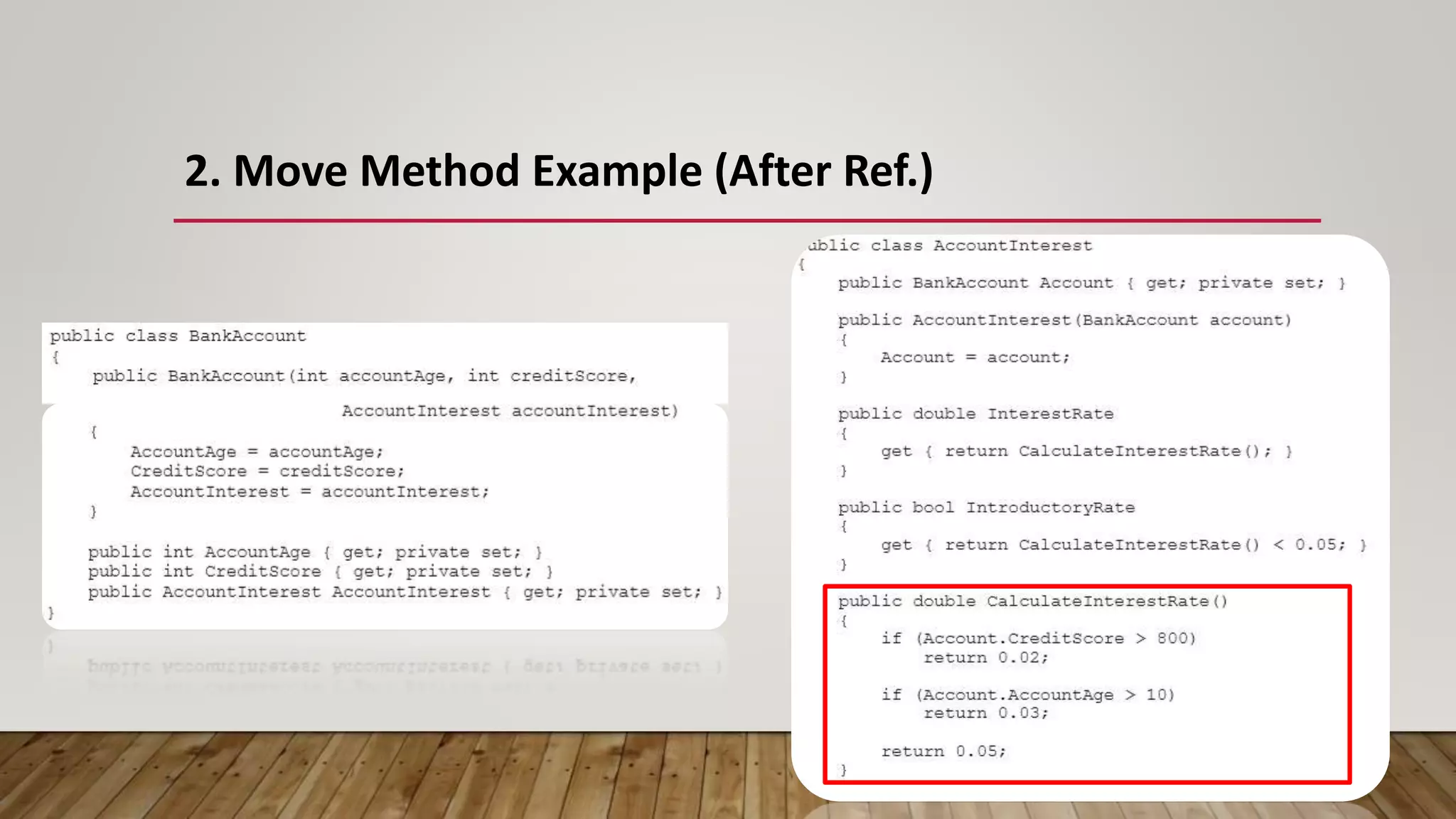
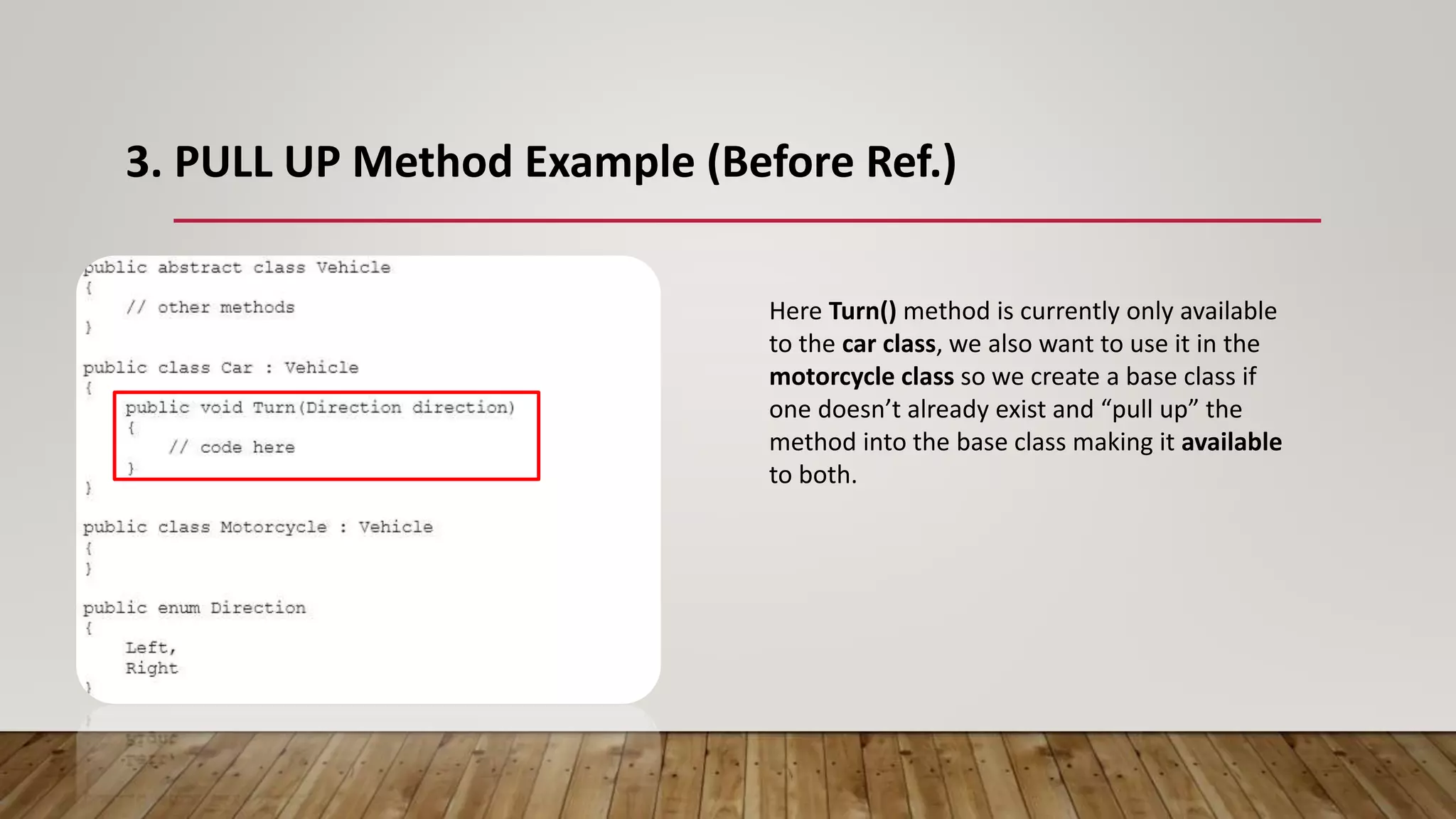
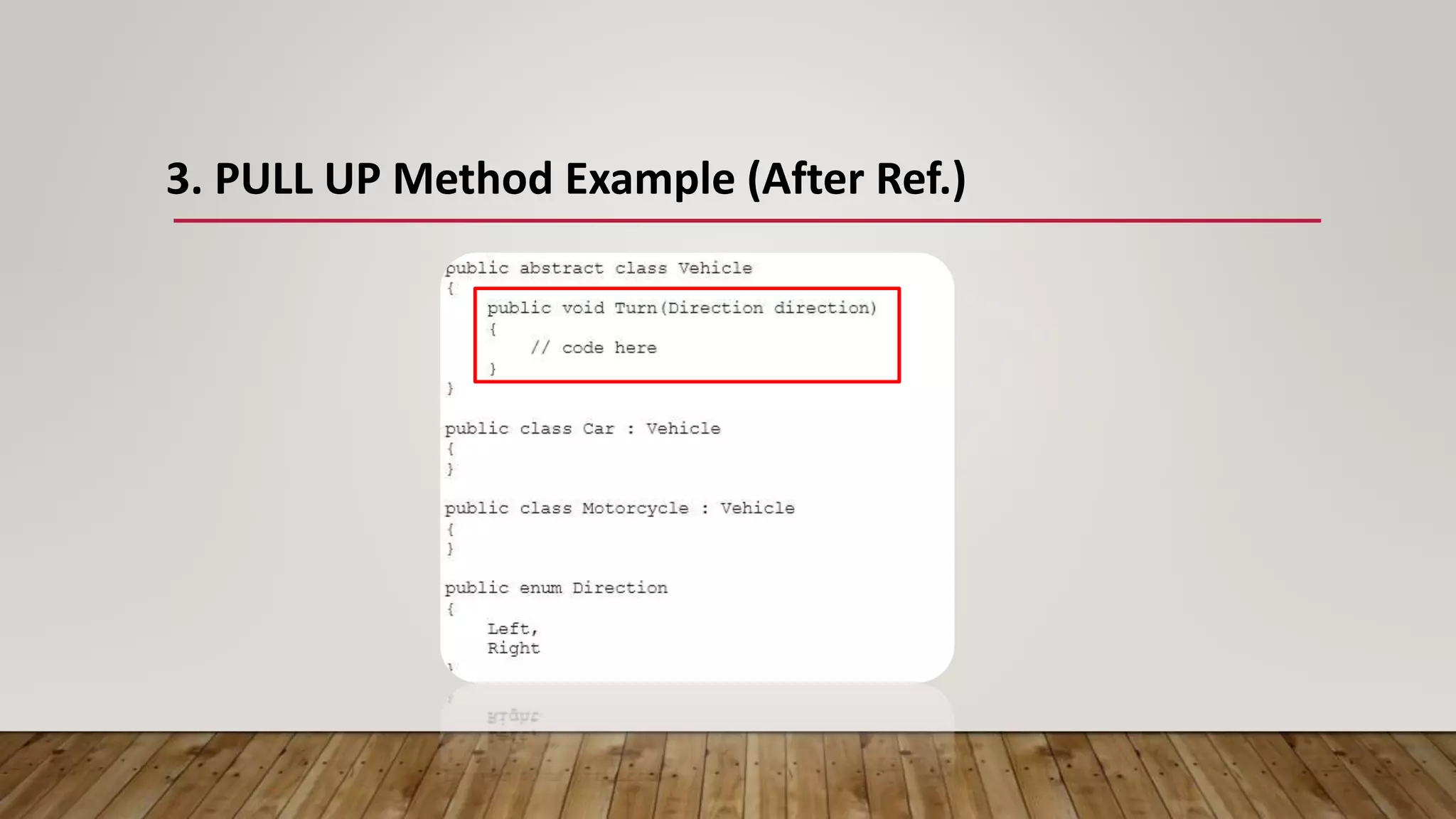
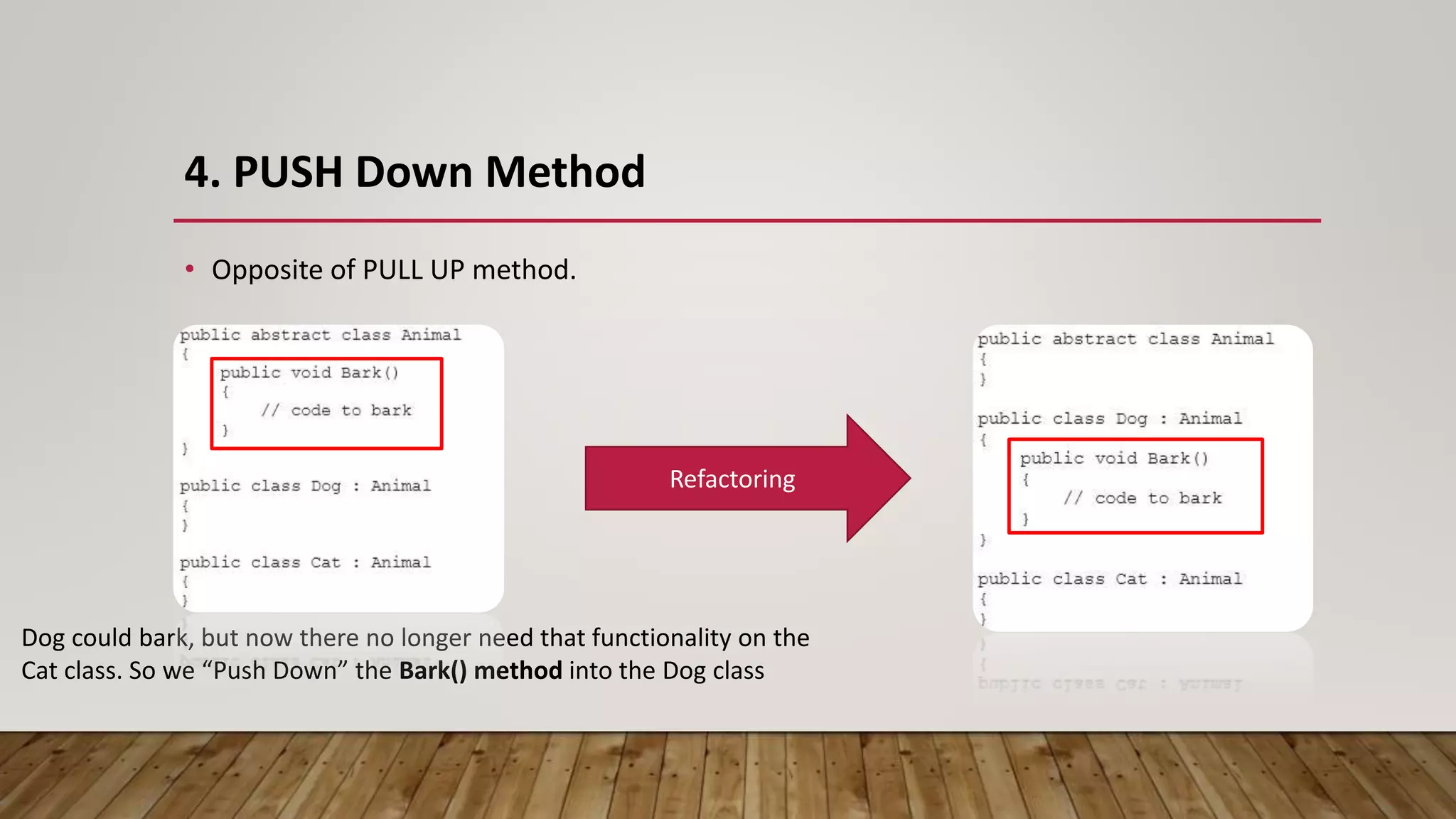
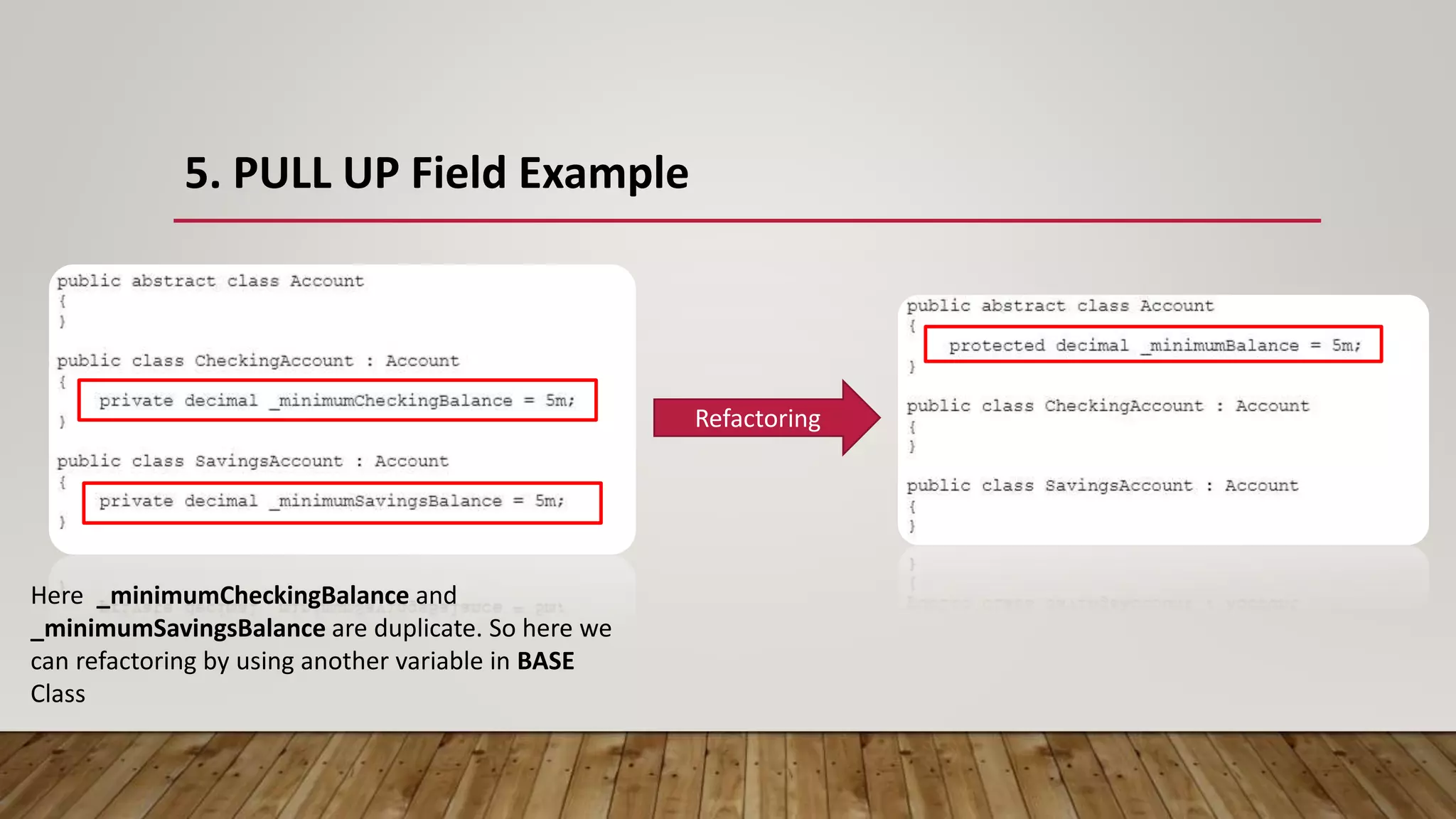
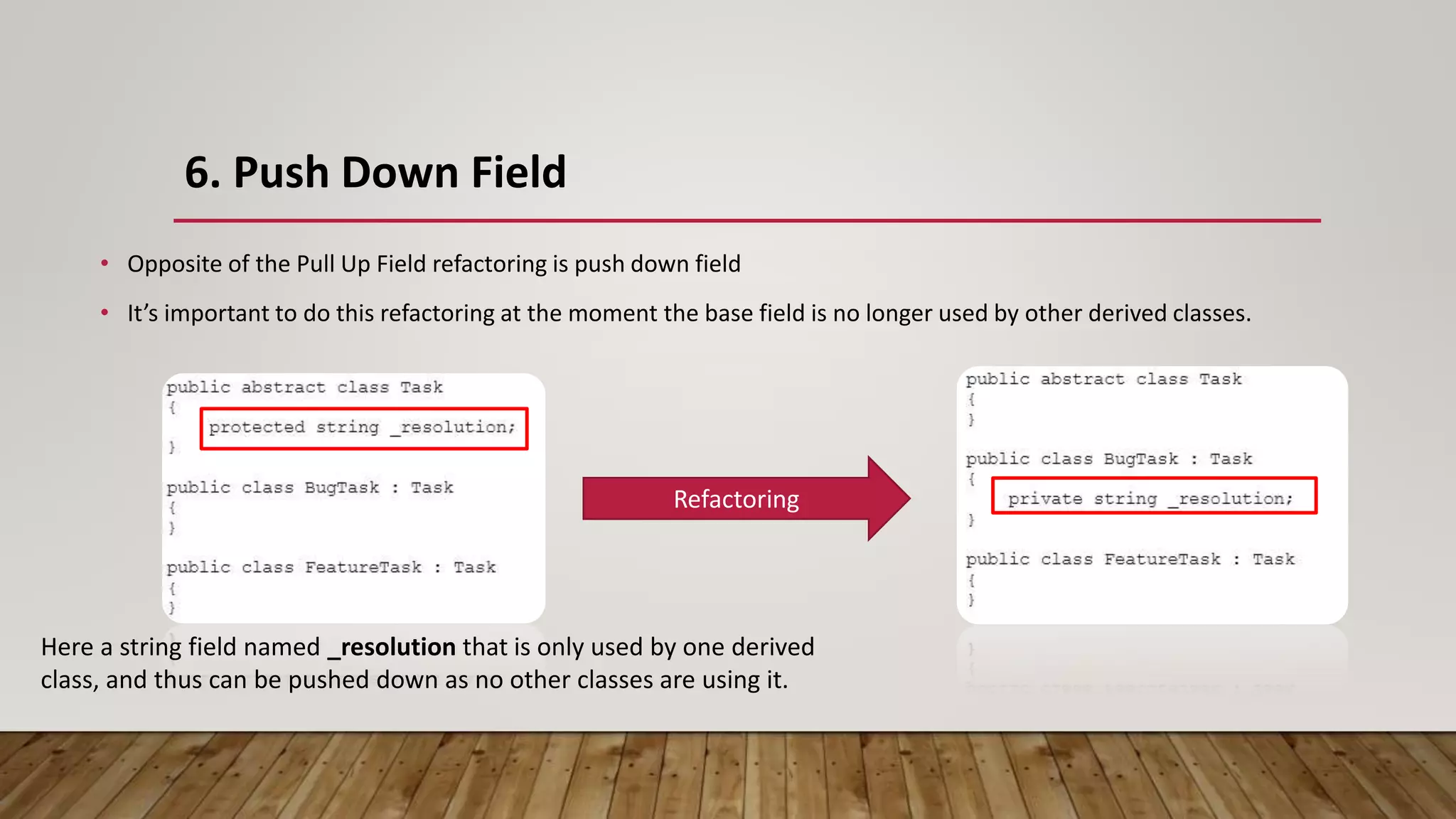
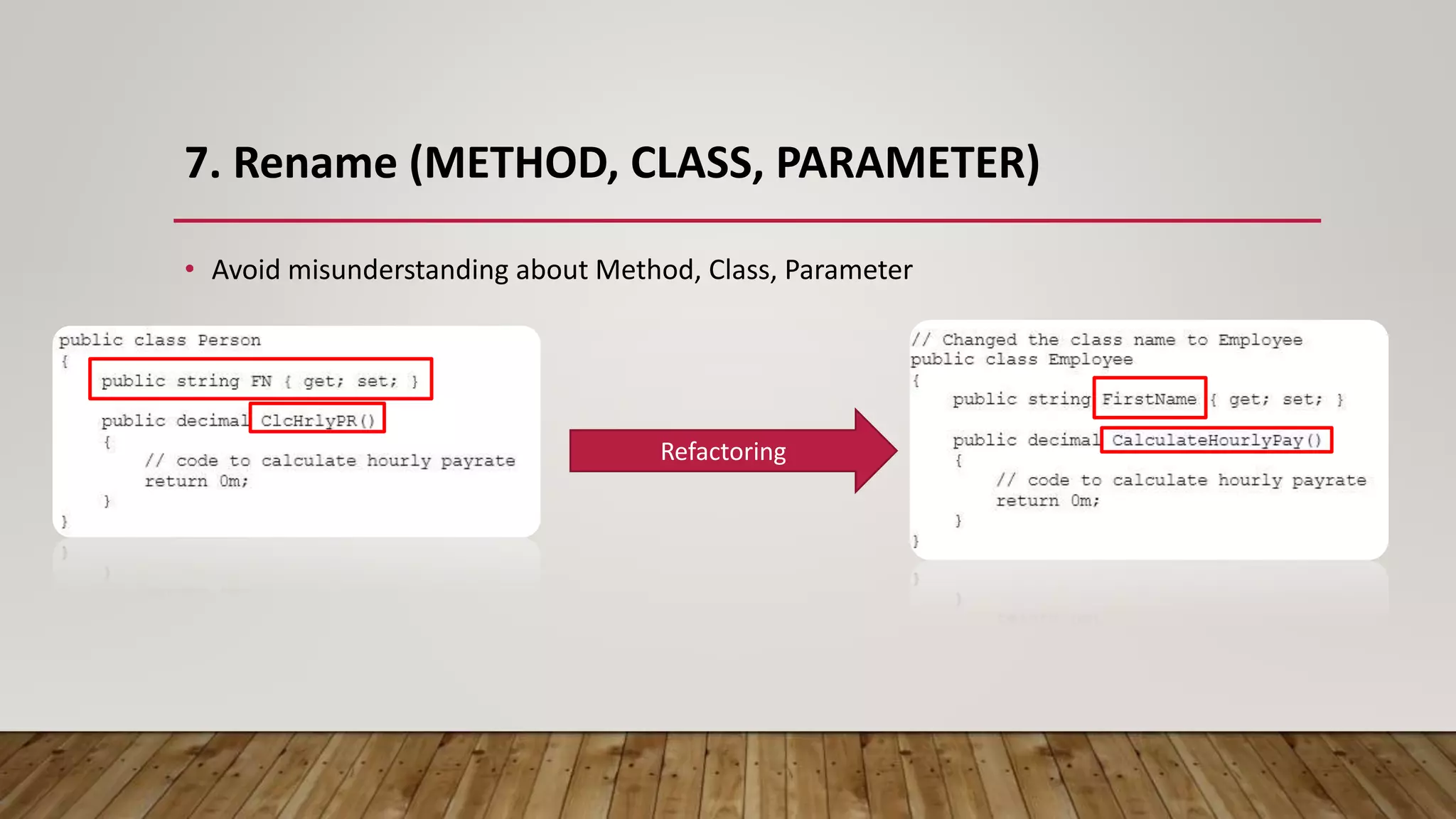
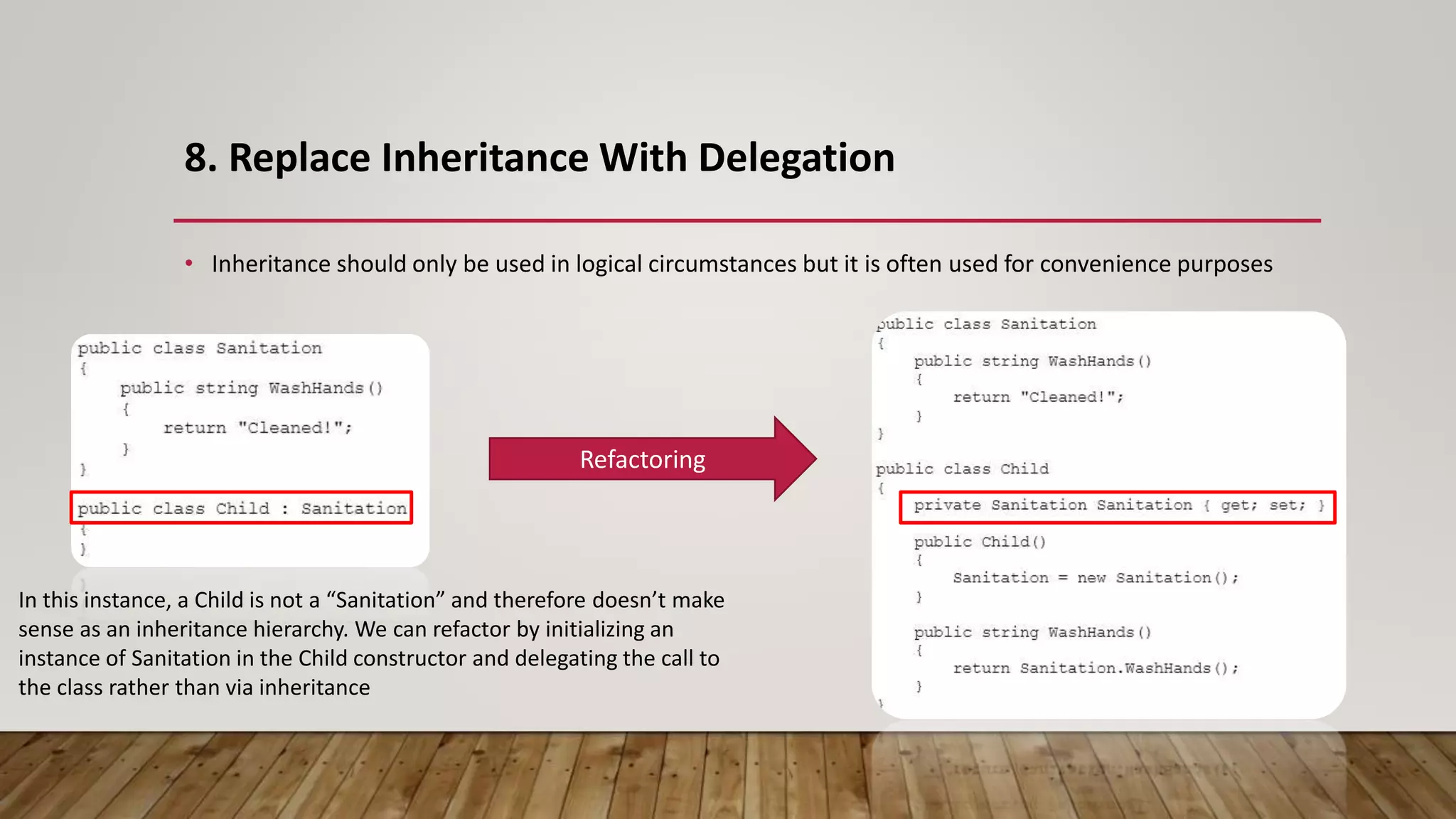
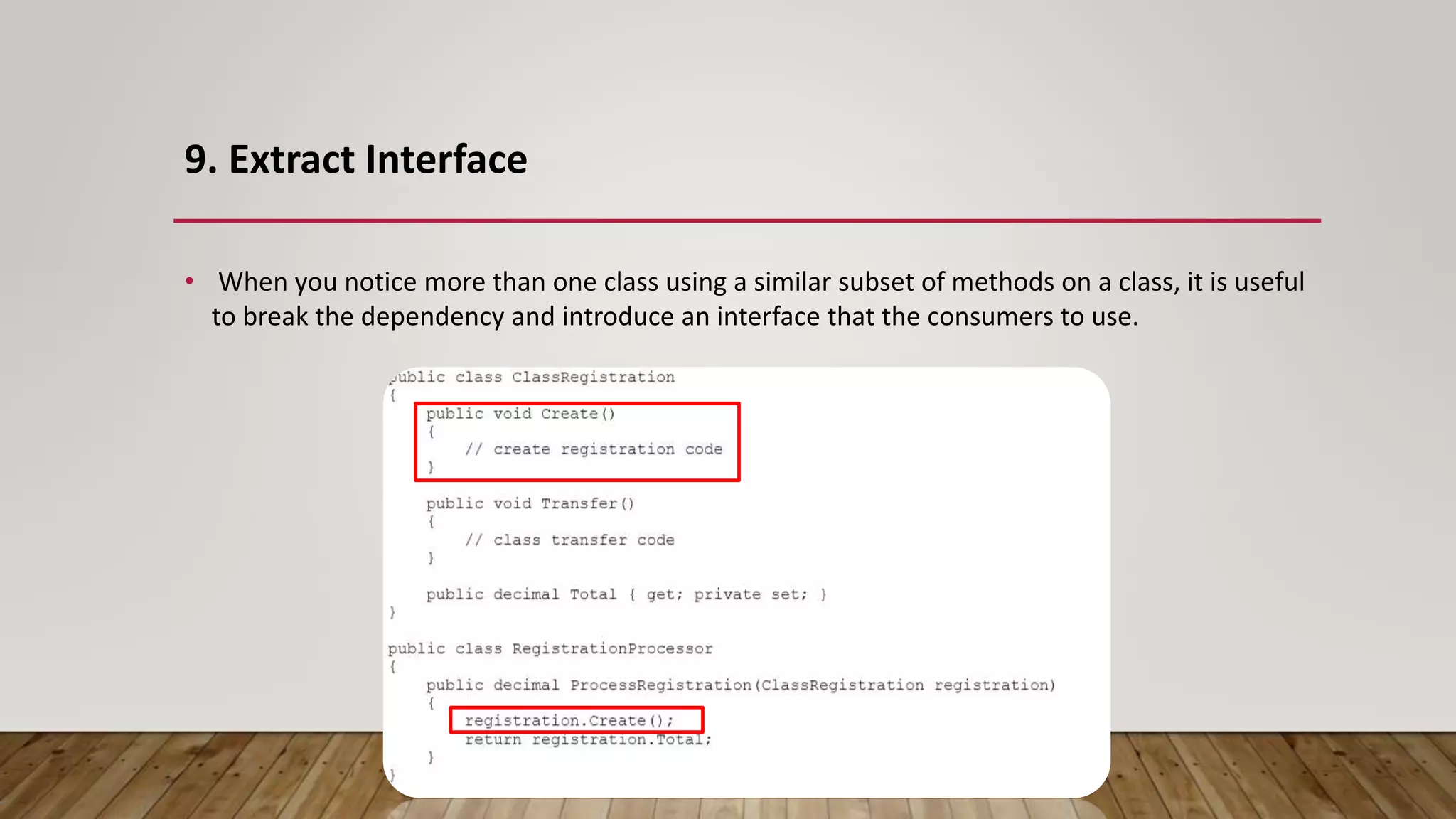
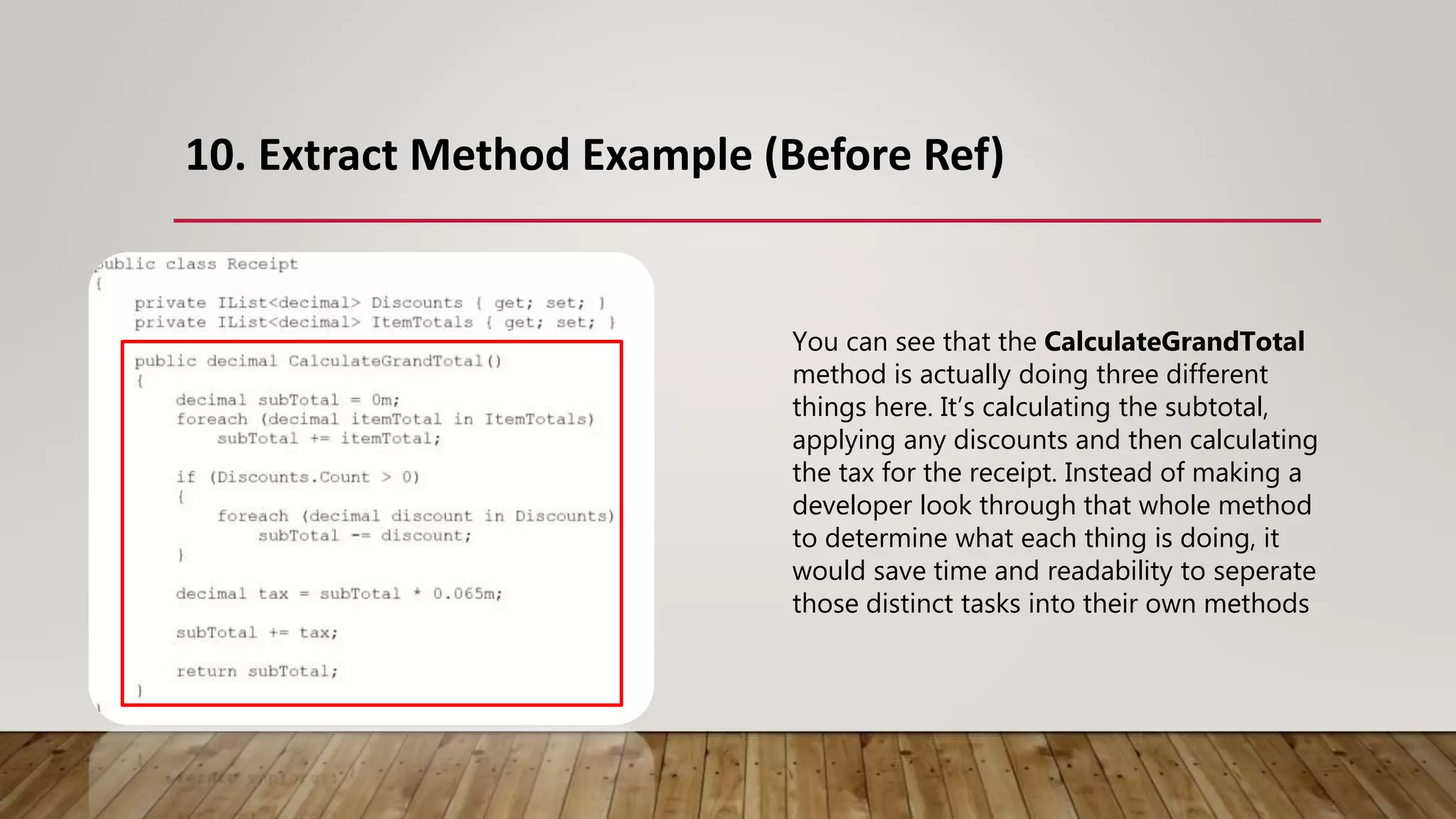
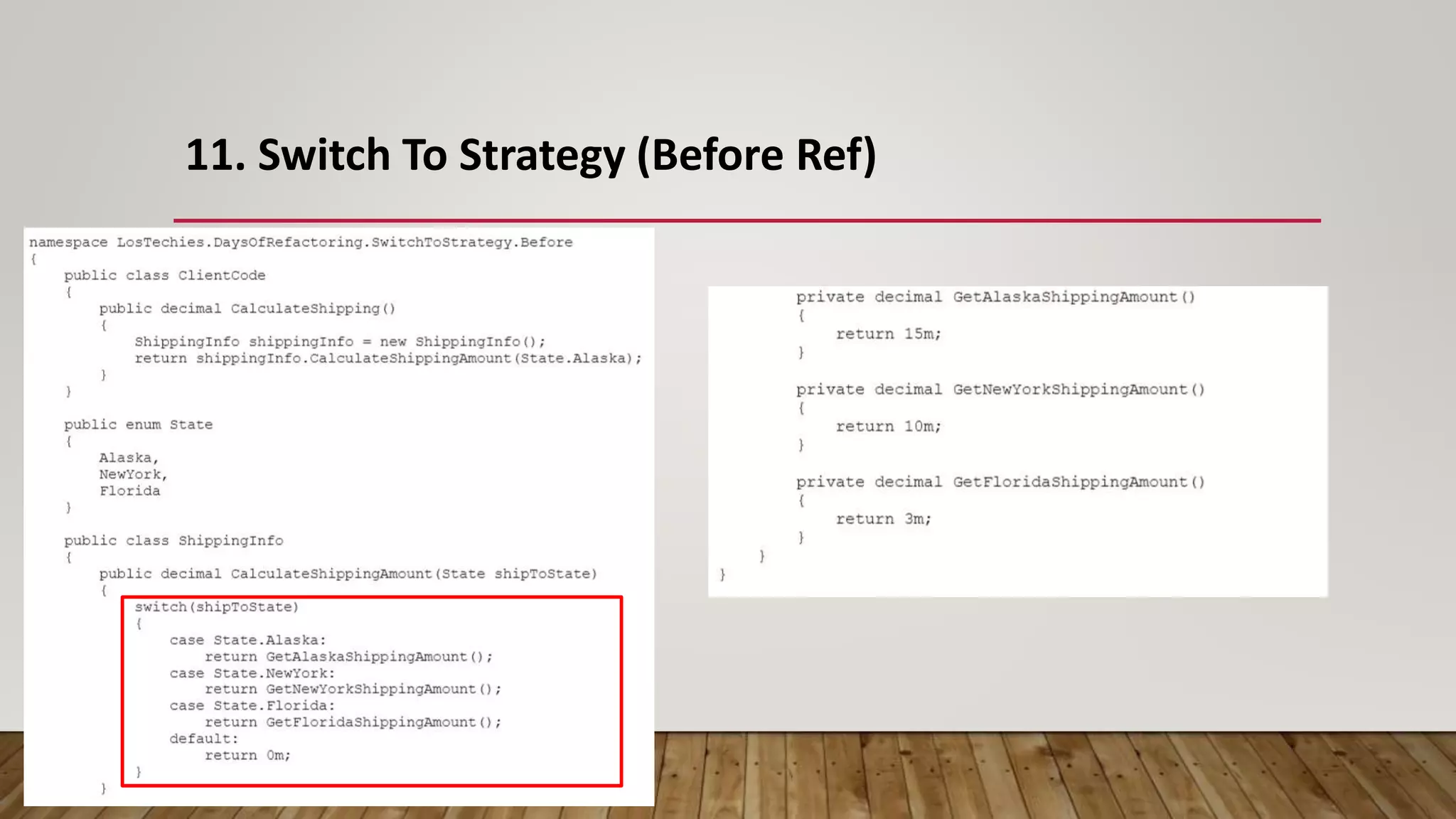
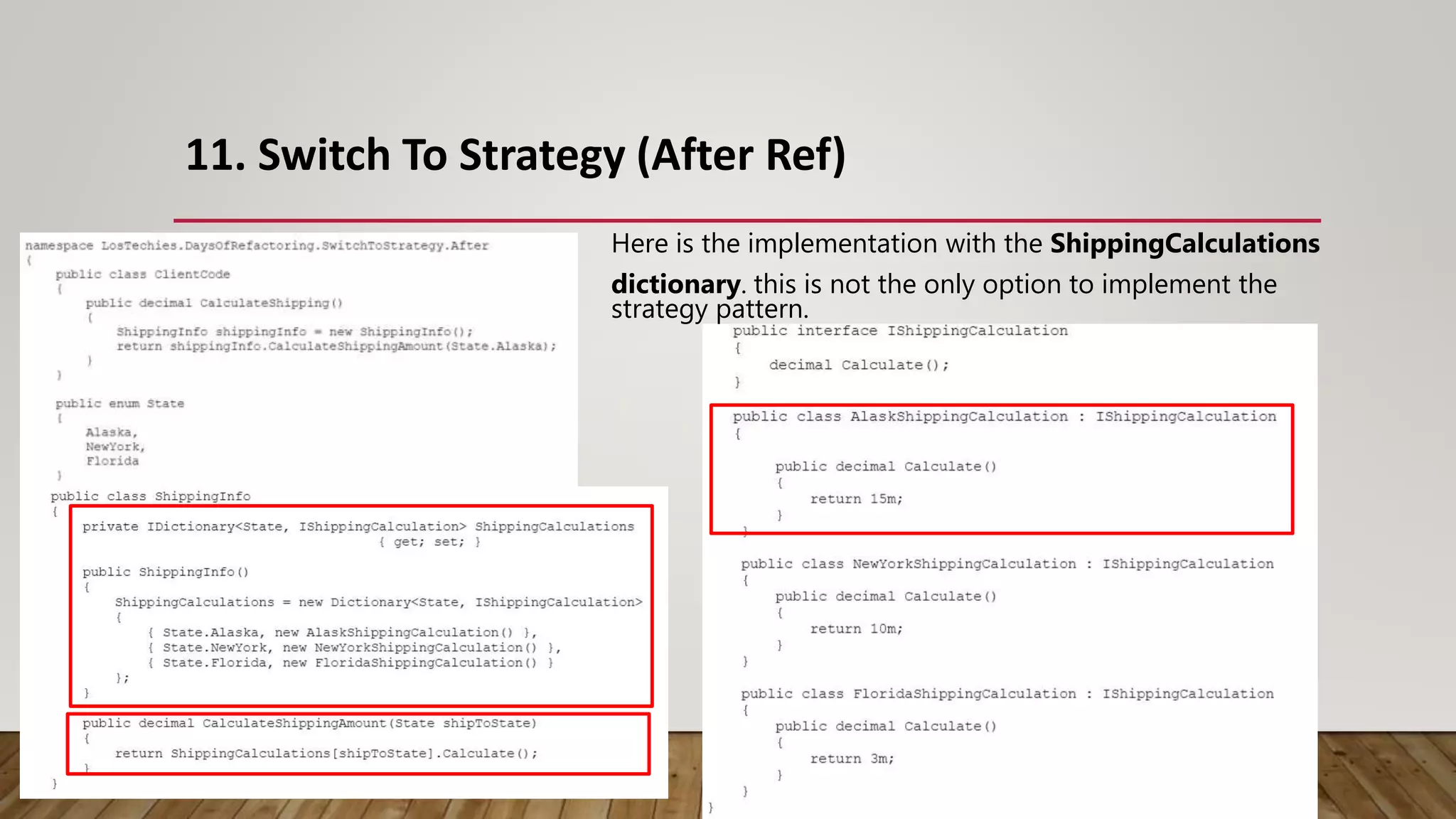
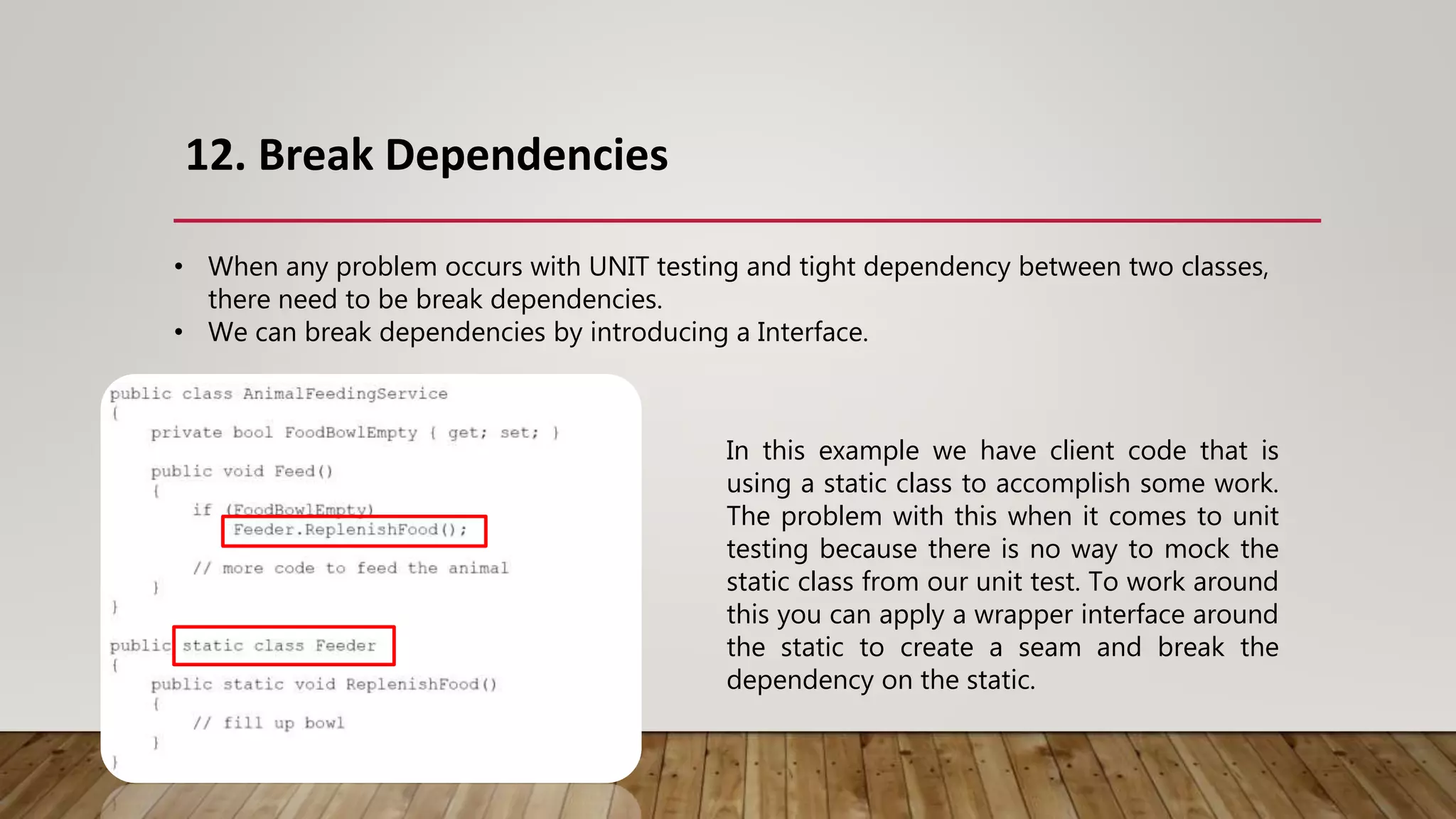
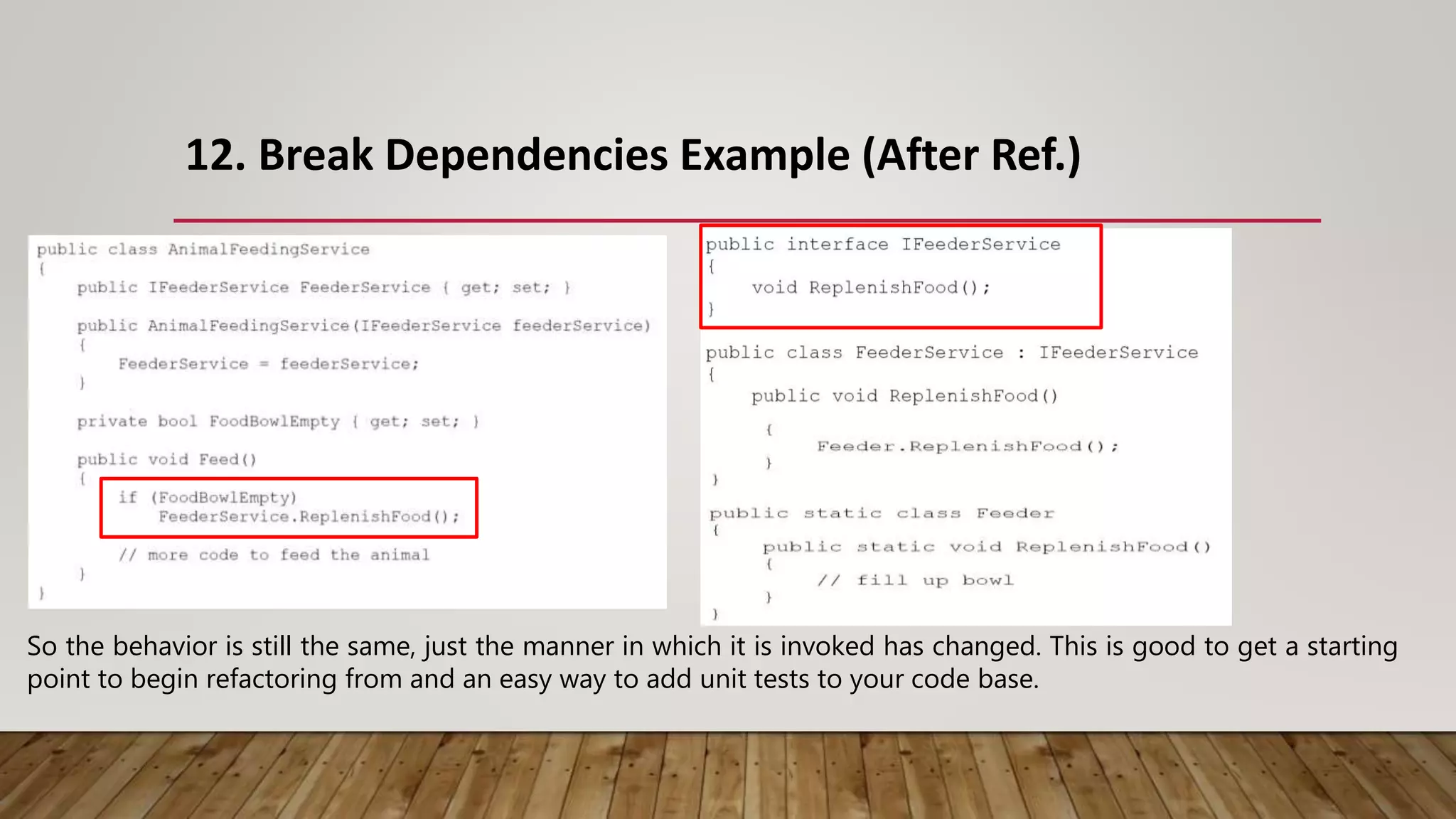
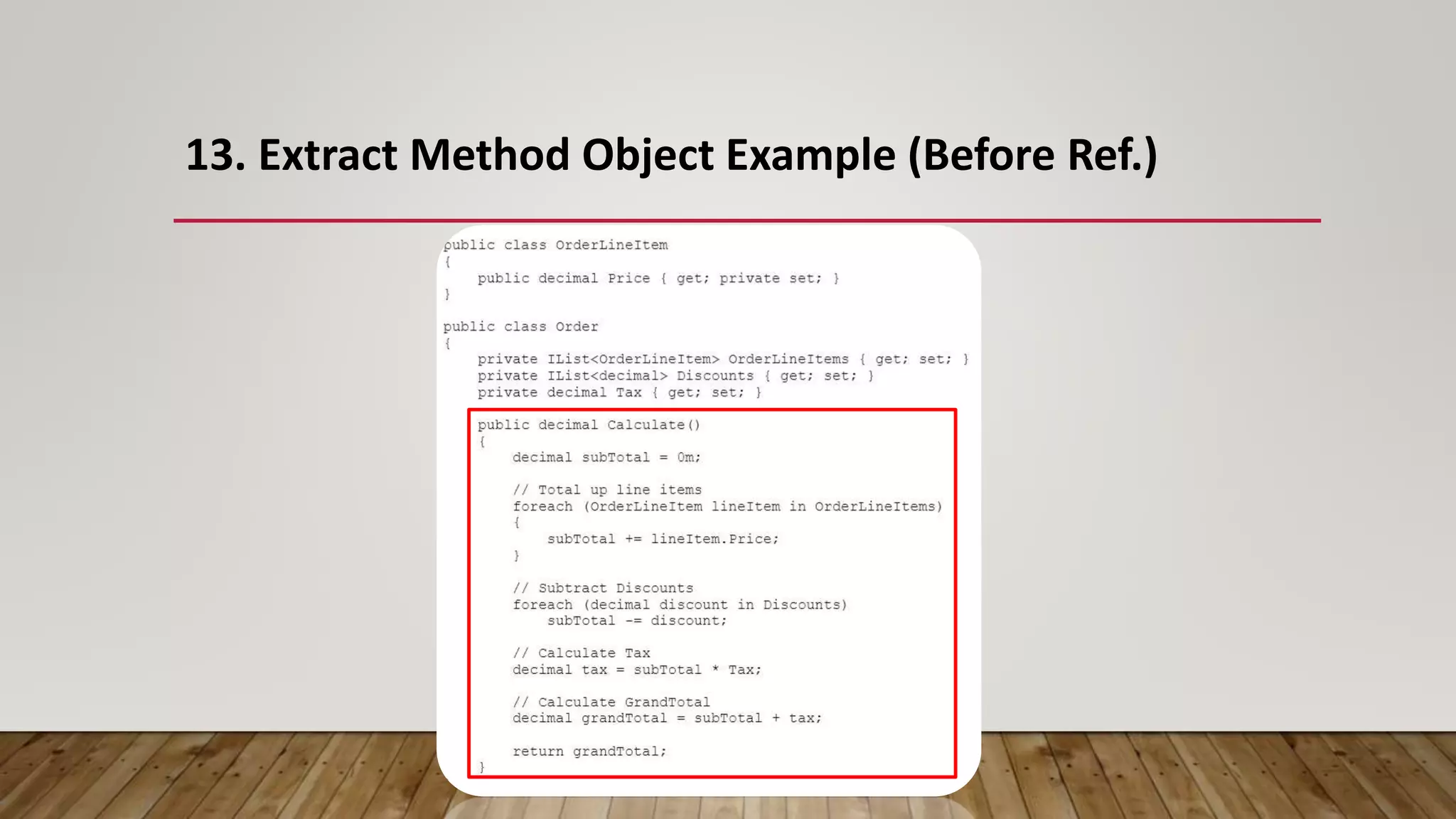
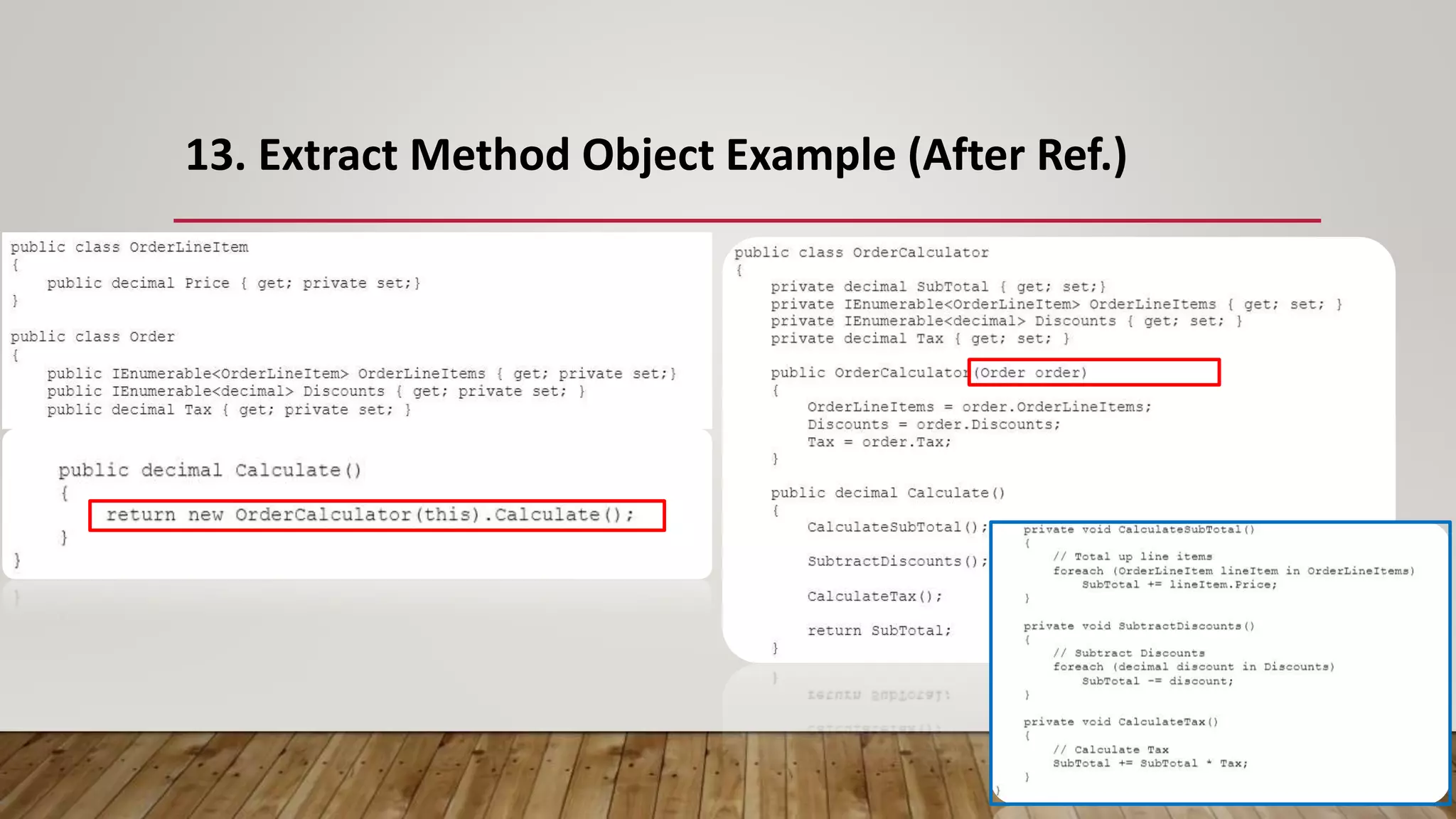
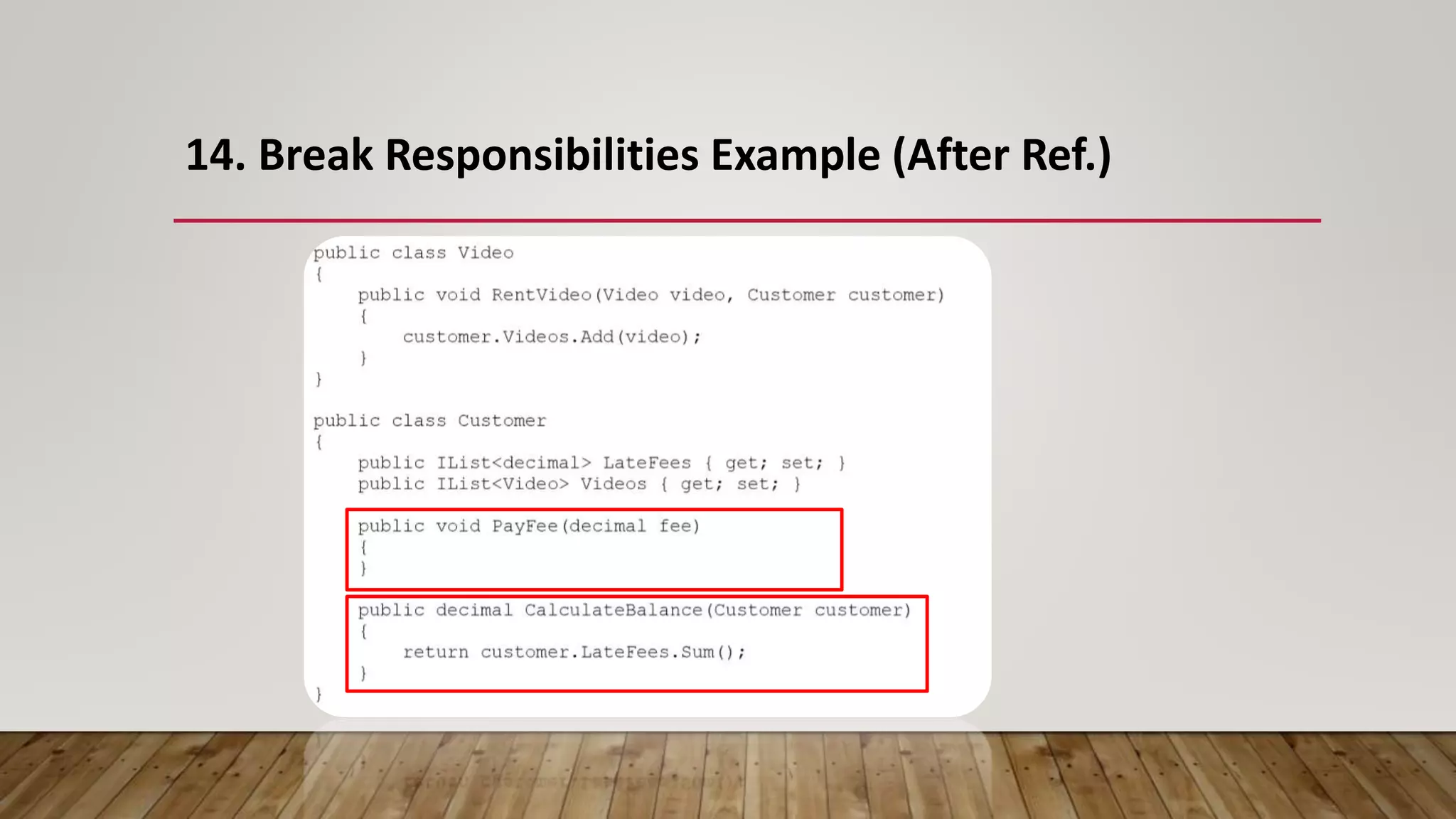
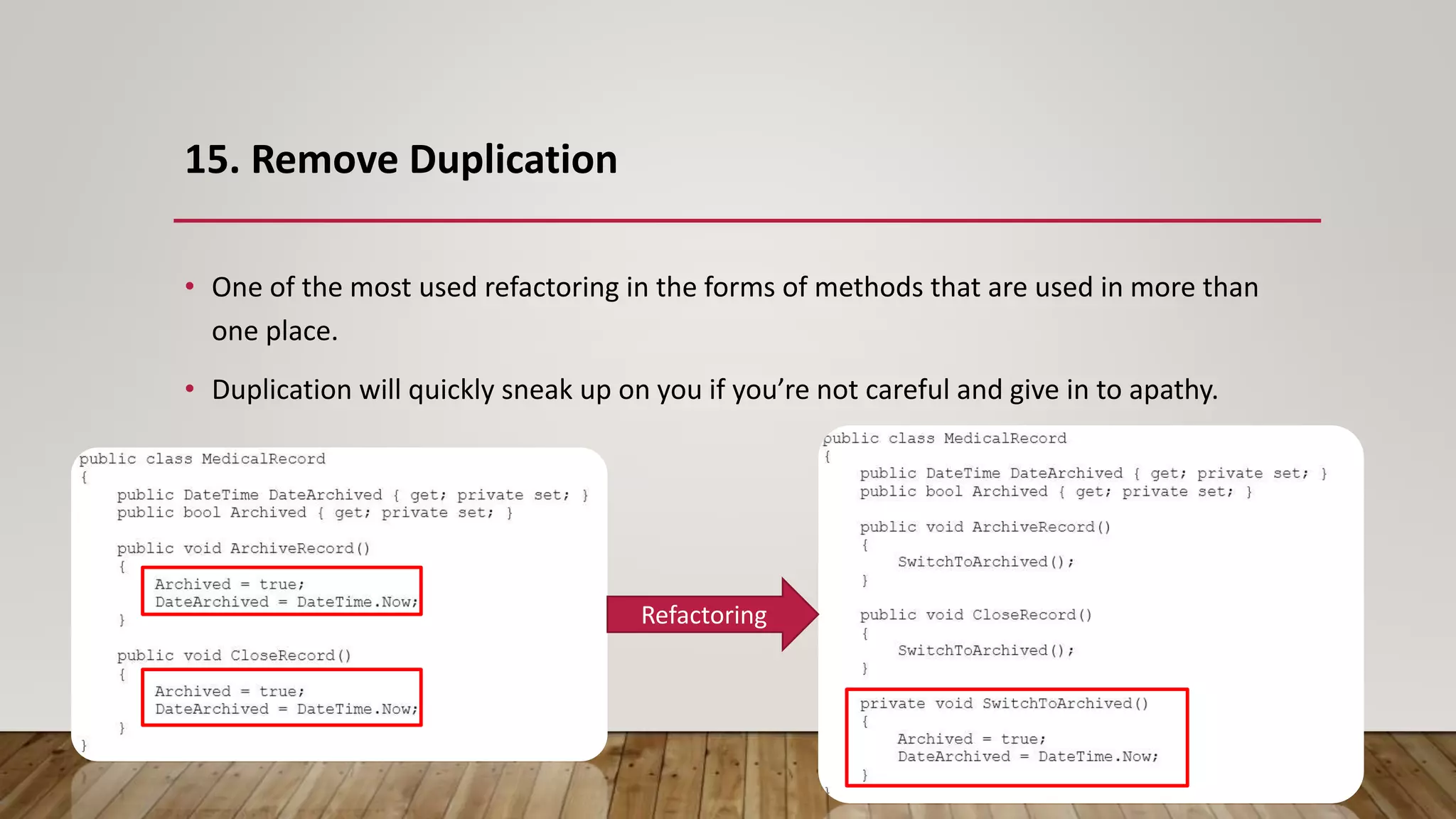
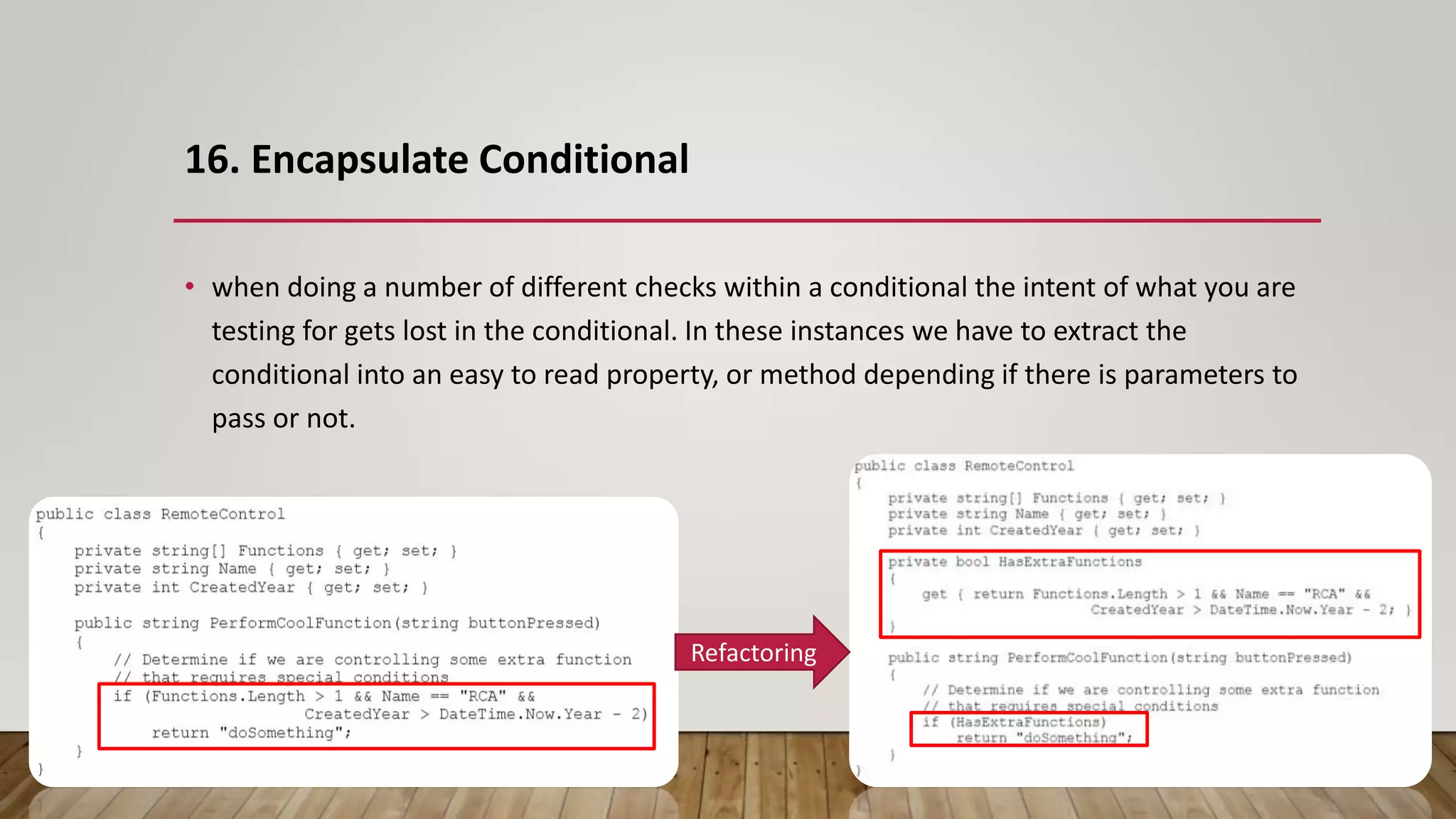
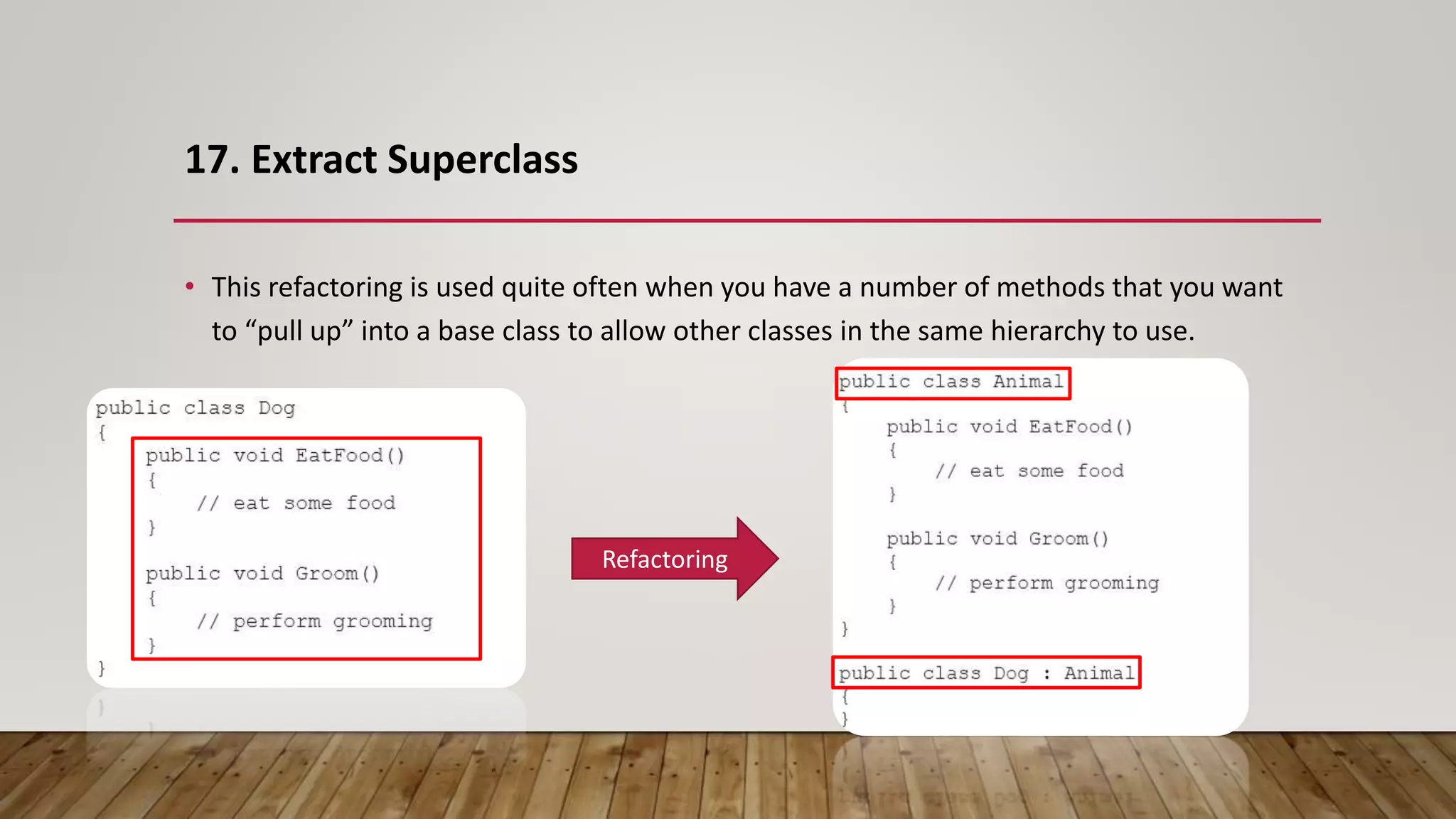
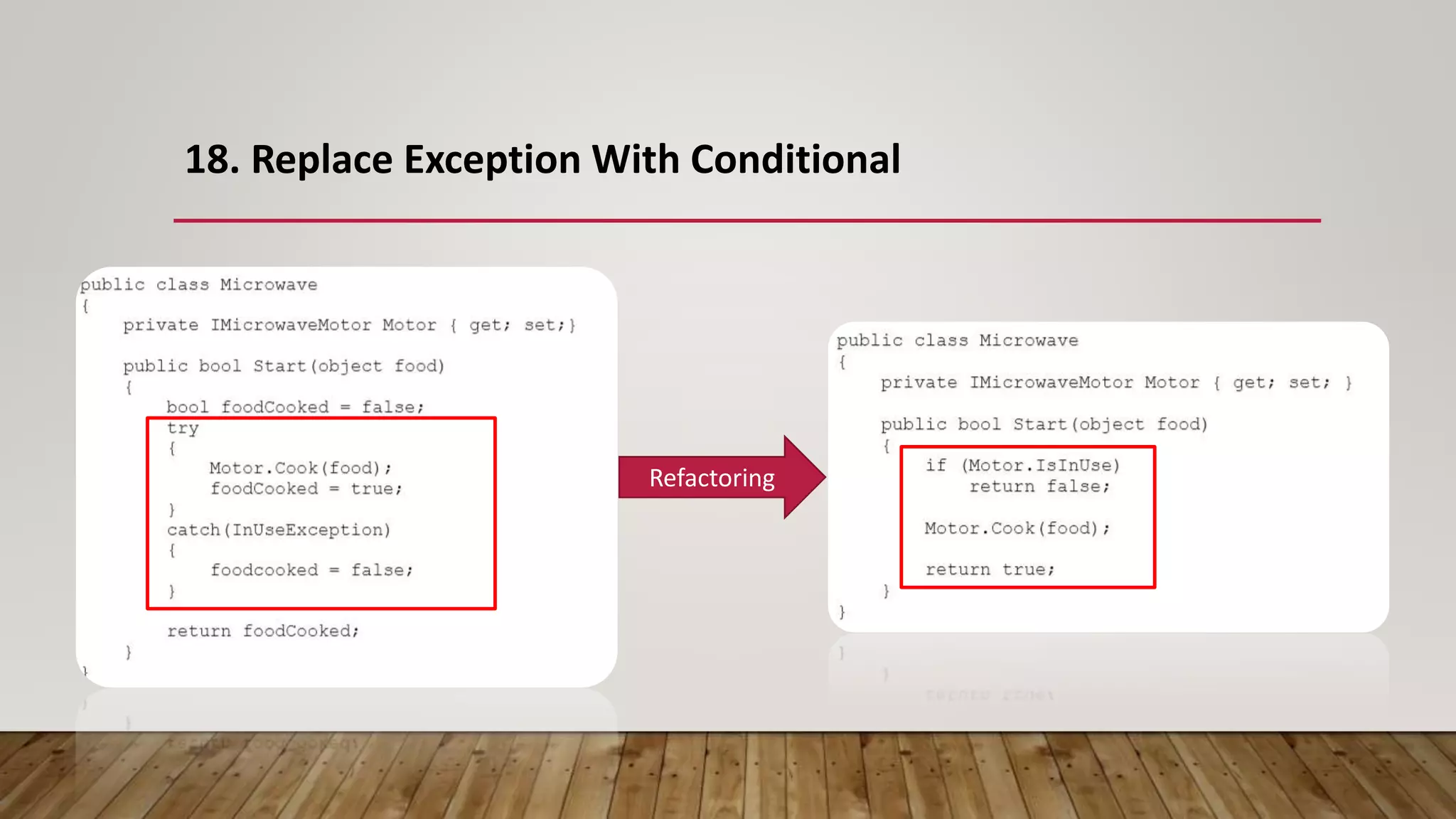
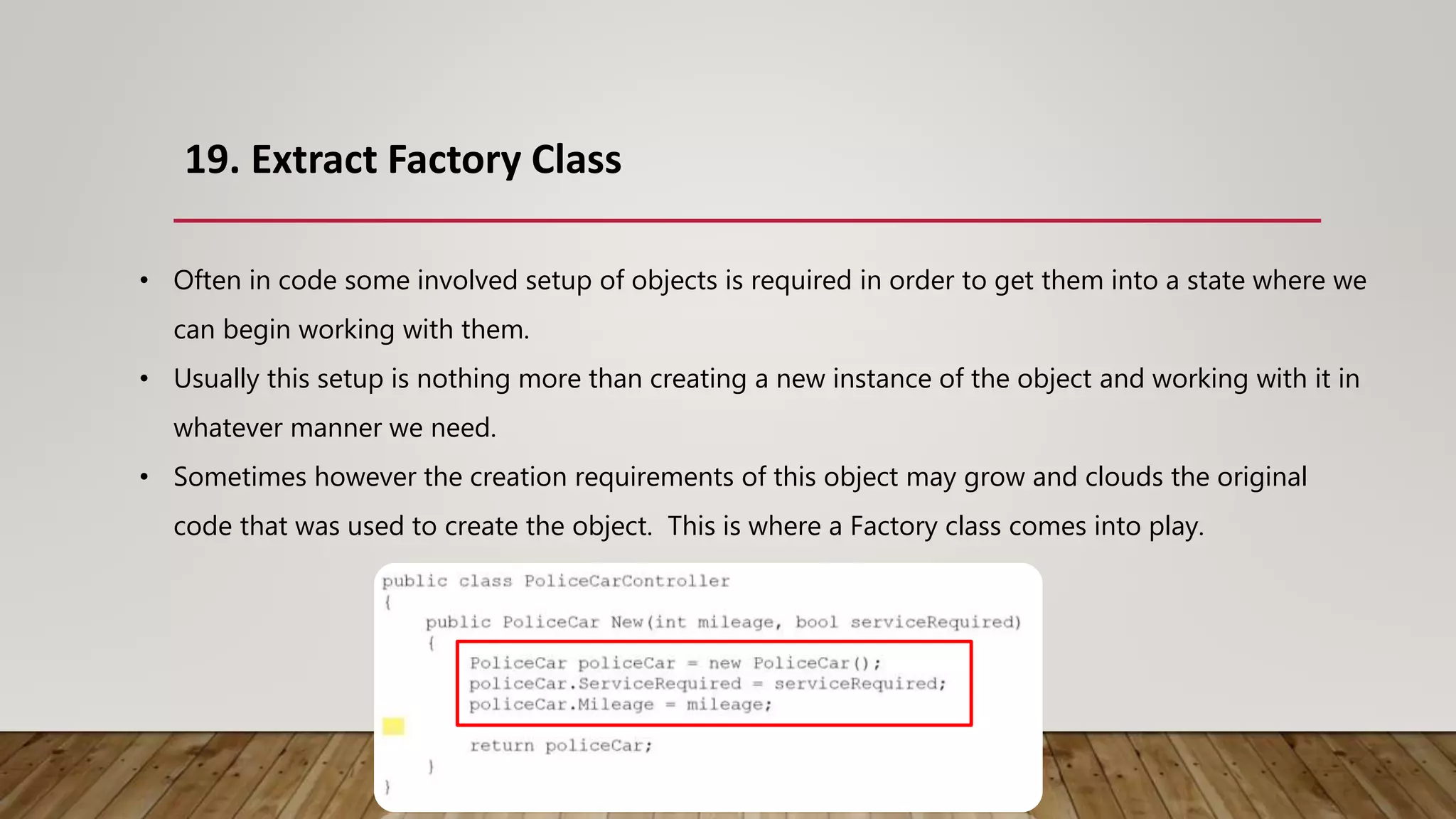
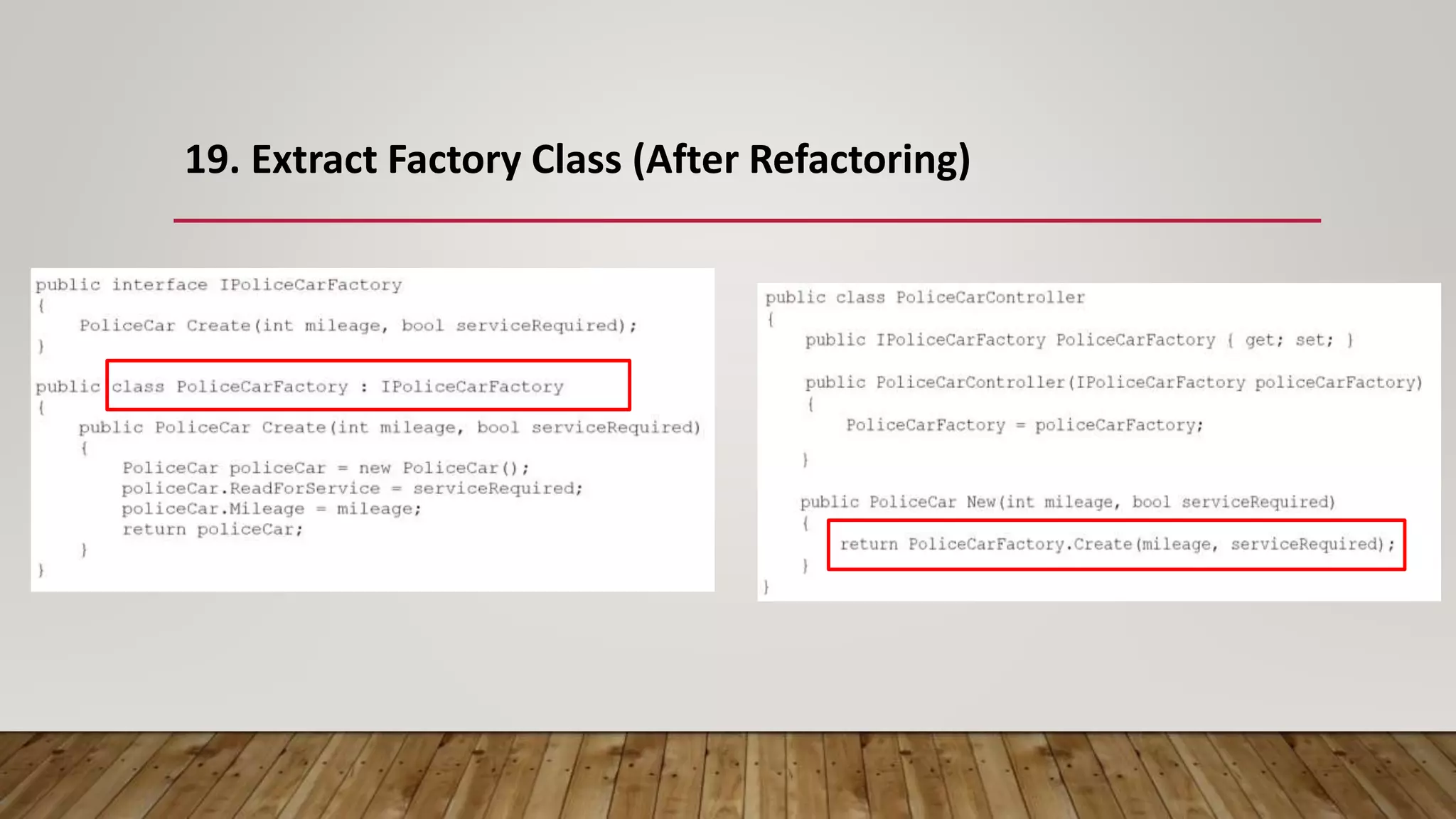
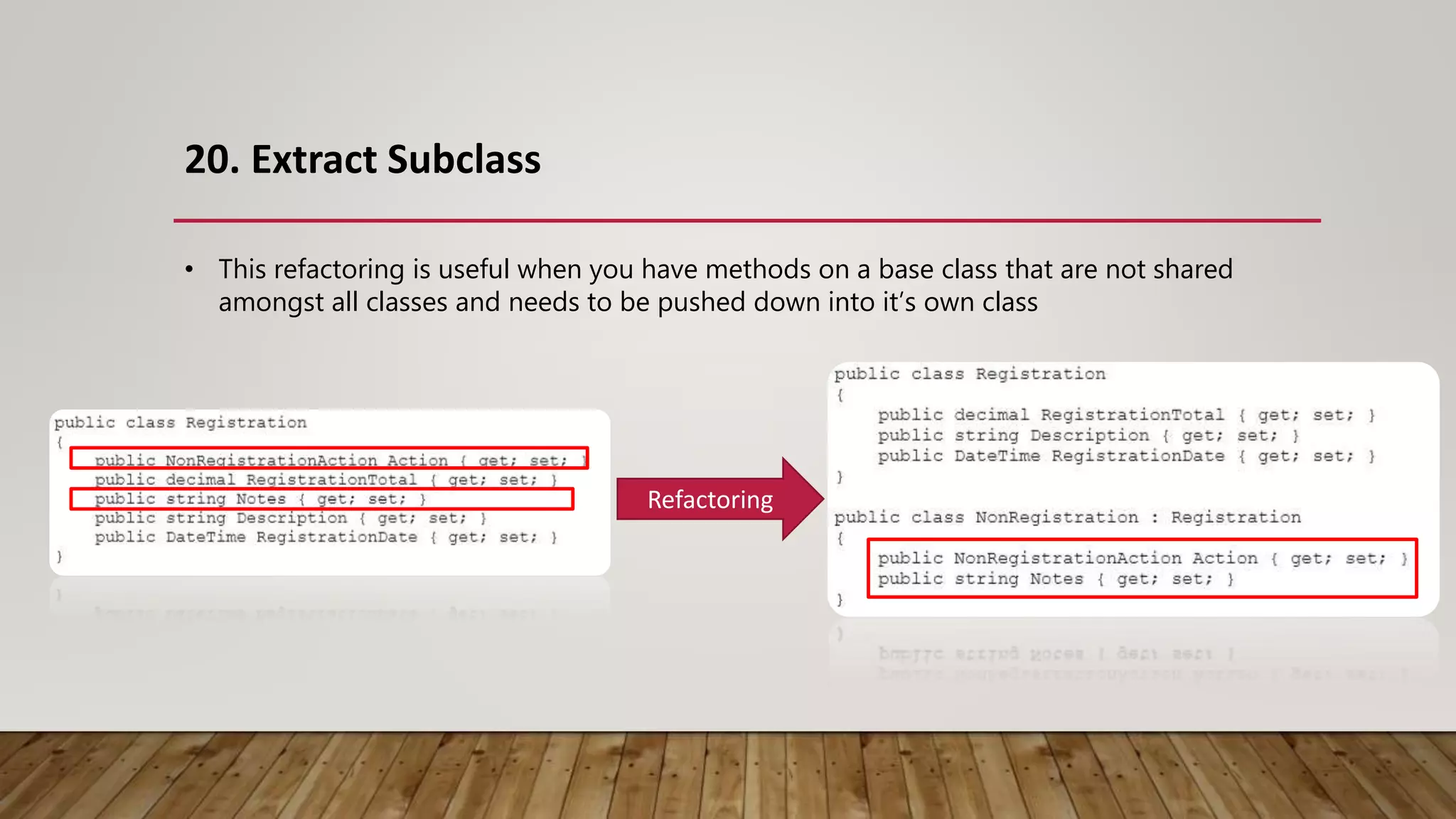
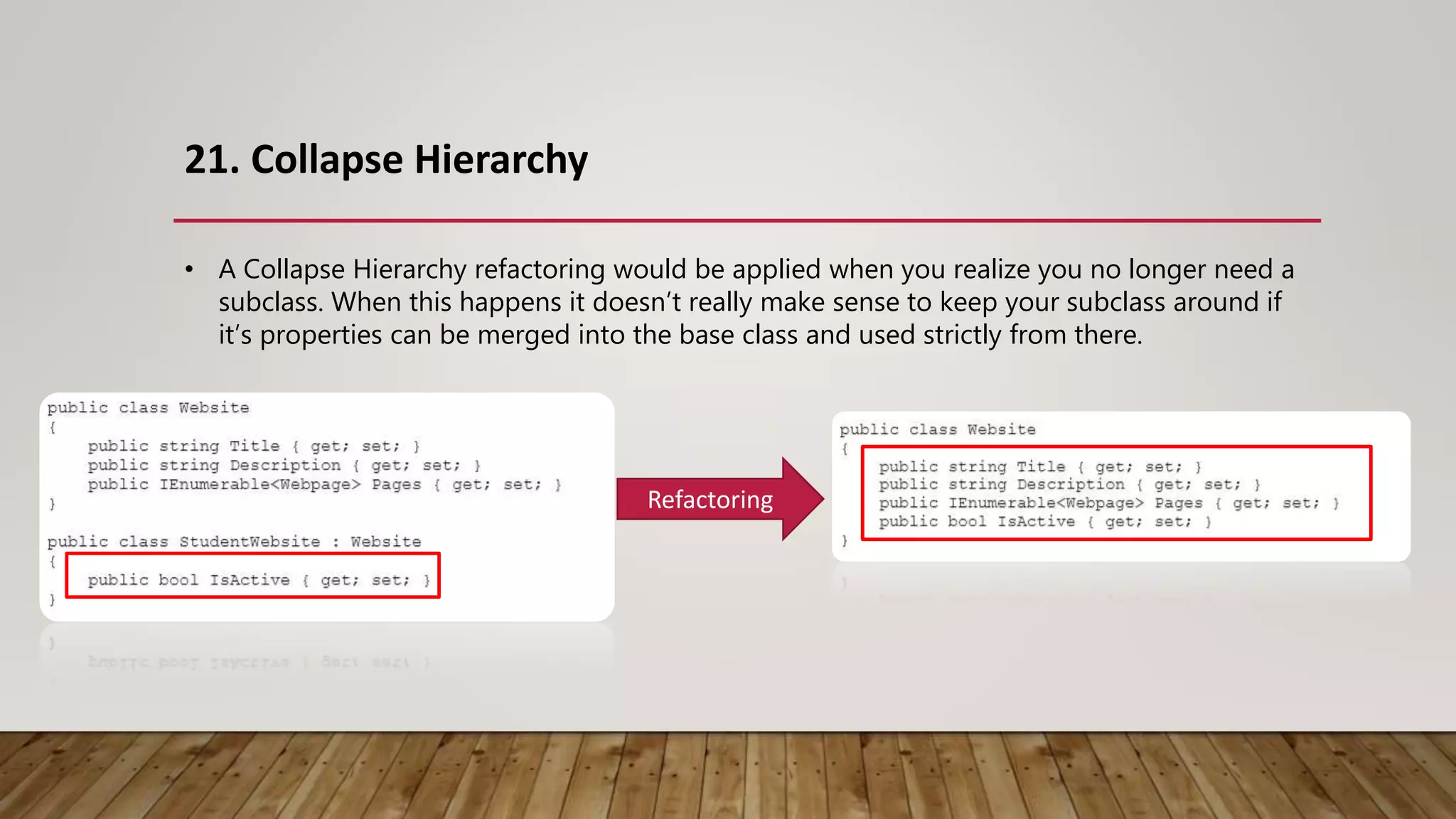
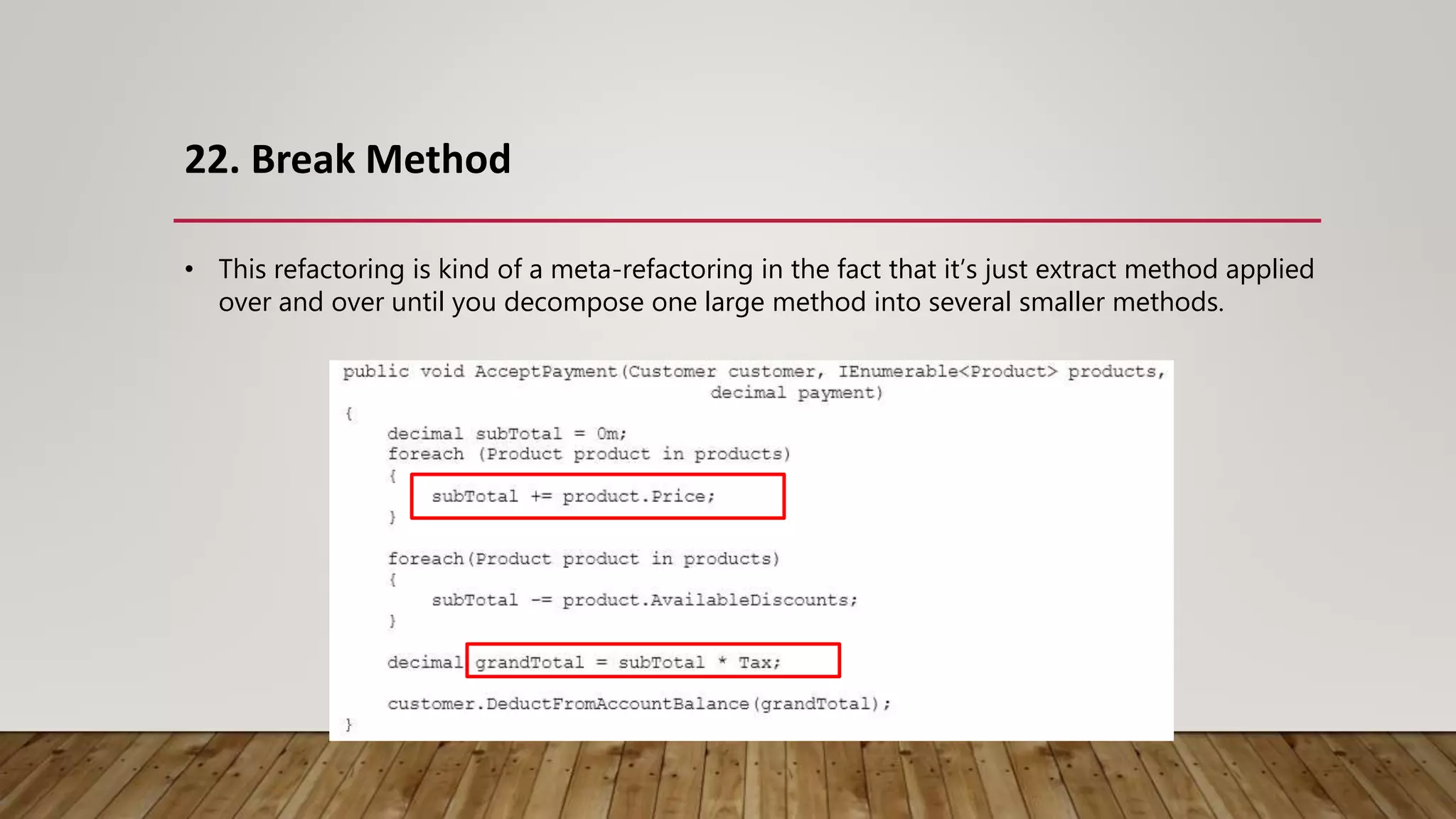
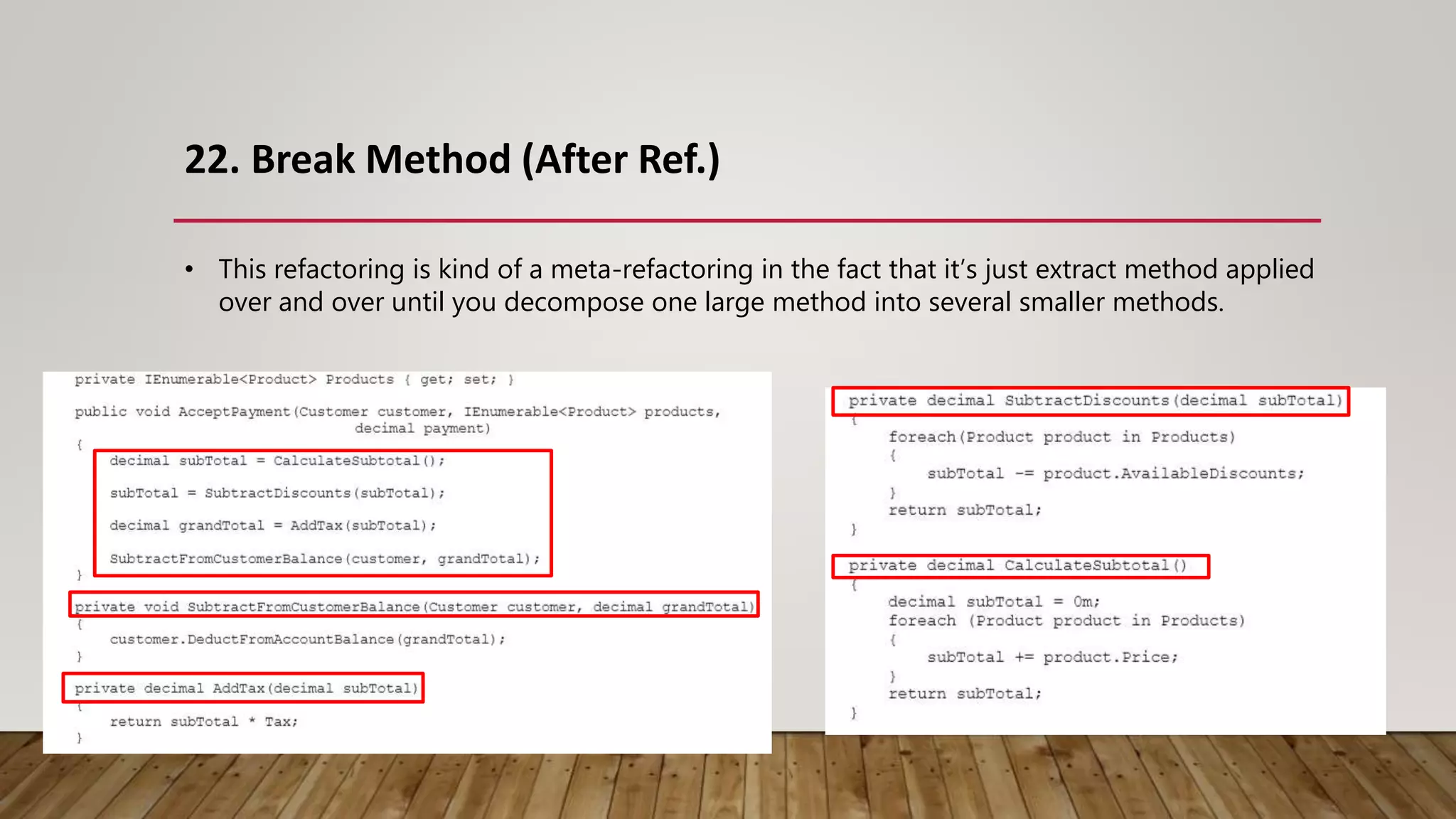
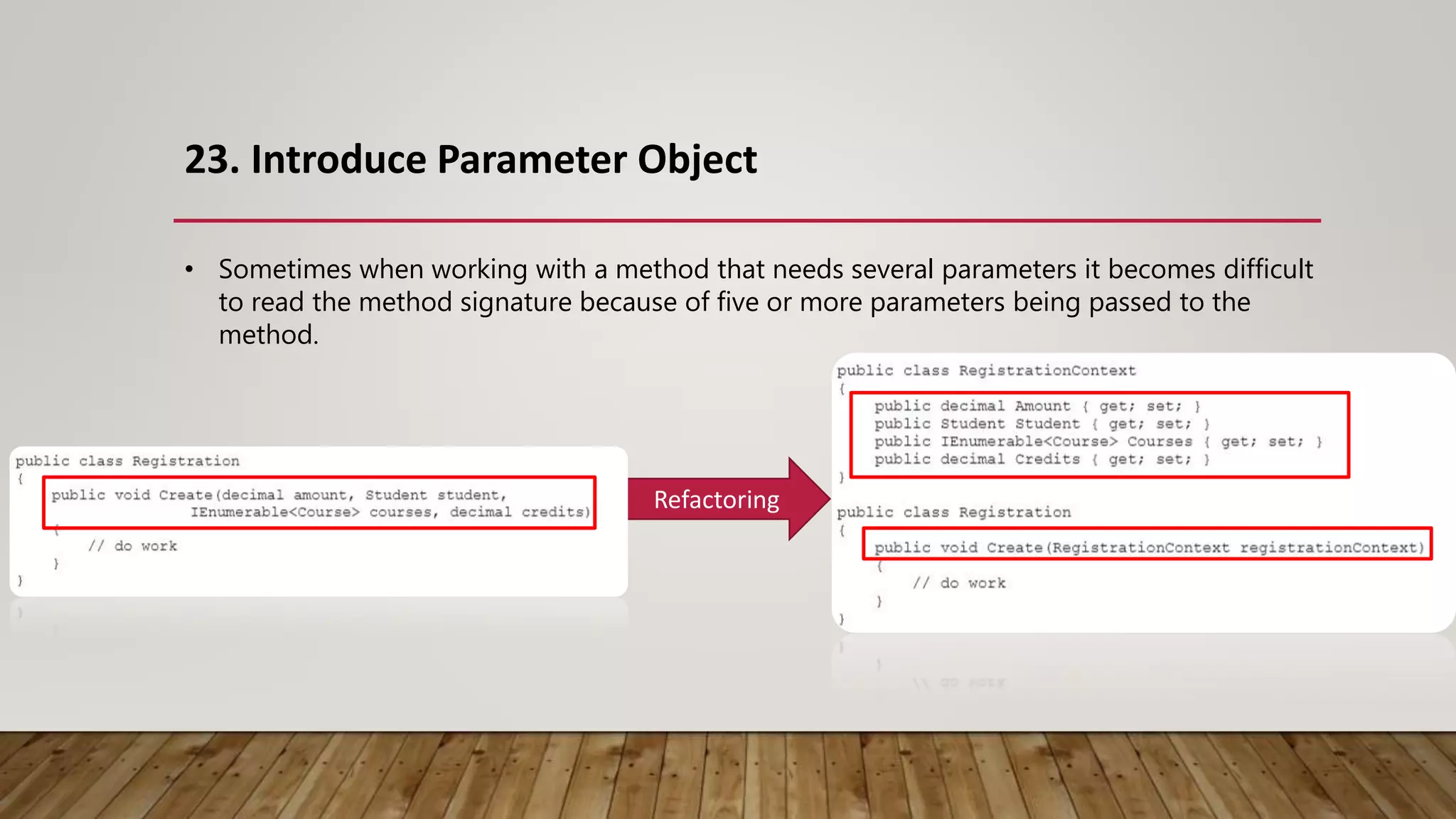
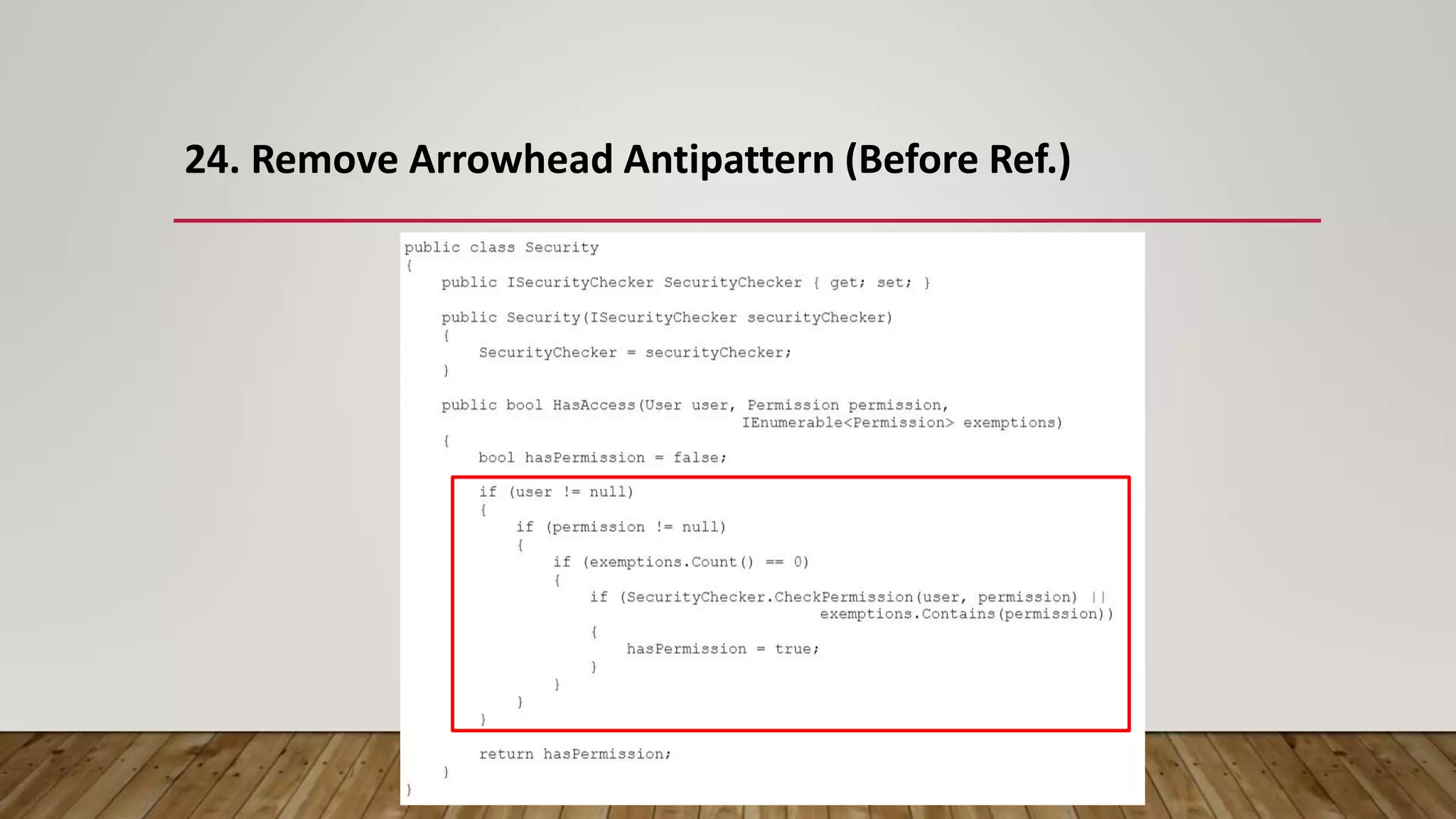
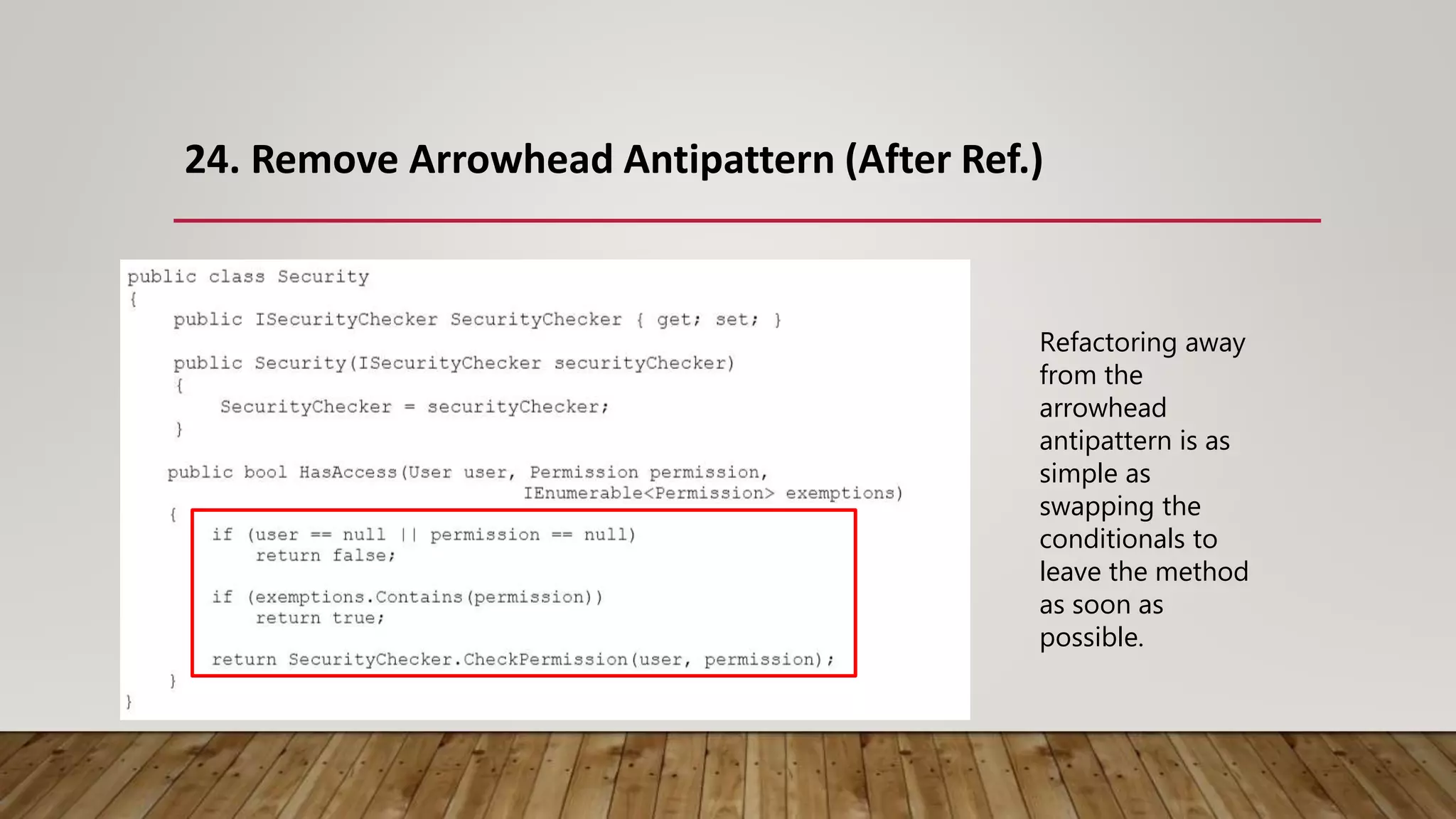
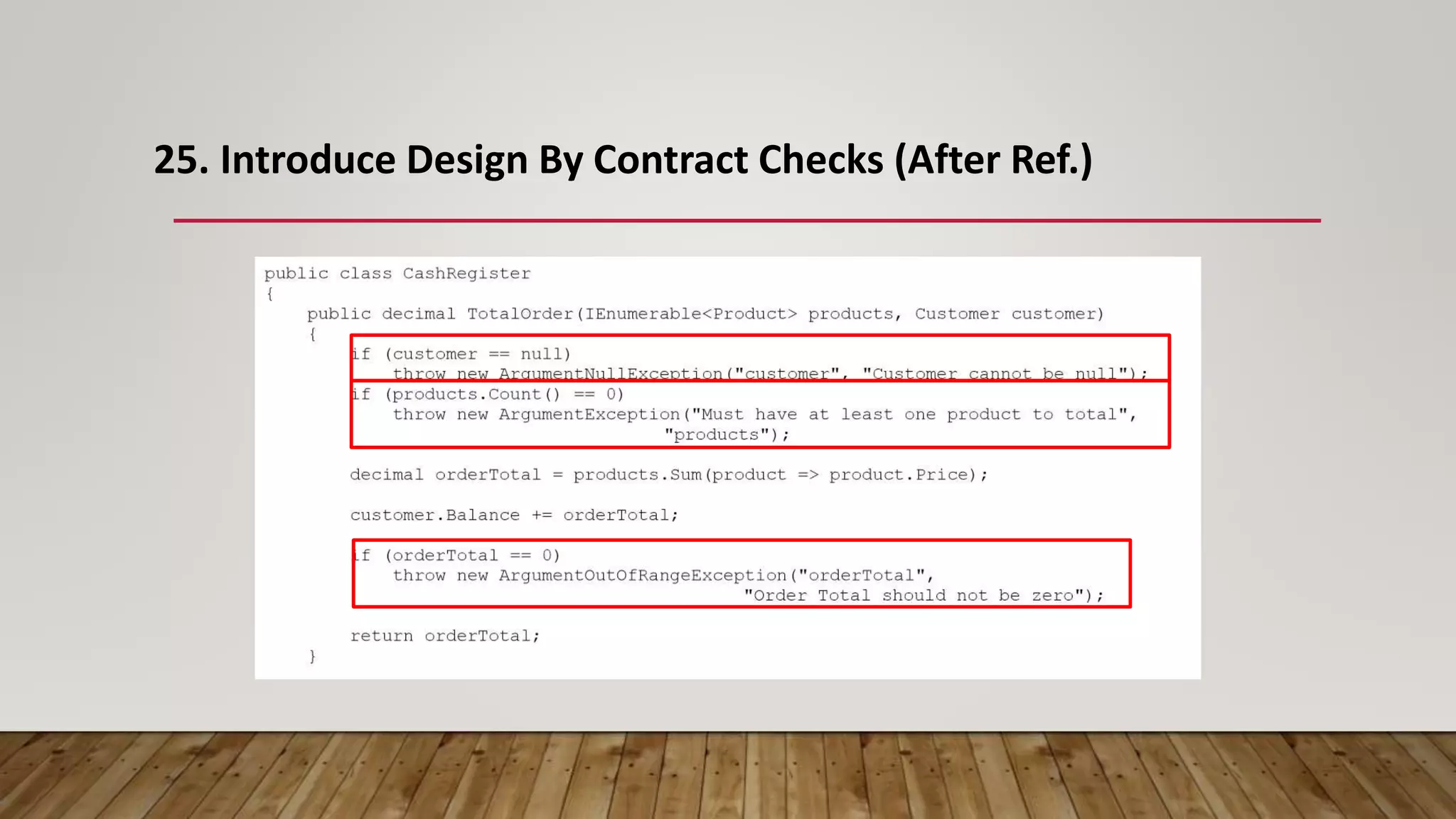
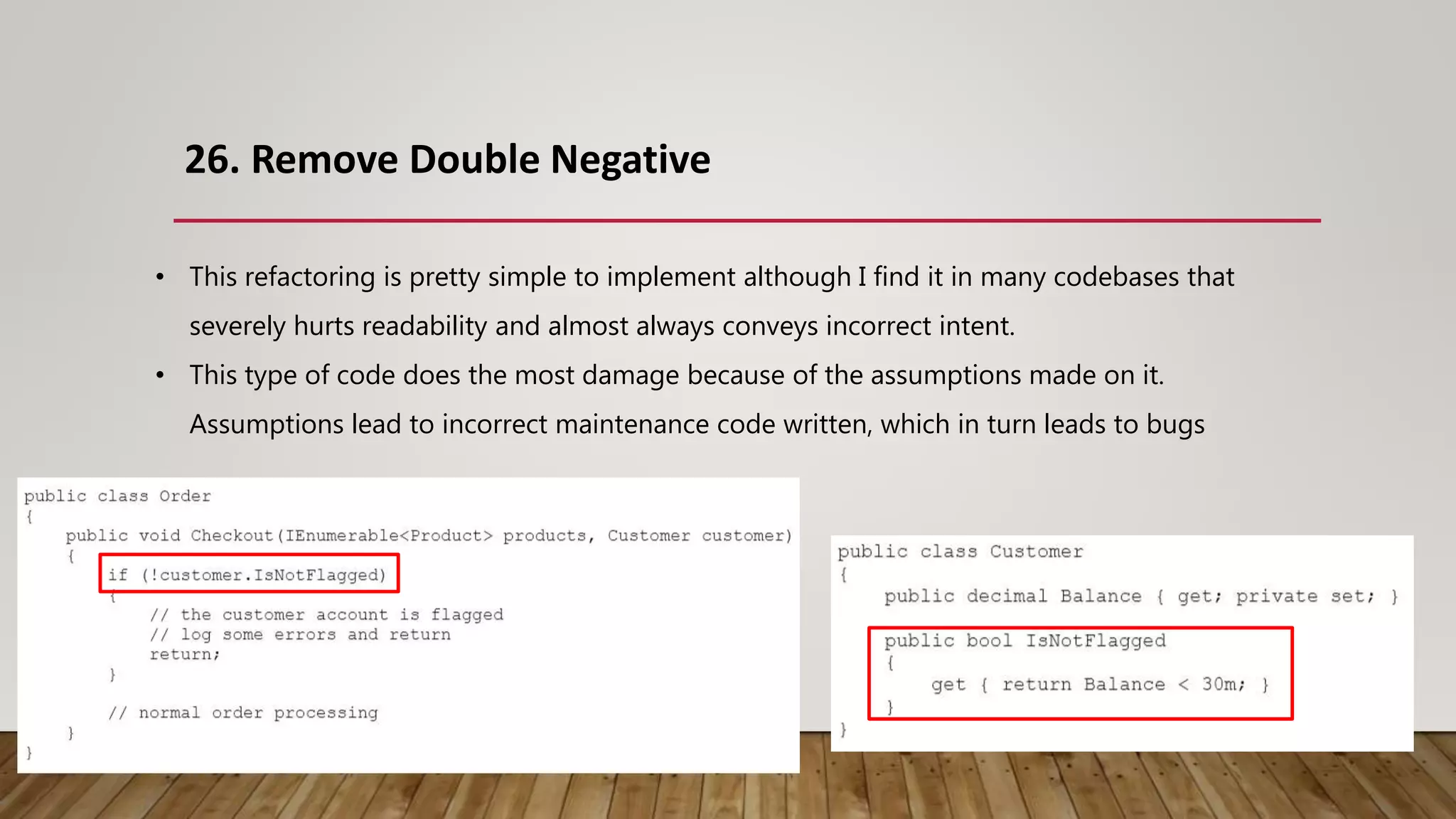
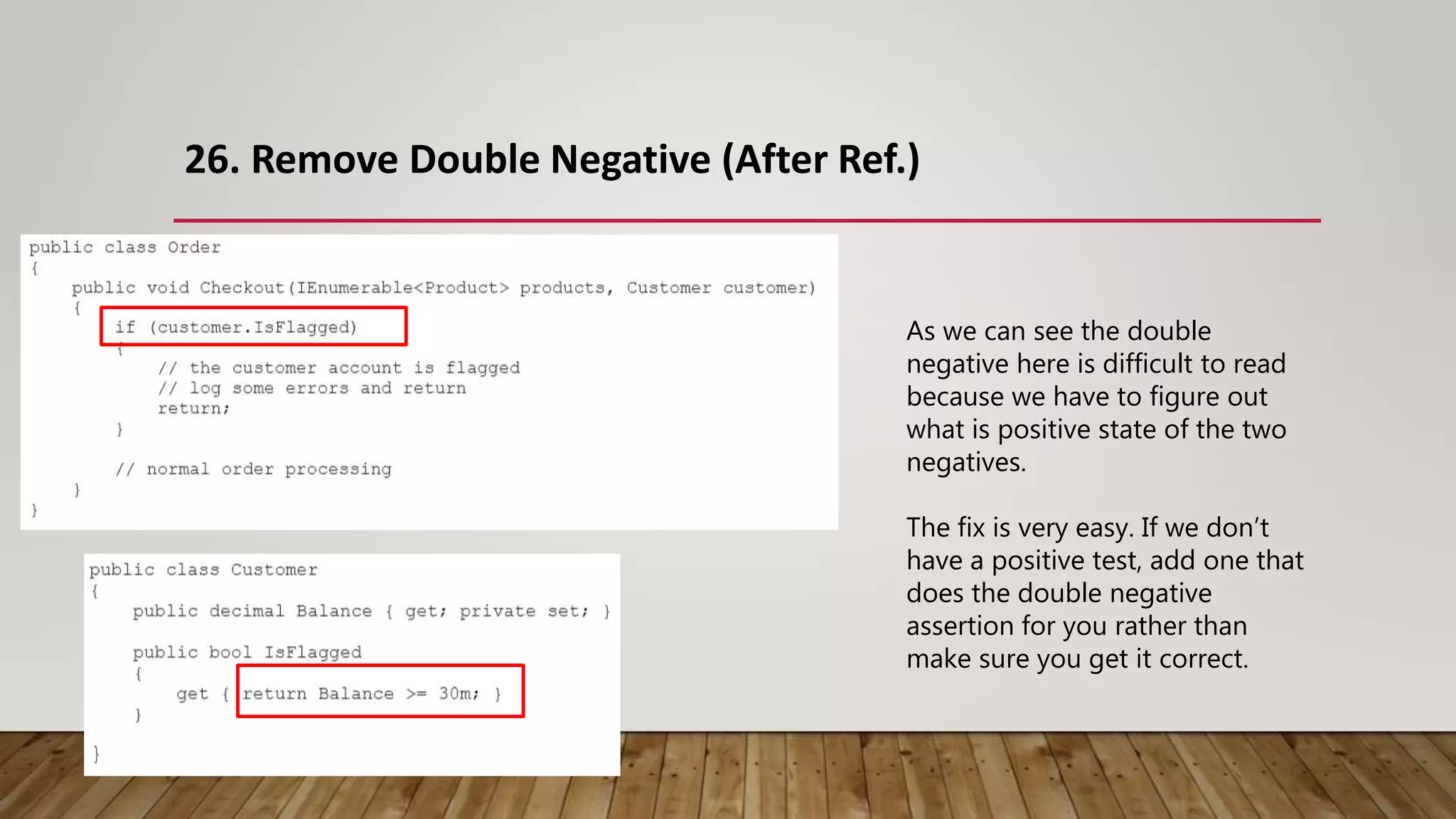
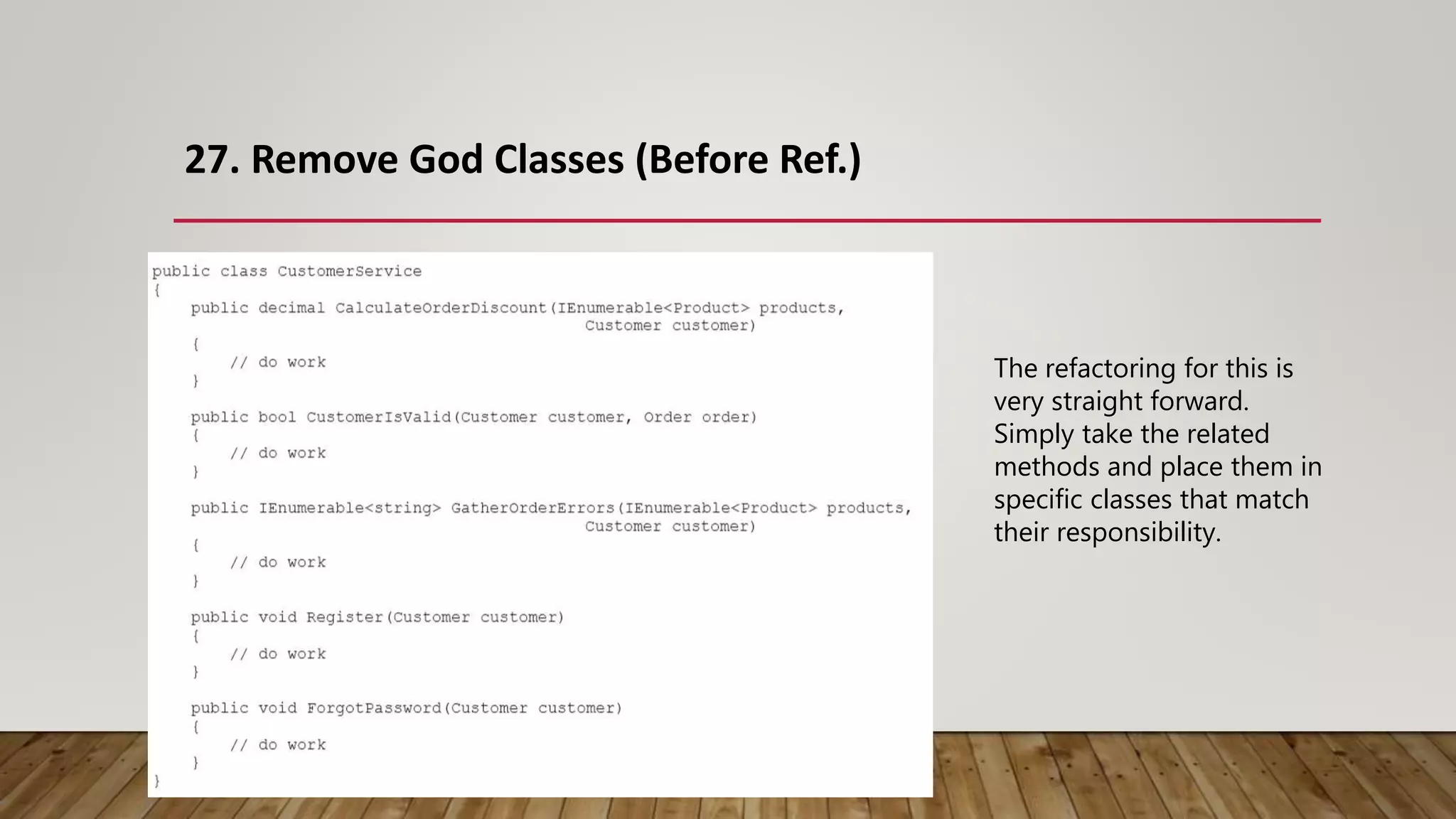
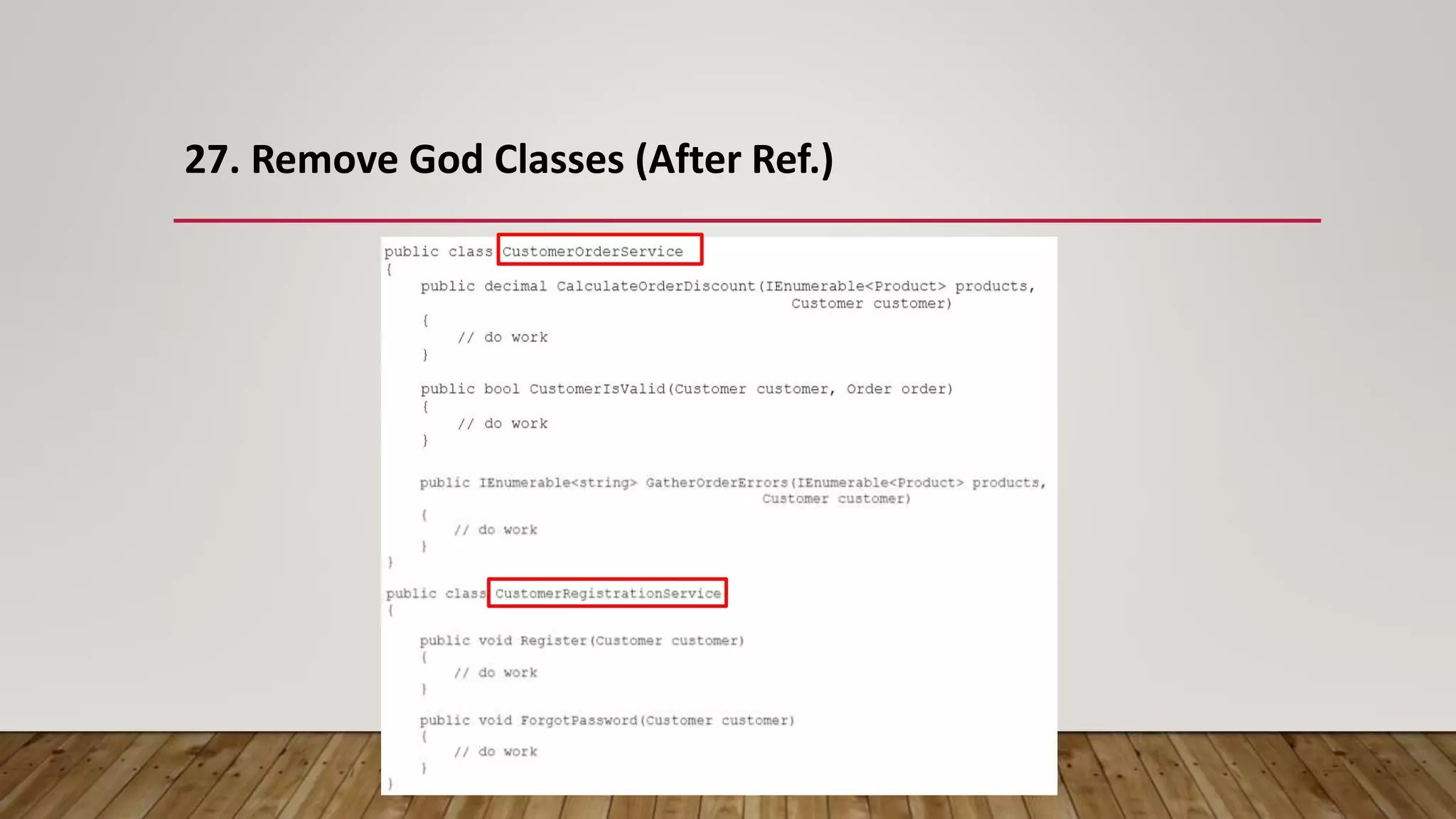
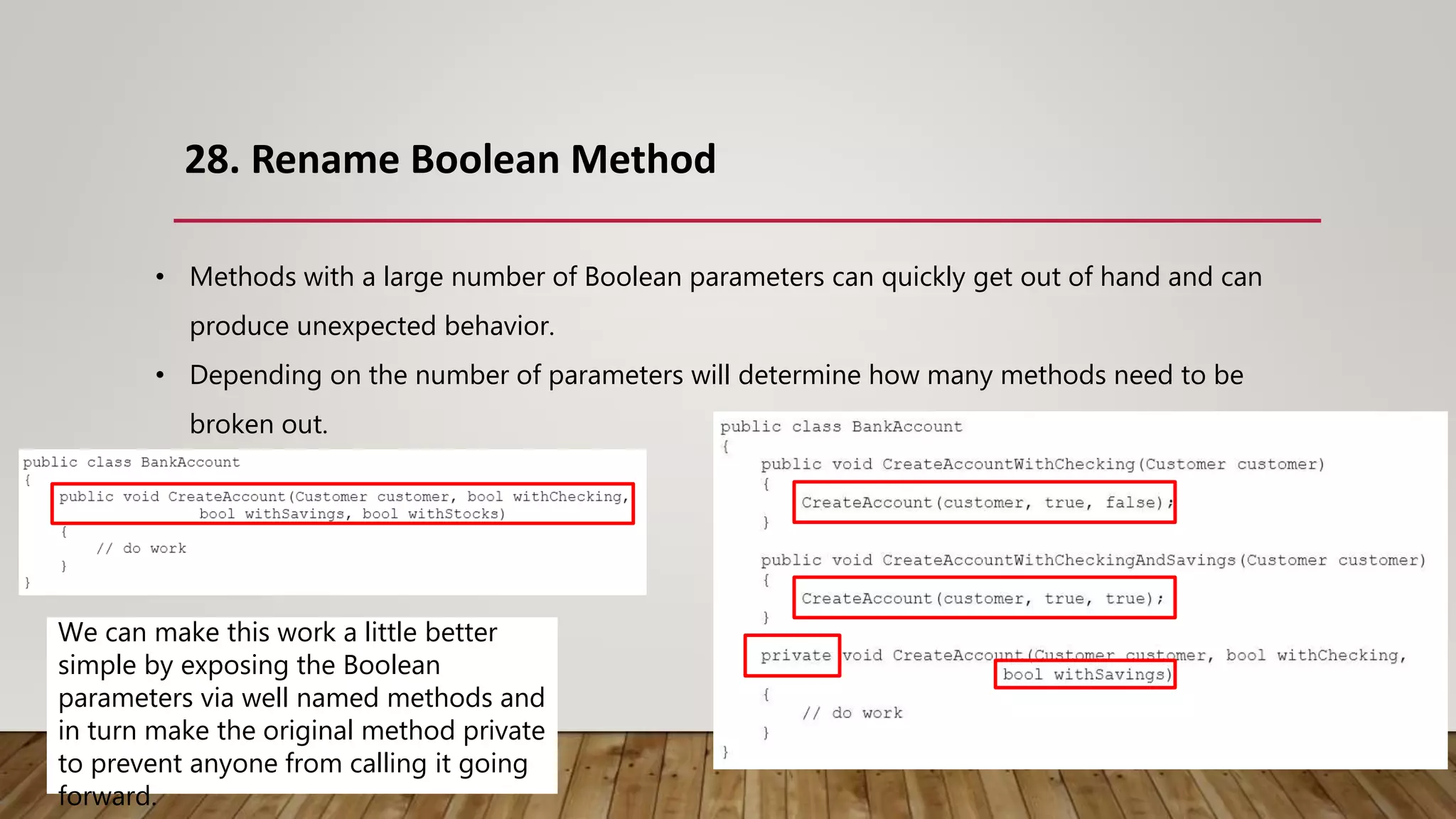
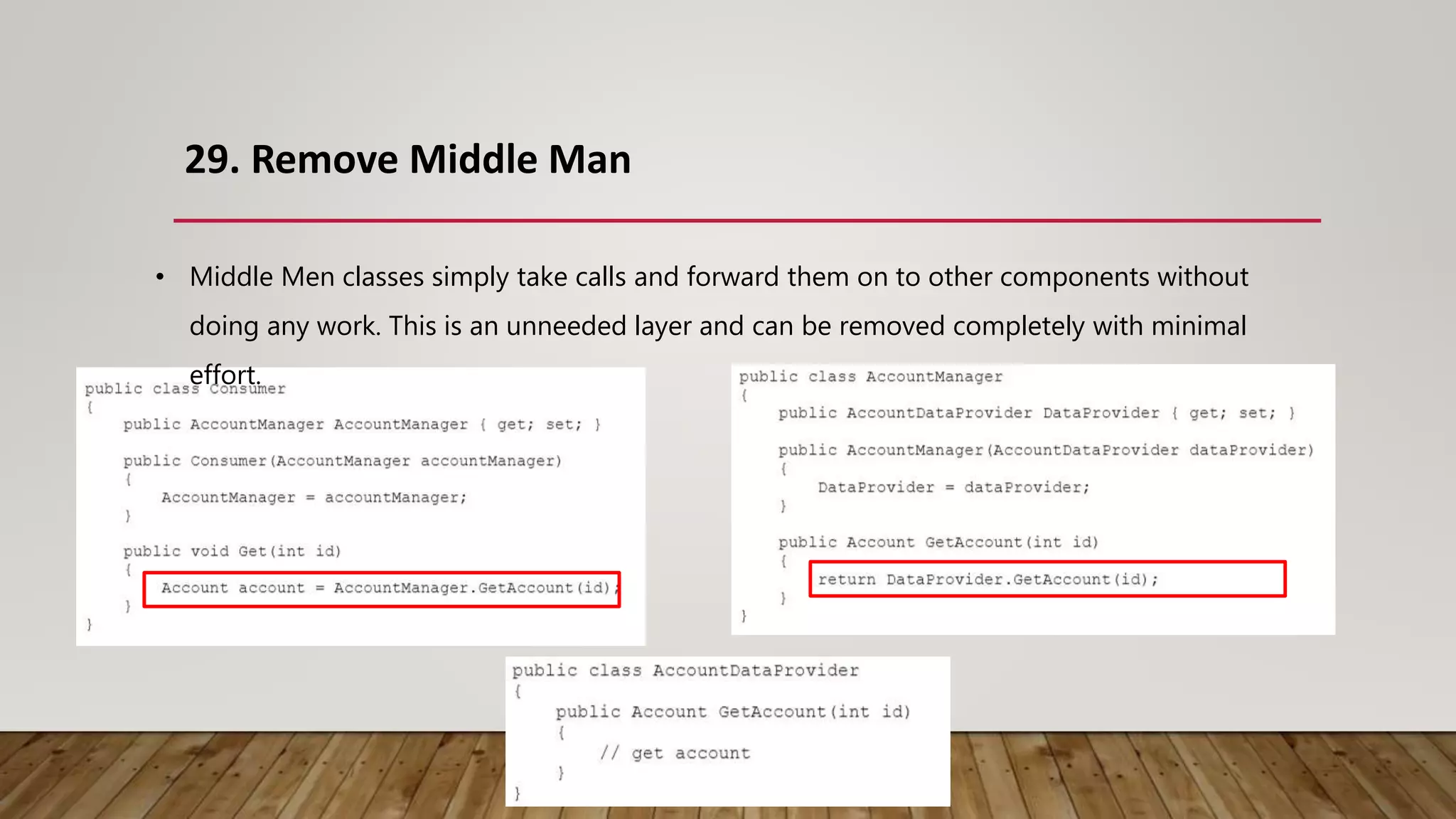
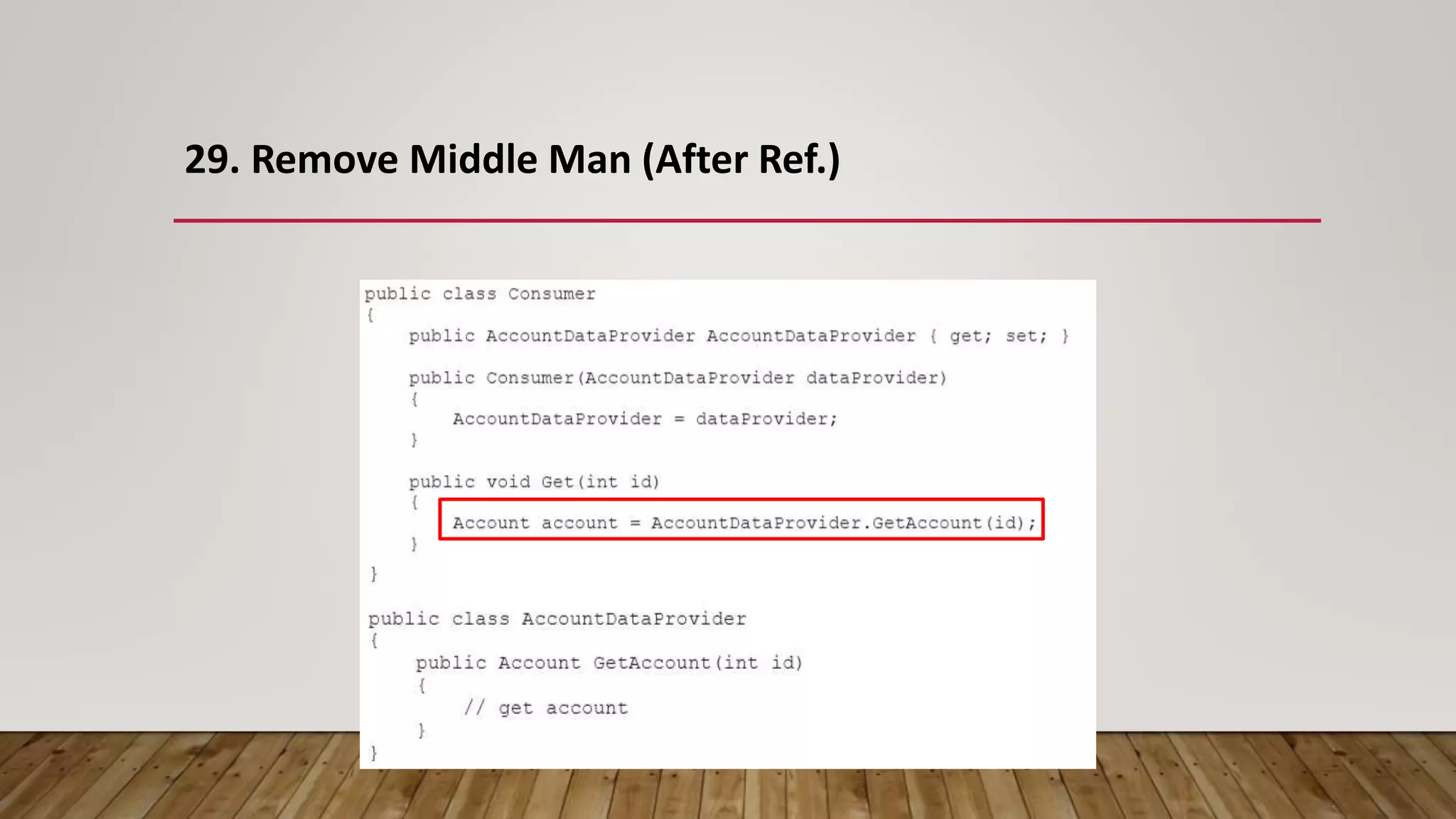
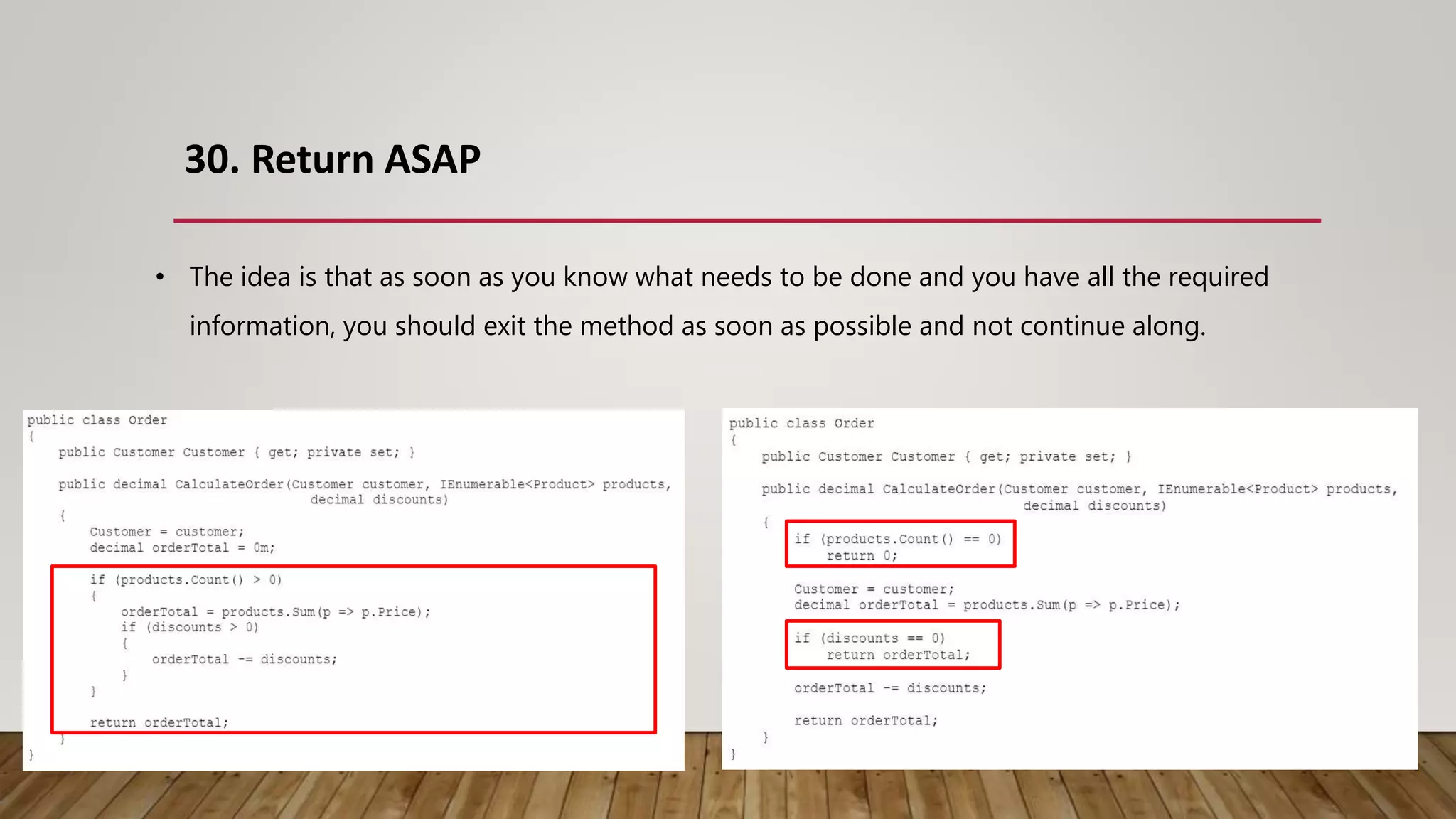
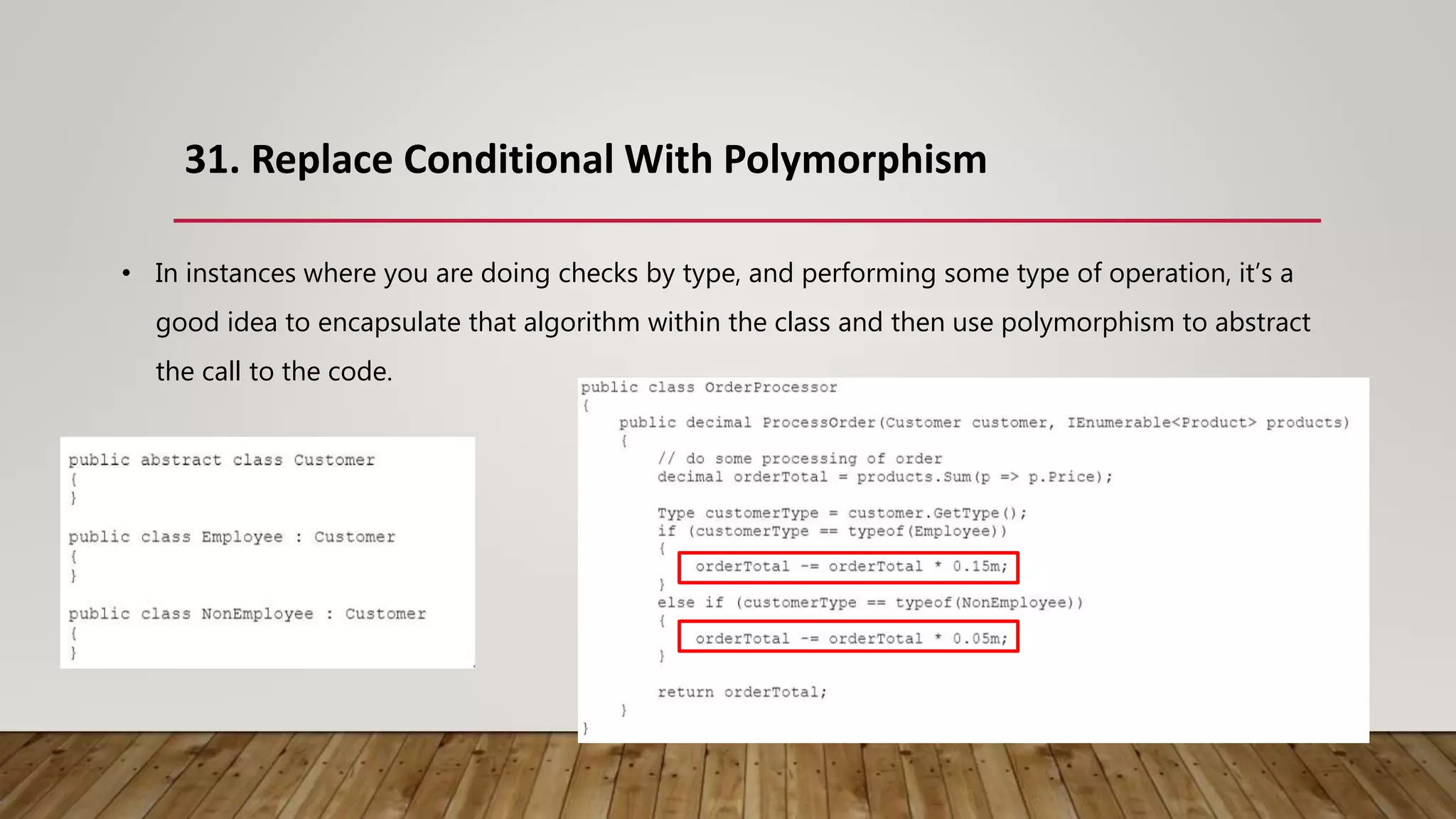
The document outlines 31 essential refactoring techniques for improving code quality, including encapsulating collections, moving methods, and managing inheritance. Each technique is explained with examples, showcasing how to enhance readability, reduce duplication, and break dependencies in code. The document serves as a comprehensive guide to effective refactoring practices aimed at enhancing software maintainability.